Copyright © 2001 O'Reilly & Associates, Inc. All rights reserved.
Perl for System Administration By David N. Blank-Edelman ISBN 1-56592-609-9
Print book copyright © 2000 O'Reilly & Associates, Inc. All rights reserved. Published by O'Reilly & Associates, Inc., 101 Morris Street, Sebastopol, CA 95472.
This electronic publication is intended for use by one individual. As such, you may make copies for your own personal use. However, you may not provide copies to others, or make this publication available to others over a LAN or other network. You may not reprint, offer for sale, or otherwise re-use material from this publication without the explicit written permission of O'Reilly & Associates, Inc.
You can purchase print editions of these books directly from O'Reilly & Associates, Inc. or from bookstores that carry O'Reilly & Associates books.
Logos and Trademarks
The O'Reilly logo is a registered trademark of O'Reilly & Associates, Inc. Many of the designations used by manufacturers and sellers to distinguish their
products are claimed as trademarks. Where those designations appear in this book, and O'Reilly & Associates, Inc. was aware of a trademark claim, the designations have been printed in caps or initial caps.
Disclaimer
While every precaution has been taken in the preparation of this product, the publisher assumes no responsibility for errors or omissions, or for damages resulting from the use of the information contained herein.
Colophon
Our look is the result of reader comments, our own experimentation, and feedback from distribution channels. Distinctive covers complement our distinctive approach to technical topics, breathing personality and life into potentially dry subjects.
The animal on the cover of Perl for System Administration is a sea otter. North American sea otters make their homes along the Pacific coast, near the kelp beds containing the shellfish that make up the majority of their diet. Sea otters can be found in great numbers in Alaska, and on beaches as far south as California. Sea otters are agile and intelligent mammals, and are known to make ingenious use of tools. Floating on their backs, they hold a shellfish such as a mussel or abalone on their bellies, and use a rock to break the shell.
Intensely social, sea otters gather to float in groups called rafts. They are
excellent swimmers, propelling themselves swiftly through the water with their flipper-like, webbed back paws. Their thick fur provides them with efficient insulation in the water. At times, their existence has been threatened as they have been mercilessly hunted to near extinction for their fur.
Colleen Gorman was the production editor and copyeditor for Perl for System Administration. Jane Ellin was the proofreader. Mary Sheehan and Emily Quill provided quality control. Molly Shangraw, Maeve O'Meara, Gabe Weiss, Mary Sheehan, and Darren Kelly provided production support. Nancy Crumpton wrote the index.
Hanna Dyer designed the cover of this book, based on a series design by Edie Freedman. The cover image is an original illustration created by Lorrie LeJeune. Emma Colby produced the cover layout with QuarkXPress 3.32 using Adobe's ITC Garamond font.
Photoshop 5. This colophon was written by Colleen Gorman.
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Index: Symbols
There are no index entries for this letter.
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
V | W | X | Y | Z
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Index: A
Access Control List (ACL): 2.2.2. Microsoft Windows NT/2000
account creation/deletion, programs for
Unix: 3.3.2.1. Unix account creation and deletion routines
Windows NT/2000: 3.3.2.2. Windows NT/2000 account creation and deletion routines
account systems: 3.3.1. The Backend Database
building: 3.3. Building an Account System to Manage Users
databases, use in: 3.3.1. The Backend Database
Active Directory: 6.5. ADSI (Active Directory Service Interfaces)
Active Directory Service Interfaces (see ADSI)
ActiveState repository: 1.5. Locating and Installing Modules
ActiveX Data Objects (see ADO)
adcomplain program: 8.3.3. Tracking Down Spam
ADO (ActiveX Data Objects): 6.5.6. Searching
ADSI (Active Directory Service Interfaces): 3.2.1. NT/2000 User Identity Storage and Access
6.5. ADSI (Active Directory Service Interfaces) 6.5.1. ADSI Basics
resources for using: 6.5.1. ADSI Basics
searches in: 6.5.6. Searching
system administration with: 6.5.8. Working with Users via ADSI
using from Perl: 6.5.2. Using ADSI from Perl
ADSIDump program: 6.5.5. So How Do You Know Anything About an Object?
