Full Terms & Conditions of access and use can be found at
http://www.tandfonline.com/action/journalInformation?journalCode=vjeb20
Download by: [Universitas Maritim Raja Ali Haji] Date: 11 January 2016, At: 22:13
Journal of Education for Business
ISSN: 0883-2323 (Print) 1940-3356 (Online) Journal homepage: http://www.tandfonline.com/loi/vjeb20
Information Systems Security and Computer
Crime in the IS Curriculum: A Detailed Examination
C. Bryan Foltz & Janet S. Renwick
To cite this article: C. Bryan Foltz & Janet S. Renwick (2011) Information Systems Security and Computer Crime in the IS Curriculum: A Detailed Examination, Journal of Education for Business, 86:2, 119-125, DOI: 10.1080/08832323.2010.489587
To link to this article: http://dx.doi.org/10.1080/08832323.2010.489587
Published online: 23 Dec 2010.
Submit your article to this journal
Article views: 145
ISSN: 0883-2323
DOI: 10.1080/08832323.2010.489587
Information Systems Security and Computer Crime
in the IS Curriculum: A Detailed Examination
C. Bryan Foltz
University of Tennessee at Martin, Martin, Tennessee, USA
Janet S. Renwick
University of Arkansas at Fort Smith, Fort Smith, Arkansas, USA
The authors examined the extent to which information systems (IS) security and computer crime are covered in information systems programs. Results suggest that IS faculty believe security coverage should be increased in required, elective, and non-IS courses. However, respondent faculty members are concerned that existing curricula leave little time for additional topics.
Keywords: information assurance, information systems curricula, security
INTRODUCTION
Computer crime and misuse continues to be an issue in our society and is very common among college students (Carnevale, 2002; Cronan, Foltz, & Jones, 2006; Vaughn & Boggess, 1999). As a result, many universities attempt to protect themselves by using computer usage policies. These policies attempt to prevent misuse by explaining cor-rect and incorcor-rect usage of systems. However, many students (Cronan et al.) and faculty members (Foltz & Hauser, 2004) are unfamiliar with these policies.
Further, many universities simply fail to cover computer security and computer misuse topics within their curricu-lum. Previous research by Anderson and Schwager (2002) suggested that many information systems programs provide little or no coverage of this increasingly important topic.
Purpose
The purpose of this research is to further examine the extent to which information systems security and computer crime are covered in information systems programs around the United States. This work will both update and expand Anderson and Schwager’s (2002) study. Rather than examining a
self-Correspondence should be addressed to C. Bryan Foltz, PhD, University of Tennessee at Martin, College of Business and Public Affairs, Department of Computer Science & Information Systems, BA 226, Martin, TN 38238, USA. E-mail: foltz@utm.edu
reported list of coverage, this research examines the amount of time actually spent discussing given topics.
Information Systems Security and Computer Crime Coverage in the Information Systems Curriculum
Although the cost and frequency of information systems mis-use and computer crime is often studied—for example, the 2007 CSI Computer Crime and Security survey reported the cost of computer crime to respondents as$66,930,950
(Richardson, 2007)—these topics are underrepresented in many undergraduate information systems curricula today (Walters, 2007). Indeed, a recent survey of the core cur-ricula of undergraduate information systems programs in the United States did not mention information systems security at all (Kung, Yang, & Ahang, 2006). Further, a recent survey of the most popular textbooks used in introductory infor-mation systems courses found a surprising lack of depth of information systems security coverage (Sousa, MacDonald, & Fougere, 2005).
