802.11® Wireless Networks The Definitive Guide
As we all know by now, wireless net works offer m any advant ages over fixed ( or wired) net works. Forem ost on t hat list is m obilit y, since going wireless frees you from t he t et her of an Et hernet cable at a desk. But t hat 's j ust t he t ip of t he cable- free iceberg. Wireless net works are also m ore flexible, fast er and easier for you t o use, and m ore affordable t o deploy and m aint ain.
The de fact o st andard for wireless net working is t he 802.11 prot ocol, which includes Wi- Fi ( t he wireless st andard known as 802.11b) and it s fast er cousin, 802.11g. Wit h easy- t o- inst all 802.11 net work hardware available everywhere you t urn, t he choice seem s sim ple, and m any people dive int o wireless com put ing wit h less t hought and planning t han t hey'd give t o a wired net work. But it 's wise t o be fam iliar wit h bot h t he capabilit ies and risks associat ed wit h t he 802.11 prot ocols. And
802.11 Wireless Net w orks: The Definit ive Guide, 2nd Edit ion is t he perfect place t o st art .
This updat ed edit ion covers everyt hing you'll ever need t o know about wireless t echnology.
Designed wit h t he syst em adm inist rat or or serious hom e user in m ind, it 's a no- nonsense guide for set t ing up 802.11 on Windows and Linux. Am ong t he wide range of t opics covered are discussions on:
deploym ent considerat ions
net work m onit oring and perform ance t uning wireless securit y issues
how t o use and select access point s net work m onit oring essent ials wireless card configurat ion
securit y issues unique t o wireless net works
Wit h wireless t echnology, t he advant ages t o it s users are indeed plent iful. Com panies no longer have t o deal wit h t he hassle and expense of wiring buildings, and households wit h several com put ers can avoid fight s over who's online. And now, wit h 802.11 Wireless Net w orks: The
Definit ive Guide, 2nd Edit ion, you can int egrat e wireless t echnology int o your current infrast ruct ure
wit h t he ut m ost confidence.
As we all know by now, wireless net works offer m any advant ages over fixed ( or wired) net works. Forem ost on t hat list is m obilit y, since going wireless frees you from t he t et her of an Et hernet cable at a desk. But t hat 's j ust t he t ip of t he cable- free iceberg. Wireless net works are also m ore flexible, fast er and easier for you t o use, and m ore affordable t o deploy and m aint ain.
The de fact o st andard for wireless net working is t he 802.11 prot ocol, which includes Wi- Fi ( t he wireless st andard known as 802.11b) and it s fast er cousin, 802.11g. Wit h easy- t o- inst all 802.11 net work hardware available everywhere you t urn, t he choice seem s sim ple, and m any people dive int o wireless com put ing wit h less t hought and planning t han t hey'd give t o a wired net work. But it 's wise t o be fam iliar wit h bot h t he capabilit ies and risks associat ed wit h t he 802.11 prot ocols. And
802.11 Wireless Net w orks: The Definit ive Guide, 2nd Edit ion is t he perfect place t o st art .
This updat ed edit ion covers everyt hing you'll ever need t o know about wireless t echnology.
Designed wit h t he syst em adm inist rat or or serious hom e user in m ind, it 's a no- nonsense guide for set t ing up 802.11 on Windows and Linux. Am ong t he wide range of t opics covered are discussions on:
deploym ent considerat ions
net work m onit oring and perform ance t uning wireless securit y issues
how t o use and select access point s net work m onit oring essent ials wireless card configurat ion
securit y issues unique t o wireless net works
Wit h wireless t echnology, t he advant ages t o it s users are indeed plent iful. Com panies no longer have t o deal wit h t he hassle and expense of wiring buildings, and households wit h several com put ers can avoid fight s over who's online. And now, wit h 802.11 Wireless Net w orks: The
Definit ive Guide, 2nd Edit ion, you can int egrat e wireless t echnology int o your current infrast ruct ure
802.11® Wireless Networks The Definitive Guide
Prometheus Untethered: The Possibilities of Wireless LANs Audience IEEE 802 Network Technology Family Tree 802.11 Nomenclature and Design
Encapsulation of Higher-Layer Protocols Within 802.11 Contention-Based Data Service
Frame Transmission and Association and Authentication States Chapter 5. Wired Equivalent Privacy (WEP)
Dynamic WEP The Temporal Key Integrity Protocol (TKIP)
Chapter 15. A Peek Ahead at 802.11n: MIMO-OFDM
802.11 Performance Calculations Improving Performance
Tunable 802.11 Parameters
Chapter 26. Conclusions and Predictions Standards Work
Current Trends in Wireless Networking The End
glossary
8 0 2 .1 1 ® W ir e le ss N e t w or k s: Th e D e fin it ive Gu ide , Se con d Edit ion
by Mat t hew S. Gast
Copyright © 2005 Mat t hew S. Gast . All right s reserved. Print ed in t he Unit ed St at es of Am erica.
Published by O'Reilly Media, I nc., 1005 Gravenst ein Highway Nort h, Sebast opol, CA 95472.
O'Reilly books m ay be purchased for educat ional, business, or sales prom ot ional use. Online edit ions are also available for m ost t it les (safari.oreilly.com) . For m ore inform at ion, cont act our
corporat e/ inst it ut ional sales depart m ent : ( 800) 998- 9938 or corporat [email protected].
Edit or : Mike Loukides
Pr odu ct ion Edit or : Colleen Gorm an
Cove r D e sign e r : Ellie Volckhausen
I n t e r ior D e sign e r : David Fut at o
Pr in t in g H ist or y:
April 2002: First Edit ion.
April 2005: Second Edit ion.
Nut shell Handbook, t he Nut shell Handbook logo, and t he O'Reilly logo are regist ered t radem arks of O'Reilly Media, I nc. 802.11® Wireless Net w orks: The Definit ive Guide, Second Edit ion, t he im age of a horseshoe bat , and relat ed t rade dress are t radem arks of O'Reilly Media, I nc.
802.11® and all 802.11- based t radem arks and logos are t radem arks or regist ered t radem arks of I EEE, I nc. in t he Unit ed St at es and ot her count ries. O'Reilly Media, I nc. is independent of I EEE. Many of t he designat ions used by m anufact urers and sellers t o dist inguish t heir product s are claim ed as t radem arks. Where t hose designat ions appear in t his book, and O'Reilly Media, I nc. was aware of a t radem ark claim , t he designat ions have been print ed in caps or init ial caps.
While every precaut ion has been t aken in t he preparat ion of t his book, t he publisher and aut hor assum e no responsibilit y for errors or om issions, or for dam ages result ing from t he use of t he inform at ion cont ained herein.
Foreword
Mat t hew Gast was m y m ent or long before I m et him . I began report ing on wireless dat a net working in Oct ober 2000 when I discovered t hat Apple's claim s for it s 802.11b- based AirPort Base St at ion were act ually t rue.
I 'd been burned wit h anot her form of wireless net working t hat used infrared, and had spent m any fruit less hours using ot her " int erest ing" net working t echnologies t hat led t o dead ends. I figured 802.11b was j ust anot her one. Was I glad I was wrong! expanding WDS int o Wireless Dist ribut ion Syst em int o underst anding precisely how t wo access point s could exchange dat a wit h each ot her t hrough a built - in 802.11 m echanism t hat allowed four part ies t o a packet 's t ransit .
Now as t im e went by and t he 802.11 fam ily grew and becam e baroque, t he first edit ion of t his t it le st art ed feeling a lit t le out of dat ealt hough it rem ained surprising how m any " new" innovat ions were firm ly root ed in developm ent s of t he early t o m id- 1990s. The alphabet soup of t he first edit ion was gruel com pared t o t he m ulligat awny of 2005.
Mat t hew filled t he gap bet ween t he book and cont em porary wireless realit y t hrough his ongoing writ ing at O'Reilly's Wireless DevCent er, which I read avidly. And som ewhere in t here I was
int roduced t o Mat t hew at a Wi- Fi Planet conference. We hit it off im m ediat ely: I st art ed pest ering him for det ails about 802.1X, if I rem em ber correct ly, and he want ed t o t alk about books and business. ( I wound up writ ing t wo edit ions of a general m arket Wi- Fi book, neit her of which did nearly as well as Mat t hew's ext raordinarily t echnical one.)
Since t hen, I have been in t he rare and privileged posit ion t o be t he recipient of Mat t hew's generosit y wit h his knowledge and hum ble insight . Mat t hew isn't one who assum es; he researches. His nat ural curiosit y com pels him t o dig unt il he get s an answer t hat 's t echnically and logically consist ent .
Take, for inst ance, t he incredibly polit ical and com plicat ed evolut ion of t he 802.1X st andard. ( I know, from Mat t hew, t hat it 's properly capit alized since it 's a freest anding st andard not reliant on ot her specificat ions. Even t he I EEE m akes t his m ist ake, and it 's t heir rule for capit alizat ion t hat we're bot h following.)
