This thesis entitled "Automated Border Control System Using Blockchain Technology" submitted by Shanjita Akter Prome to the Department of Software Engineering, Daffodil International University has been accepted in partial fulfillment of the requirements for the degree of Bachelor of Science in Software . Engineering and approval of its style and content. I declare that this thesis was made by me under the supervision of Mrs. I also declare that neither this project nor any part of this project has been submitted elsewhere for the award of any degree or diploma.
First of all, I am grateful to Almighty Allah for giving me the opportunity to complete the final thesis. Farzana Sadia for consistently helping me with my dissertation and research work, through her understanding, inspiration, energy and sharing of knowledge. I would like to express my sincere gratitude and appreciation to all our faculty members of the Software Engineering Department for their kind help, generous advice and support during the research.
I would also like to extend my gratitude to Delwar Alam of BugsBD for sharing his pearls of wisdom with me during this research. I also express our gratitude to all our friends, seniors, juniors, who have directly or indirectly lent their helping hand in this venture. Each passport contains various security and identity attributes to find out the owner of the passport and also bypass attempts to tamper with the passports.
The validators mine the blocks continuously, unless any irregularities are found, if a validator gets a suspicious problem, the pass is included in the blacklist.
INTRODUCTION
- Background
- Motivation of the Research
- Problem Statement
- Research Questions
- Research Objectives
- Research Scope
- Thesis Organization
The verification of work is completed by padding a nonce in the block until the value is created that has the necessary number of zero bits after the beginning of the block hash. The rule is that the longest chain that has the majority consensus in the network is the correct one, so if the attacker wants to change a block, he must have enough computing power to overcome the vote of the majority of honest nodes and thus the race problem. After that, the validators bet on the obstacles they feel will be added to the chain.
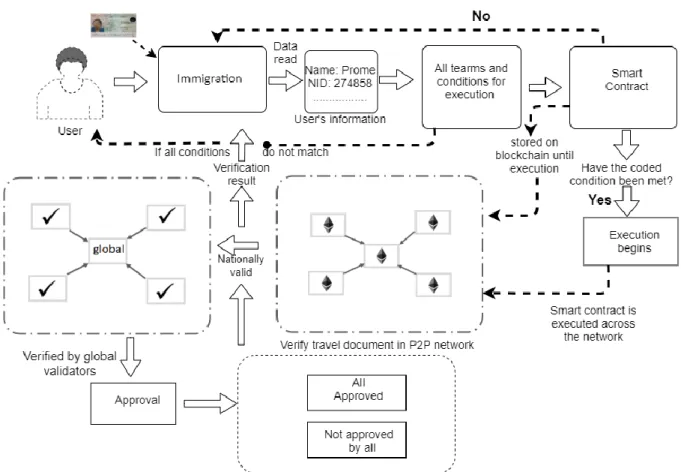
Digital agreements are responsible for going through and compiling information on the blockchain, just as they are for carrying out business purposes. You can create an instance of the contract and hail procedure to view and change data. In the current border control system, the travelers who started with one country and then went to the next country required a visa which at that time was checked by the identification scanner, physically approved the data and originated from the country.
The next process is the transfer of data to the destination country by the flight carrier. These frameworks have clearly contributed to the simplicity of air travel, especially for residents, and have helped reduce extensive screening and congestion at airports. For each transaction in the transaction list, a new balance is created using the previous balance.
Under the current framework, holders of fake passports can obtain authenticity to cross the border without much difficulty. Some countries have tried to digitalize their identity verification process despite being unable to recognize a blacklisted traveler. Another essential motivation to demand more protection is on the grounds that all entities involved allow anyone from the information exchange within the system that is not in accordance with the existing one.
Additionally, provide an algorithm depending on the proposed model and demonstrate step by step implementation procedure. The fourth chapter is about the implementation result of the proposed model and discusses the result. Finally, fifth chapter maintains the overall process, some advantages of our proposed model that have compromised the existing approach and future plan.
LITERATURE REVIEW
Blockchain Technology
Blockchain in Border Control System
Related Work
At the same time, blockchain technology is known for its security purposes, which will reduce data leaks. 10 ©Daffodil International University upgrade using blockchain technology, for example for the education sector, healthcare sector, business segment and even the government sector. Tanesh and Vidhya [38] maintain the shortcomings of the existing healthcare system and have improved the model using blockchain technology to propose a model using blockchain and smart contracts.