Previous research into the teaching of computer security has revealed various recommendations to include more com-puter security topics (Prichard & MacDonald, 2004; Vaughn & Boggess, 1999). Some studies have looked at the efficacy of particular programs or courses (National Security Agency, 2009). Anderson and Schwager (2002) found that many of the areas in the Certified Information Systems Security Pro-fessional (CISSP) common body of knowledge were consid-ered relevant to the IS curriculum. The authors concluded
120 C. B. FOLTZ AND J. S. RENWICK
that no required IS curriculums covered all of the CISSP se-curity issues. In fact, only 2% of curriculums covered 80% of the CISSP issues. Further, only 8% of elective curriculums covered all of the CISSP issues, whereas 22% of elective cur-riculums covered over 80% of the CISSP issues. The authors also found that the majority (70%) of respondents wanted se-curity integrated into other courses, although 32% felt that, if a security course were available, it should be required. However, the authors were unable to determine the extent to which these topics are actually being taught (Anderson & Schwager). Our study attempts to fill this void by collecting data from IS faculty regarding classroom coverage. Because of the evolving nature of the field, IS faculty often include topics from sources outside of textbooks. Rather than relying on measures of coverage within textbooks, we gathered data directly from faculty teaching IS courses.
Model Curricula
In trying to evaluate present curricula, we first turned to the model curriculum in the field. The most recent model cur-riculum for Information Systems is IS 2002 (Gorgone, 2002). Published jointly by the Association for Computing Machin-ery (ACM), the Association for Information Systems (AIS), and the Association for IT Professionals (AITP), it is used for guidance by colleges and universities offering informa-tion systems as an undergraduate major. Representatives of each of these professional societies worked to develop this document as both a reflection of present practice and as a guide for the future. Faculty in computing programs across the United States provided input. This model curriculum rep-resents a high degree of consensus among a very diverse group of individuals.
IS 2002 lists computer security as a topic area in the “Fundamentals of IS” course. This course, often offered at the freshman level, is described as a prerequisite to upper level course work. It includes concepts such as systems theory, specification and design of information systems, object-oriented design, and procedural and nonprocedural programming languages, database, features of networks, and IS career paths. This course is clearly covering a large number of varied topics. In some programs, these topics are lumped together with the model curriculum course “Personal Productivity with IS Technology” in a single three-credit course. The introductory nature of this course suggests a low level of coverage for security topics.
IS 2002 also describes courses in “Electronic Business” and “Hardware and Software Systems.” These courses are also candidates for the inclusion of security-related topics.
Because the IS 2002 curricula was published in 2002, most of the input from the IS community was gained prior to the September 11, 2001 terrorist attacks. Unfortunately, those events have changed many aspects of society, including our emphasis on security. This study endeavors to assess the degree to which IS security issues are being addressed not
only in the model curriculum, but also in the actual curricula being delivered to students in Information Systems.
METHOD
In order to ascertain the coverage of security as a topic, we developed a web-based survey. Target subjects are IS faculty members in colleges of business. These individuals are actively involved in developing and delivering curriculum to information systems majors. Participants in the pilot study were solicited via personal e-mail and telephone. Comments from the pilot study were used to finalize the questions and format of the survey instrument. Responses from the pilot survey were not combined with those from the full study. For the broader study, participants were solicited through Internet discussion lists used by faculty in information systems, as well as via e-mail. Although responses were solicited via telephone for the pilot study, all responses for the main study were solicited via e-mail.
Survey Items
The survey items were based on the items in the common body of knowledge as defined by the CISSP examination. This certification is an indication of expertise in the area of information systems security and is highly regarded in the computing industry (Gregory, 2003). Other certifications such as GIAC, CISA, and CISM are also available, but are less well known. CISSP provides clearly stated areas within the applicable body of knowledge, which adapt well to our research methodology. It was also used as the basis of earlier research in this field (Anderson & Schwager, 2002).
One item of potential confusion related to CISSP’s inclu-sion of applications and systems development as an area in the common body of knowledge. Certainly, a knowledge of development techniques and how they are used would be an advantage to an IS security professional, and well-designed systems should, by their nature, be more secure. However, it does not seem that all of applications and systems de-velopment is intrinsically related to IS security. Anderson and Schwager (2002) remedied this by rewording this topic area as applications and systems development security. To avoid potentially confusing respondents, two questions were used on the present survey. The first focused on coverage of application and systems development, whereas the second question focused on application and systems development security.