802.1X is sim ple enough in it s use of t he Ext ensible Aut hent icat ion Prot ocol, a generic m et hod of passing m essages am ong part ies t o aut hent icat ion. But t he ways in which EAP is secured are, quit e frankly, insanereflect ing Microsoft and Cisco's parallel but conflict ing at t em pt s t o cont rol support of legacy prot ocols in a way t hat only dam ages easy access t o it s higher level of securit y.
int eroperabilit y issues in an O'Reilly Net work art icle t hat 's t he nugget of t he expanded coverage in t his book. I defy any reader t o find as cogent and exhaust ive an explanat ion before t his book was published. There's not hing as clear, com prehensive, and unaffect ed by m arket polit ics.
At t im es, Mat t hew bem oaned t he delays t hat led t o t he gap bet ween edit ions of t his book, due part ly t o his j oining a st art up wireless LAN swit ch com pany, but I t hink readers are bet t er served t hrough his very hard- won, lat e- night , long- hours knowledge.
Mat t hew's relat ionship wit h 802.11 m ight have previously been considered t hat of a handy m an who knew his way around t he infrast ruct ure of his house. I f a t oilet was running, he could replace a valve. I f t he living room needed new out let s, he could research t he process and wire t hem in.
But Mat t hew's new j ob t ook him allegorically from a weekend household warrior t o a j ack- of- all-t radesm an. Maall-t all-t hew can all-t ear ouall-t all-t hose inner walls, refram e, plum b, and wire all-t hem , all all-t he while bit ching about t he local building code.
I t 's been a pleasure knowing Mat t hew, and it 's even m ore a pleasure t o int roduce you t o his book, and let you all in on what I and ot hers have been m ore privat e recipient s of for t he last few years. Glenn Fleishm an
Seat t le, Washingt on
Preface
People m ove. Net works don't .
More t han anyt hing else, t hese t wo st at em ent s can explain t he explosion of wireless LAN hardware. I n j ust a few years, wireless LANs have grown from a high- priced, alpha- geek curiosit y t o
m ainst ream t echnology.
By rem oving t he net work port from t he equat ion, wireless net works separat e user connect ivit y from a direct physical locat ion at t he end of a cord. To abst ract t he user locat ion from t he net work, however, requires a great deal of prot ocol engineering. For users t o have locat ion- independent services, t he net work m ust becom e m uch m ore aware of t heir locat ion.
This book has been writ t en on m ore airplanes, in m ore airport s, and on m ore t rains t han I care t o count . Much of t he research involved in dist illing evolving net work t echnology int o a book depends on I nt ernet access. I t is safe t o say t hat wit hout ubiquit ous net work access, t he arrival of t his book would have been m uch delayed.
Prometheus Untethered: The Possibilities of Wireless
LANs
Wireless net works offer several advant ages over fixed ( or " wired" ) net works:
Mobilit y
Users m ove, but dat a is usually st ored cent rally, enabling users t o access dat a while t hey are in m ot ion can lead t o large product ivit y gains. Net works are built because t hey offer valuable services t o users. I n t he past , net work designers have focused on working wit h net work port s because t hat is what t ypically m aps t o a user. Wit h wireless, t here are no port s, and t he net work can be designed around user ident it y.
Ease and speed of deploym ent
Many areas are difficult t o wire for t radit ional wired LANs. Older buildings are oft en a problem ; running cable t hrough t he walls of an older st one building t o which t he blueprint s have been lost can be a challenge. I n m any places, hist oric preservat ion laws m ake it difficult t o carry out new LAN inst allat ions in older buildings. Even in m odern facilit ies, cont ract ing for cable
inst allat ion can be expensive and t im e- consum ing.
Flexibilit y
No cables m eans no recabling. Wireless net works allow users t o quickly form am orphous, sm all group net works for a m eet ing, and wireless net working m akes m oving bet ween cubicles and offices a snap. Expansion wit h wireless net works is easy because t he net work m edium is already everywhere. There are no cables t o pull, connect , or t rip over. Flexibilit y is t he big selling point for t he " hot spot " m arket , com posed m ainly of hot els, airport s, t rain st at ions ( and even t rains t hem selves! ) , libraries, and cafes.
Cost
I n som e cases, cost s can be reduced by using wireless t echnology. As an exam ple, 802.11® equipm ent can be used t o creat e a wireless bridge bet ween t wo buildings. Set t ing up a wireless bridge requires som e init ial capit al cost in t erm s of out door equipm ent , access point s, and wireless int erfaces. Aft er t he init ial capit al expendit ure, however, an 802.11- based, line- of-sight net work will have only a negligible recurring m ont hly operat ing cost . Over t im e, point - t o-point wireless links are far cheaper t han leasing capacit y from t he t elephone com pany.
Unt il t he com plet ion of t he 802.11 st andard in 1997, however, users want ing t o t ake advant age of t hese at t ribut es were forced t o adopt single- vendor solut ions wit h all of t he risk t hat ent ailed. Once 802.11 st art ed t he ball rolling, speeds quickly increased from 2 Mbps t o 11 Mbps t o 54 Mbps.
Several service providers have j um ped at t he idea, and ent husiast ic bands of volunt eers in m ost m aj or cit ies have st art ed t o build public wireless net works based on 802.11.
Audience
This book is int ended for readers who need t o learn m ore about t he t echnical aspect s of wireless LANs, from operat ions t o deploym ent t o m onit oring:
Net work archit ect s cont em plat ing rolling out 802.11 equipm ent ont o net works or building net works based on 802.11
Net work adm inist rat ors responsible for building and m aint aining 802.11 net works
Securit y professionals concerned about t he exposure from deploym ent of 802.11 equipm ent and int erest ed in m easures t o reduce t he securit y headaches
Overture for Book in Black and White, Opus 2
Part of t he difficult y in writ ing a book on a t echnology t hat is evolving quickly is t hat you are never quit e sure what t o include. The years bet ween t he first and second edit ion were filled wit h m any developm ent s in securit y, and updat ing t he securit y- relat ed inform at ion was one of t he m aj or part s of t his revision. This book has t wo m ain purposes: it is m eant t o t each t he reader about t he 802.11 st andard it self, and it offers pract ical advice on building wireless LANs wit h 802.11 equipm ent . These t wo purposes are m eant t o be independent of each ot her so you can easily find what int erest s you. To help you decide what t o read first and t o give you a bet t er idea of t he layout , t he following are brief sum m aries of all t he chapt ers.
Chapt er 1, I nt roduct ion t o Wireless Net w orking, list s ways in which wireless net works are different from t radit ional wired net works and discusses t he challenges faced when adapt ing t o fuzzy
boundaries and unreliable m edia. Wireless LANs are perhaps t he m ost int erest ing illust rat ion of Christ ian Huit em a's assert ion t hat t he I nt ernet has no cent er, j ust an ever- expanding edge. Wit h wireless LAN t echnology becom ing com m onplace, t hat edge is now blurring.
Chapt er 2, Overview of 802.11 Net works, describes t he overall archit ect ure of 802.11 wireless LANs. 802.11 is som ewhat like Et hernet but wit h a num ber of new net work com ponent s and a lot of new acronym s. This chapt er int roduces you t o t he net work com ponent s t hat you'll work wit h. Broadly speaking, t hese com ponent s are st at ions ( m obile devices wit h wireless cards) , access point s
( glorified bridges bet ween t he st at ions and t he dist ribut ion syst em ) , and t he dist ribut ion syst em it self ( t he wired backbone net work) . St at ions are grouped logically int o Basic Service Set s ( BSSs) . When no access point is present , t he net work is a loose, ad- hoc confederat ion called an independent BSS ( I BSS) . Access point s allow m ore st ruct ure by connect ing disparat e physical BSSs int o a furt her logical grouping called an Ext ended Service Set ( ESS) .
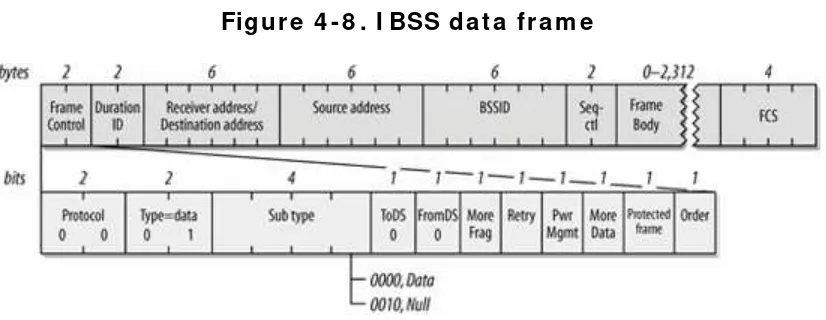
Chapt er 3, 802.11 MAC Fundam ent als, describes t he Media Access Cont rol ( MAC) layer of t he 802.11 st andard in det ail. 802.11, like all I EEE 802 net works, split s t he MAC- layer funct ionalit y from t he physical m edium access. Several physical layers exist for 802.11, but t he MAC is t he sam e across all of t hem . The m ain m ode for accessing t he net work m edium is a t radit ional cont ent ion- based access m et hod, t hough it em ploys collision avoidance ( CSMA/ CA) rat her t han collision det ect ion ( CSMA/ CD) . The chapt er also discusses dat a encapsulat ion in 802.11 fram es and helps net work adm inist rat ors underst and t he fram e sequences used t o t ransfer dat a.