ADsPaths: 6.5.1. ADSI Basics
6.5.5. So How Do You Know Anything About an Object?
6.5.7. Performing Common Tasks Using the WinNT and LDAP Namespaces
algorithm, message-digest: 10.1.1. Local Filesystem Changes
American Registry for Internet Numbers (ARIN): 8.3.3.2. Checking against Internet-wide blacklists
APNIC (Asia Pacific Address Allocations): 8.3.3.2. Checking against Internet-wide blacklists
Apple Events: 8.1.2. Using the OS-Specific IPC Framework.
8.1.2. Using the OS-Specific IPC Framework.
@ARGV, retrieving under Mac OS: 2.4. Walking the Filesystem Using the File::Find Module
ARIN (American Registry for Internet Numbers): 8.3.3.2. Checking against Internet-wide blacklists
Asia Pacific Address Allocations (APNIC): 8.3.3.2. Checking against Internet-wide blacklists
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
V | W | X | Y | Z
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Index: B
base DN (LDAP): 6.4.3. Performing LDAP Searches
Berkeley DB
format: 9.5.4.1. Using Perl-only databases
module: 8.3.3.1. Checking against a local blacklist
Berkeley Fast File System: 2.2.1. Unix
bigbuffy program: 9.4.2. Circular Buffering
bind DN (LDAP): 6.4.2. The Initial LDAP Connection
blacklists, checking spam against
Internet-wide: 8.3.3.2. Checking against Internet-wide blacklists
local: 8.3.3.1. Checking against a local blacklist
blat program: 8.1.1. Getting sendmail (or Similar Mail Transport Agent)
bots: 4.4.2. Tracking Operations in Unix
security and: 4.3.4. Using the Proc::ProcessTable Module
BSD 4.4 password files: 3.1.3. Binary Database Format in BSD 4.4
building account systems: 3.3. Building an Account System to Manage Users
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
V | W | X | Y | Z
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Index: C
chpasswd command (BSD 4.4): 3.1.3. Binary Database Format in BSD 4.4
ci command (RCS): A. The Five-Minute RCS Tutorial
CIM (Common Information Model): 4.2.4. Using Window Management Instrumentation (WMI)
CIM Schema: 4.2.4. Using Window Management Instrumentation (WMI)
clog program: 10.4.1. Perl Saves the Day
closure programming construct: 8.2.1.1. Controlling the frequency of mail
co command (RCS): A. The Five-Minute RCS Tutorial
Collaborative Data Objects Library: 8.1.2. Using the OS-Specific IPC Framework.
COM (Component Object Model): 4.2.4. Using Window Management Instrumentation (WMI)
6.5.1. ADSI Basics
Common Information Model (CIM): 4.2.4. Using Window Management Instrumentation (WMI)
Component Object Model (see COM)
Comprehensive Perl Archive Network (see CPAN) configuration files
DNS
administrative header: 5.3.1.1. Creating the administrative header
generating multiple: 5.3.1.2. Generating multiple configuration files
reading, security of: 1.6.3. Be Careful When Reading Data
container objects (COM): 6.5.1. ADSI Basics
6.5.3. Dealing with Container/Collection Objects
identifying: 6.5.4. Identifying a Container Object
CPAN (Comprehensive Perl Archive Network): 1.5. Locating and Installing Modules
modules, installing on Unix: 1.5.1. Installing Modules on Unix
CPAN Search: 1.5. Locating and Installing Modules
Crack program: 10.5. Preventing Suspicious Activities
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Index: D
Data Source Name (DSN): 7.3. Using the ODBC Framework
data structures, transforming: 3.3.1.4. Writing XML using XML::Simple
database handle, DBI: 7.3. Using the ODBC Framework
Database Interface (see DBI) databases
analyzing log files with: 9.5.4. Using Databases
generating DNS configuration files from: 5.3.1. Generating DNS Configuration Files
generating host files from: 5.1.1. Generating Host Files
error checking while: 5.1.2. Error Checking the Host File Generation Process
improving output while: 5.1.3. Improving the Host File Output
MySQL: D. The Fifteen-Minute SQL Tutorial
relational: D.5. Relating Tables to Each Other
SAM: 3.2.1. NT/2000 User Identity Storage and Access
SQL