The topic areas for coverage of IS security in curricula thus became
• Access Control Systems & Methodology
• Applications & Systems Development
• Applications & Systems Development Security
• Business Continuity Planning
• Cryptography
• Law, Investigation & Ethics
• Operations Security
• Physical Security
• Security Architecture & Models
• Security Management Practices
• Telecommunications, Network & Internet Security.
Likert-type scales were developed for each of these sub-ject areas, with responses ranging from 0 hr to more than 25 hr. Respondents were also asked whether their programs offered a course dedicated to computer security issues, either as an elective or graduation requirement. Other questions in-cluded the individual respondent’s position and the extent to which they were personally teaching security issues.
Hypotheses
The first research question involves the general coverage of computer security in undergraduate IS degrees.
Proposition 1: IS undergraduate curricula includes instruction on computer security. IS undergraduate cur-ricula includes courses that are required of all IS graduates, those that are elective, and non-IS courses. Subsequently, this proposition was broken down to the three following hypothe-ses.
• Hypothesis 1a:
◦ H0: IS undergraduate curricula will not include
classroom hours on computer security in required courses.
◦ Ha:IS undergraduate curricula will include classroom
hours on computer security in required courses.
• Hypothesis 1b:
◦ H0:IS undergraduate curricula will not include
class-room hours on computer security in IS elective courses.
◦ Ha:IS undergraduate curricula will include classroom
hours on computer security in IS elective courses.
• Hypothesis 1c:
◦ H0:IS undergraduate curricula will not include
class-room hours on computer security in non-IS classes.
◦ Ha:IS undergraduate curricula will include classroom
hours on computer security in non-IS classes.
In addition, the various topical areas are examined to de-termine what areas of computer security are covered in the curriculum.
As computer security increases its mainstream status in industry, a corresponding shift should occur in IS curricula. This should reflect in anticipated changes over the next five years. This leads to the second proposition and associated hypotheses.
Proposition 2: Over the next five years, computer security will become more a part of required IS under-graduate curricula.
• Hypothesis 2a:
◦ H0: IS faculty members will not project a need for
more coverage of IS security in required courses over the next five years.
◦ Ha:IS faculty members will project a need for more
coverage of IS security in required courses over the next five years.
• Hypothesis 2b:
◦ H0:IS faculty members will not project a decrease in
the coverage of IS security in elective courses over the next five years.
◦ Ha:IS faculty members will project a decrease in the
coverage of IS security in elective courses over the next five years.
• Hypothesis 2c:
◦ H0:IS faculty members will project no change in the
coverage of IS security in non-IS courses over the next five years.
◦ Ha: IS faculty members will project a change in the
coverage of IS security in non-IS courses over the next five years.
Curriculum changes, however, do not come without chal-lenges. IS faculty teach in a subject area that requires con-stant updating as technology changes. They also struggle with balancing course requirements in general education, general business, and other areas within the IS major. These conditions lead to proposition 3 and associated hypotheses.
Proposition 3: IS faculty see the need to increase the level of instruction on computer security but are challenged to do so.
• Hypothesis 3a:
◦ H0:IS faculty will not see a need to shift instruction
on computer security from elective courses to required courses.
◦ Ha:IS faculty will see a need to shift instruction on
computer security from elective courses to required courses.
• Hypothesis 3b:
◦ H0:IS faculty expertise is not a challenge in including
computer security in the curriculum.
◦ Ha: IS faculty expertise is a challenge in including
computer security in the curriculum.
• Hypothesis 3c:
◦ H0:IS curricula are not challenged to include computer
security because the curriculum is already full.
◦ Ha: IS curricula are challenged to include computer
security because the curriculum is already full.
122 C. B. FOLTZ AND J. S. RENWICK
FIGURE 1 Accreditation.
