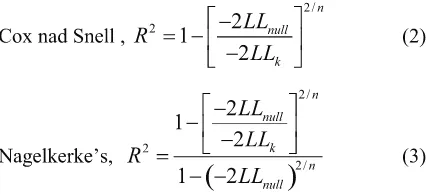Faizal, M.A.2, Shahrin, S1., Asrul, H.Y. 3, Fairuz, M.I.O. 2, and Robbie, Y2. 1Professor Dr. 2Faculty Information Technology and Communication
University Technical Malaysia, Melaka
3Faculty Information System and Technology University Multimedia Melaka
Corresponding author’s e-mail: [email protected],
ABSTRACT: Over the last decade, networks have grown in both size and importance especially in exchange data and carry out transactions. They have also become the main mean to attack a host. The popularity of intrusion tools and scripts are the main contributors of the attacks inside the network. Gathering valuable information from vulnerable machine is a irst step for an attacker to launch an attack against the vulnerable machine. There are numerous techniques to get this information such as sweeping, scanning, probing and so on. These information gathering techniques can be divided into 2 categories which are fast attack and slow attack. Fast attack can be deined as an attack that uses a large amount of packets or connections within a short period of a few seconds. Meanwhile the slow attack can be deined as an attack which takes a much longer time, usually taking in minutes or a few hours to complete. In order to detect these attacks, introducing intrusion detection system (IDS) inside the network is necessary. An IDS has the capabilities to analyze the network trafic and recognize incoming and on-going intrusion. This system can be classiied into 2 types, namely, signature-based IDS and anomaly based IDS. Before developing the intrusion detection system, selecting necessary features are important. Selecting unnecessary features may cause computational issues and decrease the accuracy of detection. Furthermore, current research more concentrates more on the technique of detection rather than feature selection. They just used the features without mentioning the inluence of the feature inside the system itself. Therefore this research will reveal the inluence of the features in predicting the result of the detection. Besides that, we also introduce a set of minimum features that can be used to detect a fast attack. The result shows that the feature selected in the research has a strong potential to detect the fast attack and signiicantly reduce the false alarm generated by the intrusion detection system.
1.0
Introduction
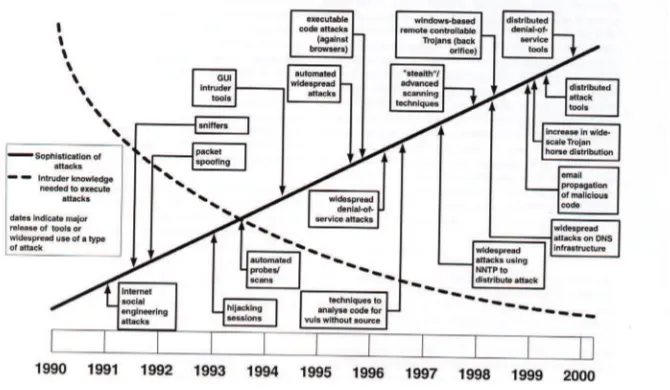
In recent years, the Internet and networks as a whole has seen a great increase in its role in our society especially in government and business sectors. During these times, we also witness more and more sophisticated attack launched by intruders, which of course are motivated by inancial and political objectives. The types of attacks are generated using tools and exploit scripts which are freely available on the internet and widely used by novice malicious users to launch an attack inside the network. Mc Hugh also provide further evidence by stating that “anyone can attack Internet site using readily made available intrusion tools and exploit script that capitalize on widely known vulnerabilities (Mc Hugh et al, 2000). Therefore the increase in the number of the exploit tools may have inluenced the number of novice attackers inside the internet as shown in Figure 1.
