Thesis entitled "Key Distribution Technique with Strong Authentication" submitted by Saba Tasnim, ID no. in the Department of Computer Science and Engineering, Daffodil International University, has been accepted as satisfactory in partial fulfillment of the requirements for the degree of M.Sc. . Department of Computer Science and Engineering Faculty of Science and Information Technology Daffodil International University. Syed Akhter Hossain, Professor and Head of CSE Department for his diligent help in completing my proposal and other workers and staff of CSE Department of Daffodil International University.
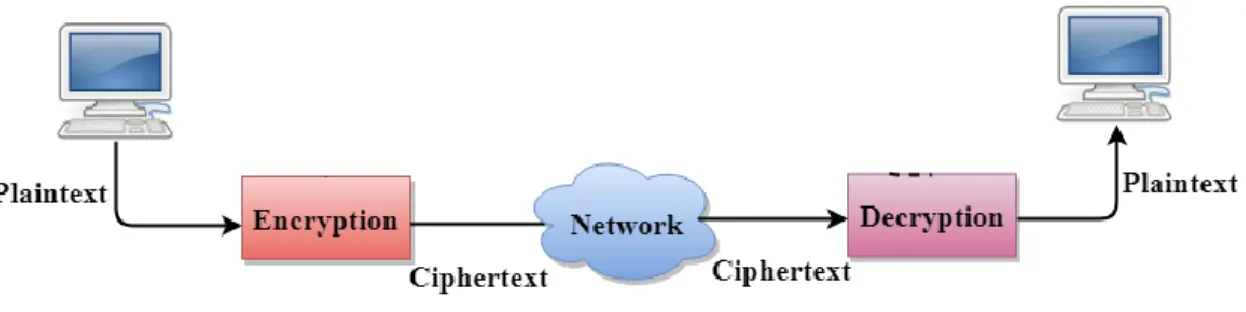
To do this, infallible cryptographic encryption and decryption systems are used to transmit messages.
INTRODUCTION
- Introduction
- Relational of the Study
- Research Questions
- How to provide authentication for electronic message over the open network without allowing access to an attacker?
- What is the procedure of the system?
- How to perform strong authenticate encryption-decryption?
- Expected Output
- Report Layout
At present, very delicate information is transmitted every day over the open system or web or other correspondence channel [2]. Our main point of this postulation is to guarantee solid validation of electronic information or message about the open key appropriation without allowing access to an attacker. The main part is the Introduction, which examines the inspiration and method of reasoning of the examination.
This section consists of six areas in which they are presented, presents the proposed framework, key circulation encryption decryption procedure and graphs of the proposed framework, computation of the proposed framework, bit by bit flowchart of the proposed framework and synopsis.
BACKGROUND
- Preliminaries
- Related Works
- Comparative Analysis and Summary
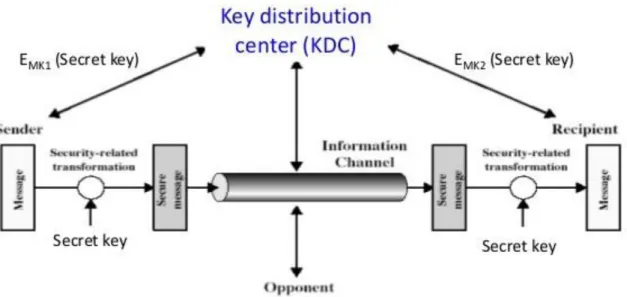
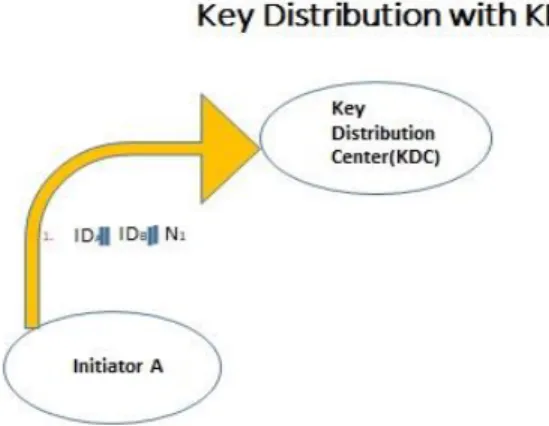
- Key Distribution Center (KDC)
- Symmetric Key Encryption with KDC
- Strong Authentication Processes by KDC
- Secret key Generation
- Secret Key Cryptography
- Challenges
Affodil International University 6 Choir text: The transformed message or data that cannot be directly understood by man or machine. Decryption Algorithm: It is a complex mathematical process that takes Cipher Text Cipher text and decryption key as input and gives Plaintext as output. Key for decryption: The key that is entered along with the plaintext into the encryption algorithm to determine the ciphertext.
