AN APPLICATION OF PUBLIC KEY CRYPTOSYSTEM
BY RIGHT INVERSE IN DIGITAL SIGNATURE SCHEME
Paper presented in Indonesia Cryptology and Information Security Conference, Jakarta, March 30 – 31, 2005
Budi Murtiyasa
Department of Mathematics Education Muhammadiyah University of Surakarta Indonesia
AN APPLICATION OF PUBLIC KEY CRYPTOSYSTEM BY RIGHT
INVERSE IN DIGITAL SIGNATURE SCHEME
Budi Murtiyasa
Department of Mathematics Education Muhammadiyah University of Surakarta Indonesia
Jl. A. Yani Pabelan Tromol Pos I Surakarta 57102 E-mail : [email protected]
Abstract
The paper presents about digital signature scheme based on public key cryptosystem by right inverse. Based on that scheme, it is discusses characteristics of the scheme, especially in key space, complexity of encryption and decryption, message expansion, and risk analysis. From the analysis, it can be concluded that the digital signature scheme is efficient in key space and fast in encryption/decryption. The disadvantage of the scheme is that it has a message expansion. If the order of private key matrix is large enough, the scheme is still secure from the intruder.
Key words : right inverse, public key cryptosystem, digital signature.
Introduction
The theory of matrices becomes a potential tool in cryptographic research. Recently, it has developed of public key cryptosystem by right inverse (Murtiyasa, et.al., 2004). The idea of development is similar to the previous public key cryptosystem, that is McEliece’s public key and Wu-Dawson’s public key cryptosystem, in term of the usage of a coding theory. Generally, a cryptosystem provides security service in (1) confidentiality, (2) integrity, (3) authenticity, and (4) nonrepudiation. Stallings (2003) explained that a public key cryptosystem can be applied in (i) encryption/decryption, (ii) digital signature, and (iii) key exchange.
signature scheme based on public key cryptosystem by right inverse of matrices in the field Z2. By digital signature, a cryptosystem will provide all the four of security services.
Right Inverse of Matrices
Definition 1: For a square and nonsingular matrixA, A-1 is inverse of A if it satisfies relationship:
AA-1 = A-1A = In [1] A method to obtain matrix A-1 can be carried out by (i) adjoint matrix and determinant, (ii) elementary row operation (ERO), (iii) elementary column operation (ECO), or (iv) combined the ERO and ECO.
The inverse of permutation matrix is also permutation matrix.
Based on Theorem 1 above, a matrix A has right inverses if and only if AT has left inverses. Conversely, a matrix A has left inverses if and only if AT has right inverses.
Furthermore, if A has a right inverse, then (AR)T is a left inverse of AT.
where P is product of elementary row matrices.
Theorem 2. A left inverse of A in form [5] is:
where Q is product of elementary column matrix.
Design of Public Key Cryptosystem
Murtiyasa, et.al (2004) gives a new design of public key cryptosystem by right inverse which can be performed as follows. An arbitrary linear code C[n,k] can be treated as a k-dimensional vector subspace of Vn(Z2). A generator matrix for C is a kxn matrix G that has rank k. For message m, c = mG is codeword. By reconstructing of generator matrix G, that is G = (PRS-1)T, the ciphertext of plaintext m with length k is c = mG. S is a kxk permutation matrix, and P is a kxn matrix with rank k. PR and S-1 are right inverse of P and inverse of S respectively. Matrix G is public to encrypt message m. The decryption to obtain message m can be performed as follows. Compute c(SP)T =
mG(SP)T = m (PRS-1)T (SP)T = m (S-1)T (PR)T PT ST = m. So, R = SP is private key to decrypt ciphertext c. To assure of unique interpretation, the message m must be blocked in k bits.
Table 1. Public Key Cryptosystem By Right Inverse Public key G
Private key R
Encryption c = mG
Decryption m = cRT
A key generation to develop a public key G and a private key R are as follows : (1) select G1 = [Ik | A] with an arbitrary a kx(n-k) matrix A, (2) select a kxk permutation
matrix S, (3) P = SG1 , (4) find a right inverse of P, i.e. PR, (5) find inverse of S, i.e.
S-1, (6) G = (PRS-1)T, and (7) R = SP. So, G is public key to encrypt message m, and R is private key to decrypt ciphertext c. (Murtiyasa, et.al, 2004).
Digital Signature Scheme
A digital signature scheme is developed by an algorithm of the public key cryptosystem. Digital signature scheme between user A and user B can be explained as follows. User A develops a public key G and a private key R each of which is a kxn
permutation matrix S, (3) P = SG1 , (4) find a right inverse of P, i.e. PR, (5) find inverse
of S, i.e. S-1, (6) G = (PRS-1)T, and (7) R = SP.