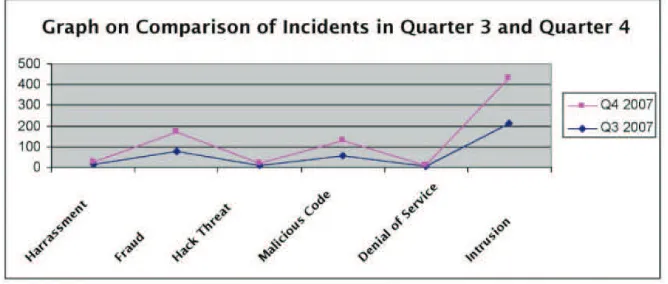
As a result it may give a signiicant impact to the number of reported incidence due to security breaches generated by Cybersecurity, Malaysia (CyberSecurity, 2007) as depicted in Figure 2. Therefore ensuring security in term of conidentially, integrity and availability is necessary to protect the network infrastructure (Mark Merkov and Jim Breithaupt, 2006).
Figure 2: Incident Statistic on Quarter 3 and Quarter 4 in 2007
The introduction of intrusion detection systems (IDS) in a network can be used to counter this problem by placing it inside the network to help users to look for known and potential threats in the network trafic and/or audit data recorded by the host (Giacinto et al, 2003). An IDS can be classiied into two general types which are signature based system and anomaly based system (Wang et al, 2006). Signature based system is a system which contains a number of attack description or signatures that are matched against a stream of audit data looking for evidence of modelled attack (Wang et al, 2006). The audit data can be gathered from network trafic or an application log. Meanwhile, the anomaly based system identiies the intrusion by identifying trafic or application which is presumed to be different from normal activity on the network or host (Wenke Lee, 1999). Both of these approaches have their own disadvantages. False alarms generated by both systems are a major concern and is identiied as a key issue and the cause of delay of further implementation of reactive intrusion detection system (Karl Levitt, 2002).
Before developing an intrusion detection system, understanding the axonomy of an attack is important. An attack can be disserted into 5 phases which are reconnaissance, scanning, gaining access and covering track (Certiied Ethical Hacker, 2006). The irst two phases are the initial stages, whereby the attacker will try to gain information on the potential vulnerable machine. These phases can be classiied into two categories which are fast attack and slow attack.
to reduce the possibilities of gaining access, maintaining access and covering tracks. Therefore this paper focuses the research conducted on detecting fast attacks to protect the computer or network at an early stage. Before detecting a fast attack, selecting useful features may help in identifying them is also paramount to help the intrusion detection process to make better decision in identifying the attacker. Unfortunately, many attackers are knowledgeable and capable of altering the detail of many attacks to avoid the detection from such as system (Caulkin. Lee and Wang,. 2005). As a result, the selection of useful feature is necessary to detect and identify the various threats that exist inside the network or application.
Before selecting a feature, understanding the relationship between the feature and the attack type is also important. Identifying the signiicant contribution of the feature in detecting the attack is necessary to avoid selecting useless features. Furthermore, iltering huge amount of network trafic is very tedious especially the complexity of the protocols involved such as UDP and TCP and the number of incidents can only be studied if deep knowledge of the protocol detail is acquired (Mellia, Meo and Muscariello, 2006). Therefore it is critical to overcome the problem of selecting the important features of the network trafic to identify an attack, especially fast attack.
The principal goal of this paper is to present a minimum feature set that can be used to detect a fast attack and the inluence of the feature to the model in detecting the fast attack. Understanding the inluence of the feature is necessary to provide better selection of the features as one of the factors which may increase the accuracy of the detection for an intrusion detection system. Additionally, the researcher and system developer of the intrusion detection system can beneit from the results provided in selecting the useful features for the intrusion detection system.
2.0
Literature Review
may help to decrease the computational issues such as time, memory and CPU time and increase the accuracy of detection.
To the best of our knowledge, there is no comprehensive classiication of features that intrusion detection system might use for detecting network based attacks especially fast attacks. Different researchers use different names for the same subset of feature while others used the same name but different type (Vinot and Ghorbani, 2006). Furthermore, understanding the relation as well as the inluence of the features in detecting the fast attack is also necessary to avoid any redundant features selected for the intrusion detection system. Therefore this research will focus on the probing and DoS attack which can be categorized as a fast attack. This research will also expose on how the feature inluence the detection of the attacker especially fast attacks.
