Cortical Steganography:
A Novel Approach to Multifactor Authentication Through Sensorimotor Coupling
✩A. Chetri∗
Faculty of Science & Technology, Department of Psychology, 115 New Cavendish Street, London, UK University of Westminster1,∗
Abstract
This paper offers an efficient solution to the rubber-hose cryptanalysis problem by training participants a high-entropy underlying target sequence in a visuomotor typing task until the skill is sufficiently acquired. On average, the target sequence reaction time was found to be significantly lower in the trained group when compared to the untrained group. But most important of all, participants failed to recall overall sequence structure, establishing tacit skill expression outside of explicit awareness. Therefore, ensuring that an authentication protocol is built around what users implicitly learn through prior sensorimotor training. Thus guaranteeing that critical information is not susceptible to coercion. The findings hope to lay a framework for future crypto primitives in large-scale security protocols.
Keywords: Implicit memory, multisensory processing, security, cryptography
1. Introduction
Motivations. From Charles Babbage’s Analytical Engine to the birth of TCP/IP and the internet, it is patently clear that the way we live our lives in the modern era has be-come increasingly dependent on computers. Consequently, this has pushed the collective drive to develop robust com-puter security in order to ensure the safekeeping of pri-vate information and preventing malicious intent. This can include protecting a variety of information pertaining to banking details, medical records, email exchanges, and other types of sensitive data. However, no security system is error-free and so discernible flaws are often exploited by unsavoury users (known as black-hat hackers) as most notably seen with the rise of hacktivism. This can include planting malicious software (Malware), distributing mal-ware which masks itself as a safe softmal-ware (Trojan), denial of service (DoS), eavesdropping, spoofing, tampering, re-pudiation, and/or leaking data among others.
By its very nature, computer networks that are built to connect large infrastructures are often targeted and ex-ploited ahead of smaller networks. Therefore, vulnerabil-ities within financial sectors, military departments, con-sumer electronics, the aviation industry, government, and large corporations are kept to a minimum by various se-curity departments. With this in mind, modern sese-curity
✩This report is submitted in partial fullment of the requirements of the University of Westminster for the award of BSc (Hons) Cog-nitive Neuroscience.
∗Corresponding author
Email address: [email protected](A. Chetri) URL:www.ashchetri.co.uk(A. Chetri)
protocols have incorporated numerous measures and tech-niques ahead of cyber-attackers. Such countermeasures of-ten include multifactor authentication methods (biometric validation, picture recognition, key codes, security ques-tions) as well as strengthening network integrity through firewall, encryption, anti-virus, and security-aware policies (trusted platform modules and control lists). Despite all this, the possibility of coercion to reveal critical charac-teristics of the network infrastructure (i.e. releasing pass-words) has been little addressed by security researchers. Such flaws are often referred to as Rubber Hose Crypto-analysis, and thus presents a major issue in modern com-puter security (Jain and Nandakumar, 2012; Bojinov et al., 2012). In particular, access authorisation through the use of password authentication can be viewed as inher-ently flawed in terms of rubber hose crypoanalysis-related attacks (Bojinov et al., 2012) given that computer secu-rity is limited to protecting computers, and not humans. Therefore, applications from cognitive neuroscience and psychological research could be used.
conscious-nature of effort-based rehearsal naturally appears to be one contributing factor to rubber hose attacks.
Our current understanding of memory tends to distin-guish between aspects of recognition and recall based on conscious awareness of the particular information that is retrieved (Henke, 2010). For example, if an individual re-calls a particular memory yet fails to recognise it, then it is understood that the initial trace may have been specifically consolidated through an unconscious process. Discussions into non-conscious processing and memory have been dis-cussed by various researchers, where implicit memories are said to form outside of conscious processing (Dutta et al., 2014). Therefore, manipulating implicit memory function-ing may be key to storfunction-ing sensitive information such as passwords without conscious awareness. Hence, acting as a possible solution to the rubber hose cryptoanalsysis prob-lem (Bojinov et al., 2012; Weinshall and Kirkpatrick, 2004; Denning et al, 2011).
As described by Squire (2009), explicit memory is often referred to as declarative memory, which involves memo-ries relating to facts or experiences. One particular as-pect of explicit memory, is that explicit memories can be conceptualised into knowledge and therefore verbalised through conscious means. Explicit memory can be tested by recall and recognition, and strictly requires effort and intention. However, explicit memories are not durable and can be susceptible to contamination through paired as-sociative learning. On the other hand, implicit memory, otherwise known as procedural memory, involves the learn-ing of skills, habituation, primlearn-ing, and classical condition-ing. The characteristic of implicit memory which makes it an ideal candidate for psychobiometric research is that implicit knowledge is inaccessible due to unconscious pro-cessing. Nevertheless, knowledge can be expressed through several measures not yet fully understood in the literature. Over the years, various researchers have dabbled with implicit learning in the context of computer security. One Microsoft Research (Stubblefield and Simon, 2004) report implemented the use of automatically generated Rorchach ink blots for password synthesis. With each ink blot repre-senting a character used to create a semantic value in the form of a password. However this study makes no effort in inhibiting explicit processing from consciously encoding the passwords, namely through memory techniques such as mnemonics. Participants can therefore divulge informa-tion about the inkblot values under coercion as a result of this protocol. In the same year, Weinshall and Kirkpatrick (2004) studied the nature of behavioural imprinting which allows for gradual learning of rich and complicated experi-ences. The study looked into various paradigms involving picture recognition, objective recognition, and pseudoword recognition used as a method for creating secure crypo-graphic tokens as an adaptive model for securing pass-words. Across all paradigms, information was presented in a seemingly random manner under a common theme. Once rehearsed, authentication was later undertaken to verify if the information has been processed, but also in an
implicit manner. The authentication task involved recog-nising items that were previously seen in the initial set. This is repeated after a number of times to ensure sus-picious behaviour such as guessing is accounted for. Af-ter comparing the results with a simulated imposAf-ter, the trained group performed significantly better than the con-trol. Also, further studies revealed high levels of durabil-ity with 90% accuracy after 1-3 months, and later 70-80% after over 2 months. However, the study posed multi-ple flaws such as the saliency of items affecting consoli-dation. For one, object recognition and pseudoword gen-erated produced less than favourable results compared to image recognition. Secondly and most importantly, if two or more items contained shared central themes, then this would often lead to each item being confused as a single trace. Thus, presenting a problem for memory recognition, and in turn, authentication as a whole. In order to address this, Gaddy and Ingram (2014) employed a partial picture recognition task, which was first introduced by Srinivas et al (1991).
Fragmented images are used with item familiarisation being the ideal measure in place of total recognition. The research found no significant result in the data to suggest this method could be a viable security protocol. Neverthe-less, the study revealed that encoding implicit memories was highly prone to emotion, and fatigue. Since the stim-uli was lengthy to authenticate, not only would this pose a problem for practical use, but this also fed into user fatigue and anxiety, affecting consolidation Gaddy and In-gram (2014). Denning et al (2011) also presented a similar study juxtaposing fragmented images with their completed counterparts for familiarization based on image fidelity. However, the results also produced unfavourable results much like Gaddy and Ingram (2014). Moreover, Rossion and Pourtois (2001) suggested that the use of image and object recognition for such studies are troublesome since central themes and motifs are attended consciously and thus, transferred to explicit memory stores. This leaves a substantial wealth of partial explicit information which a potential interrogator, if successful in coercion, may use to piece together the full information. Kulkarni et al. (2012) also comments on the flaws of graphical recogni-tion by suggesting it creates a pertinent conflict between protocol usability and overall security. Therefore, another method of implicit encoding in password security must be explored. According to Henke (2010), implicit memory re-lies upon a merged unitised representation, therefore indi-vidual reactivation of cues cannot suffice. Instead, implicit memories is reliant upon an element of sensory coupling during the learning episode in order to fully encode into implicit stores. Taking this into account, Bojinov et al (2012) sought to explore the area of sensorimotor integra-tion in implicit encoding.
for an underlying sequence over a foil sequence, despite being presented as a singular structure. This is due to the underlying sequence being repeated more often than the foil sequence, enhancing repeatability. The results of the study indicated that sequence specific knowledge was expressed through fragments, where the trained sequence was typed significantly faster in terms of RT (Reaction Time) compared to the foil sequence. However most im-portant of all is that all participants failed to recognise the correct sequence in an explicit memory test. Accordingly, the results can be derived to form a security protocol based upon individual sequence skill expression where the pass-word is not the sequence per se, but rather the signature performance for the sequence.
