This project/internship titled Network Device Introduction, Router Configuration and Troubleshooting Problem Solving submitted by MD.Billal Hossain Rifat, ID no. to the Department of Computer Science and Engineering, Daffodil International University has been accepted as satisfactory for the partial fulfillment of the requirements for the degree of B.Sc. Department of Computer Science and Engineering Faculty of Natural Sciences and Information Technology Påskelilje International University. Lecturer, Department of CSE Daffodil International University and co-supervised by Raja Tariqul Hasan Tusher, Sr.
Lecturer, Department of CSE Daffodil International University, Dhaka and co-supervised by Raja Tariqul Hasan Tusher, Sr. Touhid Bhuiyan, Head of CSE Department and also other faculty members and staff of CSE Department of Daffodil International University for their kind help in completing my internship. I would like to thank my entire colleague at Daffodil International University who participated in this discussion while completing the course.
My practice is all about up-to-date computer networking information to help fix any difficulties and make sure people can use it properly. Introduction of network equipment, router configuration and troubleshooting is about the networking system where I am learning hands-on by doing my internship. I am doing my internship in Computer Networks to know from top to bottom a Networking System.
The ultimate goal of my internship is to make my future career in the field of networking smooth and clear.
ORGANIZATION [Rf:1]
- Organization Profile
- Services and Market Situation
- Target Group
- SWOT Analysis [Rf:2]
- Organizational Structure [Rf:1]
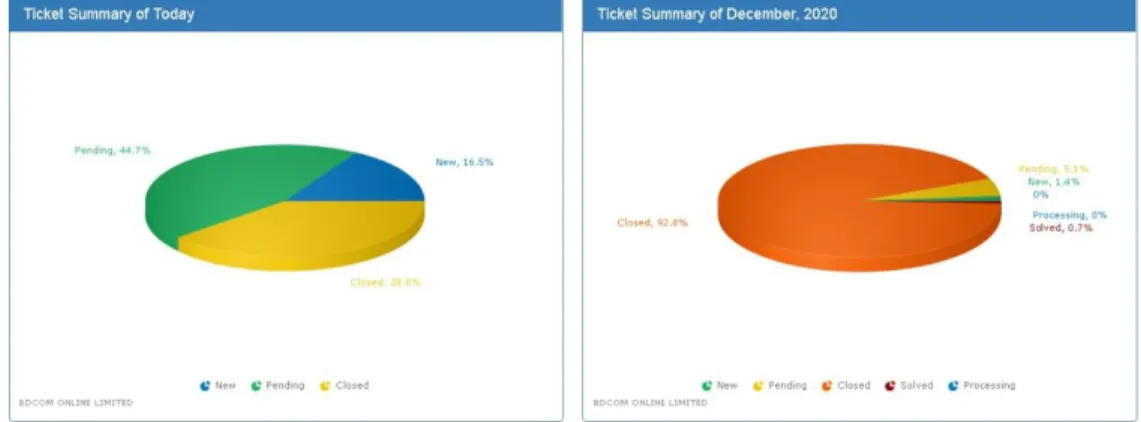
"Extensive" distribution (giving signup CDs to every mass market retailer you can find, or running ads in mass media). SWOT analysis is an important method for identifying the strengths, weaknesses, opportunities and risks of companies. There are some inherent strengths and vulnerabilities of an organization, but there are also external openings and challenges throughout its existence.
The following will introduce the internal strengths and vulnerabilities of BDCOM Online Limited, as well as external risks and opportunities. We should boost our broadband internet access and the service is the strength to succeed in this competitive environment. The company may lose its way from the market if we do not take the appropriate steps.
BDCOM is still based on service quality and stability, the two most important WAN connection requirements. Enterprise Fiber Optic and Mobile Broadband deliver enterprise-class mission-critical networking criteria for both remote and small and medium-sized businesses.
TASKS, PROJECTS AND ACTIVITIES [Rf:1]
Daily Task and Activities
Events and Activities
Project Task and Activities
Hardware devices used to connect computers, printers, fax machines, and other electronic devices to a network are called network devices.
Fiber Optic and Power Over Ethernet Fiber Optic
These devices transfer data quickly, reliably and correctly over the same or different networks. Some devices are mounted on the device, such as the NIC card or RJ45 connector, while others are part of the network, such as a router, switch, etc. Daffodil International University 11 The fiber optic means medium and thus the technology for transmitting data a glass or plastic strand or fiber, as lightweight pulses.
The second layer of glass, called the protective shield, is the closure of the heart of the optical fiber. The protective coating is covered by a plate called a buffer tube, and the coat works because of the final protective layer of the strand. Power over LAN or the author explains one of the standardized or ad-hoc schemes that integrate power with LAN cabling expertise.
It's not like the Universal Serial Bus standards, which allow long cables in addition to powering devices over data cables. Power is often carried through the same drivers, as information or power is carried within the same cable from dedicated drivers.
Media Converter
Media converters are versatile and inexpensive tools that allow fiber connections to be embedded and optimized in all types of networks. The most popular type of media converter is the unit that acts as a receiver to transform the electrical signal used by copper twisted pair (UTP) cables into light waves in fiber optic cables. Fiber optic connection is expected where the propagation distance of copper cables exceeds the distance between two network devices.