RESULTS
Survey responses were solicited using a combination of tech-niques. Responses were initially requested on the ISWorld listserv. This listserv reaches over 5,000 individuals, presum-ably faculty in IS programs around the world. In addition, an initial mailing was sent to a list of 2,829 faculty e-mails gleaned from AACSB-accredited university web sites. Be-cause this list was a few years old, many of the addresses were obsolete. We received 418 read receipts from identifi-able addresses from this initial contact. A follow-up note was sent to these individuals approximately two weeks following the initial request.
From this effort 63 responses were received, 61 of which were usable. Forty-three of the respondents identified them-selves with their return e-mail address asking for a copy of the preliminary results. This indicates both a high level of interest as well as a lack of concern for anonymity among the respondents.
Fifty of the responses were from AACSB-accredited col-leges of business. Twelve were accredited by ABET. Three responses indicated they were accredited by ACM. These results are shown in Figure 1.
Program sizes were predominately small. Almost half of respondents (of 57 providing program size responses) were from programs that had 0–24 graduates in 2006, shown in Figure 2.
Proposition 1: Degree of Coverage
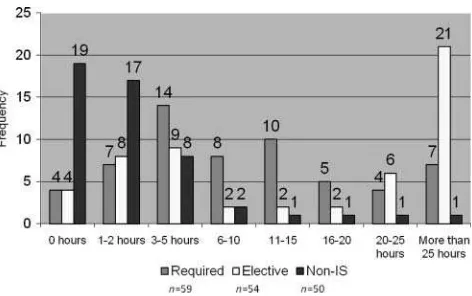
IS faculty were asked to estimate the total number of hours spent on IS security in their curriculum. The results are shown in Figure 3.
FIGURE 2 Program size.
FIGURE 3 Estimated hours on computer security.
By taking the midpoints of the ranges, the means of each of these areas were calculated. These are shown in Table 1. Null hypotheses 1a, 1b, and 1c were rejected and support was given to the alternate hypotheses, suggesting that security issues are taught in IS courses.
Topic Areas
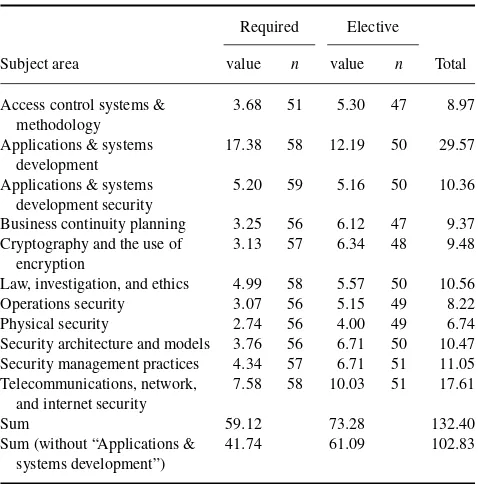
In addition to asking about the total number of hours covering IS security, respondents were also asked more specifically about topical areas within security, as discussed previously. The means of the responses are shown in Table 2.
There are several interesting results shown here. The sub-ject area receiving the most coverage is applications and sys-tems development. This area, however, is not completely sub-sumed in IS security, as shown by the different responses for applications and systems development versus applications and systems development security. This indicates a degree of ambiguity as to what IS security includes. Areas receiving the least attention include physical security and operations security in both required and elective courses.
Secondly, it is worthy of note that the sum of these areas significantly exceeds the summary results shown in Table 5. We did not ask about topical coverage in non-IS courses. It does show, however, that more time is spent on secu-rity topics in elective courses versus those required of all students.