Figure 1: SIL visuomotor task comprised of 6 keys (SDFJKL).
Theoretical Framework.
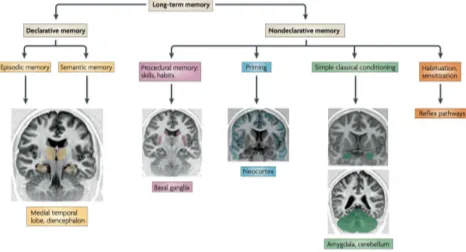
Nondeclarative memory As mentioned by Henke (2010), long term memory can be viewed as a hierarchy based upon processing. The main divisions are factored by conscious (declarative memory) and unconscious (non-declarative memory) recognition systems. Contained within the declarative memory branch are episodic (periodic life events) and semantic (facts and general knowledge) mem-ory stores. Neuroimaging evidence has shown activation of both episodic and semantic memory expression in the medial temporal lobe and diencephalon. On the other hand, the nondeclarative memory branch consists of 4 dis-crete stores; procedural or implicit memory (skills and habits), priming (the altering of perception through pro-cessing specific stimuli), simple classical conditioning (as-sociative learning), and habituation (sensitisation) stores. Also neuroimaging data shows procedural and implicit mem-ory activation in the Basal Ganglia, while priming is found in the Neocortex, and simple classical conditioning in the Amygdala and Cerebellum. Although habituation and sensitisation, two aspects crucial to procedural and im-plicit memory is mostly associated with various reflex path-ways. Since rubber hose cryptanalysis entails explicit (declar-ative) processing to be the root cause of the problem, non-declarative stores or namely implicit and procedural func-tioning must be looked at.
The discovery of implicit memory was made by War-rington and Weiskrantz (WarWar-rington and Weiskrantz, 1974 cited in Mancia, 2006) through studies into priming with
Figure 2: The hierarchy of Long-Term Memory according to their processing characteristics via neuroimaging (Henke, 2010).
Korsakovs amnesia sufferers who exhibited damage in ex-plicit (conscious, declarative) stores, yet showed signs of a intact implicit memory function. Further to this, sensori-motor skill learning, priming, conditioning, as well as cog-nitive skill learning have all been found to be spared in am-nesic sufferers, confirming Mancia (2006)s ndings (Henke, 2010). In addition to this, the spared nondeclarative stores have also shown signs of functional perceptual learning, vi-sual categorisation, prototype learning, and tactual maze learning (Henke, 2010). Along with this, artificial gram-mar learning was also intact suggesting that cognitive skill learning is preserved (Knowlton, Ramus and Squire, 1992). All of this points to the sheer robustness of nondeclarative stores, which share an ideal characteristic of unconscious processing requirements. Therefore coupling nondeclara-tive functioning with sensorimotor integration as described in Bojinov et al (2012) proves to be an ideal method for this area of study.
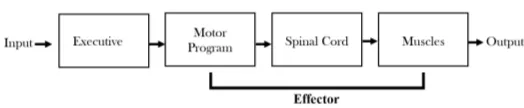
Figure 3: The executive structure of the information processing con-trol system.
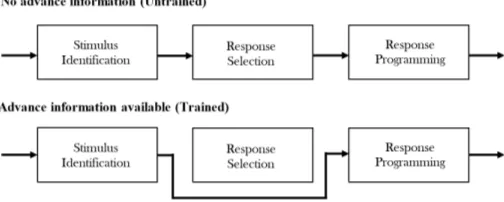
of this, there has been quite a lot of studies on memory codes which is associated with multiple sensory ing modalities (Posner, 1978) including abstract process-ing (Kroll and Potter, 1984), and spatial elements (Badde-ley and Lieberman, 1980). Whether this includes a motor output buffer is still subject to debate (Rosenbaum, 2010). Nonetheless, many proponents of a unified motor learning model of information processing suggests motor program as a open-loop/closed-loop system with an input-output mechanism of signal detection to effector action as an exec-utive model (Schmidt and Wrisberg, 2008). In this model, the first stage is stimulus identification where the percep-tion gathers informapercep-tion for an adequet response. The second stage is response selection which deals with deci-sion making for which type of response should be taken. The third and final stage is response programming, which sums the outputs from the prior stages and arranges the motor system for the overall response. Interestingly, no attention is required for the primary stage in the informa-tional processing model of stimulus identification. How-ever, for response programming to occur attention is re-quired, while attention is sometimes understood to be a factor of response selection (Schmidt and Wrisberg, 2008). Therefore, stimulus identification may play a significant role in implicit encoding.
Figure 4: The expanded structure of the information processing con-trol system, including the executive and effector.
Further to this, the control system models have been extended to account for full motor performance in order to conceptualise the connection between the processing of sensory inputs into muscular output. The expanded model proposes that the executive acts as a mediator in which a directionality state is maintained in order to process into the effector (Schmidt and Wrisberg, 2008). The effector is composed of the motor program, the spinal cord, and muscles necessary to distribute and produce a desired ac-tion (Bapi, Doya and Harner, 2000). This model is then classified into either a closed or open loop control systems based upon either the use of feedback, error detection, correctional process for fine motor control (closed-loop) or no feedback for rapid discrete motor action (open-loop). At the heart of both models is the motor program which dictates the action of acquired skill at the executive level through an array of motor instructions (Schmidt and Wris-berg, 2008). In Bojinov et al (2012)s study, a keyboard was implemented to record keystroke reaction time in order to carry out executive sensory sequence learning facilitated through effector action. Considering this, a closed-loop model of keyboarding may be useful in the overall
concep-tualisation of the motor control contributions to implicit memory function discussed in Bojinov et al (2012)s work.
The visual system Nevertheless, motor function in terms of sensory memory processing is not restricted purely to finger and/or limb movement.
Figure 5: The Optomotor Cycle. Another important
area in this research lies within ocularmo-tor function, specifi-cally saccades, rapid eye jumps (100-300ms) that fixate items of inter-est within the fovea (Rosenbaum, 2010). In a general sense, sac-cades are conducted in order for the brain to
create a rapid account of the visual field through 3-5 sac-cadic snap shots (Rosenbaum, 2010). This includes the in-termediatary events and breaks between eye-movements, suggesting a use of a temporary memory store. It is there-fore understandable to suggest that the fixation allows in-dividuals to attract spatial attentional resources into the fixated image. The link between spatial attention and sac-cades was first suggested by Posner (1978) who proposed that reaction time is lowered when spatial (and movement) information of objects are anticipated to a degree of accu-racy. Although, recent evidence has suggested that it is conversely implicit learning which guides attentional re-sources via saccades (Jiang, Won and Swallow, 2014).
(dor-sal, where pathway). Additionally through the 2-stream hypothesis, later findings suggested a dual-process model for vision (Norman, 2002). According to the model, the dorsal stream requires low conscious effort and typifying autonomic processing, and the ventral stream necessitates high conscious effort and is relatively slow in processing.
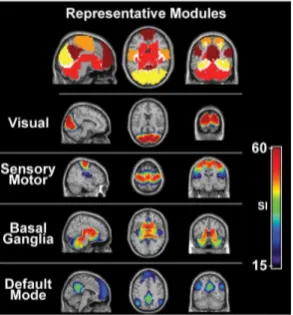
Figure 6: Neuroimaging data shows patterns of activation in areas implicated in implicit memory, sensorymotor, and visual processing (Moussa et al., 2012).
Therefore in a broad sense, the visual system can be viewed in terms of stimulus identification-recognition and visually guided behaviour. Considering this model, for efficient implicit sensorimotor learning, small amounts of conscious visual information may be required in order for the encoding process to take place effectively.