Ciphertext: A transformed message or data that cannot be directly understood by a human or machine. Decryption Algorithm: It is a complex mathematical process that takes ciphertext and a decryption key as input and gives plaintext as output. Decryption Key: A key that is fed to the decryption algorithm along with the ciphertext to determine the plaintext.
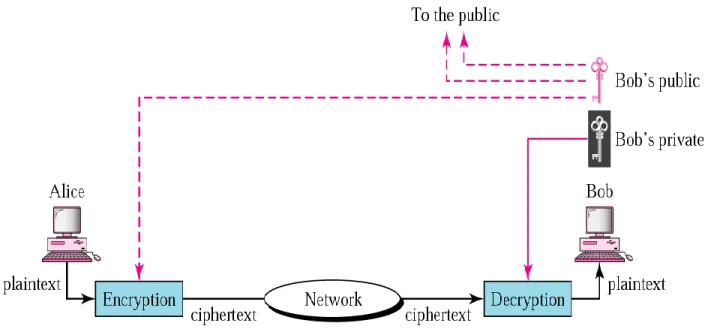
Key: A key is a value or some critical piece of information that is fed to an algorithm to convert plaintext to ciphertext and decrypt plaintext from ciphertext. Daffodil International University 7 Encryption: Encryption is a technique of converting plain text into cipher text which is unreadable by human and machine without knowledge of the algorithm and decryption key. Decryption: the process of changing encrypted text into plain text with prior knowledge of the algorithms or keys used.
Decryption: Decryption is the technique of converting code text into plain text with prior knowledge of the algorithms or keys used. Cryptanalysis: Cryptanalysis is the investigation of the rule and procedures of recovering plaintext from ciphertext without knowing the key calculation or used. This normal key is used for both plaintext encryption and ciphertext decoding.
Cipher text: the transformed information that cannot be directly understood by human or machine without knowing the algorithm or secret used.