TABLE 1
Estimated Hours on Computer Security: Means
Total hours (Summary question)
M(using
midpoints) SD n p
IS required 10.82 9.06 59 <.001
IS elective 15.78 11.87 54 <.001
Non-IS 3.11 5.74 50 <.001
TABLE 2
Estimated Hours for IS Courses, by Subject Area
Required Elective
Subject area value n value n Total
Access control systems & methodology
3.68 51 5.30 47 8.97
Applications & systems development
17.38 58 12.19 50 29.57
Applications & systems development security
5.20 59 5.16 50 10.36
Business continuity planning 3.25 56 6.12 47 9.37
Cryptography and the use of encryption
3.13 57 6.34 48 9.48
Law, investigation, and ethics 4.99 58 5.57 50 10.56
Operations security 3.07 56 5.15 49 8.22
Physical security 2.74 56 4.00 49 6.74
Security architecture and models 3.76 56 6.71 50 10.47
Security management practices 4.34 57 6.71 51 11.05
Telecommunications, network, and internet security
7.58 58 10.03 51 17.61
Sum 59.12 73.28 132.40
Sum (without “Applications & systems development”)
41.74 61.09 102.83
Proposition 2: Adequacy of Coverage and Need for Change
Respondents were asked whether present coverage of com-puter security was adequate or if it should be changed. The respondents resoundingly indicated that current coverage is inadequate and should be increased. These results are shown in Figure 4. Fully 73% of respondents feel that coverage of security issues should be increased in presently required IS courses.
In an effort to see where the coverage of computer security is going, respondents were asked to predict what change they believe should happen over the next five years. Results are shown in Figure 5.
FIGURE 4 Adequacy of coverage.
FIGURE 5 Predicted change over the next five years.
TABLE 3
Percentage for Increase, by Time Period
Course Present n Next 5 years n
Required 73% 60 87% 60
Elective 65% 54 70% 53
Non-IS 52% 48 71% 48
With increased focus on security issues, Hypothesis 3a predicted that coverage of computer security issues would shift from elective courses to required courses. We felt that IS faculty would desire to increase security coverage in re-quired courses while at the same time decreasing the time spent in elective courses. This belief was partially correct: respondents reported a desire for increased coverage in re-quired courses, but did not report an accompanying desire for decreased coverage in elective courses. To the contrary, respondents saw the need for increases in all areas. A strong majority (87%) saw the need for increased coverage of com-puter security in the required IS curriculum over the next five years. This is accompanied by a full 70% desiring an increase in coverage in elective courses. Figure 5 and Table 3 summarize these results.
TABLE 4
Reasons for Lack of Coverage, Distribution of Opinions
Value
Faculty expertise
Curriculum full
1 Strongly disagree 2 1
2 Disagree 13 10
3 Slightly disagree 6 9
4 Slightly agree 13 9
5 Agree 19 13
6 Strongly agree 8 18
Total 61 60
Weighted average 3.95 4.28
124 C. B. FOLTZ AND J. S. RENWICK
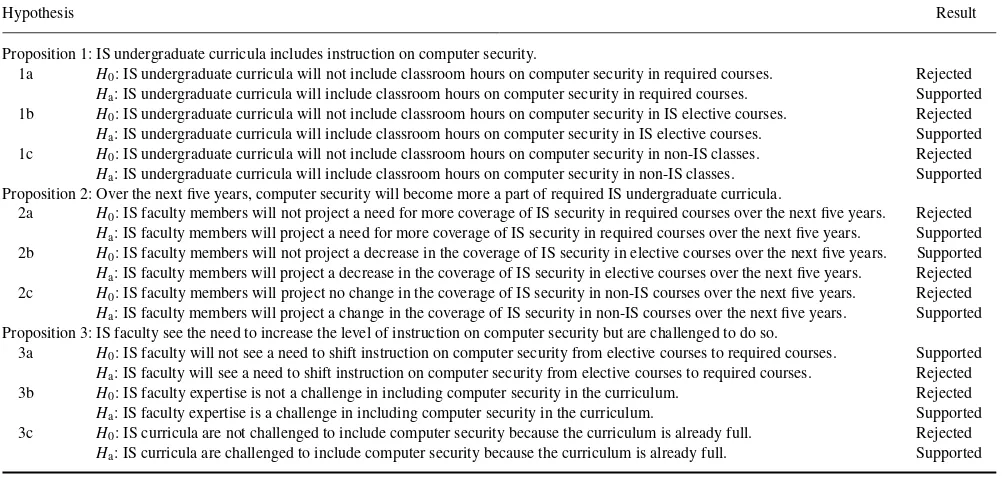
TABLE 5 Summary of Results
Hypothesis Result
Proposition 1: IS undergraduate curricula includes instruction on computer security.