Although not widely accepted, the Default Mode net-work (made up of the precuneus/posterior cingulate, infe-rior parietal lobes, and medial frontal gyrus) in the brain is understood to be active during low-attentional focus and wakeful rest (Broyd et al., 2009). As measured through fMRI resting state network (RSN), the Default Mode is found to be involved with the attentional focus switch from resting state to high focus (Fox et al., 2005). This was also confirmed in later neuroimaging data, where the visual network’s capacity for RSN attentional switch was found to be highly consistent with sensory-motor, and basal gan-glia (implicated in implicit learning) cortices; but not so much for the Default Mode network (Moussa et al., 2012). Other regions such as the lateral and ventral intrapari-etal cortex of the intra-pariintrapari-etal sulcus (IPS) in the pariintrapari-etal lobe is understood to play a significant role in visual atten-tion and saccadic eye movement (Culham and Kanwisher, 2001). The IPS is also strongly implicated in sequence learning through fine finger moments through perceptual motor coordination (Sakai et al,. 2002). Such findings uni-fies several highly functional visuomotor networks and at-tention with the idea of a Visual Association Cortex (Zeki, 1993).
Keeping this in mind, the individual and combined roles of the two specialised visual systems, focal vision and ambient vision, is also fundamental to the visuomotor
structure described. Focal vision specialises in the con-scious visual identification of the stimuli for an appropri-ate input response as described in the information process-ing model. Through the use of attention, the focal visual system allows individuals to consciously fixate to form a perception of objects of interest (Schmidt and Wrisberg, 2008). Ambient vision on the other hand is largely respon-sible for movement control in both central and peripheral visual fields. Unlike focal vision, ambient vision detect the spatial location and moment of objects in relation to the individual. But most importantly, the ambient visual sys-tem contributes largely to fine-motor control without con-scious awareness (Schmidt and Wrisberg, 2008). The way in which focal attention orientates attention into muscular output is based upon feedback and error correction, which contributes to calibrating attention to information on the surroundings for efficient motor performance (Schmidt and Wrisberg, 2008).
Attention In order to inhibit conscious awareness of the trained item(s), an authentication protocol based upon implicit learning must discriminate between explicit and implicit processing. It is therefore worth investigating the role of attention as a mediator of information process-ing for this particular area of study. To which, Lozito and Mulligan (2010) looked into the role of attention in the implicit memory retrieval process during test phase. Within the study was three separate experiments based upon perceptual identification, word-stem completion test, and category exemplar production test. Out of all the tasks, attention was found to strengthen the performance of a secondary task through ’automatic’ retrieval.
break-down in decision making (Richards et al., 2014).
Inference for research Similarly to attention, the encoding process of implicit memory is also highly vul-nerable to emotion (Mancia, 2006). More still, attentional interference also disrupts familiarity and recollection in im-plicit memory recall (Topolinski, 2012). This is very much akin to how interference disrupts automaticy, unconscious skill expression (Schmidt and Lee, 2011). Which in turn, feeds into motor performance through the measure of re-action time (Bojinov et al., 2012). As discussed, the motor system is a trigramic relationship between the task, the in-dividual, and the environment (Repp and Su, 2013). How this feeds into perceptual learning is another dimension can be explained through sensorimotor skill expression as a function of implicit (procedural) memory (Henke, 2010). Although, enhanced motor learning is highly associated with systematic practice and habituation which results in permanent and autonomous (unconscious) performance (Schmidt and Lee, 2011). Combining these lines of evi-dence; attention, visuomotor system, perceptual learning, and implicit memory all share substantial commonground for further research.
As with Bojinov et al (2012)s findings, repeating ele-ments of a structure were superior to the implicit learn-ing than the non-repeatlearn-ing (and sometimes changlearn-ing) el-ements (Pew, 1974; Magill, Schoenfelder-Zohdi, and Hall cited in Maghill, 1998; Wulf and Schmidt, 1997). With the pertinent problem presented in rubber hose cryptoanalysis (and the findings from previous implicit learning studies pointing less favourly to visual recall) the method of mo-tor learning to aid implicit learning of momo-tor commands to produce a signature performance may be a viable area to explore in security research. However, Bojinov et al (2012)s design could be improved upon, alongside inves-tigating effects of saccaddic manipulation and the role of attention in the encoding process. Although in order for the protocol to act as a viable security system, efforts must be taken to lower the authentication time. All the while, expression of skill must be viewed as the password rather than the item being rehearsed, as ultimately authenitca-tion will identify correct users based upon performance. Overall, this creates a strong situation-based approach by combining context (environment), sensory-perceptual de-mands (task), and motor performance (individual) into a framework for the rubber hose cryptoanalysis problem.
2. Methodology
Key Selection & Cluster Topology. An array of 32 key-board keys discriminated by left hand (x keys) and right hand (y keys) was uniformly distributed into paired bi-grams sequences for optimal motor performance and en-hanced security.
For this, 3 keys per hand are selected on a pseudo-random basis using a software number generator, and thus
Figure 7: Specific mapping (A) of fingers to 6 keys (SDF, JKL) in Bojinov et al. (2012) compared to novel method of non-specific mapping of 6 keys within determined areas (B).
can be demonstrated in the expression below.
Lef t Hand={x1, x2, x3}, Right Hand={y1, y2, y3}
To verify the usability of such a wide space of keys, a num-ber of measures will be taken. Namely, analysing the com-bining properties of how the 32 keys is spread across two spaces, and the chances of an unauthorised user guessing a correct combination. Given that keys 1-16 are within a set of the left keyboard space (x) and keys 17-32 are within a set of the right keyboard space (y), the number of possible permutations of all 16 keys for each keyboard space is 313,600, as expressed below.
16 3
·
16 3
=
16! 3!(16−3)!
2
= 313,600
This greatly improves upon Bojinov et al (2012)s keyboard layout as there can only be (4C3)2
= 16 possible combi-nations in the previous study. Therefore, the layout used in this study is an effective solution for non-authorised users pre-empting keystroke patterns due to humans form-ing a symbolic internal layout for motor plannform-ing effects (Krakauer and Shadmehr, 2006). This creates a robust platform for developing strong and secure sequence syn-thesis.
Figure 8: Euler cycle was used to generate 30 bigrams keys.
In the same manner as Bojinov et al (2012), using the bigram matrix generated from the 6-node Euler circuit, the 30-character alphanumeric Target sequence (T) was synthesised as expressed below.
To synthesise the primary sequence, T, 15 bigrams from the matrix are selected at random from the pool, creating a 30 character string. Whereas for the secondary sequence, the Foil (F), 9 bigrams are selected at random from either the remaining pool of bigrams or the entire matrix, depending on cluster typing. A Cluster is made up of the 2 sequences (Target and Foil), with the Target repeating 3 times and the foil repeating once. Therefore a typical Cluster for this study can be expressed as:
3T+F
Moreover, the distribution of the bigrams in the com-position of T and F is also dependant on cluster typing. Cluster A and Cluster C will be randomly ordered, Cluster B will have a determined order to ensure less overt pat-terns occurring in the sequences, but also patpat-terns which can be construed by the user to make semantic sense (e.g. HI, LO = High Low).
The method of synthesising an 18-character secondary sequence, F, from the remainder of bigrams is also depen-dant on cluster typing. The property of Cluster A is such that F is synthesised from the entire alphanumeric pool, which includes items that have already been assigned to a sequence. This creates a less-salient overlap between Tar-get and Foil sequences. Whereas Cluster B generates F by randomly selecting 9 bigrams from the remaining pool, creating a more salient relationship between T and F. In Cluster C, elements of the secondary sequence is derived from a completely new matrix, and so contains a higher number of keys used (6 keys per hand). This creates a far more salient perception of T and F, while also, disrupting the motor planning effects of T when shifting to a com-pletely new layout in the F sequence. However because of the clear separation between the sequences, participants may perceive an underlying structure inhibiting implicit encoding of T. Hence why cluster typing analysis is in-cluded in the investigation.
