At best, teachers in introductory programming courses also learn to "apply" and "create." This is the essence of teaching problem solving using patterns, an approach based on the work of Christopher Alexander (i.e. the so-called pattern language movement in architecture). For example, one could argue that the following implementation is preferable because it is consistent with the implementation of max() (assuming the third implementation is chosen).
Again, these arguments are more about the programming of the solution (i.e. the style) than the solution itself. Each chapter contains a motivation (i.e. a situation in which the problem under consideration arises), the pattern (i.e. the solution to the problem) and examples.
PART I]
Patterns Requiring Knowledge of Types,
Variables, and Arithmetic Operators
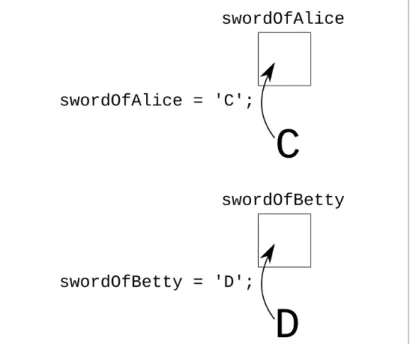
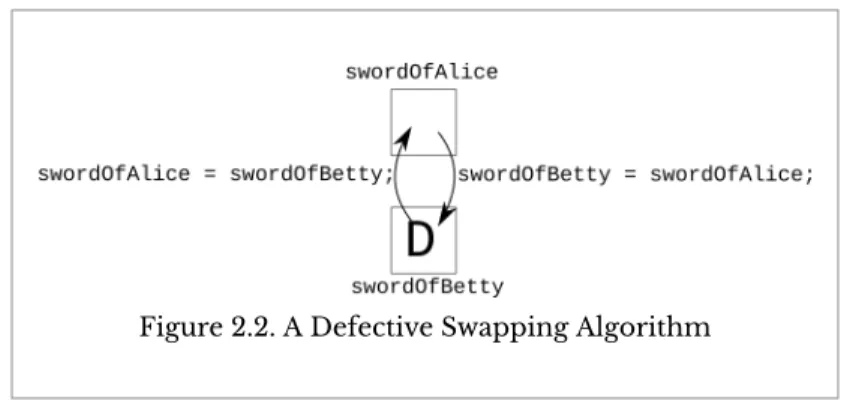
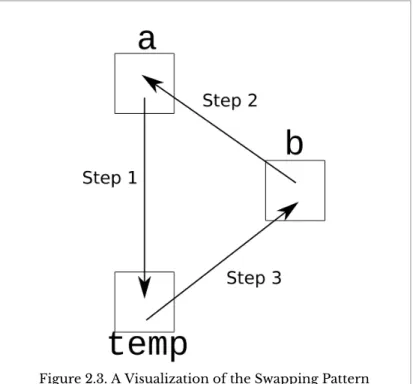
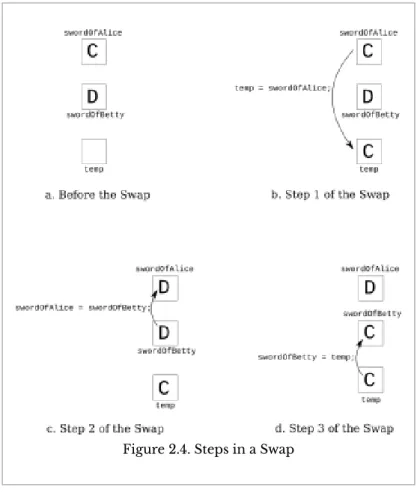
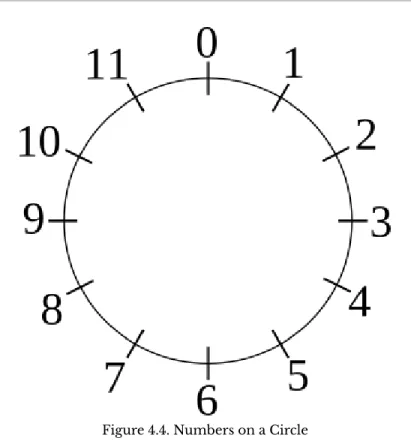
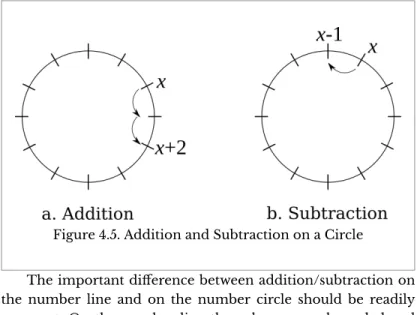
This idea can be generalized in a variety of ways by recognizing that the important pattern is the presence of the left-hand operand on the right-hand side of the assignment operator. Instead, the memory locations identified by both variables now contain a binary representation of the character 'D'. To get this part of the account number, you must first drop the leftmost three digits (i.e. you must find the remainder after dividing by
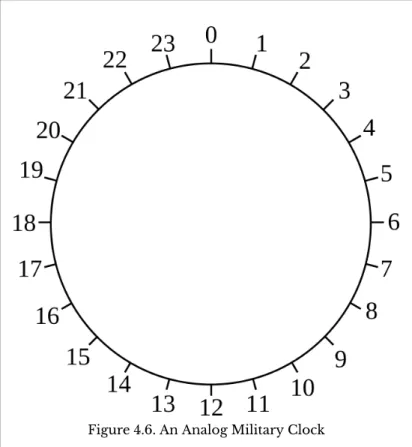
You must then drop the rightmost digit of the result (ie you must divide the result by. One common use is to determine the day of the week several days into the future.
