IPv6 Address Generation Mechanism for Enterprise
Wireless Network
Akhmad U. Priantoro, Nashrul Hakiem, M. Umar Siddiqi and Talib H. Hasan
Faculty of Engineering, International Islamic University MalaysiaP.O. Box 10, 50728 Kuala Lumpur, Malaysia
Abstract- Wireless local area network (WLAN) has become a norm in campuses as well as established enterprises to compliment or completely replace the wired networks. While this believed to be positively contributing to staff productivity, at the same time it also poses new challenges in network management, especially the security aspect such as internal threats due to abuse or exploit. Meanwhile, migration to IPv6 has steadily increasing amidst the accelerating rate of IPv4 address depletion, which is expected to be exhausted in the near future. This paper proposes a new mechanism to generate IPv6 addresses, specifically the 64 bit LSB which correspond to the interface ID, in enterprise wireless network that facilitates dynamic address assignment via DHCP and yet can be associated with any individual user exclusively for management purpose
Keywords: IPv6 address management, enterprise wireless network, interface ID, DHCP
I. INTRODUCTION
Wireless local area network (WLAN) has been widely deployed in campuses, companies and government offices across the globe to complement the pre-existing wired network or to completely replace the wired network [1]. WLAN offers flexibility for topology changes and network clients’ mobility across the campus’ or enterprise’s compounds. It has been credited as a factor contributing to increasing staff productivity in companies and enhanced learning culture in universities [1]. WLAN allows clients to access the available resources anytime, anywhere within the coverage area.
In WLAN environment, managing wireless users is a tedious and cumbersome task since access to the network is not limited by ports anymore. This is particularly true for campuses since most of the users, i.e., students, are unmanaged. In WLAN, virtually ports are available throughout the coverage areas, therefore it is very important to properly secure the network from external and internal threats, and manage the network resources such as available internet bandwidth, network infrastructure and IP addresses. This paper focuses on IP address management in IPv6-based WLAN. Traditionally, in IPv4, Dynamic host configuration via Dynamic Host Configuration Protocol (DHCP) server is the common approach taken in WLAN deployment to manage the IP addresses. DHCP simplifies IP address and other necessary network parameters assignment from the network administrator point of view and removes the need for end user to configure their mobile devices manually. When DHCP is deployed, client or user
will be provisioned with IP address available from the IP address pool in the DHCP server each time they connect to the network. In IPv6, similar approach is also supported with minor differences [2].
The limitation of the address space in IPv4 has been motivating many organizations, especially in developing countries, to migrate to the IPv6 which provides unlimited address space to cater for future network growth and improvement of network services. In IPv6, several IP address configuration/ generation mechanisms have been proposed such as stateless autoconfiguration [3,4] and stateful configuration via DHCP server [2,5]. Cryptographically generated address (CGA) [6,7] and its extension multi-key CGA (MCGA) [8]. These mechanisms have different target applications and concerns to meet the future requirement ranging from sensor network deployment to mobile networking.
On the other hand, the proliferation of WLAN has also contributes to increasing security threats from within the enterprise network [9]. Virus and worm outbreaks and confidential information leakage are among the top in the list [10]. Current deployment of WLAN although equipped with data encryption and authentication specified in 802.11i and 802.11x standards respectively, and network access control [11], usually doesn’t monitor users’ traffic once they are authenticated to join the network. Since users are given dynamic IP address, generally is difficult to trace users’ online behavior which is becoming more important from network/security administrator point of view.
In this paper, we propose a new mechanism of generating IP address in IPv6-based WLAN by taking advantage of the availability of “unlimited” IP address space and the fact that enterprise wireless network is under one administrative domain. In the proposed mechanism, each user is given a unique user ID that will be embedded into the generated IP address that allows simple detection of IP address owner by using a binary mask. Specifically, the mechanism focuses on the least significant 64 bits of the IP address, which corresponds to interface ID. To reduce accidental match of randomly generated IP address checksum bits are also embedded.