Chapt er 4, 802.11 Fram ing in Det ail, builds on t he end of Chapt er 3 by describing t he various fram e t ypes and where t hey are used. This chapt er is int ended m ore as a reference t han act ual reading m at erial. I t describes t he t hree m aj or fram e classes. Dat a fram es are t he workhorse of 802.11. Cont rol fram es serve supervisory purposes. Managem ent fram es assist in perform ing t he ext ended operat ions of t he 802.11 MAC. Beacons announce t he exist ence of an 802.11 net work, assist in t he associat ion process, and are used for aut hent icat ing st at ions.
Chapt er 5, Wired Equivalent Privacy ( WEP), describes t he Wired Equivalent Privacy prot ocol. I n spit e of it s flaws, WEP is t he basis for m uch of t he following work in wireless LAN securit y. This chapt er discusses what WEP is, how it works, and why you can't rely on it for any m eaningful privacy or securit y.
Chapt er 7, 802.11i: Robust Securit y Net w orks, TKI P, and CCMP, describes t he 802.11i st andard for wireless LAN securit y. I n recognit ion of t he fundam ent al flaws of WEP, t wo new link- layer encrypt ion prot ocols were designed, com plet e wit h new m echanism s t o derive and dist ribut e keys.
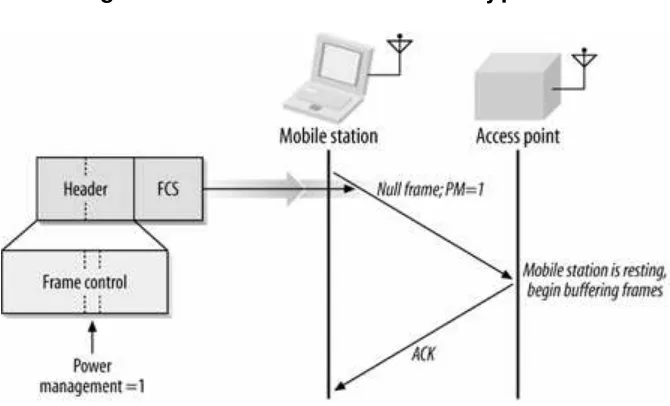
Chapt er 8, Managem ent Operat ions, describes t he m anagem ent operat ions on 802.11 net works. To find net works t o j oin, st at ions scan for act ive net works announced by access point s or t he I BSS creat or. Before sending dat a, st at ions m ust associat e wit h an access point . This chapt er also discusses t he power- m anagem ent feat ures incorporat ed int o t he MAC t hat allow bat t ery- powered st at ions t o sleep and pick up buffered t raffic at periodic int ervals.
Chapt er 9, Cont ent ion- Free Service w it h t he PCF, describes t he point coordinat ion funct ion. The PCF is not widely im plem ent ed, so t his chapt er can be skipped for m ost purposes. The PCF is t he basis for cont ent ion- free access t o t he wireless m edium . Cont ent ion- free access is like a cent rally cont rolled, t oken- based m edium , where access point s provide t he " t oken" funct ion.
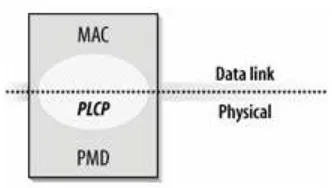
Chapt er 10, Physical Layer Overview, describes t he general archit ect ure of t he physical layer ( PHY) in t he 802.11 m odel. The PHY it self is broken down int o t wo " sublayers." The Physical Layer
Convergence Procedure ( PLCP) adds a pream ble t o form t he com plet e fram e and it s own header, while t he Physical Medium Dependent ( PMD) sublayer includes m odulat ion det ails. The m ost com m on PHYs use radio frequency ( RF) as t he wireless m edium , so t he chapt er closes wit h a short discussion on RF syst em s and t echnology t hat can be applied t o any PHY discussed in t he book.
Chapt er 11, The Frequency- Hopping ( FH) PHY, describes t he oldest physical layer wit h 802.11. Product s based on t he FH PHY are no longer widely sold, but a great deal of early 802.11 equipm ent was based on t hem . Organizat ions wit h a long hist ory of involvem ent wit h 802.11 t echnology m ay need t o be fam iliar wit h t his PHY.
Chapt er 12, The Direct Sequence PHYs: DSSS and HR/ DSSS ( 802.11b), describes t wo physical layers based on direct sequence spread spect rum t echnology. The init ial 802.11 st andard included a layer which offered speeds of 1 Mbps and 2 Mbps. While int erest ing, it was not unt il 802.11b added 5.5 Mbps and 11 Mbps dat a rat es t hat t he t echnology really t ook off. This chapt er describes t he t wo closely- relat ed PHYs as a single package.
Chapt er 13, 802.11a and 802.11j : 5- GHz OFDM PHY, describes t he 5- GHz PHY st andardized wit h 802.11a, which operat es at 54 Mbps. This physical layer uses anot her m odulat ion t echnique known as ort hogonal frequency division m ult iplexing ( OFDM) . Slight m odificat ions were required t o use t his PHY in Japan, which were m ade by t he 802.11j st andard.
Chapt er 14, 802.11g: The Ext ended- Rat e PHY ( ERP), describes a PHY which uses OFDM t echnology, but in t he 2.4 GHz frequency band shared by 802.11b. I t has largely supplant ed 802.11b, and is a com m on opt ion for built - in connect ivit y wit h new not ebook com put ers. The PHY it self is alm ost ident ical t o t he 802.11a PHY. The differences are in allowing for backwards com pat ibilit y wit h older equipm ent sharing t he sam e frequency band.
Chapt er 15, A Peek Ahead at 802.11n: MI MO- OFDM, describes t he PHY current ly in developm ent . 802.11n uses a PHY based on m ult iple- input / m ult iple- out put ( MI MO) t echnology for m uch higher speed. At t he t im e t his book went t o press, t wo proposed st andards were dueling in t he com m it t ee. This chapt er describes bot h.
Chapt er 16, 802.11 Hardw are, begins t he t ransit ion from t heoret ical m at t ers based on t he st andards t o how t he st andards are im plem ent ed. 802.11 is a relat ively loose st andard, and allows a large num ber of im plem ent at ion choices. Cards m ay differ in t heir specified perform ance, or in t he m anner in which cert ain prot ocols are im plem ent ed. Many of t hese variat ions are based on how t hey are built .
Chapt er 18, 802.11 on t he Macint osh, describes how t o use t he AirPort card on MacOS X t o connect t o 802.11 net works. I t focuses on Mac OS X 10.3, which was t he first soft ware version t o include 802.1X support .
Chapt er 19, Using 802.11 on Linux, discusses how t o inst all 802.11 support on a Linux syst em . Aft er discussing how t o add PC Card support t o t he operat ing syst em , it shows how t o use t he wireless ext ensions API . I t discusses t wo com m on drivers, one for t he older Orinoco 802.11b card, and t he MADwifi driver for newer cards based on chipset s from At heros Com m unicat ions. Finally, it shows how t o configure 802.1X securit y using xsupplicant .
Chapt er 20, Using 802.11 Access Point s, describes t he equipm ent used on t he infrast ruct ure end of 802.11 net works. Com m ercial access point product s have varying feat ures. This chapt er describes t he com m on feat ures of access point s, offers buying advice, and present s t wo pract ical configurat ion exam ples.
Chapt er 21, Logical Wireless Net work Archit ect ure, m arks t he t hird t ransit ion in t he book, from t he im plem ent at ion of 802.11 on t he scale of an individual device, t o how t o build 802.11 net works on a larger scale. There are several m aj or st yles t hat can be used t o build t he net work, each wit h it s advant ages and disadvant ages. This chapt er sort s t hrough t he com m on t ypes of net work t opologies and offers advice on select ing one.
Chapt er 22, Securit y Archit ect ure, should be read in t andem wit h t he previous chapt er. Maint aining net work securit y while offering net work access on an open m edium is a m aj or challenge. Securit y choices and archit ect ure choices are m ut ually influent ial. This chapt er addresses t he m aj or choices t o be m ade in designing a net work: what t ype of aut hent icat ion will be used and how it int egrat es wit h exist ing user dat abases, how t o encrypt t raffic t o keep it safe, and how t o deal wit h unaut horized access point deploym ent .