Copper-to-fiber conversion using media conversion systems allows two-port copper network equipment to be connected with fiber optic cables over long distances. Therefore, the company should be a top priority in the design, engineering, purchase and security of a business computer network. You need to look at a number of things to set up a computer network for your business.
The computer network is somewhat different from creating a home or household network in an effective business environment. To design a network based on any criteria, you can use the following eight-step architectural approach. A design must be built that allows for stability and development to achieve a network's specific goals.
When many sensors and apps compute elsewhere in a flat network, response times degrade until the network is unusable. Keeping it higher than we can use the hierarchy in the style of our ideal network. Specifically, the access layer traffic must be aggregated and transmitted to the rest of the network.

LAN and WAN
Here is a limited connection using a workstation, which is called a Local Area Network or LAN node. Select Network Configuration from the main menu and LAN Configuration from the device menu of the browser application. Prove that there are many subgroups to discuss the local port science discipline and the demilitarized port science discipline.
In the discipline of network science, the mask defines the network variation aspect of the Associate part. The subnet mask assisted by the scientific address you assign can be determined by your router mechanically. BDCOM offers Layer 2 & Layer 3 wireless networking, IP VPN Wide Area Network (WAN), Internet connectivity and VLAN (virtual LAN).
IP Address
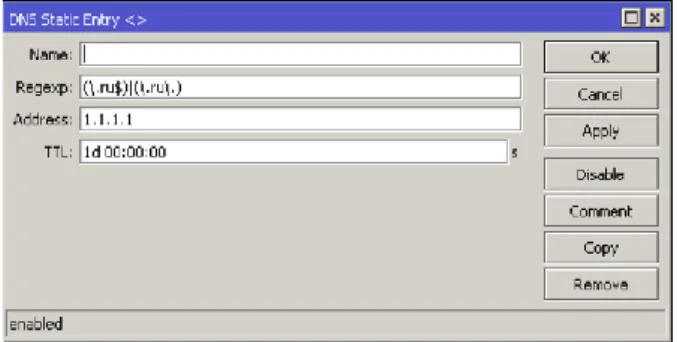
DNS and DHCP Server [Rf:5]
So now I need to find what ip and port, Bdcom normally use extension number as port and even ip address. Daffodil International University 19 It also stores the addresses of specialized equipment, such as email servers, that the world wants to find. If a sending device needs to identify the address of a device belonging to another entity, DNS can find the appropriate DNS server in an area of the Internet so that you can have IP address information for the correct target device.
One approach is to manually enter system administrator from the right address field in the network administrator's device configuration. Another approach to customizing each interface is to assign an IP address from the appropriate network address pool when it connects to a network device running a DHCP server program.
Router and Switch [Rf:3]
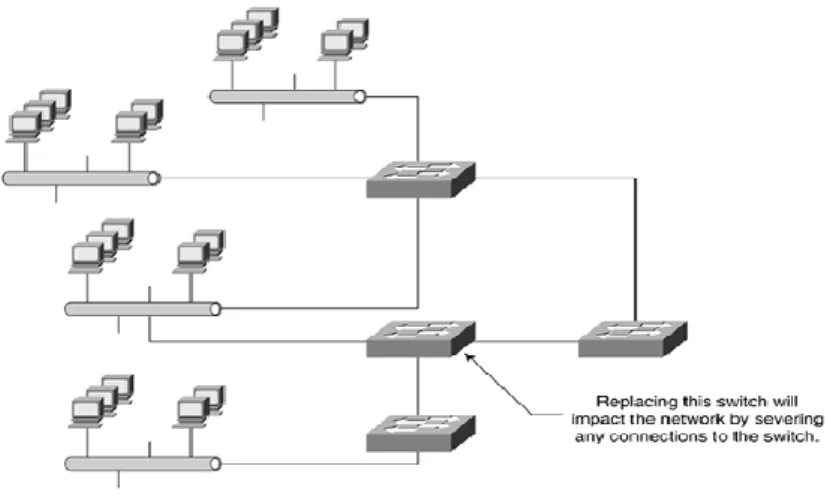
Step 1: Open winbox>tails>simple queues> press >call=tail=tail>goal deal n.b: your site ip is lan in case you want to adjust bandwidth against unique laptop or unique ip). Switches control the transfer of network data only through one or more computers for which the transmission would be intended by relaying a received network packet. The Daffodil International University 23 network address can be used to identify any networked system attached to a switch in order to allow the switch to direct a traffic flow that maximizes network protection and performance.
An Ethernet hub that essentially retransmits packets from every port except the port to which the packet is sent cannot distinguish between separate receivers and achieves lower overall network performance, making the transmission more familiar. An Ethernet switch will be used to create a second collision domain for each switch at the data link layer (Layer 2) of the model. Any port switching system will be able to forward data to other ports at any time and the transmissions will not be interrupted.[a] Newly developed parts of the network remain a broadcast domain, since the broadcast is already transmitted to all connected devices through the switch.

NOC Support System
Winbox
This should be along such lines as the ISP doesn't understand which addresses are advancing {neighborhood LAN computer network} and the world wide machine won't address our LAN. File systems define file names and the overall file size and storage space to be managed. Many file systems are in use, for example, FAT32, exFAT and NTFS are used in Windows while FAT32, exFAT, HFS+ and APFS are used for Mac.
Challenges
Competencies Earned
- Competencies Earned
- Smart Plan
- Reflections
Conclusion and Career
- Discussion and Conclusion
- Scope for Further Career
APPENDIX