RESEARCH METHODOLOGY
- Research Subject and Instruction
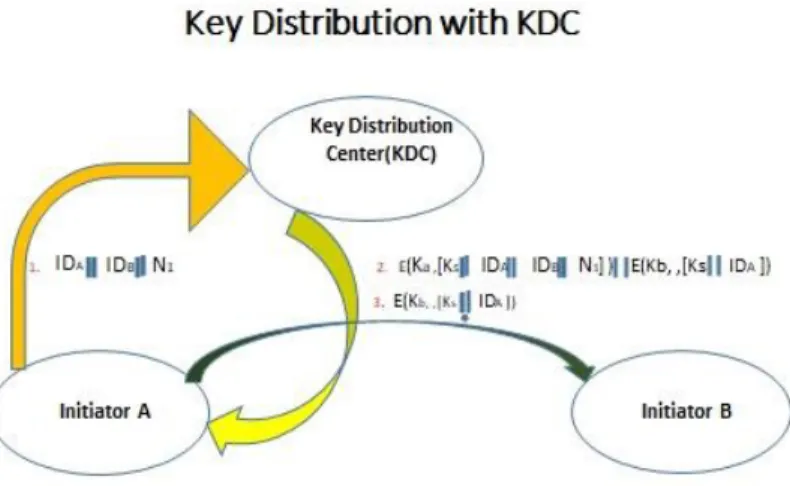
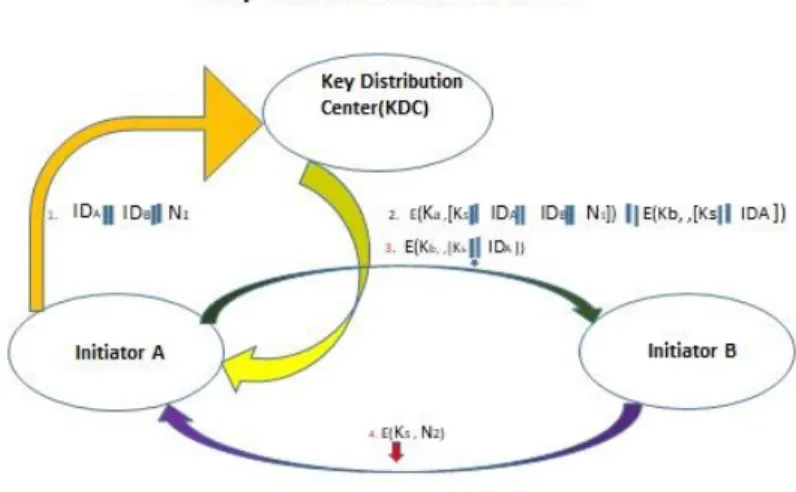
- Secret Key Distribution Analysis
- Strong Authentication Analysis Technique in Key Distribution 3.2 Algorithms of the Proposed System or Data Utilization System
- Statistical Analysis
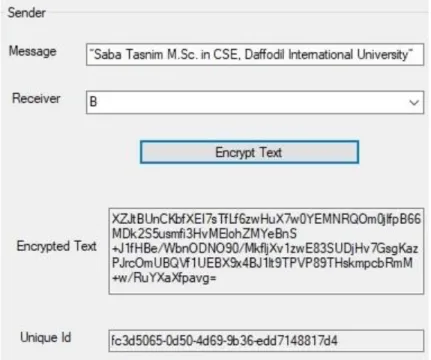
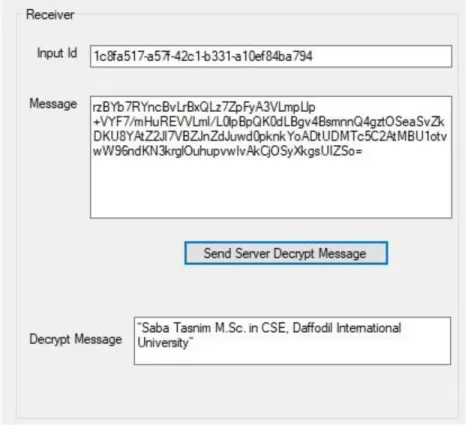
- issues a request to the KDC for a session key to ensure a logical connection with B
- Using the recently printed session key for encryption, B sends a nonce, N2, to A
- Implementation Requirements
- Experimental Setup
- Experimental Results and Analysis
- Discussion
Specifically, the enemy can start completely new "instances" of any of the social events, which shows the limitation of passing administrators to participate in multiple gatherings at the same time. In this part, a presentation of the proposed framework, process depiction, Secret key circulation exam, solid verification investigation strategy in Key Distribution, maps, encryption calculation and detangling calculation of the proposed arrangement of Key appropriation and validation is planned and illustrated. The fundamental point of our updated framework is to guarantee key transfer with solid validation for the safety of message transfer.