PART II]
Patterns Requiring
Knowledge of Logical and Relational Operators,
Conditions, and Methods
It is also important to note that many of the patterns in this part of the book make use of patterns from earlier in the book. Further, there is an even more general problem where you need a method that returns a value of 0 or 1 based on the value of the parameters it is passed. Second, to determine whether the rounded value should be greater than the truncated value, compare the difference between the number and the truncated value (ie, in the example), which is also the remainder after dividing by half the amount.
Basically, this pattern is a combination of the trim pattern from Chapter 5 and the Threshold Indicator from Chapter 6. Programs often need to determine the number of work-related tasks based on the amount of work per task. If you simply divide each of these elements (by dividing by an integer) by the denominator of 3 (ie the length of the track in miles), you get a set.
So you only need to add 1 to the result of integer division to get the correct answer. Suppose you want to know if any of the bits that are set required are also set to true. Instead, you might want to know if all the bits that are set required are also set in reality.
For example, consider the 8-bit representations of the food mask and the water mask. In general, it is the value of what it complements, which is referred to as the base (or radix) of the logarithm. Instead, typecasting is used to get the integer part of the value returned by Math.log10().
PART III]
Patterns Requiring Knowledge of Loops,
Suppose you need to write a program that works with all elements of a sequence of numbers (for example, double values). It then returns the average of the elements of the array after the minimum has been reduced. The purported advantage of this approach is that there is one less iteration of the loop.
In some cases this can be achieved with multiple accumulators as discussed in Chapter 13. The expression data[i] / 10 is used to calculate the index (i.e., centile) of data[i] in the accumulator array, and the statement count[centile] += 1; increases the value of the . This pattern works best when the accumulator index calculation algorithm is simple.
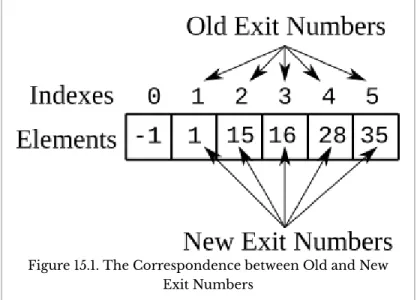
Later, freeway exit numbers were changed to (at least closely) correspond to the mile marker (i.e., the number of miles since the start of the freeway). Since the bounds are homogeneous (ie, they are values of the same type), they can be stored in a single array. There is no need to do the interval membership search separately for each of the two lookups.
People's names are stored in string[] named fieldA, and the number of sci-fi books they own is stored in int[] named fieldB. Suppose you have two arrays of the same size, both of which contain duplicate values. An array with twice as many elements can obviously hold all the values in both strings.
Then you could store all the elements of both arrays in one array of length 8. Regardless of the implementation, the end result is an array organized as shown in Figure 18-1.
PART IV]
Advanced Knowledge of Arrays and Arrays of
Arrays
Most examples of arrays you've seen probably involve repeating all the elements. However, there are many situations where you only need to iterate over some of the elements in an array. The problem with this implementation is that it doesn't allow you to find the sum of a subset of the elements.