KDDCUP99 has introduced a set of features that can be used to detect the intrusion (KDDCUP99, 1999). There are some researchers who are concentrated on feature classiication by using a set of features that have been constructed by KDDCUP99 (Kayacik et al, 2005; Sung and Mukkamala, 2005). Special techniques have been used in classifying the features and they produced dissimilar results. Table 1 shows the labeling of features used by KDDCUP99.
Table 1: Network Data Feature Labels
Diot has combined some ield inside IP header and TCP header such as source IP, destination IP and source port (Lakhina et al, 2005). Payload also has been considered as a parameter that can be used to recognized the network anomalies (Moore and Zuev 2005; Moore and Zuev, 2005). By inspecting the payload, the hidden code that is suspicious can be identiied and comparison can be made to a normal packet. Therefore it is a good opportunity to investigate the payload of the trafic to recognize the intruder (Vandemant and Pras, 2003). Although examining the payload is a better approach, it is still not widely used due to some restrictions such as security, privacy and legal issue (Moore and Papagiannaki, 2005). From the previous research, non of the researchers mention the usefulness of the features in identifying the attack and how the features can contribute to the detection of the attackers. Therefore this research will investigate the inluence and usefulness of the features in identifying the attacker.
3.0
Feature Classiication
For intrusion to occur there must be both an overt act by the attacker and a manifestation from the victims. Therefore creating a taxonomy that organizes intrusion from both perspectives; attacker perspective and victim perspective, may help to detect fast attack activities (Mc Hugh et al. 2000). Therefore, the detection process introduced in this research was motivated by the attacker perspective and victims perspective (Shahrin et al. 2007). Understanding the detection process of detecting a fast attack is important since it can inluence the selection of the features. Therefore, in order to achieve a good detection ratio for fast attack, feature classiications have been done as follows:
3.1 Basic Feature
Mahoney and Chan, 2001, identiies this category under the name of Packet Header Features. Basic Feature can be derived from packet header without inspecting the payload. The possible candidates for this feature category includes timestamp, source port, source IP, destination port, destination IP, lag, to name a few.
3.2 Derived Feature
3.2.1 Time based trafic feature
Time based trafic feature are designed to include all the derived feature computed with respect to the past t seconds (where t is the size of the time windows interval, for example one second or one minute) (Wenke Lee, 1999).
3.2.2 Connection based trafic feature
Connection based trafic feature, which is also known as host-based trafic feature. It will capture similar characteristic of the connection records in the last k connection (where k is the number of connection) (Wenke Lee, 1999).
Based on this classiication, basic features can be used to detect an ongoing attack that uses only a single connection such as DoS. Meanwhile the derived feature can be used to detect multiple attacks launched by the attacker such as DDoS and worms. Without basic feature, derived feature cannot be created. Derived features are dependent on the basic feature. Unfortunately, KDDCUP99 (KDDCUP99, 1999) does not mention some of the important basic features which is necessary to create derived feature. This research will use time based feature which has capabilities to identify the fast attack category. Finally, for detecting the slow attack category, the connection based trafic features are predominantly used. Table 2 describe the features involve in this research.
4.0
Methodology and Analysis
We grounded our exploration of the problem space using a set of real trafic data which was captured from one of the local university. The real trafic was captured for one day only and the total number of connection recorded was 22,616,725 connections. By using the real trafic and not simulation trafic we can see the actual behavior of the attacker in launching the fast attack against the network. The real trafic was captured for one day because we made an assumption that normally the attacker will not do the damage to the system for more that one day. If the attacker stays inside the system for a long period of time, the chances of being detected by the administrator are high.
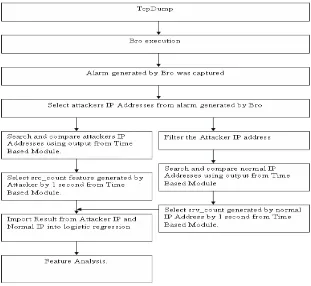
Due to huge amounts of network trafic, it is dificult to distinguish the normal and abnormal behavior of network trafic (Jalili et al, 2005). Therefore we used Snort to distinguish the abnormal behavior of the network trafic (Caulkins et al, 2006). After distinguishing the normal trafic and abnormal trafic, logistic regression model was used to validate the result. Figure 3 show the methodology used for the research. Logistic regression will be used to reveal the inluence of the src_count and srv_count feature to recognize the fast attack activity.