Experimental design. Participants will be arranged in two groups in an independent groups design. The first group will be categorised as the trained group, who will receive prior training before undergoing a test phase. The second group will be the untrained group, who will only partake in the test phase without prior training. The research ques-tion aims to address whether training of target sequences has an effect on target sequence-specific performance rates via reaction time.
In order to investigate the effects of sensorimotor pre-training on test phase reaction time, reaction time will be measured as the continuous dependent variable. Al-though percentage advantage for specific sequences over the other will also be measured as a modulus of reac-tion time. Whereas, the training vs no training category, and the session category being the between-groups fac-tors. Within-groups factors such as sequence type (Target or Foil) performance will also be taken into account.
The first hypotheses are two-tailed and will concern the sequence-level investigation, with the null hypothesis being that mean reaction time between Target and Foil sequences are equal for both groups. Whereas the alterna-tive hypothesis in this level is that the mean reaction time difference between Target and Foil sequences are unequal for both groups.
H0:target=f oil, HA:target6=f oil
Finally, the second hypotheses will concern the one tailed group-level investigation, with the null hypothesis as the mean reaction time of target sequences in the trained group will be equal to the mean reaction time of target sequences in the untrained group. On the other hand, the alternative hypothesis will be that mean reaction time of target sequences in the trained group will not be equal to the mean reaction time of target sequences in the un-trained group.
H0:trained=untrained, HA:trained6=untrained
Participants. 2 groups of 5 healthy adult participants (n= 10) were voluntarily recruited for the study through Uni-versity mailing lists and noticeboard advertisements. 40% of the participants were male and 60% were female, with the youngest participant being 18 years old and the old-est being 55 years old. One participant withdrew from the study, and therefore was not included in the final data pool. Therefore, the participant’s control counterpart was also not recruited as no comparisons could be made oth-erwise.
Procedure. Despite sequences being arranged in bigrams, the bigrams will be grouped in order to appear as paired-trigrams in the final stimuli (e.g. bigrams FI, P8, UJ -¿ FIP, 8UJ). A trigram of consecutive sequence items shift-ing from box 1 to box 2 to box 3 one at a time. This method was selected due to saccadic eye movements play-ing a significant role in the spatial anticipatory factor of oculomotor sequence learning and its effects for proce-dural memory consolidation (Albouy et al., 2008). But more importantly, trigrams facilitates the user to antici-pate motor patterns in groups of 3, which in turn allows for stronger performance advantage (Destrebecqz and Cleere-mans, 2001).
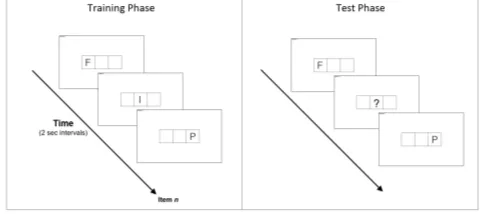
Figure 9: An example of the difference between the tasks. Unlike the 35-trial training phase, the 3-trial test phase involves the participant to quickly type keys including hidden elements of the sequence with no time constraint.
Primarily, the experiment will be carried out in two phases, the training phase and the test phase. The train-ing phase will involve participants typtrain-ing keys that quickly appear on the screen in a seemingly random manner. Keys displayed will be ordinal, dependant on cluster topogra-phy. So therefore, the participant will be typing both Target and Foil sequences. However, since the Target se-quence is repeated 3 times and the Foil once, the partici-pant should be better trained on the Target sequence. It is understood that this comprehension in Target sequences over Foil sequences should manifest in motor performance over the course of the training phase. And so, such per-formance should involve faster reaction time and fewer in-correct keystrokes for the Target sequences compared to Foil sequences. Each cluster will be considered as 1 trial, with 5 trials per block. Thus in total, the training phase will comprise of 7 blocks (35 clusters, 3780 items) with a maximum timer of 2 seconds per item. This is enforced to ensure that items that exceed the temporal window will be skipped and considered a miss (incorrect keystroke), in-hibiting the user to attend to the item promoting explicit processing. Therefore, the issue of explicit memorisation techniques such as chunking can be addressed through the sheer speed of the task. Participants will be given a break upon competition of each block.
Within the test phase, there will be 2 further tests sep-arated by at least 24 hours (Session 1 and Session 2). This phase is almost identical to the training phase, however, there is no timeout and various elements of the sequences
will be hidden. Therefore the test phase will rely on both the speed, and correct keypresses which will be the hall-marks that learning has taken place. The second session is purely to test the robustness of the learning through observing retention rates (performance over the course of 2 sessions). A final verification of the type of learning will be made by asking the participant to explicitly reveal the sequence(s).
Participants will be divided into 2 groups, the Trained group and the Untrained group. The Trained group will undergo the training phase prior to the test phase, while the Untrained group will only undergo the test phase (al-beit, with explicit knowledge of the sequence for Session 1). Cluster typing for this study will be predetermined prior to the study, with 2 participants in each group be-ing assigned a cluster type. Therefore, participants 1-2 (group 1) and 6-7 (group 2) will be assigned to cluster A, while participants 3-4 (group 1) and 8-9 (group 2) will be assigned to type A. Due to the attrition of 1 participant, Cluster C will not be assigned to 2 participants per group. The choice to not recruit the group 2 Cluster type C will be assigned to the remaining participants, participant 5 (group 1) participant 10 (group 2).
Ethics. In terms of ethical implications, the study aimed to keep participant harm at a minimal level. However, there may be acute issues that may have arisen during the course of the study. Namely, there may be issues with participant eye-strain during lengthy training phase ses-sions. In a broad sense, the average duration of each training phase was around 40-50 mins (with breaks be-tween blocks). Despite this, the stimuli was coded on a white background on black text. But since the study re-quires the participant to make saccadic eye movements across each box, this may harm the participant.
To address this, a screen tint was offered to each ticipant at the beginning of the session. However, no par-ticipant made use of this. It could be the case that the participant may have been naive to the extent of how the stimuli will affect their eyes prior to the start of the study. Although, allowing the participant to use a screen tint mid-way may affect results and thus poses a flaw in the methodology in maintaining controlled conditions of the experiment. With this in mind, a grey background will be used for all participants in future studies.
3. Results
Training Phase.
Figure 10: Target sequence disparity rates over foil.
(a) (b)
Figure 11: Participant-level data for mean reaction time (a), and the target sequence advantage rates (b)
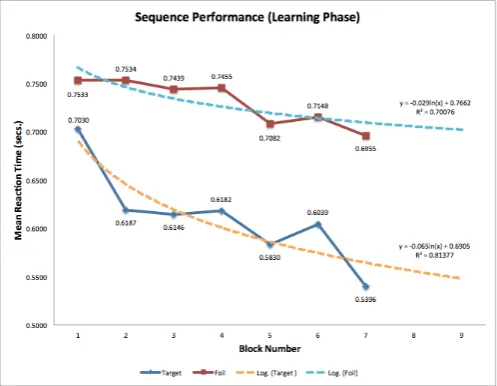
in the performance advantage of Target sequence reaction time, compared to and Foil sequence reaction time. In Block 2 to Block 5, reaction time stabilised around the 21% mark in performance advantage. However, this soon dips slightly in Block 5 (21.47%) to Block 6 (18.36%) before rising further in Block 7 to make for the second highest in-crease (28.88%). In addition, participant-level differences (figure 11) was also extracted from the data with partic-ipant 1-2 (cluster A), particpartic-ipant 3-4 (cluster B), partici-pant 5 (cluster C). On average, there is a 22.96% difference in Target sequence-specific knowledge advantage over Foil sequences. Participant 5 had the fastest reaction time, however displayed a minuscule Target-specific advantage over Foil reaction times (0.17%). Participant 1 had the fastest reaction time with a 3rd highest magnitude of dif-ference between Target and Foil sequences (24.04%).Par-ticipant 4 also exhibited the largest reaction time differ-ence between Target and Foil sequdiffer-ences (65.70%). Par-ticipant 2 displayed the second highest predicted diver-gence (25.67%). Finally, Participant 3 showed a mod-est difference between Target and Foil sequence reaction times (9.41%), the second lowest Target-Foil predicted di-vergence.