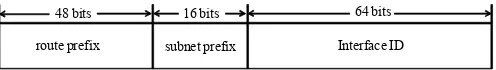
48 bits 16 bits 64 bits
route prefix subnet prefix Interface ID II. STATEFUL IPV6ADDRESS CONFIGURATION
IPv6 was designed to provide indefinite support to the existing IPv4 as well as expanding network services to support ubiquitous networking whereby most of electronic devices are interconnected such as sensor networks, RFID’s as well as ad hoc networks [12]. In order to support a wide array of devices’ capabilities and constraints, IPv6 has several mechanisms to facilitate “plug and play” autoconfiguration and manual configuration of nodes. However the latter practice is not highly recommended considering the complexity of the address which is comprised of 128 bits.
Stateless autoconfiguration is intended for ease of deployment of unmanaged network or network whose nodes have limited capability such as sensor network. The stateless mechanism allows a host to generate its own addresses using a combination of locally available information and information advertised by routers [3].
In stateless auto configuration IP address can be derived from MAC address [12] or other mechanism such as Cryptographically Generated Address (CGA) [6] and its extension, Multi-key CGA (MCGA) [8]. CGA was originally defined for resolving security issues in Neighbor Discovery protocol. It generates the interface ID by using one way hash function with user’s public key and auxiliary parameters as the input. When required, anyone can verify the binding between the public key and the interface ID portion of the IP address by regenerating the interface ID using the public key and associated auxiliary parameters. A user who send a signed message, using his/her private key, from the IP address and attaching the public key and the auxiliary parameters can be verified by the packet recipient without a Public Key Infrastructure (PKI). This is very useful to secure the Neighbor Discovery protocol in unsecured environment such as public hot spots to prevent spoofing. As extended usage of CGA, it has been proposed to secure other protocols such as the Mobile IPv6 (MIPv6) protocol [13,14]. Further enhancement was done to support multiple hash function [15].
As a complementary of stateless autoconfiguration there is stateful autoconfiguration which is widely used in managed network, such as enterprise and campus networks. In the scheme, hosts obtain interface addresses and other configuration information from a server. Servers maintain a database that keeps track of which addresses have been assigned to which hosts, or the binding information. DHCPv6 simplifies network administration and requires minimum or no manual configuration of DHCPv6 clients. Thus a DHCPv6 client may be given different IP address each time it requests to the DHCP server. Although DHCPv6 server maintains the binding information, and can be logged for later retrieval, it (the binding information) is only known to the DHCP server. Any network node requires the information must send queries to the DHCP server.
Recently there is an increasing interest to merge the goodness of DHCPv6 and CGA [16]. Since CGA address generation is computationally expensive, it was suggested to offload the operation to a proxy in an environment whereby hosts do not support CGA address generation by themselves or use DHCPv6 server to manage CGA addresses via
registration. In either case, a mechanism to ensure that the IP address generated is routable within the link duplicate address detection (DAD) [RFC2462] will be executed before an address is assigned to an interface by the host. However, it is worth noting that DAD can be disabled when deemed unnecessary by system administrator.
IPv6 address configuration mechanisms previously described, do not facilitate IPv6 address owner detection in real time which may be of interest to enterprise wireless network administrator for various reasons. In the next section, we describe a novel IPv6 node interface ID generation mechanism that supports IPv6 address owner identification in real time. The mechanism takes advantage of the huge size of IPv6 address.
III. PROPOSED INTERFACE IDGENERATION MECHANISM
In IPv6, 128 bits are used to specify the address of a node which format is shown in Figure 1.
Fig. 1 IPv6 address format
The first 48 bits are allocated for network address which is globally unique, thus globally routable. The following 16 bits are allocated for subnet prefix within a network to allow network administrator defining the desired internal network hierarchy. The remaining 64 bits are allocated for interface ID for nodes. This proposal focuses on the mechanism to generate the interface ID in order to simplify the IP address management in enterprise WLAN.
We propose to generate IP address which can be exclusively mapped to each individual user in real time. Identification of the owner of valid IP address is done by masking the interface ID with a certain binary mask. Further, to reduce the probability of coincidental match of randomly generated interface ID, checksums are embedded in the generated interface ID. Thus, theoretically a valid user can have sufficient number of IP addresses for his exclusive use, a many-to-one mapping from the IP address space to the user space. The detail IP address generation mechanism is as follows.