1a H0: IS undergraduate curricula will not include classroom hours on computer security in required courses. Rejected
Ha: IS undergraduate curricula will include classroom hours on computer security in required courses. Supported
1b H0: IS undergraduate curricula will not include classroom hours on computer security in IS elective courses. Rejected
Ha: IS undergraduate curricula will include classroom hours on computer security in IS elective courses. Supported
1c H0: IS undergraduate curricula will not include classroom hours on computer security in non-IS classes. Rejected
Ha: IS undergraduate curricula will include classroom hours on computer security in non-IS classes. Supported
Proposition 2: Over the next five years, computer security will become more a part of required IS undergraduate curricula.
2a H0: IS faculty members will not project a need for more coverage of IS security in required courses over the next five years. Rejected
Ha: IS faculty members will project a need for more coverage of IS security in required courses over the next five years. Supported
2b H0: IS faculty members will not project a decrease in the coverage of IS security in elective courses over the next five years. Supported
Ha: IS faculty members will project a decrease in the coverage of IS security in elective courses over the next five years. Rejected
2c H0: IS faculty members will project no change in the coverage of IS security in non-IS courses over the next five years. Rejected
Ha: IS faculty members will project a change in the coverage of IS security in non-IS courses over the next five years. Supported
Proposition 3: IS faculty see the need to increase the level of instruction on computer security but are challenged to do so.
3a H0: IS faculty will not see a need to shift instruction on computer security from elective courses to required courses. Supported
Ha: IS faculty will see a need to shift instruction on computer security from elective courses to required courses. Rejected
3b H0: IS faculty expertise is not a challenge in including computer security in the curriculum. Rejected
Ha: IS faculty expertise is a challenge in including computer security in the curriculum. Supported
3c H0: IS curricula are not challenged to include computer security because the curriculum is already full. Rejected
Ha: IS curricula are challenged to include computer security because the curriculum is already full. Supported
Proposition 3: Reasons for Lack of Coverage
Hypotheses 3b and 3c addressed the challenges that faculty face in including IS security. Respondents tended to agree with the statements “The lack of faculty expertise in security makes it difficult to incorporate this topic in our curriculum” and “our curriculum is already full and there isn’t sufficient time to incorporate security issues.” Most respondents felt that a lack of time in the curriculum presented a greater challenge than lack of faculty expertise; however, 65% of respondents felt that a lack of expertise was an issue as well. Results are shown in Table 4
CONCLUSION
Results of this survey reveal some very interesting patterns. First of all, there was an overwhelming consensus among IS faculty that IS security needs to be addressed and that the present curricula are not meeting those needs, especially in the required courses (73% of respondents felt security is-sue coverage should be increased in currently required IS courses). Further, most respondents suggested a need for increased security coverage during the next five years in re-quired, elective, and non-IS courses. There is less consensus, however, as to what should actually be included in IS secu-rity coverage. The topical areas presently receiving the most attention include Applications and systems development and telecommunications, network and internet security, with each receiving more than seventeen hours of instruction. These are significantly greater than any other topic area. Security
man-agement practices, law, investigation and ethics, and security architecture and models are in a second tier, receiving 10–12 hrs of instruction. The area receiving the least attention is physical security. An extension of this project would be to further refine recommendations for IS security curriculum.
Another interesting result is the disparity between re-ported security coverage in the classroom. Respondents were asked to report the total hours spent on security as well as the number of hours spent on specific areas of security. Respon-dents reported a total of 26.6 hrs for instruction in security, the sum of hours spent on specific areas greatly exceeded this (the sum of hours reported is 102.83 after the removal of the Applications and systems development item). This in-consistency suggests that either respondents are unsure of the coverage within their own curriculum or that there is a large degree of overlap between these topic areas.