Training phase model Through the data collected from overall sequence-level performance, a logarithmic re-gressional model for both Target and Foil sequences for each cluster was made (figure12). From this, predictions for future performance for 2 additional blocks were fore-casted. Type A and Type B clusters display similar log-arithmic patterns, with a minor 0.11265 R2
-difference in Foil sequences. Additionally, there is also a much closer
±0.08761 difference in Target Sequences. However, as pre-dicted, Type C clusters show less Target-Foil disparity. As such, there is not enough sufficient data found in Type C clusters in order to create a robust model on the sequence interactions observed in Type A and B. However, Type C cluster performance is still important for comparative rea-sons. The issue of structural saliency (typical to Type C clusters) affecting Target-Foil reaction time disparity can be applied when formulating effective sequence structures for optimal performance.
(a) Type-A (b) Type-B (c) Type-C
Figure 12: Cluster-level regressional analysis through logarithmic models to predict future block performance.
Figure 13: Overall cluster-level regressional analysis
pre-diction of rehearsal facilitating motor knowledge, which in turn manifests in faster reaction time. R2
values are sep-arated by approximately ±0.1 difference between Target and Foil sequences, however the reaction time disparity is evident through the wide reaction time margin as noted in (Fig 1) and in the intercept difference showing approxi-mately±0.1 seconds, a≈100ms difference. Although rela-tively small, such a difference can provide a framework for a baseline level for crypto primitives when recording per-formance. In terms of designing these security algorithms, the data presented above may prove to be especially use-ful. However there may be issues with a saturation point in the separation of explicit and implicit processing. For example, identifying the point in which over-rehearsal of tacit information feeds into explicit processing. Neverthe-less, it is important to view such findings as early work to create a framework for further investigation. Overall, the general models presented are as follows:
F oil:y=−0.029ln(x) + 0.7662, R2= 0.70076
T arget:y=−0.065ln(x) + 0.6905, R2= 0.81377
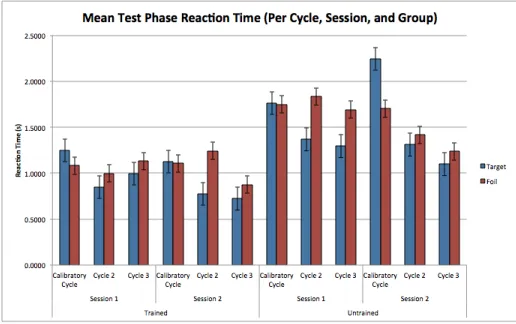
Test Phase. Test phase was evaluated per 3 cycles (3 repe-titions of the cluster), with the mean reaction time of each target and foil sequences for every cycle being recorded for later analysis (figure 14). As the calibratory period lies pri-marily within the first cycle, this tends to skew the data greatly to which it is no longer representative of the overall trend. For this, the first cycle for each session was viewed as a practice phase and omitted from the final analysis. Therefore, the mean test phase reaction time is adjusted to reflect a more accurate total measure for the average reaction time between Cycles 2, 3 (session 1 and session 2).
Figure 14: Observable non-parity in Target-Foil is inverse for all calibratory cycles.
A three-way mixed ANOVA was carried out to inves-tigate the effects of sessional progression, sequence type, and training on test phase reaction time across correct keystrokes. Mean reaction time was normally distributed, as assessed by Shapiro-Wilk’s test (p > .05). There were
five outliers in the data, as assessed by inspection of a boxplot for values greater than 1.5 box-lengths from the edge of the box. These values were not omitted from the data as the values did not considerably affect the over-all outcome of the findings. There was homogeneity of variances, as assessed by Levene’s test for equality of vari-ances (p > .05). Mauchly’s test of sphericity was assumed to be violated as the outcome did not return a significant result. Therefore, a Greenhouse-Geisser correction was ap-plied instead. Through this, there was a statistically sig-nificant three-way interaction between sequence, session and group, F(1,8) = 5.736, p=.044, partial η2
= .418,
ε= 1.
An independent t-test was carried out to analyse sequence-level differences. During Session 1, the Trained group showed a significant disparity with Target and Foil se-quences (t(297.853) = −2.246, p = .025). However, the Untrained group displayed an insignificant difference (t(228.709) =
−1.263, p = .208). In Session 2, the Trained group se-quence disparity was also significant (t(194.930) =−2.824, p=
.005), while the Untrained group sequence difference re-mained insignificant (t(478) = −.727, p = .468). Over-all across both sessions, the Trained group exhibited a significant difference between Target and Foil sequences (t(458.145) =−3.608, p=.0001), as the Untrained group exhibited an insignificant difference (t(507.081) =−1.443, p=
.150). Therefore, there was a statistically significant dif-ference between means in the Trained group (p < .05) and an insignificant difference between the means in the Un-trained group (p > .05). Hence, the null hypothesis is rejected in order to accept the alternative hypothesis of the first supposition.
Table 1: Overall test phase performance over correct keystrokes.
Mean RT (s)
Advantage (%) Session Group Target Foil
1 Trained 0.8973 1.1746 30.9038
Untrained 1.3310 1.7634 32.4869
2 Trained 0.7055 1.2922 83.1609
Untrained 1.2672 1.3271 4.727
In order to measure group-level differences (table 1), an independent samples t-test was run. The first session saw the trained group perform on average significantly faster on Target (t(489.994) = −3.354, p = .001) but in-significantly faster on Foil (t(232.476) =−1.893, p=.06) sequences compared to the untrained group. Moreover, in the second session, the trained group performed on average significantly faster on the Target (t(371.571) =
−4.574, p=.0001) yet insignificantly on the Foil (t(358) =
se-Session Group Cluster Advantage (%) Mean Target RT (s)
Table 2: Overall cluster-level performance rates over correct keystrokes.
quences and insignificantly faster on Foil (t(601.351) =
−1.868, p = .062) sequences compared to the Untrained group. Therefore, there was a statistically significant dif-ference between means in the Target sequence performance between groups (p < .05), and an insignificant difference between the means in the Foil sequence performance be-tween groups (p > .05). Hence, the null hypothesis is rejected in order to accept the alternative hypothesis of the second supposition.
Finally, for clusteral analysis as observed in the over-all findings the untrained group performed worse across sessions for all cluster types (table 2). This was also true for Type B clusters in the trained group which saw per-formance rate fall from 65.7% to 52.23% across sessions. Globally, Type C sequences showed the strongest reten-tion rates among all cluster types. This is due to a 49.02% performance advantage in session 1 (3rd lowest target se-quence RT), which further increased to an incredible 222.5% in session 2 as the lowest RT among other clusters. Whereas in group 2 (untrained), there was a 12.73% decrease per-formance which is consistent with the other untrained clus-ters apart from one participant in Type B trained group which saw a sessional decrease from 65.7% to 52.23%. Trained Type A clusters showed the second highest advan-tage, however produced the highest RT of all the trained clusters. Taking all groups into account, untrained Type C clusters showed the slowest RT and untrained Type B had the worst performance advantage rate. Whereas con-versely, trained Type C clusters showed the highest per-formance rate and lowest RT.
4. Discussion
Interpreting the data. During the training phase, the find-ings suggested that the Target sequence was significantly better learnt than Foil sequences due to the increasing per-formance advantage rates along 7 blocks. This gradual ex-pression of Target sequences over Foil sequences can be de-scribed as a result of repeating the Target sequences more
often than Foil sequences. Therefore, despite presenting clusters as a unitary sequence, participants expressed a preference for a predicted structure which is blind to the user.