Chapt er 23, Sit e Planning and Proj ect Managem ent, is t he final com ponent of t he book for net work adm inist rat ors. Designing a large- scale wireless net work is difficult because t here is great user dem and for access. Ensuring t hat t he net work has sufficient capacit y t o sat isfy user dem ands in all t he locat ions where it will be used requires som e planning. Choosing locat ions for access point s depends a great deal on t he radio environm ent , and has t radit ionally been one of t he m ost t im e-consum ing t asks in building a net work.
Chapt er 24, 802.11 Net w ork Analysis, t eaches adm inist rat ors how t o recognize what 's going on wit h t heir wireless LANs. Net work analyzers have proven t heir wort h t im e and t im e again on wired net works. Wireless net work analyzers are j ust as valuable a t ool for 802.11 net works. This chapt er discusses how t o use wireless net work analyzers and what cert ain sym pt om s m ay indicat e. I t also describes how t o build an analyzer using Et hereal, and what t o look for t o t roubleshoot com m on problem s.
Chapt er 25, 802.11 Perform ance Tuning, describes how net work adm inist rat ors can increase t hroughput . I t begins by describing how t o calculat e overall t hroughput for payload dat a, and com m on ways of increasing perform ance. I n rare cases, it m ay m ake sense t o change com m only exposed 802.11 param et ers.
Chapt er 26, Conclusions and Predict ions, sum m arizes current st andards work in t he 802.11 working group. Aft er sum m arizing t he work in progress, I get t o prognost icat e and hope t hat I don't have t o revise t his t oo ext ensively in fut ure edit ions.
Major Changes from the First Edition
t echnology pat h of " fast er, bet t er, and cheaper," t he dat a rat e of m ost 802.11 int erfaces has shot from 2 or 11 Mbps wit h 802.11b t o 54 Mbps wit h 802.11a and 802.11g. I ncreased speed wit h backwards com pat ibilit y has proved t o be a com m ercially successful form ula for 802.11g, even if it has lim it at ions when used for large- scale net works. The com ing st andardizat ion of 802.11n is set t o boost speeds even fart her. New developm ent s in PHY t echnology are anxiously await ed by users, as shown by t he popular releases of pre- st andard t echnology. Two ent irely new chapt ers are devot ed t o 802.11g and 802.11n. European adopt ion of 802.11a was cont ingent on t he developm ent of
spect rum m anagem ent in 802.11h, which result ed in ext ensive revisions t o t he m anagem ent chapt er.
When t he first edit ion was released in 2002, t he percept ion of insecurit y dom inat ed discussions of t he t echnology. WEP was clearly insufficient , but t here was no good alt ernat ive. Most net work
adm inist rat ors were m aking do wit h rem ot e access syst em s t urned inward, rat her t han t heir nat ural out ward orient at ion. The developm ent of 802.11i was done a great deal t o sim plify net work securit y. Securit y is now built in t o t he specificat ion, rat her t han som et hing which m ust be added on aft er get t ing t he net work right . Securit y im provem ent s perm eat e t he book, from new chapt ers showing how t he new prot ocols work, t o showing how t hey can be used on t he client side, t o how t o sort t hrough different opt ions when building a net work. Sort ing t hrough securit y opt ions is m uch m ore com plex now t han it was t hree years ago, and m ade it necessary t o expand a sect ion of t he deploym ent discussion in t he first edit ion int o it s own chapt er.
Conventions Used in This Book
I t alic is used for:
Pat hnam es, filenam es, class nam es, and direct ories New t erm s where t hey are defined
I nt ernet addresses, such as dom ain nam es and URLs
Bold is used for:
GUI com ponent s
Constant Width is used for:
Com m and lines and opt ions t hat should be t yped verbat im on t he screen All code list ings
Constant Width Italic is used for:
General placeholders t hat indicat e t hat an it em should be replaced by som e act ual value in your own program
Constant Width Bold is used for:
Text t hat is t yped in code exam ples by t he user
I ndicat es a t ip, suggest ion, or general not e
How to Contact Us
Please address com m ent s and quest ions concerning t his book t o t he publisher: O'Reilly Media, I nc.
1005 Gravenst ein Highway Nort h Sebast opol, CA 95472
( 800) 998- 9938 ( in t he U.S. or Canada) ( 707) 829- 0515 ( int ernat ional/ local) ( 707) 829- 0104 ( fax)
There is a web sit e for t he book, where errat a and any addit ional inform at ion will be list ed. You can access t his page at :
http://www.oreilly.com/catalog/802dot112/
I n a fast - m oving field, sm aller art icles bridge t he gap bet ween cont em porary pract ice and t he last version of t he print ed book. You can access m y weblog and art icles at :
http://weblogs.oreillynet.com/pub/au/692/
To com m ent or ask t echnical quest ions about t his book, send em ail t o:
For m ore inform at ion about our books, conferences, soft ware, Resource Cent ers, and t he O'Reilly Net work, see our web sit e at :
Safari Enabled
When you see a Safari® Enabled icon on t he cover of your favorit e t echnology book, it m eans t he book is available online t hrough t he O'Reilly Net work Safari Bookshelf.
Safari offers a solut ion t hat 's bet t er t han e- books. I t 's a virt ual library t hat let s you easily search t housands of t op t echnology books, cut and past e code sam ples, download chapt ers, and find quick answers when you need t he m ost accurat e, current inform at ion. Try it for free at
Acknowledgments
As m uch as I would like t o believe t hat you are reading t his book for it s ent ert ainm ent value, I know bet t er. Technical books are valued because t hey get t he det ails right , and convey t hem in an easier fashion t han t he unadorned t echnical specificat ion. Behind every t echnical book, t here is a review t eam t hat saw t he first draft and helped t o im prove it . My review t eam caught num erous m ist akes and m ade t he book significant ly bet t er. Dr. Malik Audeh of Tropos Net works is, for lack of a bet t er t erm , m y radio conscience. I am no radio expert what I know about radio, I learned because of m y int erest in 802.11. Malik knew radio t echnology before 802.11, and I have been privileged t o share in his insight . Gerry Creager of Texas A&M offered insight int o t he FCC rules and regulat ions for
unlicensed devices, which was valuable because wireless LANs have been upending t he rules in recent years. When Glenn Fleishm an agreed t o writ e t he foreword, I had no idea t hat he would offer so m uch help in placing 802.11 wit hin it s larger cont ext . Many of t he det ails he suggest ed were references t o art icles t hat had run in t he past years on his own Wi- Fi Net working News sit e. As a writ er him self, Glenn also point ed out several locat ions where bet t er exam ples would m ake m y point s m uch clearer. Finally, Terry Sim ons of t he Open1X proj ect has worked ext ensively wit h 802.11 on Linux, and wit h nearly every 802.1X supplicant on t he m aj or operat ing syst em s. Terry also is one of t he archit ect s of t he wireless aut hent icat ion syst em at t he Universit y of Ut ah. His expert ise can be felt t hroughout t he early part of t he book on securit y specificat ions, as well as in t he pract ical m at t er of using supplicant s and building an aut hent icat ion syst em .
I am also indebt ed t o m any ot hers who help keep m e abreast of current developm ent s in 802.11, and share t heir knowledge wit h m e. Since 2002, I have been privileged t o part icipat e in t he I nt erop Labs init iat ives relat ed t o wireless securit y and 802.1X. The real world is far t oo m essy for t he classroom . Every year, I learn m ore about t he st at e of t he art by volunt eering t han I ever could by t aking a prepared class. Through t he I nt erop Labs, I m et Chris Hessing, t he developm ent lead for xsupplicant . Chris has always generously explained how all t he keying bit s m ove around in 802.11, which is no sm all feat ! Sudheer Mat t a, a colleague of m ine, always has t im e t o explain what is happening in t he st andards world, and how t he m inut e det ails of t he MAC work.
The large support ing cast at O'Reilly was t rem endously helpful in a wide variet y of ways. Ellie Volckhausen designed a st unning cover t hat has adorned m y cubicle as well as m ost of t he personal elect ronics devices I own since 2001, when I began writ ing t he first edit ion. ( I t even looks good as ways I have been accust om ed t o from our past collaborat ions, and his background as a ham radio operat or proved especially useful when I st art ed writ ing about t he dark and forbidding world of ant ennas and RF t ransm ission. ( Am ong m any, m any ot her it em s, you have him t o t hank for t he foot not e on t he gain of t he Aricebo radio t elescope! )
or an econom ist gift ed wit h t he abilit y t o explain com plex subj ect s t o his st udent s. Dr. Bat em an is not shackled by his narrow academ ic expert ise. During t he preparat ion of t he second edit ion of t his book, I at t ended a lect ure of his about t he social hist ory of m y alm a m at er. I n a capt ivat ing hour, he t raced t he hist ory of t he inst it ut ion and it s int ersect ion wit h wider social m ovem ent s, which explained it s present - day cult ure in far m ore dept h t han I ever appreciat ed while a st udent . Not all professors t each t o prepare st udent s for graduat e school, and not all professors confine t heir t eaching t o t he classroom . I am a far bet t er writ er, econom ist , and cit izen for his influence.