Unfortunately, respondents also noted that present curric-ula leave little time for additional topics. This lack of time may hinder efforts to add new material to the curriculum. The challenges of IS security, however, are an important is-sue that we and our students will continue to face. The need for additional instruction in this area cannot be disregarded. It is perhaps time to look to new teaching methods and ap-proaches to learning to increase both the breadth and depth of our student’s educational experience. While we cannot con-tinually add more content, we can make an effort to maximize their learning in a changing world.
This study extended previous research by providing a glimpse inside IS program classrooms. Whereas previous work looked primarily at external sources such as textbook reviews, catalogs, and external recommendations, our study
endeavored to ask faculty directly what was presently being taught. Our results go beyond textbooks to reflect what fac-ulty are including from more up-to-date resources. As the field of information systems continues to develop, it contin-ues to be important for faculty to remain current in the field and incorporate this knowledge in their teaching.
Future researchers should continue to examine IS security curricula content as well as how it relates to other fields such as computer science and information technology. As an evolving field, information systems must continue to examine content and coverage for currency. It should also endeavor to more clearly define topical areas in IS security. As mentioned previously, results suggest that either faculty members are unsure of the IS security coverage within their own curriculum or there is significant overlap between the topic areas. Further, the inclusion of these various IS secu-rity topic areas within the curriculum should be evaluated. Given the limited time available within the existing curricula and the importance of covering IS security, the model curricula needs to be revised to reflect these developments in the field.
REFERENCES
Anderson, J., & Schwager, P. (2002). Security in the information systems curriculum: Identification and status of relevant issues.Journal of Com-puter Information Systems,42(3), 16–23.
Carnevale, D. (2002, March 4). Software piracy seems rampant among students in a survey at 2 universities.The Chronicle of Higher
Educa-tion. Retrieved from http://chronicle.com/article/software-piracy-seems-rampant/114903
Cronan, T. P., Foltz, C. B., & Jones, T. (2006). Piracy, computer crime, and IS misuse at the university.Communications of the ACM,49(6), 84–90. Foltz, C. B., & Hauser, R. (2004). Faculty awareness of computer
secu-rity regulations.Proceedings of the Decision Sciences Institute, 4501– 4506.
Gorgone, J., Davis, G. B., Valacich, J. S., Topi, H., Feinstein, D. L., & Longenecker, H. E. (2002). IS 2002: Model curriculum and guidelines for undergraduate degree programs in information systems. Communi-cations for the Association for Information Systems,11. Retrieved from http://aisel.aisnet.org/cais/vol11/iss1/1
Gregory, P. (2003, January 24). Are security certifications worth it? Com-puterworld. Retrieved from http://www.comCom-puterworld.com/s/article/ 77849/Are security certifications worth it
Kung, M., Yang, S. C., & Ahang, Y. (2006). The changing information systems (IS) curriculum: A survey of undergraduate programs in the United States.Journal of Education for Business,81, 291–300. National Security Agency. (2009).National centers of academic
excel-lence. Retrieved from http://www.nsa.gov/ia/academic outreach/nat cae/ index.shtml
Prichard, J. J., & MacDonald, L. E. (2004). Cyber terrorism: A study of the extent of coverage in computer security textbooks.Journal of Information Technology Education,3, 279–289.
Richardson, R. (2007).2007 CSI computer crime and security survey. New York, NY: Computer Security Institute.
Sousa, K. J., MacDonald, L. E., & Fougere, K. T. (2005). Computer security in the introductory business information systems course: An exploratory study of textbook coverage. Journal of Education for Business, 81, 15–20.
Vaughn, J. R., & Boggess, J. E. III. (1999). Integration of computer secu-rity into the software engineering and computer science programs.The Journal of Systems and Software,49, 149–153.
Walters, L. M. (2007). A draft of an information systems security and control course.Journal of Information Systems,21(1), 123–148.