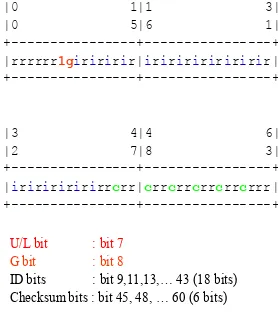
|0 1|1 3| |0 5|6 1| +---+---+ |rrrrrr1giriririr|iriririririririr| +---+---+
|3 4|4 6| |2 7|8 3| +---+---+ |iriririririrrcrr|crrcrrcrrcrrcrrr| +---+---+
U/L bit : bit 7
G bit : bit 8
ID bits : bit 9,11,13,… 43 (18 bits) Checksum bits : bit 45, 48, … 60 (6 bits)
Fig. 2 Proposed format of interface ID
where Xi,Y and Z are octal numbers, λ,κ are parametric constants that can be arbitrarily chosen by network administrator.
3. Generate 64-bit random binary sequence
4. Over write selected bit position with the user ID and checksum bits as illustrated in Fig. 3.
5. Set U/L bit =1 and G bit=0
Interface ID generated using our algorithm is guaranteed to be unique within a subnet, which is sufficient to guarantee global uniqueness since the route prefix and subnet prefix for each organization are guaranteed to be uniquely assigned by the the Internet Assigned Numbers Authority (IANA), thus DAD can be disabled that will reduce the network load during host booting.
Fig. 3 shows the (auto and cross) correlation values of randomly generated interface ID using Java library [17]. As we can see from the figure, the cross correlation of randomly generated interface ID is normally distributed with average of 0.51 and standard deviation of 0.069. Meanwhile, Fig. 4 shows the correlation values of interface ID generated using the proposed mechanism. Comparing Fig.5 and Fig. 4, we can see a noticeable increase in the correlation values and decreasing standard deviation of the interface ID generated using the proposed mechanism. The correlation values of the interface ID as illustrated in Fig. 5 also follows normal distribution with average of 0.70 and standard deviation of 0.052. This means that the generated IPv6 addresses that belong to the same user have higher degree of similarity. This increasing similarity is due to the insertion of user ID and checksum bits which are identical for all IPv6 addresses belong to the same user. This might be exploited to infer IPv6 address owner by network adversaries which may raise further security and privacy concerns. Therefore, it is desirable to reduce the cross correlation values of the generated IPv6 addresses belong to the same user. Carefully designed random number generators that reduce the cross correlation of IP addresses belong to the same user is of interest. The consequence of such random number generator is the reduction of usable IP addresses for each user.
Fig. 3 Correlation matrix of randomly generated addresses
Fig. 4 Correlation matrix of generated addresses, using proposed mechanism, belong to the same user
sample number
sample number
Table 1 Sample of generated interface ID
user ID 521000 user ID 000123
cc88:8095:4416:65be e445:4013:30a8:a64c
8cd8:94c5:011e:6cbe 8814:1012:71b1:e2ee
0cc9:90d4:5115:601a d410:4547:24ea:aacd
749d:91c1:445c:650e 2811:0453:65e0:a368
509d:8085:5005:601f 7440:5446:24e1:eecc
cc88:84d1:510d:65bf 2404:4047:60fa:abee
44d9:c084:1107:4c2f 5c41:4157:71a8:aa6c
d4dc:d5c0:0447:081c fc51:0003:60ab:c66e
f499:90d4:5146:4db8 6850:4452:20f0:ae6d
0088:d595:114c:289a 0f50:0053:35ab:aafd
949d:81d1:150f:0c29 00f4:1047:61b2:a66b
3899:d0d5:1144:6009 0e54:4016:75ba:afff
5c99:95d1:5454:411a 0441:1447:74b0:a2de
348c:c085:144e:25ab a404:5552:75a2:ebce
IV. POSSIBLE APPLICATIONS
In developing and third world countries internet bandwidth is a precious resource in organizations. Proper bandwidth management will definitely helps the organization to maximize its investment in internet connectivity, by minimizing junk traffic and prioritizing valid traffic. The proposed IPv6 address generation mechanism can be used to simplify the bandwidth management by recognizing users by his/her IPv6 addresses. Another possible application is to facilitate network policy enforcement. Today more and more ICT services and applications migrate to web based services [18] which make controlling internet (including intranet) traffic using ports is not feasible anymore. Being able to recognize users by their IPv6 addresses can automate the decision whether to grant or deny access to certain internal and external servers. This will enhance the existing security measures already implemented in the network.