Figure 3: Methodology for Fast Attack Detection
5.0
Feature Analysis
As mentioned earlier, the intrusion occurs from the attacker perspective and the victims’ perspective. The feature that has been constructed also was based on both of the perspectives. KDDCUP99 (KDDCUP99, 1999) has constructed the feature and most of the features were concentrated on the victims perspective. For the attackers perspective, we generated two extra features which are src_ count and srv_count. Bro ( V.Paxson, 1999) has been using this feature but does not mention the how signiicant and strong the relation of the feature in predicting the result of the detection. In this research, we will explore and discuss how the feature can contributed to the model in predicting the result especially in detecting the fast attack.
5.1 Feature Analysis of the Victim Perspective
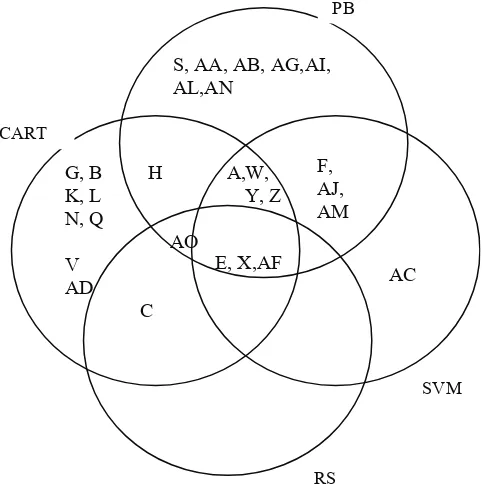
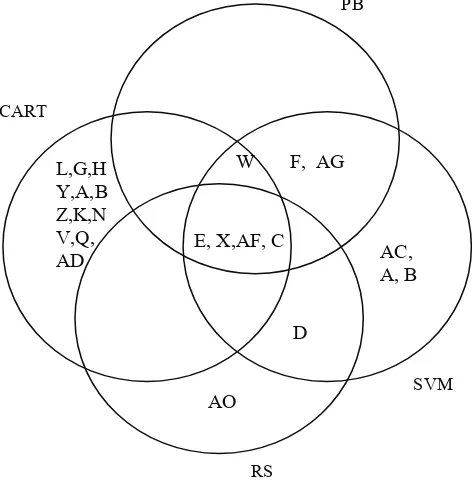
manage to introduce 17 features in detecting fast attack. Meanwhile Sung and Mukkamala (2003) used PBRM and SVDFRM technique to classify the set of feature. Using PBRM, the researchers were able to classify 8 features for probe and 20 features for DoS which can be categorized as a fast attack. Meanwhile using SVDFRM, the researchers manage to classify 11 features for both of the attacks. Anazida (2006) used rough set (RB) theory to classify the features and manage to classify only 6 features to detect the fast attack (Anazida et al, 2006). Although, they manage to classify 6 features, they fail to mention the featured used to detect the attack for each class of the attack. All the experiment explained earlier was done using the KDDCUP99 data and features introduced by KDDCUP99. By comparing the previous result from the previous research, we manage to identify the most useful features to detect the fast attack. Figure 4 and 5, illustrate the comparison between result obtained from previous research for DoS and Probing attack respectively. The description of the feature represent inside Figure 4 and 5 is given in Table 1.
W,
packet sent by windows environment which may effect the result of detection
Figure 5 illustrates the features that are useful to detect the probe activities. Features E, X, AF and C are important features as it had constantly been selected by all four approaches. Feature W can also be considered useful since it had been selected by 3 different approaches. As a conclusion, in our research we only select features C, X, AF, A and W for detecting the fast attack. All of the features selected for use is useful in our victims perspectives.
5.2 Feature Analysis of the Attacker Perspective
For src_count and srv_count, we asses the contribution of the feature using likelihood Ratio Test in equation (1) inside logistic regression. The likelihood ratio test is used by comparing the model with and without a particular predictor. If the value of the likelihood ratio model without the predictor decrease when the predictor is included inside the model, it means that adding the predictor give a signiicant contribution to the model in predicting the outcome.