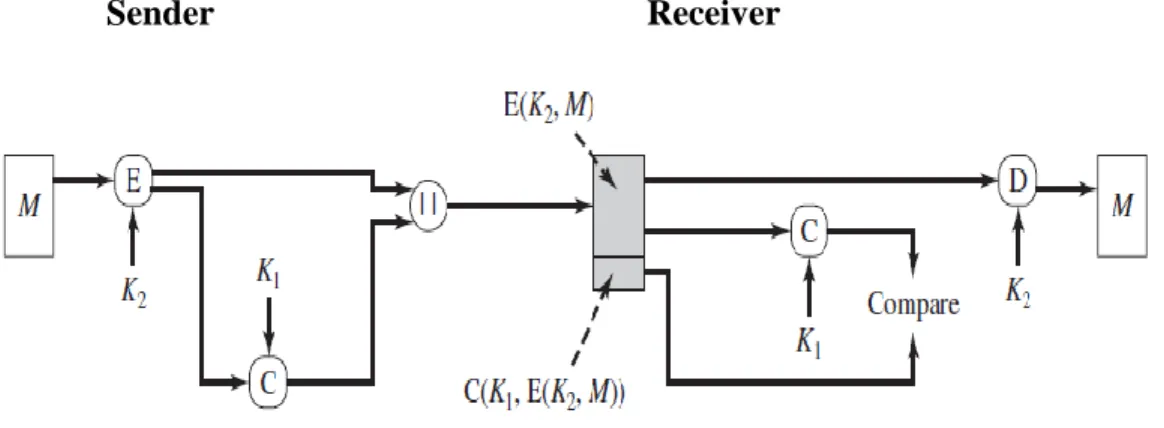
Eventually, the frame scrambles the final ciphertext with the receiver's public key, which must be decrypted with the receiver's private key; yet just collects is realized his private key that builds up second layer classification of the exchange. Integrity: The framework produces a Message Authentication Code (MAC) by encoding the ciphertext with a shared mystery key for trustworthiness of the ciphertext just like the message. Eventually, the framework encodes the last encoded data with the receiver's public key and sends to the target.
Authentication: At the sender's end, the framework encrypts the message with the sender's public key and re-encrypts the message multiple times with shared secret keys, finally encrypts with the collector's public key and sends to the destination. Thus, the sender and the collector could not deny the correspondence because the obtained data is decoded from the beginning with the recipient's private key, which is related to his public key, which is used to encrypt the data on the sender's side, which finally reconstructs the message with the sender's public key as appropriate associated with the sender's private key used to encrypt the message. Since the private key is known only to the owner; as a result, it builds confirmation for both the sender and the receiver of the sent message.
Non-repudiation: The frame encrypts the message with the sender's public key and again obfuscates the message with shared mystery keys, finally encrypts with the collector's public key and sends to the target. As a result, the sender and the collector could not give up the correspondence, since the received data is initially decoded with the receiver's private key, which is associated with his public key, which is used to encode the data in the sender's side, finally reconstructing the message with the sender's public key as well , which is associated with the sender's private key used to scramble the message. Since the private key is precisely known to the holder and consequently it sets up non-repudiation for both the recipient and the sender of the disclosure message.
In this part, the results of the experiments are broken down and the data and consequences of the created framework are quickly displayed.
IMPACT SOCIETY ENVIRONMENT AND SUSTAINABILITY
- Impaction on Society
- Impact On Environment
- Ethical Aspects On Message Authentication with KDC
- Sustainability Plan for Key Distribution with Message Authentication and Confidentiality Checking
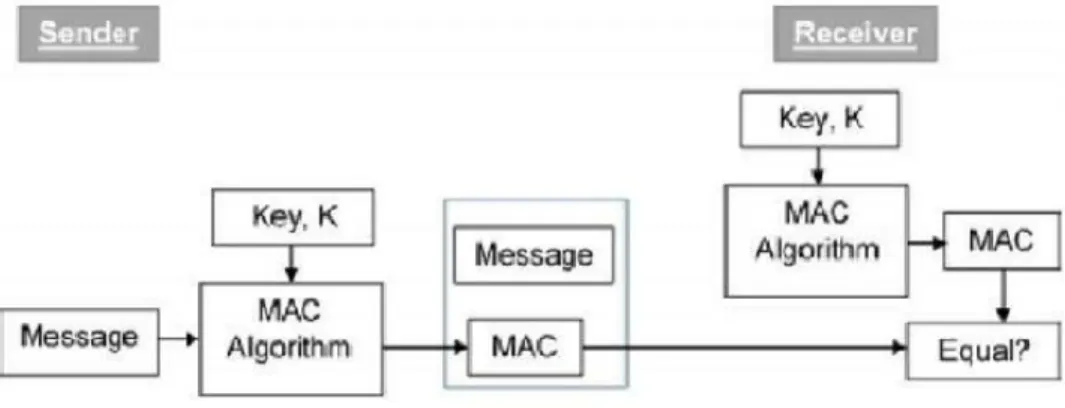
As a result, the requirement for secure collection of the board and secure collection of key circulation in mandatory conditions increases incrementally and is not yet adequately settled – neither in norms nor in writing and not as a reasonable implementation. It is demonstrated that both sender confirmation and secure collection of the board mainly address secrecy during transit, but no further validation or secure key trading or secure collection of the drivers are considered. Basically, a MAC is an encrypted checksum produced on the fundamental message sent with a message to guarantee message authentication.