Data was also isolated into specific cluster types for later analysis. With this, despite showing the lowest RT, Type C clusters revealed to be the least useful with the lowest performance advantage rates among the other clus-ter types. The salient nature of key selection for Type C clusters, where a new pool is generated for the Foil sequence may be a factor for the results shown. Hav-ing two different bigram pools for each sequence allows participants to grasp an understanding of an underlying structure of the cluster by attending the sudden change in motor sequence patterns. Although, as well as raising issues with explicit processing of the sequences, the sheer perceptual novelty of the secondary sequence may also en-code into long-term memory stores in the same manner as the primary sequence. Therefore, explaining the lit-tle difference among the sequence performance. Type A and Type B clusters showed much better learning, as se-quences consisted of a singular bigram pool, thus appear-ing blind as a unitary structure (the cluster). However the fine differences between the cluster types lies within the method of distributing the bigrams for each sequence as mentioned previously. Bearing this in mind, Cluster A has a more nonsalient overlap between the sequences compared to Cluster B. And so, the effects of such can be seen in the cluster-level differences where Type A clus-ters display faster Target keystrokes over 7 blocks than Type B. Although, Type B clusters had a wider Target-Foil disparity, entailing a stronger performance advantage. However, performance advantage alone does not describe RT performance, only the interaction between sequences. Considering this, a relatively low Target RT and standard performance advantage rate is a viable criteria for learning efficiency.
As discussed, in order to fully take account of global performance RT as well as performance advantage rates must be discussed. Keeping in line with this thought, dur-ing the test phase the performance advantage and RT of Group 1 (trained) was measured and compared to Group 2 (untrained). As expected, the trained group performed significantly better on session 2 than the untrained group. As well as this, the trained group achieved significantly faster keystrokes than the untrained group across all ses-sions (table 1). The reason why trained group performance failed to exceed the untrained group in Session 1 is due to the use of the explicit aid. This was designed in order to determine patterns that might indicate explicit memorisa-tion. Such patterns include high RT (low automaticity) due to use of aid which inhibits ideal motor performance, entailing conscious processing. This was certainly the case for Session 1 where the untrained group on average per-formed slower than the trained group. This was also found to be consistent in the second session.
phase, which interestingly suggests Type C clusters are the most efficient type of choice. This indicates that although learning was not directly observable through Target-Foil disparity, overall target skill expression can still be re-silient across sessions. Although, this might be the case due to the low participant numbers. 2 participants were assigned for every cluster apart from Type C. Which due to the attrition of a participant, only 1 (instead of 2) par-ticipant per group was allocated to Type C. This may have skewed the data to such an extent to explain the unconven-tional patterns compared to the other cluster typing. Al-though when compared to untrained group, cluster C still produced enough data to warrant interest. This included the suggestion that trained Type C clusters was the most ideal cluster, whereas untrained Type C was the least ideal (among all clusters). This strongly supports the idea that training, and not explicit processing, was the contributing factor for the Type C trained performance. This is es-pecially the case as the untrained group received explicit knowledge of the sequence in session 1. Yet despite this, the untrained group still underperformed when compared to the trained group.
An interesting aspect of the test phase is the inverse disparity found in the calibratory cycles. Across both ses-sions, and regardless of groups (trained or untrained), Tar-get sequence RT is always greater than Foil sequence RT, creating a learning disparity (Didierjean, 2007). This phe-nomenon can be explained as an aspect of information processing model previously discussed, with the calibra-tory cycle acting as a primary stage for stimulus identifi-cation. As the Target Sequence is presented ahead of the Foil sequence in all cycles in the test phase, it is natural that identification will slow down processing speed until correctly calibrated in the following cycles. Once fully calibrated, performance will converge into a stable and predictable manner. From this micro observation of per-formance calibration, inference into trained and untrained performance can be drawn. Where prior training allows for neural pathways to be established, offering a sensory short-cut to response programming. So as expected, per-formance from the trained group increased across the ses-sions compared to the untrained group. This falls in line to the the information processing model (figure 15), where sheer rehearsal strengthens overall tacit knowledge which in turn necessitates the bypass of the response selection stage. In the calibratory stage, this is modulated by er-ror correction through feedback processing. On the macro scale, this takes place during sensorimotor training, as ev-ident in the learning curve (figure 10).
Autonomous behaviour has been explained in terms of spatial and event anticipation, where according to Rosen-baum (1980), individual RT could be lessened when indi-viduals pre-engaged with response processes, through ad-vance information. In addition, it may be the case that response selection facilitates conscious processing as selec-tion involves the user to attend to the stimuli through con-scious effort. However, little is known of the mechanisms
Figure 15: Response selection acts as an intermediary in the overall processing of information, where if advance information is available, response selection may be bypassed, speeding up overall processing.
of response selection stage and its neural resources through the data gathered in this study. Although, it is believed that the use of saccadic movements along trigrams (figure 16) strengthens the visuomotor learning process. Antic-ipating discrete spatial location through motor planning effects is critical to this, where a rich knowledge of the keyboard-layout and spatial location of item on screen is calibrated and consolidated in the participants long-term nondeclarative memory store. Further to this, the speed of the task and saccades ensures that neither the stimuli nor the action is consciously attended enough to consolidate explicitly. This is confirmed in the debriefing session as all participants failed to report an awareness or recognition of the fundamental structure of the sequence. Nonetheless, in this task it is the performance, rather than the item that is rehearsed that acts as the biometric for authentication.
Figure 16: The saccadic cycle which participants exhibit along tri-grams. Item x is considered the first item of the task. The saccade resets to its initial position for every new trigram (3 items).
relatively accurate Matlab timer which was coded in ad-vance. However as this was a separate program, Matlab could not distinguish between correct and incorrect key-presses. Moreover, due to time constraints of being a 6 month project, it was not possible to make the stimuli coded entirely as an .m file. This would serve various benefits including versatility between windows and mac compatibility. This would increase productivity as devel-opment was largely done at home on a Mac OS X com-puter, whereas data collection was conducted in the lab on a Windows machine.
Furthermore, there may be a methodological issue re-garding the use of alphanumeric sequences. This was brought up by a participant during debrief, since sequences can be arranged in such a way to make semantic sense for partic-ipants (e.g. QIQ, FIP = Kick Flip). Although the task relies on the tacit comprehension of patterns in sequences (for anticipating responses), the use of letters may im-pede non-conscious process due to the formation of words and/or sentences appearing more salient in the stimuli. This is particularly troublesome as the participant, through the chunking of items, can also make explicit sense of an underlying structure of sequences, and ultimately an un-derstanding of the cluster. This may have been the case with one particular participant who reported during the debrief to be aware of certain elements and characteristics of the sequence.
Nevertheless it must be noted that while the task en-courages for the implicit memorisation of the target se-quence, it is performance (RT) rather than information recall that is being measured. As demonstrated with the untrained group, explicit knowledge (in session 1) still does not produce motor performance that is on par with indi-viduals who process the stimuli with prior encoded knowl-edge. In terms of computer security, there might also be issues with the possibility of unauthorised access to ex-plicit sequences, allowing users to engage in sensorimotor training to spoof authentication. Therefore, the immedi-ate use of an explicit aid in the untrained group may not be sufficient enough to address this. However this should not pose a major flaw for the protocol, as any practical application for the research should be expected to enforce in-situ training and authentication. Remote authentica-tion is simply not feasible for this type of authenticaauthentica-tion due to false positive access through unauthorised training and spoofing. Taking this into account, it is also worth-while considering the contribution social facilitation and investigator effects due to the prescence of a task supervi-sor. Importantly, there are several participant-level factors and individual differences that affect RT performance, at-tentional space, memory encoding and retrieval. Nicotine is widely mentioned in the literature to assist in explicit processing through the widening of individuals attentional spotlight (Hahn, Shoaib, and Stolerman, 2011).
Conversely, drugs such as scopolamine (hyoscine) has been found to disrupt explicit processing by inhibiting sus-tained attention (Danion et al., 1990). More still,
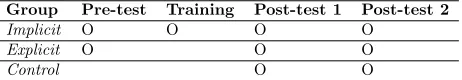
sub-Group Pre-test Training Post-test 1 Post-test 2
Implicit O O O O
Explicit O O O
Control O O
Table 3: Proposed experimental design regarding group allocation for future studies.
stances such as alcohol have been well documented to low-ers reaction time (Hernndez and Vogel-Sprott, 2010), while caffeine increases it (Foster, 1989; Hickey, 2014). All of these significant factors were not controlled or accounted for during the development of the experimental design due to time constraints.