(Cox and Snell, 1989) and Nagelkerke’s R²N in equation (3) can also be used to indicate whether the feature gives a good prediction on the result or outcome variable. Nagelkerke’s is the amendment of the Cox and Snell because the lack of Cox and Snell to reach its theoretical maximum of 1.
Now we will discuss the result based on the statistical value from likelihood ratio, Cox and Snell and Nigelkerke’s. This discussion will concentrate on src_count and srv_count respectively.
i) Assessing the Inluence of the Src_count Feature
This feature is used for detecting fast attack launched by single host to multiple hosts. By selecting this feature, it may help to detect the attacker at the initial stages because host scanning is one of the tools that can be used to launch reconnaissance and scanning activity. Furthermore, there is a question on how the feature can inluence the result of the detection of the attacker. This can be validated using statistical value from likelihood ratio test, Cox and Snell and Nigelkerke’s respectively. Table 3 shows the value of the likelihood ratio statistic after the feature include inside the model. Meanwhile, Table 4 show the chi-square (x²) value of the new model. Therefore by referring to (1), the value of the baseline model ( without the predictor) can be computed. When only the constant was included, -2LL = 509.721. but when src_count had been included this value has been reduced to 85.211. This reduction means that the features has a signiicant inluence at predicting the outcome(attack).
Table 3 : Model Summary
-2 Log likelihood Cox & Snell R Square Nagelkerke R Square
85.211 .328 .869
Table 4: Model Coeficient
Chi-square df Sig.
424.510 1 .000
Beside the likelihood ratio test and Nigelkerke’s test, chi-square test also can be used to verify whether the feature give a signiicant contribution to the model or not. This can be done by generating hypothesis which are Ho, feature does not effect the model prediction and H1, feature effect the model prediction. Table 4 show the chi-square value is 424.510 and the value is signiicant at a 0.05 and 0.01 level. Therefore the H1 hypothesis has been accepted. As a conclusion, the src_count gives a effect to the model in predicting the outcome.
ii) Assessing the Inluence of Srv_count Feature
Srv_count had also been selected as one of the features in this research. This feature also gives a signiicant inluence to the research and the validation is made using the same test with the previous feature. Table 5 shows the value of the likelihood ratio statistic after the features were included inside the model. Meanwhile, Table 6 show the chi-square (x²) value of the new model. When only the constant was included, the value of the baseline model is ,-2LL = , 528.700 but when src_count was included inside the model and this value has been reduce to 133.213. This reduction means that the feature has a signiicant inluence at predicting the outcome (attack).
Table 5 : Model Summary
-2 Log likelihood Cox & Snell R Square Nagelkerke R Square
133.213 .298 .791
Table 5 also shows the Nigelkerke’s value for the new model which is 0.791. The Nigelkerke’s value is very close to one which means that the feature selected in this research gives good inluence to the model in predicting the outcome.
Table 6: Model Coeficient
Chi-square df Sig.
395.487 1 .000
chi-square value is 395.487 and the value is signiicant at a 0.05 and 0.01 level. Therefore the H1 hypothesis has been accepted. As a conclusion, the srv_count gives an effect to the model in predicting the outcome.
6.0
Result
This section evaluates the contributions of the features in detecting fast attack in terms of its accuracy. We used comparison and observation method as our mechanism to verify the result. We will explain the result based on the result produced by logistic regression.
6.1 Classiication result from logistic regression
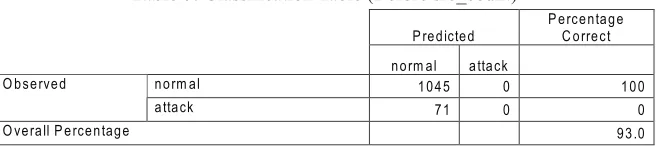
Firstly, the result was based on the accuracy of the detection before and after the features were included inside the model. Table 7 shows the result of the detection for the model when only the constant was inside the model without adding the feature for src_count.