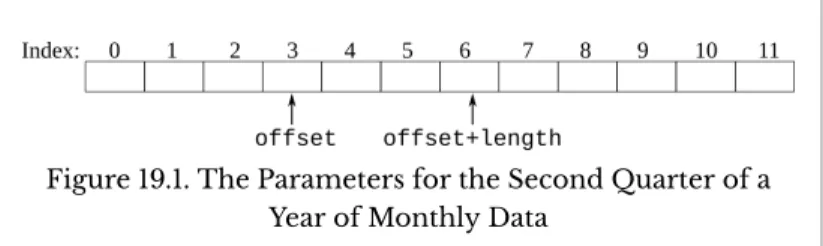
The easiest way to solve this problem of iterating over a contiguous subset of the elements is to add two formal parameters, the index to start at and the size of the subset.2 1. T he subarray pattern, discussed in Chapter 19, considers some problems where calculations need to be performed on only some of the elements of an array. To blur a discretized audio track or visual image, calculate the (weighted) average of the elements that are near a particular element.
If we were to use the subset pattern from Chapter 19, we would describe the subset of elements in Figure 20.1 with offset 3 and length 3. Similarly, we would describe the subset of elements in Figure 20.2 using roffset (row offset) of 1, offset (column offset) of 1, rlength (row length) of 5, and col umn length of 5. When domain experts think about a fuzzy problem, they think about computing multiplied by the average of the elements that are close to the central element.
As in the subarray pattern of Chapter 19, you must add formal parameters to the signature of the method you are dealing with. You may also need to use a "plus sign neighborhood" that includes only the elements in the row or column of the center element. Regardless of the approach, you must correctly count the elements that are in the total.
PART V]
Patterns Requiring Knowledge of String
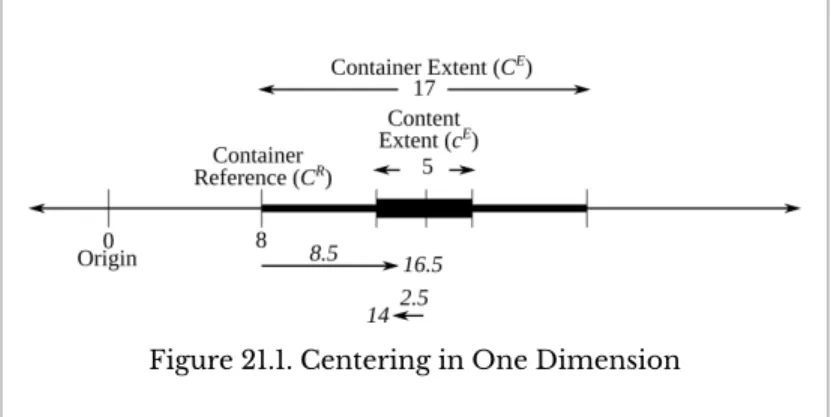
The focus problem is finding the reference to the content, given the reference and scope of the container and the scope of the content. First, you need to calculate the midpoint of the container (which had a reference of 0 and an extent of 9 in the example). Next, you need to calculate the midpoint of the content (which had a width of 5 in the example).
Finally, you need to calculate the reference to the content by subtracting the midpoint of the content from the middle of the container. The fully calculated midpoint will either "lean" to the left or right of the real-valued conceptual center. When the container span is odd, the calculated midpoint will be at the conceptual center.
On the other hand, when the container span is even, the calculated midpoint will "bend" to the right. When the content span is odd, the calculated midpoint will again be at the conceptual center. On the other hand, when the content span is equal, the calculated midpoint will again "tilt" to the right.
When the container has a scope of 9, the content reference will be 4 - 2, or 2 if the content has Program Patterns 137. When the container has a scope of 8, the content reference will be 4 - 2 or 2, regardless of whether the content has a scope of 5 or 4. Calculate the width of the source field (this field will be // right-aligned).
PART VI]
Knowledge of References
In this case, the method simply changes the attributes of the external formal parameter (which is an alias for the actual parameter). In the latter case, the method will construct an instance of the external parameter, modify it, and return it. In the first variant, you want the method to return true only when all items in the checklist have been completed.
Note that this algorithm breaks out of the inner loop once it determines that the checklist item of interest has been reached. So, if both loops terminate normally, all the items on the checklist must have been completed and the method returns true. In the second variant of the pattern, you want the method to return true when more than necessary elements of the checklist have been reached.
Again, this algorithm can break out of the inner loop when it determines that the checklist item of interest has been completed. In inner iteration 0, the method determines that it has been and breaks out of the inner loop. In inner iteration 0 the method determines that it has not been, but in inner iteration 1 it determines that it has been and breaks out of the inner loop.
In inner iteration 0, the method determines that it wasn't, but in inner iteration 1, it determines that it did and breaks out of the inner loop. In inner iteration 0, the method sees that it was and breaks out of the inner loop. In inner iteration 0, the method determines that it was, increments the count to 1, and breaks out of the inner loop.