When writ ing a book, it is easy t o acknowledge t he t angible cont ribut ions of ot hers. Behind every aut hor, t hough, t here is a support ive cast of relat ives and friends. As always, m y wife Ali cont inued t o indulge m y writ ing habit wit h ext rem ely good hum or, especially considering t he num ber of
weekends t hat were sacrificed t o t his book. Many of m y friends inform ally support ed t his proj ect wit h a great deal of encouragem ent and support ; m y t hanks m ust go t o ( in alphabet ical order) Annie, Aram azd, Brian, Dam eon, Kevin, and Nick.
Mat t hew Gast
San Francisco, California
Chapter 1. Introduction to Wireless
Networking
Over t he past five years, t he world has becom e increasingly m obile. As a result , t radit ional ways of net working t he world have proven inadequat e t o m eet t he challenges posed by our new collect ive lifest yle. I f users m ust be connect ed t o a net work by physical cables, t heir m ovem ent is dram at ically reduced. Wireless connect ivit y, however, poses no such rest rict ion and allows a great deal m ore free m ovem ent on t he part of t he net work user. As a result , wireless t echnologies are encroaching on t he t radit ional realm of " fixed" or " wired" net works. This change is obvious t o anybody who drives on a regular basis. One of t he " life and deat h" challenges t o t hose of us who drive on a regular basis is t he daily gaunt let of errat ically driven cars cont aining m obile phone users in t he driver's seat .
Wireless connect ivit y for voice t elephony has creat ed a whole new indust ry. Adding m obile connect ivit y int o t he m ix for t elephony has had profound influences on t he business of delivering voice calls because callers could be connect ed t o people, not devices. We are on t he cusp of an equally profound change in com put er net working. Wireless t elephony has been successful because it enables people t o connect wit h each ot her regardless of locat ion. New t echnologies t arget ed at com put er net works prom ise t o do t he sam e for I nt ernet connect ivit y. The m ost successful wireless dat a net working t echnology t his far has been 802.11.
Why Wireless?
To dive int o a specific t echnology at t his point is get t ing a bit ahead of t he st ory, t hough. Wireless net works share several im port ant advant ages, no m at t er how t he prot ocols are designed, or even what t ype of dat a t hey carry.
The m ost obvious advant age of wireless net working is m obilit y. Wireless net work users can connect t o exist ing net works and are t hen allowed t o roam freely. A m obile t elephone user can drive m iles in t he course of a single conversat ion because t he phone connect s t he user t hrough cell t owers.
I nit ially, m obile t elephony was expensive. Cost s rest rict ed it s use t o highly m obile professionals such as sales m anagers and im port ant execut ive decision m akers who m ight need t o be reached at a m om ent 's not ice regardless of t heir locat ion. Mobile t elephony has proven t o be a useful service, however, and now it is relat ively com m on in t he Unit ed St at es and ext rem ely com m on am ong Eur opeans.[ * ]
[*] While most of my colleagues, acquaintances, and family in the U.S. have mobile telephones, it is still possible to be a holdout.
In Europe, it seems as if everybody has a mobile phoneone cab driver in Finland I spoke with while writing the first edition of this book took great pride in the fact that his family of four had six mobile telephones!
Likewise, wireless dat a net works free soft ware developers from t he t et hers of an Et hernet cable at a desk. Developers can work in t he library, in a conference room , in t he parking lot , or even in t he coffee house across t he st reet . As long as t he wireless users rem ain wit hin t he range of t he base st at ion, t hey can t ake advant age of t he net work. Com m only available equipm ent can easily cover a corporat e cam pus; wit h som e work, m ore exot ic equipm ent , and favorable t errain, you can ext end t he range of an 802.11 net work up t o a few m iles.
Wireless net works t ypically have a great deal of flexibilit y, which can t ranslat e int o rapid deploym ent . Wireless net works use a num ber of base st at ions t o connect users t o an exist ing net work. ( I n an 802.11 net work, t he base st at ions are called access point s.) The infrast ruct ure side of a wireless net work, however, is qualit at ively t he sam e whet her you are connect ing one user or a m illion users. To offer service in a given area, you need base st at ions and ant ennas in place. Once t hat
infrast ruct ure is built , however, adding a user t o a wireless net work is m ost ly a m at t er of
aut horizat ion. Wit h t he infrast ruct ure built , it m ust be configured t o recognize and offer services t o t he new users, but aut horizat ion does not require m ore infrast ruct ure. Adding a user t o a wireless net work is a m at t er of configuring t he infrast ruct ure, but it does not involve running cables, punching down t erm inals, and pat ching in a new j ack.[ ]
[ ] This simple example ignores the challenges of scale. Naturally, if the new users will overload the existing infrastructure, the
infrastructure itself will need to be beefed up. Infrastructure expansion can be expensive and time-consuming, especially if it involves legal and regulatory approval. However, my basic point holds: adding a user to a wireless network can often be reduced to a matter of configuration (moving or changing bits) while adding a user to a fixed network requires making physical connections (moving atoms), and moving bits is easier than moving atoms.
net work, t hough, t here is no need t o suffer t hrough const ruct ion or m ake educat ed ( or wild) guesses about dem and. A sim ple wired infrast ruct ure connect s t o t he I nt ernet , and t hen t he wireless net work can accom m odat e as m any users as needed. Alt hough wireless LANs have som ewhat lim it ed
bandwidt h, t he lim it ing fact or in net working a sm all hot spot is likely t o be t he cost of WAN bandwidt h t o t he support ing infrast ruct ure.
Flexibilit y m ay be part icularly im port ant in older buildings because it reduces t he need for const ruct ion. Once a building is declared hist orical, rem odeling can be part icularly difficult . I n addit ion t o m eet ing owner requirem ent s, hist orical preservat ion agencies m ust be sat isfied t hat new const ruct ion is not desecrat ing t he past . Wireless net works can be deployed ext rem ely rapidly in such environm ent s because t here is only a sm all wired net work t o inst all.
Flexibilit y has also led t o t he developm ent of grassroot s com m unit y net works. Wit h t he rapid price erosion of 802.11 equipm ent , bands of volunt eers are set t ing up shared wireless net works open t o visit ors. Com m unit y net works are also ext ending t he range of I nt ernet access past t he lim it at ions for DSL int o com m unit ies where high- speed I nt ernet access has been only a dream . Com m unit y
net works have been part icularly successful in out - of- t he way places t hat are t oo rugged for t radit ional wireline approaches.
Like all net works, wireless net works t ransm it dat a over a net work m edium . The m edium is a form of elect rom agnet ic radiat ion.[ * ] To be well- suit ed for use on m obile net works, t he m edium m ust be able t o cover a wide area so client s can m ove t hroughout a coverage area. Early wireless net works used infrared light. However, infrared light has lim it at ions; it is easily blocked by walls, part it ions, and ot her office const ruct ion. Radio waves can penet rat e m ost office obst ruct ions and offer a wider coverage range. I t is no surprise t hat m ost , if not all, 802.11 product s on t he m arket use t he radio wave physical layer.
[*] Laser light is also used by some wireless networking applications, but the extreme focus of a laser beam makes it suited only
for applications in which the ends are stationary. "Fixed wireless" applications, in which lasers replace other access technology such as leased telephone circuits, are a common application.
Radio Spectrum: The Key Resource
Wireless devices are const rained t o operat e in a cert ain frequency band. Each band has an associat ed
bandw idt h, which is sim ply t he am ount of frequency space in t he band. Bandwidt h has acquired a
connot at ion of being a m easure of t he dat a capacit y of a link. A great deal of m at hem at ics,
Early Adoption of 802.11
802.11's explosive advance has not been even. Som e m arket s have evolved m ore quickly t han ot hers because t he value of wireless net works is m ore pronounced in som e m arket s. I n general, t he higher t he value placed on m obilit y and flexibilit y, t he great er t he int erest in wireless LANs.
Logist ics organizat ions responsible for m oving goods around ( t hink UPS, FedEx, or airlines) , were perhaps t he earliest adopt ers of 802.11. Well before t he advent of 802.11, package t racking was done wit h propriet ary wireless LANs. St andardized product s lowered t he price and enabled com pet it ion bet ween suppliers of net work
equipm ent , and it was an easy decision t o replace propriet ary product s wit h st andardized ones.
Healt h care has been an early adopt er of wireless net works because of t he great flexibilit y t hat is oft en required of healt h care equipm ent . Pat ient s can be m oved t hroughout a hospit al, and t he healt h care professionals t hat spend t im e wit h pat ient s are am ong som e of t he m ost m obile workers in t he econom y. Technologically advanced healt h care organizat ions have adopt ed wireless LANs t o m ake pat ient inform at ion available over wireless LANs t o im prove pat ient care by m aking inform at ion m ore accessible t o doct ors. Com put erized records can be t ransferred bet ween depart m ent s wit hout t he requirem ent t o decipher t he legendarily illegible doct or scrawls. I n t he clut t ered environm ent s of an em ergency room , rapid access t o im aging dat a can quit e lit erally be a lifesaver. Several hospit als have deployed PCs t o m ake radiology im ages available over wireless LANs on specially- equipped " crash cart s" t hat offer inst ant access t o X- rays, allowing doct ors t o m ake quick decisions wit hout wait ing for film t o be
dev eloped.