The sender uses an overtly known MAC calculation, inputs the message and the secret key K, and produces a MAC value. Here we accept that the message will be sent for free, because we are concerned about giving confirmation of the message, and not about privacy. If privacy is required, at that point the message needs encryption.
Upon receiving the message and the MAC, the receiver enters the received message and the shared secret key K into the MAC algorithm and recalculates the MAC value. The receiver now checks the equality of the freshly calculated MAC with the MAC received from the sender. If they match, then the recipient accepts the message and verifies that the message was sent by the intended sender.
In the event that the processed MAC does not coordinate the MAC sent by the sender, the beneficiary cannot decide whether the message has been modified or the premise has been distorted. The recipient then confirmed that the message was not modified and came from the indicated source.
SUMMARY, CONCLUSION, RECOMMENDATION AND IMPLICATION FOR FUTURE RESEARCH
- Summary of the Study
- Conclusions
- Recommendations
- Implication for Further Study
Daffodil International University 36 MAC that concatenates with the ciphertexts and re-encrypts them with the shared secret key K1, which produces a new ciphertext that is re-encrypted with the beneficiary's public key PUb to deliver the final ciphertext to be sent to the quartermaster. beneficiary. In the not so tempting end, restore the message, the beneficiary from the beginning decrypts the obtained data with his private key PRb and decodes again with the shared secret key Ks to and the MAC of the ciphertext, and some time later only deciphers the MAC so that the second ciphertext' and distinguishing of the new ciphertext' and they got the ciphertext, which provides the approval of the ciphertext similar to the confirmation of the message; in case the ciphertexts are found to be the same, until then it interprets the ciphertext with the shared puzzle key K1 and retranslates with the sender's public key PUa and recovers the message; discard regardless. In the current age of electronic correspondence, the security of electronic message exchange is a key issue and a major concern and is absolutely required.
The security of the exchange of electronic messages rests on key evaluations of the cryptosystem and various cryptographic procedures. In the diploma thesis, we proposed and developed a system for the secure transmission of electronic messages. The thesis can be of great help in further research and projects related to cryptography, especially for those who want to research the security of electronic transactions.
Stallings, načela in praksa kriptografije in omrežne varnosti, 5. izdaja, Prentice Hall Press, Upper Saddle River, NJ, ZDA, 2010. Lutfar Rahman, »Eliptična krivulja Cryptographic Technique Implementation of Textmessage (SMS) Transaction in Mobile Phone«, v Proceedings of the Annual Conference, Central Auditorium, Bangladesh University of Engineering and Technology (BUET), Daka, Bangladeš, stran: 70, maj. Lutfar Rahman, "Improved Message Authentication and Confidentiality Checking", Journal of Science and Applications, Bangladesh Atomic Energy Commission, Dhaka, Bangladesh, Vol.
Lutfar Rahman, “An Verbeterd Session-key Distribution Technique for the Key Distribution Center (KDC)”, In de Proceedings of the Annual Conference, Central Auditorium, Bangladesh University of Engineering and Technology (BUET), Dhaka, Bangladesh, Pagina: 73, Kunnen. Lutfar Rahman, “An Approach for Strong Message Authentication and Confidentiality Checking”, de 22e Bangladesh Science Conference, georganiseerd door Bangladesh Association for Advancement of Science (BAAS) en Bangladesh Council of Scientific and Industrial Research (BCSIR), Dhaka, Bangladesh op 27-29 september 2012.
APPENDICES
If the confirmed customer meets each proposed condition, the KDC can issue an admission ticket. In most (but not all) cases, the KDC provides a key to all the various social events. The server can acknowledge the submitted ticket and grant access to the client that submitted it.
Plagiarism Report