Meanwhile, user B develops a public key K and a private key H each of which is an nxw dimensional. A key generation to develop a public key K and a private key H by user B are as follows : (1) select K1 = [In | B] with an arbitrary a nx(w-n) matrix B , (2)
select a nxn permutation matrix T, (3) Q = TK1 , (4) find a right inverse of Q, i.e. QR,
(5) find inverse of T, i.e. T-1, (6) K = (QRT-1)T, and (7) H = TQ.
Encryption. Encryption to message m by user A carried out in two steps, namely (1) y =
mR, and (2) c = yK. Furthermore, ciphertext c is transmitted to user B.
Decryption. When user B receives ciphertext c, decryption and verification are also in two steps, i.e. : (1) y = cHT , and (2) m = yGT.
Characteristics of the Digital Signature Scheme
A key space for encryption depends on the dimension of matrix R and K, which are (kn + nw) bits. A key space for decryption depends on the dimension of matrix H and
G, that is (nw + kn) bits. Totally, key space is 2(kn + nw) bits.
Complexity of encryption and decryption is computing based on a number of additional and multiplication operation. Encryption complexity is (2k–1)n + (2n–1)w operation, and decryption needs (2w – 1)n + (2n – 1)k operation. Totally, encryption and decryption complexity needs (4nw + 4kn – 2n – w – k) operation, which is family of O(nw). Ratio of message expansion is w/k.
Table 2. Comparison of the digital signature scheme Digital
signature
Key pace for encryption
Key space for decryption
Complexity of encryption and decryption
Message expansion My scheme kn + nw kn + nw 4nw + 4kn – 2n – w – k
Æ O(nw)
w/k
RSA scheme 4(k + 1) 4(k + 1) O(k3) k/k = 1
and verifying of message can be done more quickly. Conversely, a digital signature scheme by RSA cryptosystem is more efficient in key space and message space than the digital signature scheme which uses the cryptosystem by right inverse.
Risk Analysis
A security of ciphertext c depends on key H which is a private key of user B. If the private key H is found, the ciphertext c can be broken and the attacker gets message
m. The private key H possibility is attacked by : (1) finding a matrix that develops H (2) finding right inverse of K, and (3) trying an arbitrary matrix H.
(1) attack 1 : finding a matrix that develops matrix H, namely matrix T and Q = TK1,
where K1 = [In | B]. In this case Q depends on T and B. Hence, finding a matrix Q
means finding an nxn permutation matrix T and nx(w-n) matrix B. By Lemma 1, a number of permutation matrices T is n!. Meanwhile, the number of possibilities of
matrix B is 2n(w-n). So, the number of ways to get matrix H is n! 2n(w-n). By this attack,
probability the intruder will succeed is only ( )
2
only one. Hence, probability the intruder will succeed is (wn)n
2
1
− .
(3) Attack 3 : trying an arbitrary matrixH. A matrix H has an order nxw. The number of elements of H is nw. In the field Z2 = {0, 1}, the number of possibilities of matrix H
is 2nw. It is a greater number to get one of the key matrices. By this attack, probability
the intruder will succeed is nw
2
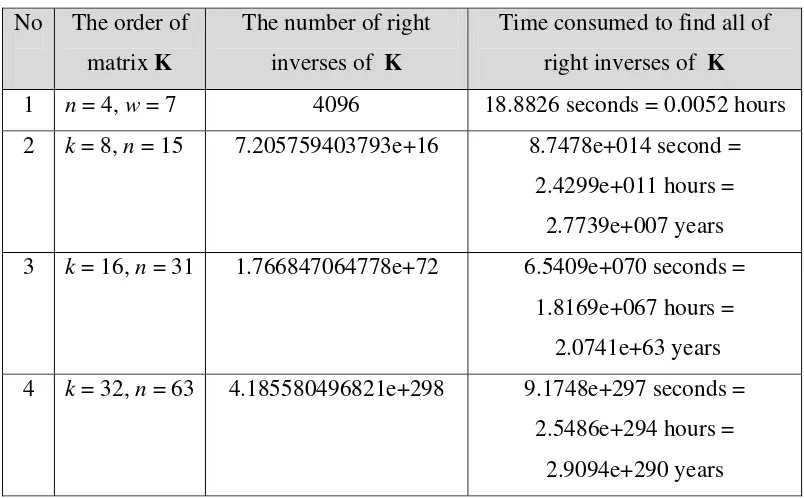