Many educt ional inst it ut ions have ent husiast ically adopt ed wireless LANs. 10 years ago, colleges com pet ed for st udent s based on how " wired" t he cam pus was. More high speed dat a port s everywhere was assum ed t o be bet t er. Nowadays, t he leading st ories in educat ion are t he colleges using wireless LANs t o blanket coverage t hroughout t he cam pus. St udent s are highly m obile net work users, and can benefit great ly from net work access bet ween classes or in t heir " hom es away from hom e" ( t he library, st udio, or science lab, depending on m aj or) .
Radio spect rum allocat ion is rigorously cont rolled by regulat ory aut horit ies t hrough licensing processes. Most count ries have t heir own regulat ory bodies, t hough regional regulat ors do exist . I n t he U.S., regulat ion is done by t he Federal Com m unicat ions Com m ission ( FCC) . Many FCC rules are adopt ed by ot her count ries t hroughout t he Am ericas. European allocat ion is perform ed by t he European Radiocom m unicat ions Office ( ERO) . Ot her allocat ion work is done by t he I nt ernat ional Telecom m unicat ions Union ( I TU) . To prevent overlapping uses of t he radio waves, frequency is allocat ed in bands, which are sim ply ranges of frequencies available t o specified applicat ions. Table 1 - 1 list s som e com m on frequency bands used in t he U.S.[ * ]
[*] The full spectrum allocation map is available from the National Telecommunications and Information Administration at
http://www.ntia.doc.gov/osmhome/allochrt.pdf.
Ba n d Fr e qu e n cy r a n ge
UHF I SM 902- 928 MHz
S- Band 2- 4 GHz
S- Band I SM 2.4- 2.5 GHz
C- Band 4- 8 GHz
C- Band sat ellit e downlink 3.7- 4.2 GHz C- Band Radar ( weat her) 5.25- 5.925 GHz
C- Band I SM 5.725- 5.875 GHz
C- Band sat ellit e uplink 5.925- 6.425 GHz
X- Band 8- 12 GHz
X- Band Radar ( police/ weat her) 8.5- 10.55 GHz
Ku- Band 12- 18 GHz
Ku- Band Radar ( police) 13.4- 14 GHz 15.7- 17.7 GHz
The ISM bands
I n Table 1- 1, t here are t hree bands labeled I SM, which is an abbreviat ion for indust rial, scient ific, and
m edical. I SM bands are set aside for equipm ent t hat , broadly speaking, is relat ed t o indust rial or
scient ific processes or is used by m edical equipm ent . Perhaps t he m ost fam iliar I SM- band device is t he m icrowave oven, which operat es in t he 2.4- GHz I SM band because elect rom agnet ic radiat ion at t hat frequency is part icularly effect ive for heat ing wat er.
I pay special at t ent ion t o t he I SM bands in t he t able because t hose bands allow license- free
operat ion, provided t he devices com ply wit h power const raint s. 802.11 operat es in t he I SM bands, along wit h m any ot her devices. Com m on cordless phones operat e in t he I SM bands as well. 802.11b and 802.11g devices operat e wit hin t he 2.4 GHz I SM band, while 802.11a devices operat e in t he 5 GHz band.
What Makes Wireless Networks Different
Wireless net works are an excellent com plem ent t o fixed net works, but t hey are not a replacm ent t echnology. Just as m obile t elephones com plem ent fixed- line t elephony, wireless LANs com plem ent exist ing fixed net works by providing m obilit y t o users. Servers and ot her dat a cent er equipm ent m ust access dat a, but t he physical locat ion of t he server is irrelevant . As long as t he servers do not m ove, t hey m ay as well be connect ed t o wires t hat do not m ove. At t he ot her end of t he spect rum , wireless net works m ust be designed t o cover large areas t o accom m odat e fast - m oving client s. Typical 802.11 access point s do not cover large areas, and would have a hard t im e coping wit h users on rapidly-m oving vehicles.
Lack of Physical Boundary
Tradit ional net work securit y places a great deal of em phasis on physical securit y of t he net work com ponent s. Dat a on t he net work t ravels over well- defined pat hways, usually of copper or fiber, and t he net work infrast ruct ure is prot ect ed by st rong physical access cont rol. Equipm ent is safely locked away in wiring closet s, and set up so t hat it cannot be reconfigured by users. Basic securit y st em s from t he ( adm it t edly m arginal) securit y of t he physical layer. Alt hough it is possible t o t ap or redirect signals, physical access cont rol m akes it m uch harder for an int ruder t o gain surrept it ious access t o t he net work.
Wireless net works have a m uch m ore open net work m edium . By definit ion, t he net work m edium in a wireless net work is not a well- defined pat h consist ing of a physical cable, but a radio link wit h a part icular encoding and m odulat ion. Signals can be sent or received by anybody in possession of t he radio t echniques, which are of course well known because t hey are open st andards. I nt ercept ion of dat a is child's play, given t hat t he m edium is open t o anybody wit h t he right net work int erface, and t he net work int erface can be purchased for less t han $50 at your local consum er elect ronics st ore. Careful shopping online m ay get you cards for half of t hat .
Furt herm ore, radio waves t end t o t ravel out side t heir int ended locat ion. There is no abrupt physical boundary of t he net work m edium , and t he range at which t ransm issions can be received can be ext ended wit h high- gain ant ennas on eit her side. When building a wireless net work, you m ust carefully consider how t o secure t he connect ion t o prevent unaut horized use, t raffic inj ect ion, and t raffic analysis. Wit h t he m at urat ion of wireless prot ocols, t he t ools t o aut hent icat e wireless users and properly encrypt t raffic are now well wit hin reach.
Dynamic Physical Medium
Once a wired net work is put in place, it t ends t o be boring, which is t o say, predict able. Once t he cables have been put in place, t hey t end t o do t he sam e t hing day in and day out . Provided t he net work has been designed according t o t he engineering rules laid out in t he specificat ion, t he net work should funct ion as expect ed. Capacit y can be added t o a wired net work easily by upgrading t he swit ches in t he wiring closet .
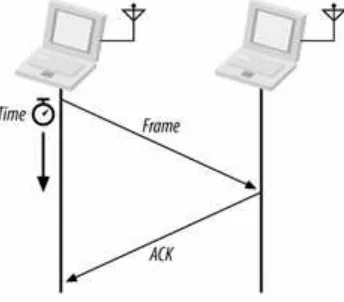
int erference and shadows. Wit hout a reliable net work m edium , wireless net works m ust carefully validat e received fram es t o guard against fram e loss. Posit ive acknowledgm ent , t he t act ic used by 802.11, does an excellent j ob at assuring delivery at som e cost t o t hroughput .
Radio links are subj ect t o several addit ional const raint s t hat fixed net works are not . Because radio spect rum is a relat ively scarce resource, it is carefully regulat ed. Two ways exist t o m ake radio net works go fast er. Eit her m ore spect rum can be allocat ed, or t he encoding on t he link can be m ade m ore sensit ive so t hat it packs m ore dat a in per unit of t im e. Addit ional spect rum allocat ions are relat ively rare, especially for license- free net works. 802.11 net works have kept t he bandwidt h of a st at ion's radio channel t o approxim at ely 30 MHz, while developing vast ly im proved encoding t o im prove t he speed. Fast er coding m et hods can increase t he speed, but do have one pot ent ial drawback. Because t he fast er coding m et hod depends on t he receiver t o pick out subt le signal differences, m uch great er signal- t o- noise rat ios are required. Higher dat a rat es t herefore require t he st at ion t o be locat ed closer t o it s access point . Table 1- 2 shows t he st andardized physical layers in 802.11 and t heir respect ive speeds.
2.4 GHz First PHY st andard ( 1997) . Feat ured bot h frequency- hopping and direct - sequence m odulat ion t echniques.
2.4 GHz Third PHY st andard, but second wave of product s. The m ost com m on 802.11 equipm ent as t he first edit ion of t his book was writ t en, and t he m aj orit y of t he legacy inst alled base at t he t im e t he second edit ion was writ t en.
802.11g Up t o 54 Mbps
2.4 GHz Fourt h PHY st andard ( 2003) . Applies t he coding t echniques of 802.11a for higher speed in t he 2.4 GHz band, while ret aining backwards com pat ibilit y wit h exist ing 802.11b net works. The m ost com m on t echnology included wit h lapt ops in 2005.