There was also no control group, where participants within the group would receive no prior knowledge includ-ing explicit aids. This restricted the empirical robustness of the experiment, and so could be something to con-sider for future research developments (table 3). More-over, there was no pre-testing (prior to sensorimotor train-ing) for the trained group. This would allow for compara-tive data from non-primed performance to primed perfor-mance.
In terms of data, keystroke error data was also omitted from final analysis due to constraints regarding time. This would have allowed insights into motor planning effects in various structures of the sequences through inferring ac-celerations among correct keystrokes, suggesting patterns of automaticity. Although, the biggest drawback for the experiment possibly was the small sample size which sug-gests a lack of statistical rigour. Ideally, the number of participants to be recruited for this type of study would be n= 24 (12 per group), or n= 36 (including control). However, as this was a relatively small-scale study it was unreasonable to recruit such a large demand of partici-pants in a tight time frame. Nevertheless, these are issues that can be addressed in future studies.
perceptual learning as demonstrated by Robertson (2007) and in the findings presented. Although the disadvantage is that tasks such as SIL and SRT are both perceptually flexible between explicit and implicit processing (Tomiczek and Burke, 2008). Further investigations into the percep-tual flexibility of the trigramic typing task used in the dissertation could be left for future studies.
Further possible investigations. In light of the findings, various possible improvements and investigations could be enquired through further studies. The most evident of them all is improving the stimuli to become adaptive to skill. For example, if the participant is performing ex-ceptionally well across the training blocks, the software will attempt to speed up the task until the participant starts making errors. This throttles the participant to converge into a certain performance baseline as noted in Bojinov et al (2012). Moreover, a rhythm based task that allows for temporal anticipation may produce higher per-formance, akin to the SIL task. In terms of key selection, alphanumeric characters were randomly drawn across two left-right keyboard spaces with 4 keys drawn per space. However, if this distribution was uneven (i.e. possible unequal number of keys distributed on each space) then the combination, as illustrated below, will create a higher number of possible keys (906,192) compared to if the dis-tribution was even (313,600).
This lop-sided allocation has striking implication for cere-bral lateralisation research, as potentially key selection could involve all 6 keys distributed for one hand, primar-ily activating only one hemisphere (Sartori et al., 2013). Comparisons into left or right hemispheric activation dur-ing sensorimotor tasks could also provide interest in neu-roimaging studies. Finally, investigations into the use of EEG reading and speeding up the pace of authentication could be looked into. In this regard, specific Event Related Potentials (ERPs) could be singled out and identified as a biomarker of implicit learning. Although this could pro-vide to be quite a large-scale study which might suit a doctorate-level research.
Much in the same manner, eye-tracking technology (e.g. Tobii) could be employed in order to measure the saccadic coordination. This could be used in conjunction to the EEG, however, this would create a more richer and com-plicated experiment rather than a simple one. Ideally, a protocol should remain as simple as possible to maximise research applicability.
In terms of designing crypto primitives, creating a strong padding policy for sequences is imperative. Moreover, con-sidering the findings from the study the authentication protocol must meet the criteria which involves a Target RT baseline of <1200ms and a sequence threshold base-line with>15% performance advantage. Alongside this, a
training phase model was synthesised for a crypographi-cal model to determine whether learning has taken place or not. Implicit learning of target structures follows parity ef-fects as noted in Didierjean (2007) and is therefore based upon performance advantage over foil structures. When combined into a unitary structure, this prevents correct ex-plicit memorisation of specific sequences unless sequences appear perceptually salient (as with Type C clusters). Al-though despite this, Type C still exhibited the strongest implicit learning performance compared to the other clus-ters on the test phase. With all things considered, the find-ings from the study provides a framework for future work into sensorimotor learning as a method for multifactor au-thentication. However, the most important aspect of the research is that participants could not recognise and/or re-call fundamental sequential structures as the memory was inaccessible to conscious processing. This alone addresses the rubber hose cryptoanalysis problem, offering a viable method to secure data with passwords so secure, even the users won’t know it.
5. Acknowledgements
I would like to thank Dr. Jane Jacobs and Dr. Chris-tianne Jacobs at the Department of Psychology, University of Westminster for their continual support and guidance throughout my research. Without their insight and ex-perience, this study would not have been possible. I also owe a lot of gratitude to Dr. Maria Flynn for her inputs in the early design of the study which helped me to build the basis for this project. Furthermore, I would would like to express my appreciation of Dr. Kevin Morgan for the recommendation and oversight of my early concepts. This inevitably led to me to meet Dr. Juha Silvanto, who eventually became my project supervisor. Dr. Silvantos invaluable assistance and numerous discussions over the year has been imperative to the completion and quality of the overall dissertation. For this, I am sincerely grateful. Finally, my appreciations extend to the most important woman in my life, my Mother, whose unbridled support has made this entire project possible. Thank you.
References
Albouy, G., Sterpenich, V., Balteau, E., Vandewalle, G., Desseilles, M., Dang-Vu, T., Darsaud, A., Ruby, P., Luppi, P., Degueldre, C., Peigneux, P., Luxen, A. and Maquet, P. (2008). Both the Hippocampus and Striatum Are Involved in Consolidation of Motor Sequence Memory. Neuron,58(2),pp.261-272.
Bapi, R., Doya, K. and Harner, A. (2000). Evidence for effector independent and dependent representations and their differential time course of acquisition during motor sequence learning. Experimental Brain Research, 132(2), pp.149-162.
Bojinov, H., Sanchez, D., Reber, P., Boneh, D. and Lin-coln, P. (2012). Neuroscience Meets Cryptography: De-signing Crypto Primitives Secure Against Rubber Hose Attacks. In: 21st USENIX Security Symposium (USENIX Security12).USENIX,pp.129-141.
Burke, D. and Roodenrys, S. (2000). Implicit Learning in a Simple Cued Reaction-Time Task. Learning and
Motiva-tion, 31(4), pp.364-380.
Broyd, S., Demanuele, C., Debener, S., Helps, S., James, C. and Sonuga-Barke, E. (2009). Default-mode brain dys-function in mental disorders: A systematic review. Neuro-science & Biobehavioral Reviews, 33(3), pp.279-296.
Culham, J. and Kanwisher, N. (2001). Neuroimaging of cognitive functions in human parietal cortex. Current Opinion in Neurobiology, 11(2), pp.157-163.
Danion, J., Zimmermann, M., Willard-Schroeder, D., Grang, D., Welsch, M., Imbs, J. and Singer, L. (1990). Effects of scopolamine, trimipramine and diazepam on explicit mem-ory and repetition priming in healthy volunteers.
Psy-chopharmacology, 102(3), pp.422-424.
Denning, T., Bowers, K., Dijk, M. and Jules, A. (2011). Exploring implicit memory for painless password recov-ery. In: Proceedings of ACM CHI 2011 Conference on Hu-man Factors in Computing Systems 2011. pp.2615-2618.
Destrebecqz, A. and Cleeremans, A. (2001). Can sequence learning be implicit? New evidence with the process disso-ciation procedure. Psychonomic Bulletin & Review, 8(2), pp.343-350.
Didierjean, A. (2007). Parity effects in an implicit-learning task. British Journal of Psychology, 98(4), pp.529-545.
Dutta, A., Shah, K., Silvanto, J. and Soto, D. (2014). ral basis of non-conscious visual working memory.
Neu-roImage, 91, pp.336-343.
Fischer, B. (2007). Looking for Learning: Auditory, Vi-sual and Optomotor Processing of Children with Learning Problems. New York: Nova Science Publishers.
Foster, N. (1989). An investigation into the effects of caf-feine on reaction time. Journal of Biological Education,
23(4), pp.303-307.
Fox, M., Snyder, A., Vincent, J., Corbetta, M., Van
Es-sen, D. and Raichle, M. (2005). From The Cover: The hu-man brain is intrinsically organized into dynamic, anticor-related functional networks. Proceedings of the National Academy of Sciences, 102(27), pp.9673-9678.
Gaddy, M. and Ingram, R. (2014). A meta-analytic review of mood-congruent implicit memory in depressed mood. Clinical Psychology Review, 34(5), pp.402-416.