Table 3. The number of Possibilities to find right inverses of K
No The order of matrix K
The number of right inverses of K
Time consumed to find all of right inverses of K
1 n = 4, w = 7 4096 18.8826 seconds = 0.0052 hours 2 k = 8, n = 15 7.205759403793e+16 8.7478e+014 second =
2.4299e+011 hours = 2.7739e+007 years 3 k = 16, n = 31 1.766847064778e+72 6.5409e+070 seconds =
1.8169e+067 hours = 2.0741e+63 years 4 k = 32, n = 63 4.185580496821e+298 9.1748e+297 seconds =
2.5486e+294 hours = 2.9094e+290 years
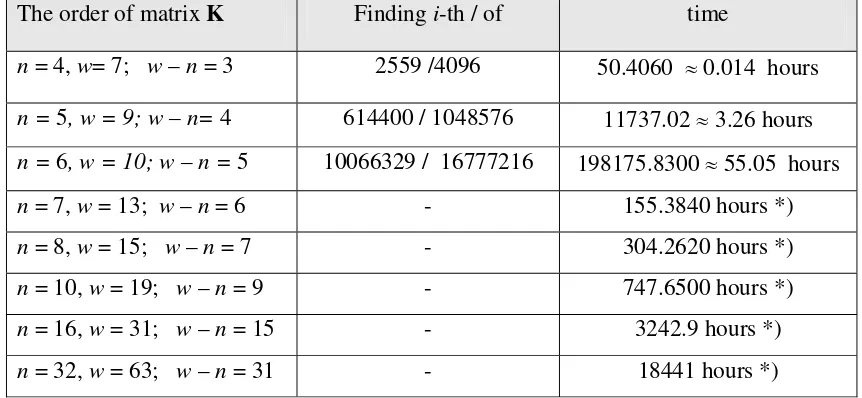
From the above discussion, finding right inverse of K provides the greatest probability to succeed on attacking to the digital signature scheme. Table 3 gives an illustration to find all possibilities of right inverses of matrix K. Data in Table 3 are worst cases to find right inverse of K. However, if the intruder is lucky, it is possible to break the ciphertext faster than the time indicated. Table 4 gives an illustration about best case to break the ciphertext. Based on data in Table 4, extrapolation for the value of n and w
Tabel 4. Best Case to Break the Ciphertext
The order of matrix K Finding i-th / of time
n = 4, w= 7; w – n = 3 2559 /4096 50.4060 ≈ 0.014 hours
n = 5, w = 9; w – n= 4 614400 / 1048576 11737.02 ≈ 3.26 hours
n = 6, w = 10; w – n = 5 10066329 / 16777216 198175.8300 ≈ 55.05 hours
n = 7, w = 13; w – n = 6 - 155.3840 hours *)
n = 8, w = 15; w – n = 7 - 304.2620 hours *)
n = 10, w = 19; w – n = 9 - 747.6500 hours *)
n = 16, w = 31; w – n = 15 - 3242.9 hours *)
n = 32, w = 63; w – n = 31 - 18441 hours *) Note : *) extrapolation from the prior data.
Conclusion and Suggestion
The public key cryptosystem by right inverse is applicable for digital signature. Hence, the cryptosystem provides a confidentiality, integrity, authenticity, and non repudiation service. The digital signature scheme is efficient in key space and lower complexity than RSA Scheme. The disadvantage of the digital signature scheme is that it has a message expansion. It can be pointed out that if the value of n and w , which are dimension of private key K, such that n – w > 250, with w ≈ 2n, the digital signature scheme is still secure from the intruder.
References
Ayres Jr., F., 1982, Theory and Problems of Matrices. Asian Edition. Singapore : Mc Graw-Hill Book Company.
Huang, H.F., and, Chang, C.C, 2002, “Cryptanalysis of the WD Public-Key Cryptosystem” Paper in First International Symposium on Cyber World, November 2002, Institute of Electrical Electronics Engineers.
Kwak, J.H., and Hong, S., 1997, Linear Algebra, Boston : Birkhauser
Murtiyasa, B., Subanar, Wardoyo, R., Hartati, S., 2004, “Right Inverse in Public Key Cryptosystem Design” in Proceeding of the SEAMS-GMU Conference 2003, Pp 414-418. Yogyakarta : Department of Mathematics Gadjah Mada University.
Stallings, W., 2003, Cryptography and Network Security Principles and Practice Third Edition, New Jersey : Pearson Education, Inc.
Sun, H.M., 2001, “Cryptanalysis of a Public Key Cryptosystem Based on Generalized Inverses of Matrices” in IEEE Communication Letter Vol. 5 No. 2, Pp. 61 – 63.