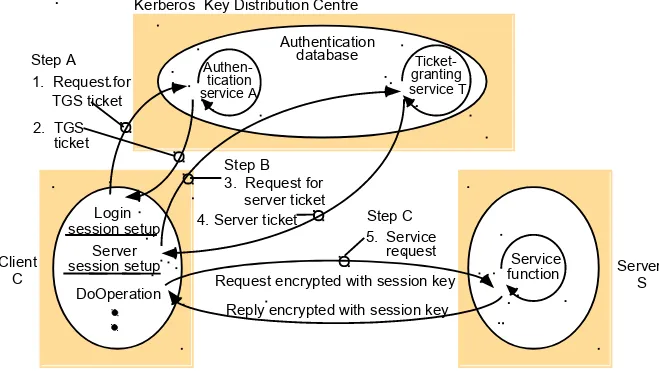
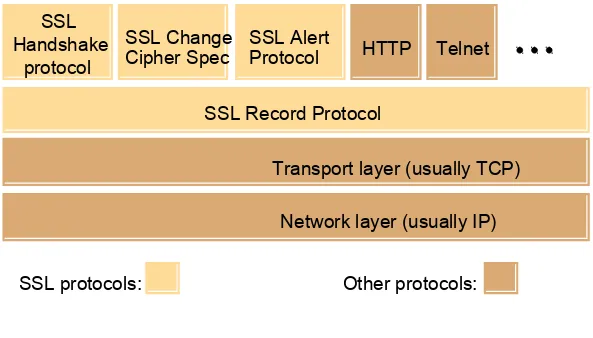
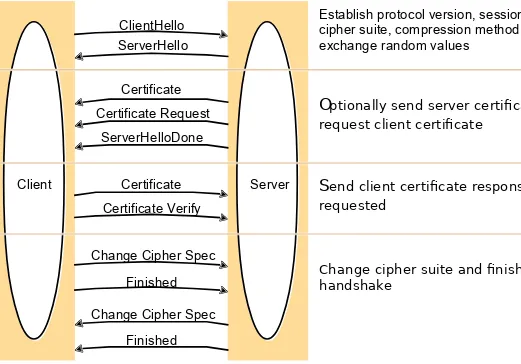
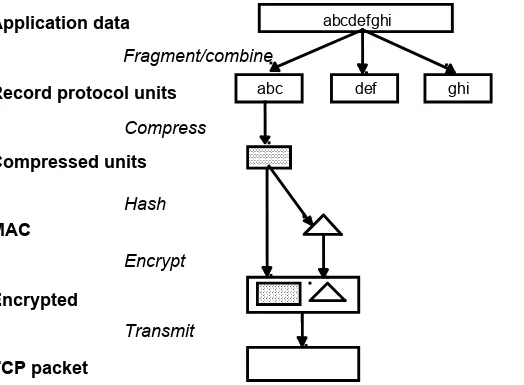
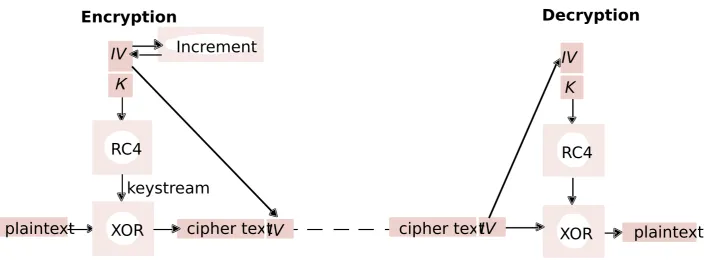
Slides for Chapter 7: Security - Chapter 7 slides
Teks penuh
Gambar



Dokumen terkait
Proses oksidasi ini dapat terjadi dengan adanya oksigen di udara baik pada suhu kamar dan selama proses pengolahan pada suhu tinggi yang akan menyebabkan minyak mempunyai rasa dan
Definisi pajak menurut Undang-Undang Nomor 16 Tahun 2009 tentang perubahan keempat atas Undang-Undang Nomor 6 Tahun 1983 tentang Ketentuan Umum dan Tata Cara
Kemajuan di bidang biologi molekuler telah melahirkan berbagai teknik yang dapat dimanfaatkan dalam pengelolaan penyakit tungro, di antaranya (1) diagnosis penyakit tungro, (2)
Sekunder yaitu berupa data yang diambil dengan cara studi pustaka yang dilakukan dengan melakukan penelusuran bahan hukum melalui alat bantu catatan untuk dapat
Berikut ini adalah beberapa contoh adat ke- biasaan Etnis Arab dalam kehidupan sehari- hari (Fadhli2011) : 1.) Karena menegakkan syariat Islam, orang Arab dilarang berbaur
Panitia akan melakukan verifikasi dalam rangka pembuktian kualifikasi terhadap calon-calon pemenang yang telah ditetapkan dan akan diusulkan kepada Pengguna Jasa untuk
Berdasarkan Surat Penetapan Pemenang Panitia Pengadaan Barang dan Jasa di Lingkungan Dinas Cipta Karya dan Tata Ruang Kabupaten Pelalawan Kegiatan Pembangunan
Kesimpulan yang diperoleh adalah bahwa kadar serat kasar ransum sampai tingkat 15% dala ransum tidak menurunkan konsumsi ransum, kadar lemak darah dan daging bobot badan harian