V. CONCLUSION
IPv6 address management in enterprise wireless network is of interest to network administrator. It helps network administrator to efficiently manage the network and improve the controllability and visibility of the network that in the long run will increase the ROI of ICT investment and compliance to regulations via policy enforcement. A simple mechanism to generate IPv6 addresses for enterprise wireless network was proposed that facilitates real-time user identification from their IPv6 addresses. The generated IPv6 address is embedded with user ID so that users can be identified by using simple binary mask and check sum values also embedded to reduce the probability of randomly generated address coincides with valid IPv6 addresses generated by the proposed mechanism.
The proposed IPv6 address management can be used to develop future applications that will enhance the enterprise network security.
REFERENCES
[1] Gartner, “User Survey Report: Wireless LANs, North America and Europe 2005,” http://www.gartner.com/it/page.jsp?id=493658
[2] Perkins, C.E. Bound, J.,”DHCP for IPv6,” Proceedings Third IEEE Symposium on Computers and Communications, July 2008 pp. 493-497
[3] S. Thomson and T. Narten,” IPv6 Stateless Address Autoconfiguration,” RFC 2462, December 1998
[4] T. Narten and R. Draves,” Privacy Extensions for Stateless Address Autoconfiguration in IPv6,” RFC 3041, January 2001
[5] R. Droms, Ed., J. Bound, B. Volz, T. Lemon, C. Perkins and M. Carney,” Dynamic Host Configuration Protocol for IPv6,” RFC 3315, July 2003
[6] Aura, T., "Cryptographically Generated Addresses (CGA)", RFC 3972, March 2005.
[7] M. Bagnulo and J. Arkko,” Cryptographically Generated Address Extension,” RFC 4581, October 2006
[8] James Kempf, Jonathan Wood, Zulfikar Ramzan, and Craig Gentry, “IP Address Authorization for Secure Address Proxying Using Multi-key CGAs and Ring Signatures,” Lecture Notes in Computer Sciences,
SpringerLink 2006, pp. 196-211.
[9] http://www.infosectoday.com/IT%20Today/Mazu.htm; retrieved 10 June 08
[10] Delloite,” Global Security Survey 2007: The Shifting Security Paradigm,”http://www.deloitte.com/dtt/research/0,1015,cid%253D17 1332,00.html
[11] López, G., Cánovas, O., Gómez, A. F., Jiménez, J. D., and Marín, R.,”A network access control approach based on the AAA architecture and authorization attributes,” J. Netw. Comput. Appl. 30, Aug. 2007, pp. 900-919
[12] J.J. Amos and D. Minoli,”Handbook of IPv4 to IPv6 Transition,” Auerbach Publications, 2008
[13] G. O’Shea and M. Roe, “Child-Proof Authentication for MIPv6 (CAM), ”SIGCOMM Comput. Commun. Rev., vol. 31, no. 2, pp. 4–8, 2001.
[14] Arkko, J., "Applying Cryptographically Generated Addresses and Credit-Based Authorization to Mobile IPv6", Work in Progress, June 2006.
[15] M. Bagnulo and J. Arkko,” Support for Multiple Hash Algorithms in Cryptographically Generated Addresses (CGAs),” RFC 4982, July 2007
[16] I. V. Beijnum,” Interaction between CGA and DHCPv6,” IETF Network Working Group Internet Draft, November 2007 [17] http://java.sun.com/j2se/1.3/docs/api/java/util/Random.html