According to another paper, Patel and Vasu [8] discuss the existing system, state the security vulnerabilities in the existing system, the power of blockchain technology, proposed solution with Hyperledger framework, etc. Another project work [6] was done to propose an ethereum-based framework and analyze the verification system. It describes the verification process with a smart contract, and such contracts are generally written in Solidity, which is a JavaScript-like language.
The increasing number of fake passports is a major concern, which is why Kim and Kwangbaek [13] came up with an intelligent immigration control system. In the wake of audit or analysis related research work, we find point by point blockchain innovation.
RESEARCH METHODOLOGY
- Proposed Solution
- Proposed Model
- Comparison
- Implementation
Specify the origin of the information in the blockchain: The main flaw in the current system. In recent years, blockchain technology contributes to various innovation challenges and effectively provides a better solution than others. The crucial reason for using blockchain technology is that it serves a decentralized approach and complete package of information security.
Blockchain technology is thought to be one of the reasonable methods for removing and sharing passport information where the miner repeatedly verified the digital document. Our step-by-step workflow is similar to the existing one with a necessary difference that we use blockchain technology. 13 ©Daffodil International University using blockchain technology and compared with the existing one on some clear parameters.
Smart contract used to collect precise and impeccable information of the successful transaction from a decentralized system when the transaction takes place to put this data away in a new block. The blockchain properties that include an immutable record of data are stored in the digital document [34]. When a valid transaction is made and recorded on the chain [35] then a smart contract can be used to automatically trigger exchanges under specific circumstances.
The moment immigration passes, a transaction is executed in the distributed ledger while validators are constantly mining the data. In the event that changes occur, the proposed framework at that time will require updating as soon as time permits and this will be noticeable to others. In the case of the validators confirmed locally, while different nations included in the country list that has been saved in the transaction history.
Smart contract refers to rechecking the logic. If this matches, the border gate will be opened. Unlike the existing contracts available, a smart contract is faster as it additionally reduces the ideal possibility of executing and transmitting the traveler's information. The promotion regarding the use of blockchain in border control is a reality in the coming future as scientists explore different parts of blockchain in border control frameworks.
Using blockchain technology provide information security where the incumbent is not verified and commits information breaches. In use, we use the web3 javascript library to connect to the Ethereum blockchain.
RESULT AND DISCUSSION
Build a Dapp
Mining Ethereum Blockchain using POS
SWOT Analysis
23 ©Daffodil International University but unable to identify criminal activities or fake travel documents which are authenticated without problems. In the proposed approach, if changes occur, the distributed system will be updated quickly and notify the other validators, which is a major strength of the approach. Moreover, each and every transaction of travelers contained in the distributed system, which helps to locate travelers instantly.
Be that as it may, in the event that we give space to advanced modules, at that point, it will be reduced. In the event that a traveler contains dual visas and has committed their crimes against one identification, at that point it would be slightly difficult to track the explorer's crime. In the event that we limit the poor purpose of these proposed innovations, at that point, it will be a suitable approach to recognize the traveler's criminal activities.
Moreover in the future, if it will be explored all over the world, then it would be a bigger innovation of blockchain technology. The proposed model is not implemented by another organization in the whole of Bangladesh, so there is currently no threat. In this chapter we support the strengths, weaknesses, opportunities and threats of the proposed solution.
We need to improve our model to overcome the following weakness and explore blockchain technology properly.
CONCLUSION AND RECOMMENDATION
Findings and Conclusion
34;Passport, Visa and Immigration Management using Blockchain RD Annual International Conference on Advanced Computing and Communications (ADCOM). 34;Towards a Blockchain-Based Digital Identity Verification, Data Authentication and Data Sharing System."
34;Intelligent Immigration Control System Using Passport Recognition and Face Verification." International Symposium on Neural Networks. 34;An Intelligent Passport Recognition System Using Extended RBF Network." International Conference on Computer and Information Science. 34;A decentralized sharing application running a smart contract on the ethereum blockchain.” Proceedings of the 6th International Conference on the Internet of Things.
34;Blockchain Technology in Healthcare: The Revolution Starts Here IEEE 18th International Conference on e-Health Networking, Applications and Services (Healthcom). 34; The Random Neural Network with a BlockChain Configuration in Digital Documentation." International Symposium on Computer and Information Sciences.