Radio is inherent ly a broadcast m edium . When one st at ion t ransm it s, all ot her st at ions m ust list en. Access point s act m uch like old shared Et hernet hubs in t hat t here is a fixed am ount of t ransm ission capacit y per access point , and it m ust be shared by all t he at t ached users. Adding capacit y requires t hat t he net work adm inist rat or add access point s while sim ult aneously reducing t he coverage area of exist ing access point s.
Security
Wireless net works m ust be st rongly aut hent icat ed t o prevent use by unaut horized users, and
A Network by Any Other Name...
Wireless net working is a hot indust ry segm ent . Several wireless t echnologies have been t arget ed prim arily for dat a t ransm ission. Bluet oot h is a st andard used t o build sm all net works bet ween peripherals: a form of " wireless wires," if you will. Most people in t he indust ry are fam iliar wit h t he hype surrounding Bluet oot h, t hough it seem s t o have died down as real devices have been brought t o m arket . I n t he first edit ion, I wrot e t hat I have not m et m any people who have used Bluet oot h devices, but it is m uch m ore com m on t hese days. ( I use a Bluet oot h headset on a regular basis.) Post - second- generat ion ( 2.5G) and t hird- generat ion ( 3G) m obile t elephony net works are also a fam iliar wireless t echnology. They prom ise dat a rat es of m egabit s per cell, as well as t he " always on" connect ions t hat have proven t o be quit e valuable t o DSL and cable m odem cust om ers. Aft er m any years of hype and press from 3G equipm ent vendors, t he rollout of com m ercial 3G services is finally underway. 2.5G services like GPRS, EDGE, and 1xRTT are now widely available, and t hird- generat ion net works based on UMTS or EV- DO are quickly being built . ( I recent ly subscribed t o an unlim it ed GPRS service t o get connect ed during m y t rain t rips bet ween m y office and m y hom e.) Many art icles quot e peak speeds for t hese t echnologies in t he hundreds of kilobit s per second or even m egabit s, but t his capacit y m ust be shared bet ween all users in a cell. Real- world downst ream speeds are roughly com parable t o dial- up m odem connect ions and cannot t ouch an 802.11 hot spot . This is a book about 802.11 net works. 802.11 goes by a variet y of nam es, depending on who is t alking about it . Som e people call 802.11 wireless Et hernet, t o em phasize it s shared lineage wit h t he t radit ional wired Et hernet ( 802.3) . A second nam e which has grown dram at ically in popularit y since t he first edit ion of t his book is Wi- Fi, from t he int eroperabilit y cert ificat ion program run by t he Wi- Fi Alliance, t he m aj or t rade assocat ion of 802.11 equipm ent vendors. The Wi- Fi Alliance, form erly known as t he Wireless Et hernet Com pat ibilit y Alliance ( WECA) , will t est m em ber product s for
com pat ibilit y wit h 802.11 st andards.[ * ] Ot her organizat ions will perform com pat ibilit y t est ing as well; t he Universit y of New Ham pshire's I nt erOperabilit y Lab ( I OL) recent ly launched a wireless t est
consor t ium .
[*] More details on the Wi-Fi Alliance and its certification program can be found at http://www.wi-fi.org/.
The Wonderful Thing About Standards...
Several st andards groups are involved in 802.11- relat ed st andardizat ion effort s because 802.11 cut s across m any form erly dist inct boundaries in net working. Most of t he effort rem ains concent rat ed in t he I EEE, but im port ant cont ribut ions t o wireless LAN st andards have com e from several m aj or locat ions.
Wit hin a working group, t ask groups form t o revise part icular aspect s of t he st andard or add on t o t he general area of funct ionalit y. Task groups are assigned a let t er beneat h t he working group, and t he docum ent produced by a t ask group com bines t he proj ect and working group num ber, followed by t he let t er from t he t ask group. ( Som e let t ers t hat are subj ect t o easy confusion wit h let t ers, such as t he lowercase " l," are not used.) I n wireless net working, t he first t ask group t o gain wide
recognit ion was Task Group B ( TGb) , which produced t he 802.11b specificat ion. Table 1- 3 is a basic list ing of t he different 802.11 st andards.
I nt erest ingly enough, t he case of t he let t er in a st andards revision encodes inform at ion. Lowercase let t ers indicat e dependent st andards t hat cannot st and alone from t heir parent , while uppercase let t ers indicat e full- fledged st andalone specificat ions.
802.11b adds a new clause t o 802.11, but cannot st and alone, so t he " b" is writ t en in lowercase. I n const rast , st andards like 802.1Q and 802.1X are st andalone specificat ions t hat are com plet ely self- cont ained in one docum ent , and t herefore use uppercase let t ers.
At periodic int ervals, t he addit ions from dependent t ask groups will be " rolled up" int o t he m ain parent specificat ion. The init ial revision of 802.11 cam e out in 1997. Minor changes t o t he t ext were released as 802.11- 1999, which was t he baseline st andard for quit e som e t im e. The m ost recent rollup is 802.11- 2003.
Ta ble 1 - 3 . st a n da r ds
I EEE
st a n da r d N ot e s
802.11 First st andard ( 1997) . Specified t he MAC and t he original slower frequency- hopping and direct - sequence m odulat ion t echniques.
802.11a Second physical layer st andard ( 1999) , but product s not released unt il lat e 2000. 802.11b Third physical layer st andard ( 1999) , but second wave of product s. The m ost
com m on 802.11 equipm ent as t he first book was writ t en.
TGc Task group t hat produced a correct ion t o t he exam ple encoding in 802.11a. Since t he only product was a correct ion, t here is no 802.11c.
802.11d Ext ends frequency- hopping PHY for use across m ult iple regulat ory dom ains TGe ( fut ure
802.11e)
Task group producing qualit y- of- service ( QoS) ext ensions for t he MAC. An int erim snapshot called Wi- Fi Mult i- Media ( WMM) is likely t o be im plem ent ed before t he st andard is com plet e.
802.11F I nt er- access point prot ocol t o im prove roam ing bet ween direct ly at t ached access point s
802.11g Most recent ly st andardized ( 2003) PHY for net works in t he I SM band.
802. 11h St andard t o m ake 802.11a com pat ible wit h European radio em issions regulat ions. Ot her regulat ors have adopt ed it s m echanism s for different purposes.
802.11i I m provem ent s t o securit y at t he link layer.
I EEE
st a n da r d N ot e s
TGk ( fut ure 802.11k)
Task group t o enhance com m unicat ion bet ween client s and net work t o bet t er m anage scarce radio use.
TGm Task group t o incorporat e changes m ade by 802.11a, 802.11b, and 802.11d, as well as changes m ade by TGc int o t he m ain 802.11 specificat ion. ( Think " m " for m aint enance.)
TGn ( fut ure 802.11n)
Task group founded t o creat e a high- t hroughput st andard. The design goal is t hroughput in excess of 100 Mbps, and t he result ing st andard will be called 802.11n.
TGp ( fut ure 802.11p)
Task group adopt ing 802.11 for use in aut om obiles. The init ial use is likely t o be a st andard prot ocol used t o collect t olls.
TGr ( fut ure
802.11r) Enhancem ent s t o roam ing perform ance. TGs ( fut ure
802.11s) Task group enhancing 802.11 for use as m esh net working t echnology. TGT ( fut ure
802.11T)
Task group designing t est and m easurem ent specificat ion for 802.11. I t s result will be st andalone, hence t he uppercase let t er.
TGu ( fut ure 802.11u)
Task group m odifying 802.11 t o assist in int erworking wit h ot her net work t echnologies.
When it becam e clear t hat aut hent icat ion on wireless net works was fundam ent ally broken, t he I EEE adopt ed several aut hent icat ion st andards originally developed by t he I nt ernet Engineering Task Force ( I ETF) . Wireless LAN aut hent icat ion depends heavily on prot ocols defined by t he I ETF.
The Wi- Fi Alliance is a com binat ion of a t rade associat ion, t est ing organizat ion, and st andardizat ion
organizat ion. Most of t he Wi- Fi Alliance's em phasis is on act ing as a t rade associat ion for it s m em bers, t hough it also well- known for t he Wi- Fi cert ificat ion program . Product s are t est ed for int eroperabilit y wit h a t est bed consist ing of product s from m aj or vendors, and product s t hat pass t he t est suit e are awarded t he right t o use t he Wi- Fi m ark.
The Wi- Fi Alliance's st andardizat ion effort s are done in support of t he I EEE. When t he securit y of wireless net works was called int o quest ion, t he Wi- Fi Alliance produced an int erim securit y
Chapter 2. Overview of 802.11 Networks
Before st udying t he det ails of anyt hing, it oft en helps t o get a general " lay of t he land." A basic int roduct ion is oft en necessary when st udying net working t opics because t he num ber of acronym s can be overwhelm ing. Unfort unat ely, 802.11 t akes acronym s t o new height s, which m akes t he int roduct ion t hat m uch m ore im port ant . To underst and 802.11 on anyt hing m ore t han a superficial basis, you m ust get com fort able wit h som e esot eric t erm inology and a herd of t hree- let t er acronym s. This chapt er is t he glue t hat binds t he ent ire book t oget her. Read it for a basic underst anding of 802.11, t he concept s t hat will likely be im port ant t o users, and how t he prot ocol is designed t o provide an experience as m uch like Et hernet as possible. Aft er t hat , m ove on t o t he low- level prot ocol det ails or deploym ent , depending on your int erest s and needs.