Goodale, M. and Milner, A. (1992). Separate visual path-ways for perception and action. Trends in Neurosciences,
15(1), pp.20-25.
Hahn, B., Shoaib, M. and Stolerman, I. (2011). Selec-tive nicotinic receptor antagonists: effects on attention and nicotine-induced attentional enhancement.
Psychophar-macology, 217(1), pp.75-82.
Halvorson, K., Wagschal, T. and Hazeltine, E. (2013). Conceptualization of task boundaries preserves implicit se-quence learning under dual-task conditions. Psychon Bull
Rev, 20(5), pp.1005-1010.
Henke, K. (2010). A model for memory systems based on processing modes rather than consciousness. Nature Re-views Neuroscience, 11(7), pp.523-532.
Hernndez, O. and Vogel-Sprott, M. (2010). Alcohol Slows the Brain Potential Associated With Cognitive Reaction Time to an Omitted Stimulus*. J. Stud. Alcohol Drugs,
71(2), pp.268-277.
Hickey, S. (2014). The study of caffeine on reaction time and error rate among college students. BSc. Dublin
Busi-ness School.
Jacoby, L., Lindsay, D. and Toth, J. (1992). Unconscious influences revealed: Attention, awareness, and control. Amer-ican Psychologist, 47(6), pp.802-809.
James, W. (1890). The Principles of Psychology (Vol. 1).
New York: Holt.
Jiang, Y., Won, B. and Swallow, K. (2014). First sac-cadic eye movement reveals persistent attentional guidance by implicit learning. Journal of Experimental Psychology: Human Perception and Performance, 40(3), pp.1161-1173.
Knowlton, B., Ramus, S. and Squire, L. (1992). Intact Artificial Grammar Learning in Amnesia: Dissociation of Classification Learning and Explicit Memory for Specific Instances. Psychological Science, 3(3), pp.172-179.
Krakauer, J. and Shadmehr, R. (2006). Consolidation of motor memory. Trends in Neurosciences, 29(1), pp.58-64.
pic-tures, and concepts: A comparison of lexical, object, and reality decisions. Journal of Verbal Learning and Verbal
Behavior, 23(1), pp.39-66.
Kulkarni, P., Satsangi, C. and Easo, S. (2012). Authoriza-tion using Implicit Password. IOSRJEN, 02(07), pp.91-95.
Lee, J. and Livesey, E. (2013). Effects of Explicit Abstract Knowledge and Simple Associations in Sequence Learning. In: Cooperative Minds: Social Interaction and Group Dy-namics. Berlin: Cognitive Science Society, pp.2843-2848.
Lozito, J. and Mulligan, N. (2010). Exploring the role of attention during implicit memory retrieval. Journal of Memory and Language, 63(3), pp.387-399.
Magill, R. (1998). Knowledge is More than We Can Talk about: Implicit Learning in Motor Skill Acquisition. Re-search Quarterly for Exercise and Sport, 69(2), pp.104-110.
Mishkin, M. and Ungerleider, L. (1982). Contribution of striate inputs to the visuospatial functions of parieto-preoccipital cortex in monkeys. Behavioural Brain
Re-search, 6(1), pp.57-77.
Mancia, M. (2006). Implicit memory and early unrepressed unconscious: Their role in the therapeutic process (How the neurosciences can contribute to psychoanalysis) 1. In-ternational Journal of Psychoanalysis, 87(1), pp.83-103.
Moussa, M., Steen, M., Laurienti, P. and Hayasaka, S. (2012). Consistency of Network Modules in Resting-State fMRI Connectome Data. PLoS ONE, 7(8), p.e44428.
Norman, D. A. (1981). The categorization of action slips.
Psychological Review, 88, pp.1-15.
Norman, J. (2002). Two visual systems and two theories of perception: An attempt to reconcile the constructivist and ecological approaches. Behavioral and Brain Sciences, 25(01).
Overmars, M., Louis, D., Ellis, D., Kay, R. and Boyarint-sev, D. (1999). Computer Software. Vers. 7.5.87. GameMaker Pro for OS X. YoYo Games., 22 Jan. 2014.
Pew, R. W. (1974). Levels of Analysis in Motor Control.
Brain Research, 71, pp.393-400.
Posner, M. (1978). Chronometric explorations of mind. Hillsdale, N.J.: L. Erlbaum Associates.
Repp, B. and Su, Y. (2013). Sensorimotor synchroniza-tion: A review of recent research (20062012). Psychon Bull
Rev, 20(3), pp.403-452.
Richards, H., Benson, V., Donnelly, N. and Hadwin, J. (2014). Exploring the function of selective attention and hypervigilance for threat in anxiety. Clinical Psychology
Review, 34(1), pp.1-13.
Robertson, E. (2007). The Serial Reaction Time Task: Implicit Motor Skill Learning?. Journal of Neuroscience,
27(38), pp.10073-10075.
Rosenbaum, D. (2010). Human motor control. 2nd ed.
San Diego: Academic Press.
Rosenbaum, D. (1980). Human movement initiation: spec-ification of arm, direction, and extent. Journal of Experi-mental Psychology: General, 109(4), pp.444-74.
Rosenbaum, D. (2005). The Cinderella of Psychology: The Neglect of Motor Control in the Science of Mental Life and Behavior. American Psychologist, 60(4), pp.308-317.
Rossion, B. and Pourtois, G. (2001). Revisiting snodgrass and Vanderwart’s object database: Color and texture im-prove object recognition. Journal of Vision, 1(3), pp.413-413.
Sakai, K., Ramnani, N., Passingham, R. E. (2002). Learn-ing of sequences of fLearn-inger movements and timLearn-ing: Frontal lobe and action-oriented representation. Journal of
neuro-physiology, 88(4), pp.2035-2046.
Sartori, L., Begliomini, C. and Castiello, U. (2013). Motor resonance in left- and right-handers: evidence for effector-independent motor representations. Front. Hum.
Neu-rosci., 7.
Schmidt, R. and Lee, T. D. (2011). Motor control and learning. Champaign, Ill.: Human Kinetics Publishers.
Schmidt, R., Wrisberg, C. (2008). Motor learning & per-formance. Champaign, Ill.: Human Kinetics Books.
Song, S., Howard, J. and Howard, D. (2007). Implicit probabilistic sequence learning is independent of explicit awareness. Learning & Memory, 14(3), pp.167-176.
Squire, L. (2009). Memory and Brain Systems: 1969-2009. Journal of Neuroscience, 29(41), pp.12711-12716.
Srinivas, K. (1993). Perceptual specificity in nonverbal priming. Journal of Experimental Psychology: Learning, Memory, and Cognition, 19(3), pp.582-602.
Stubblefield, A. and Simon, D. (2004). Inkblot
Authenti-cation. Microsoft Research.
cued reaction-time task. Learning and Motivation, 39(2), pp.95-113.
Topolinski, S. (2012). The sensorimotor contributions to implicit memory, familiarity, and recollection. Journal of Experimental Psychology: General, 141(2), pp.260-281.
Weinshall, D. and Kirkpartick, S. (2004). Passwords you’ll never forget, but can’t recall. In: CHI ’04 Extended Ab-stracts on Human Factors in Computing Systems. New
York: ACM, pp.1399-1402.
Whiting, H. T. A. (1989). Toward a Cognitive Psychol-ogy of Human Movement. In P. C. W van Wieringen & R. J, /bootsma (Eds.), Catching up: Selected essays of H. T. A Whiting (pp. 195-230). Amsterdam: Free University Press.
Wickens, C. and McCarley, J. (2008). Applied attention
theory. Boca Raton: CRC Press.
Wulf, G. and Schmidt, R. (1997). Variability of practice and implicit motor learning. Journal of Experimental Psy-chology: Learning, Memory, and Cognition, 23(4), pp.987-1006.
Xcode. (2015). Computer software. Vers. 6.3. Apple Inc.,
8 Apr. 2015. Web. 8 Apr. 2015.
Yu, C. and Smith, L. (2011). What you learn is what you see: using eye movements to study infant cross-situational word learning. Developmental Science, 14(2), pp.165-180.