Table 7: Classiication Table (Before src_count)
Table 7, shows that the model manage to predict 93% correct in classifying the normal but the false negative was also very high which is 7%. Unfortunately the model do not have capabilities to detecting the attack because using constant, the model assume most of the data are normal. After the src_count feature was included inside the model, the detection accuracy was high and reduces the false positive as depicted in Table 8. The model has capabilities to predict 96.8% correct in classifying the attack and only 3.2% misclassiied it. The model has better prediction and has the capabilities to distinguish the difference between the attack and normal trafic.
Srv_count also has a signiicant contribution to the detection accuracy of the fast attack. Table 9 shows the classiication table before the srv_count features was included inside the model.
Table 9: Classiication Table (Before srv_count)
The result shows that the model has the capabilities to predict 93.6% correct for the normal behaviors of the network trafic. Unfortunately, the model does not have capabilities to predict the attack detection. But after the srv_count features was added inside the model, the prediction become more accurate. Table 10 shows the result of the model in classifying between the attack and normal network trafic.
Table 10 : Classiication Table (After srv_count)
The result as depicted in Table 10 shows that the model manage to classify 96.5 % of the attack and only 3.5% false positives. Overall percentage show that the model in capable to predict 98.4% correct to distinguish between the normal and attack trafic.
From the comparison result, the classiication between the normal and attack trafic can be decided when both of the features are include inside the model. Therefore, it is proven that both of the features give a signiicant contribution in classifying between the attack and normal network trafic.
7.0
Conclusion and Future Work
detection. Nowadays, most of the researchers only use the selected features in their research without mentioning the reason of selecting the feature in predicting the intrusion activity. The previous researchers also did not mention the inluence of the selected features to the system developed in their research. Understanding the relation and inluence of the feature before using them may help to reduce the possibilities of selecting unnecessary feature which may give an impact in detecting the intrusion activity especially fast attack since fast attack is an initial stage for the attacker to begin their attack inside the network. Therefore identifying the attacker earlier may help the administrator to overcome further damage cause by the attacker. In this research, we manage to reveal the inluence of the feature in predicting the detection of the intrusion especially fast attack using statistical approach. In additional, the researcher who concentrates on developing the intrusion detection system can beneit from the result provide as they can consider these features when addressing features selection issues inside the research. Besides validating the inluence of the features, we also manage to introduce the minimum feature that can be used to detect the fast attack. Although the rough set theory was able to produce minimum feature, but the features selected did not state the basic features which is important to compute derive features. Furthermore, the research also provides a general detection and did not focus on the fast attack detection.
For our future work, we would like to develop a system using the proposed features and test the system in a real time environment. Furthermore, the future work will also make use of real-trafic from other organization to produce more accurate results.
References
Amol, S. and Tim, B., 2006, “TCP Connection Management Mechanisms for Improving Internet Server Performance”. Proceeding of HotWeb.
Anazida, Z., Aizaini, M.M., and Mariyam, S., 2006, “Feature Selection Using Rough Set in Intrusion Detection”. Proceeding of the IEEE Region 10 Conference TENCON 2006, IEEE.
Andy, F., 2005, Discovering Statistic Using SPSS, 2nd edition, Sage Publication London.
Caulkin, B.D., Lee, J., and Wang, M., 2005. “Packet vs Session Based Modeling for Intrusion Detection System”. In Proceeding of IEEE International Conference on Information Technology, Coding and Computing, IEEE.
Chebrolu, S., Abraham, A., and Thomas, J.P., 2004, “Feature Deduction and Ensemble Design of Intrusion Detection System”, Journal of Computer and Security, Elsevier Ltd.
Cox, D.R, and Snell, D.J., 1989. The Analysis of Binary Data, 2nd edn, Chapman and Hall, London.
Cyber Security Malaysia, 2007, “E-Security Volume 13-(Q4/2007)”. Technical Report for e-Security, CyberSecurity Malaysia, MOSTI.
EC-Council. 2005, CEH Training Module.
Giancinto, G., Roli, F., and Didaci, L. 2003, “Fusion of Multiple Classiiers for Intrusion Detection in Computer Network”. Pattern Recognition Letter, ACM.