Part of t he reason t his int roduct ion is im port ant is because it int roduces t he acronym s used t hroughout t he book. Wit h 802.11, t he int roduct ion serves anot her im port ant purpose. 802.11 is superficially sim ilar t o Et hernet . Underst anding t he background of Et hernet helps slight ly wit h 802.11, but t here is a host of addit ional background needed t o appreciat e how 802.11 adapt s t radit ional Et hernet t echnology t o a wireless world. To account for t he differences bet ween wired net works and t he wireless m edia used by 802.11, a num ber of addit ional m anagem ent feat ures were added. At t he heart of 802.11 is a whit e lie about t he m eaning of m edia access cont rol ( MAC) .
Wireless net work int erface cards are assigned 48- bit MAC addresses, and, for all pract ical purposes, t hey look like Et hernet net work int erface cards. I n fact , t he MAC address assignm ent is done from t he sam e address pool so t hat 802.11 cards have unique addresses even when deployed int o a net work wit h wired Et hernet st at ions.
IEEE 802 Network Technology Family Tree
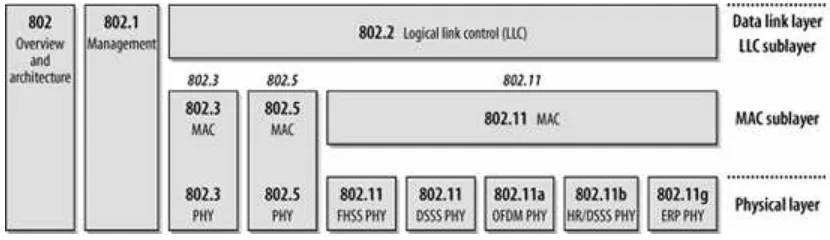
802.11 is a m em ber of t he I EEE 802 fam ily, which is a series of specificat ions for local area net work ( LAN) t echnologies. Figure 2- 1 shows t he relat ionship bet ween t he various com ponent s of t he 802 fam ily and t heir place in t he OSI m odel.
Figu r e 2 - 1 . Th e I EEE 8 0 2 fa m ily a n d it s r e la t ion t o t h e OSI m ode l
I EEE 802 specificat ions are focused on t he t wo lowest layers of t he OSI m odel because t hey incorporat e bot h physical and dat a link com ponent s. All 802 net works have bot h a MAC and a Physical ( PHY) com ponent . The MAC is a set of rules t o det erm ine how t o access t he m edium and send dat a, but t he det ails of t ransm ission and recept ion are left t o t he PHY.
I ndividual specificat ions in t he 802 series are ident ified by a second num ber. For exam ple, 802.3 is t he specificat ion for a Carrier Sense Mult iple Access net work wit h Collision Det ect ion ( CSMA/ CD) , which is relat ed t o ( and oft en m ist akenly called) Et hernet , and 802.5 is t he Token Ring specificat ion. Ot her specificat ions describe ot her part s of t he 802 prot ocol st ack. 802.2 specifies a com m on link layer, t he Logical Link Cont rol ( LLC) , which can be used by any lower- layer LAN t echnology.
Managem ent feat ures for 802 net works are specified in 802.1. Am ong 802.1's m any provisions are bridging ( 802.1D) and virt ual LANs, or VLANs ( 802.1Q) .
802.11 is j ust anot her link layer t hat can use t he 802.2/ LLC encapsulat ion. The base 802.11
specificat ion includes t he 802.11 MAC and t wo physical layers: a frequency- hopping spread- spect rum ( FHSS) physical layer and a direct - sequence spread- spect rum ( DSSS) link layer. Lat er revisions t o 802.11 added addit ional physical layers. 802.11b specifies a high- rat e direct - sequence layer
( HR/ DSSS) ; product s based on 802.11b hit t he m arket place in 1999 and was t he first m ass- m arket PHY. 802.11a describes a physical layer based on ort hogonal frequency division m ult iplexing
( OFDM) ; product s based on 802.11a were released as t he first edit ion of t his book was com plet ed. 802.11g is t he newest physical layer on t he block. I t offers higher speed t hrough t he use of OFDM, but wit h backwards com pat ibilit y wit h 802.11b. Backwards com pat ibilit y is not wit hout a price, t hough. When 802.11b and 802.11g users coexist on t he sam e access point , addit ional prot ocol overhead is required, reducing t he m axim um speed for 802.11g users.
t he 802.11 MAC m ay seem baroquely com plex com pared t o ot her I EEE 802 MAC specificat ions. The use of radio waves as a physical layer requires a relat ively com plex PHY, as well. 802.11 split s t he PHY int o t wo generic PMcom ponent s: t he Physical Layer Convergence Procedure ( PLCP) , t o m ap t he MAC fram es ont o t he m edium , and a Physical Medium Dependent ( PMD) syst em t o t ransm it t hose fram es. The PLCP st raddles t he boundary of t he MAC and physical layers, as shown in Figure 2-2. I n 802-2.11, t he PLCP adds a num ber of fields t o t he fram e as it is t ransm it t ed " in t he air."
Figu r e 2 - 2 . PH Y com pon e n t s
All t his com plexit y begs t he quest ion of how m uch you act ually need t o know. As wit h any
802.11 Nomenclature and Design
802.11 net works consist of four m aj or physical com ponent s, which are sum m arized in Figure 2- 3.
Figu r e 2 - 3 . Com pon e n t s of 8 0 2 .1 1 LAN s
The com ponent s are:
St at ions
Net works are built t o t ransfer dat a bet ween st at ions. St at ions are com put ing devices wit h wireless net work int erfaces. Typically, st at ions are bat t ery- operat ed lapt op or handheld com put ers. There is no reason why st at ions m ust be port able com put ing devices, t hough. I n som e environm ent s, wireless net working is used t o avoid pulling new cable, and deskt ops are connect ed by wireless LANs. Large open areas m ay also benefit from wireless net working, such as a m anufact uring floor using a wireless LAN t o connect com ponent s. 802.11 is fast becom ing
a de fact o st andard for linking t oget her consum er elect ronics. Apple's AirPort Express connect s
com put ers t o st ereos via 802.11. TiVos can connect t o wireless net works. Several consum er elect ronics com panies have j oined t he 802.11 working group, apparent ly wit h t he int ent of enabling high- speed m edia t ransfers over 802.11.
Access point s
Fram es on an 802.11 net work m ust be convert ed t o anot her t ype of fram e for delivery t o t he rest of t he world. Devices called access point s perform t he wireless- t o- wired bridging funct ion. ( Access point s perform a num ber of ot her funct ions, but bridging is by far t he m ost im port ant .) I nit ially, access point funct ions were put int o st andalone devices, t hough several newer
product s are dividing t he 802.11 prot ocol bet ween " t hin" access point s and AP cont rollers.
Wireless m edium
physical layers are defined; t he archit ect ure allows m ult iple physical layers t o be developed t o support t he 802.11 MAC. I nit ially, t wo radio frequency ( RF) physical layers and one infrared physical layer were st andardized, t hough t he RF layers have proven far m ore popular. Several addit ional RF layers have been st andardized as well.
Dist ribut ion syst em
When several access point s are connect ed t o form a large coverage area, t hey m ust com m unicat e wit h each ot her t o t rack t he m ovem ent s of m obile st at ions. The dist ribut ion syst em is t he logical com ponent of 802.11 used t o forward fram es t o t heir dest inat ion. 802.11 does not specify any part icular t echnology for t he dist ribut ion syst em . I n m ost com m ercial product s, t he dist ribut ion syst em is im plem ent ed as a com binat ion of a bridging engine and a dist ribut ion syst em m edium , which is t he backbone net work used t o relay fram es bet ween access point s; it is oft en called sim ply t he backbone net w ork. I n nearly all com m ercially successful product s, Et hernet is used as t he backbone net work t echnology.
Types of Networks
The basic building block of an 802.11 net work is t he basic service set ( BSS) , which is sim ply a group of st at ions t hat com m unicat e wit h each ot her. Com m unicat ions t ake place wit hin a som ewhat fuzzy area, called t he basic service area, defined by t he propagat ion charact erist ics of t he wireless
m edium .[ * ] When a st at ion is in t he basic service area, it can com m unicat e wit h t he ot her m em bers of t he BSS. BSSs com e in t wo flavors, bot h of which are illust rat ed in Figure 2- 4.
[*] All of the wireless media used will propagate in three dimensions. From that perspective, the service area should perhaps be
called the service volume. However, the term area is widely used and accepted.