Jalili, R., Fatemeh, I.M., Morteza A., and Hamid, R.S., 2005, “Detection of Distributed Denial of Service Attacks Using Statistical Pre-processor and Unsupervised Neural Network”. ISPEC, Springer-Verlag Berlin Heidelberg.
Karl, L., 2002, “Intrusion Detection: Current Capabilities and Future Direction”.
Proceeding of IEEE Conference of the 18th Annual Computer Security Application, IEEE.
Kayacik, H.G., Heywood, A.N.Z., and Heywood, MI., 2005, “Selecting Features for Intrusion Detection: A Features Relevance on KDD 99 Intrusion Detection Datasets”. In Proceeding of the 3rd Annual Conference on Privacy, Security and Trust, St. Andrew, Canada.
KDDCUP 99 Task Description 1999, Retrieved January 2006, from Kdd web site: http://kdd.ics.uci.edu/databases/kddcup99/kddcup99.html.
Lakhina, A., Crovella, M., and Diot, M.C., 2005, “Mining Anomalies Using Trafic Feature Distribution”. Proceeding of the ACM SIGCOMM, 2005.
Lazarevic, A., Ertoz , L., Kumar, V., Ozgur, A., and Srivastava, J., 2003, “A comparative Study of Anomaly Detection Schemes in Network Intrusion detection”.
Proceeding of SIAM International Conference on Data Mining.
Mark Merkow and Jim Breithaupt. 2006, Information Security Principal and Practic. Pearson Prentice Hall, New Jersey, USA.
McHugh, J., Christie, A., and Allen, J., 2000, “Defending Yourself: he Role of Intrusion Detection System”. Proceeding of IEEE, Software.
Mellia M., Meo M., and Muscariello, L., 2006, “TCP Anomalies: Identiication and Analysis”. Distributed Cooperative Laboratories: Networking, Instrumentation and Measurement, SpringerLink.
Moore, A.W and Zue, D., 2005a., “Trafic Classiication Using Statistical Approach”.
Moore, A.W and Zuev, D., 2005b., “Internet Trafic Classiication Using Bayesian Analysis Technique”. In Proceeding of the 2005 ANC SIGMETRICS International Conference on Measurement and Modeling Computer System.
Moore, A.W and Papaiannaki, K., 2005, “Toward the Accurate Identiication of Network Application”. Passive and Active Measurement Workshop Boston, USA.
Mahoney, M.V. and Chan, P.K., 2001, “PHAD: Packet Header Anomaly Detection for Identifying Hostile Network Trafic”. Technical Report CS-2001-4, Florida Tech. 2001.
Onut, I.V and Ghorbani, A.A., 2006, “Toward a Feature Classiication Scheme for Network Intrusion Detection”. In Proceeding of the 4th Annual Communication
Network and Services Research Conference, IEEE.
Robertson, S., Siegel, EV., Miller, M., and Stolfo, SJ. 2003, “Surveillance Detection in High Band width Environment. In Proceeding of IEEE Conference on the DARPA information Survivability and Exposition, IEEE.
Shahrin, S., Faizal, M.A., and Asrul, H.Y., 2007, “Toward Early Detection of Network Intrusion”. In Proceeding of Information Technology and National Security Conference, Riyard, 1-4 December 2007, Saudi Arabia.
Sung, A.H, and Mukkamala, 2003, “Identifying Important Feature for Intrusion Detection Using Support Vector Machine and Neural Network”. In Proceeding of the International Symposium on Application and the Internet.
Vandement, R and Pras, A., “Assessing Unknown Network Trafic”’, University of Twente Enschede Netherland.
Wang, Y., Huang, GX., and Peng, D.G., 2006, “Model of Network Intrusion Detection System Based on BP Algorithm”. In Proceeding of IEEE Conference on Industrial Electronics and Applications, IEEE, 2006.
Wenke, L., 1999, A Data Mining Framework for Constructing Feature and Model for Intrusion Detection System. PhD thesis University of Columbia.
Wenke, L., Salvatore, J.S., Kui, W.M., 1999, “Mining in a Data-Flow Environment: Experience in Network Intrusion Detection”. In Proceeding of the 5th