creating/deleting: D.1. Creating /Deleting Databases and Tables
documenting from Perl: 7.4. Server Documentation
interacting with from Perl: 7.1. Interacting with an SQL Server from Perl
managing logins from Perl: 7.5. Database Logins
manipulating data in: D.3.3. Simple Manipulation of Data Returned by Queries
monitoring from Perl: 7.6. Monitoring Server Health
Perl-cliented: 9.5.4.2. Using Perl-cliented SQL databases
querying information: D.3. Querying Information
stored procedures: D.6.3. Stored Procedures
using DBI: 7.2. Using the DBI Framework
using ODBC: 7.3. Using the ODBC Framework
tracking network host data with: 5.1.1. Generating Host Files
use in account systems: 3.3.1. The Backend Database
DBAs (database administrators): 7. SQL Database Administration
DBD modules: 7.1. Interacting with an SQL Server from Perl
7.1. Interacting with an SQL Server from Perl
DBD\:\:Sybase module: 7.1. Interacting with an SQL Server from Perl
DB_File module: 9.5.4.1. Using Perl-only databases
DBI (Database Interface) module for documenting
MySQL server: 7.4.1. MySQL Server via DBI
Sybase server: 7.4.2. Sybase Server via DBI
architecture of: 7.1. Interacting with an SQL Server from Perl
database handle: 7.3. Using the ODBC Framework
placeholders: 7.2. Using the DBI Framework
statement handle: 7.2. Using the DBI Framework
using from Perl: 7.2. Using the DBI Framework
denial-of-service attack: 10.4.1. Perl Saves the Day
Dial-Up User List: 8.3.3.2. Checking against Internet-wide blacklists
Digest\:\:MD5 module: 10.1.1. Local Filesystem Changes 10.1.2. Network Service Changes
directories: 6.1. What's a Directory?
auditing: 4.4.1. Tracking Operations on Windows NT/2000
entries in
adding/deleting: 6.4.6. Adding Entries with Standard LDAP Operations
modifying: 6.4.8. Modifying Entry Names
hidden, searching for: 10.2.1. Local Signs of Peril
searches of
ADSI: 6.5.6. Searching
LDAP: 6.4.3. Performing LDAP Searches
Directory Information Tree (DIT): B.1. LDAP Data Organization
directory services: 6. Directory Services
Finger: 6.2. Finger: A Simple Directory Service
LDAP: 6.4. LDAP: A Sophisticated Directory Service
WHOIS: 6.3. The WHOIS Directory Service
Net\:\:Whois, using with: 6.3. The WHOIS Directory Service
X.500: 6.4. LDAP: A Sophisticated Directory Service
directory tree: B.1. LDAP Data Organization
disks, full
alleviating: 2.4. Walking the Filesystem Using the File::Find Module
of logging output: 9.4. Disk Space Problems
Distinguished Name (DN): B.1. LDAP Data Organization
Management Instrumentation (WMI)
DIT (Directory Information Tree): B.1. LDAP Data Organization
DMTF (Distributed Management Task Force): 4.2.4. Using Window Management Instrumentation (WMI)
DN (Distinguished Name): B.1. LDAP Data Organization
root: 6.4.2. The Initial LDAP Connection
DNS (Domain Name Service): 5.3. Domain Name Service (DNS)
configuration files
administrative header: 5.3.1.1. Creating the administrative header
generating multiple: 5.3.1.2. Generating multiple configuration files
packets: 5.3.2.2. Working with raw network sockets
querying from Perl
using Net\:\:DNS: 5.3.2.3. Using Net::DNS
using nslookup: 5.3.2.1. Using nslookup
using raw sockets: 5.3.2.2. Working with raw network sockets
Document Type Definition (DTD): C.2. XML Is Picky
documenting databases with DBI module
MySQL server: 7.4.1. MySQL Server via DBI
Sybase server: 7.4.2. Sybase Server via DBI
with Win32\:\:ODBC module, MS-SQL server: 7.4.3. MS-SQL Server via ODBC
Domain Name Service (see DNS) driver, Linux: 2.1. Perl to the Rescue
DSN (Data Source Name): 7.3. Using the ODBC Framework
DTD (Document Type Definition): C.2. XML Is Picky
dynamically linked libraries (DLLs), used by processes: 4.2.2. Using the Win32::IProc Module
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
V | W | X | Y | Z
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Index: E
edquota command (Unix): 2.5.1. Editing Quotas with edquota Trickery
eggdrop bot: 4.3.4. Using the Proc::ProcessTable Module
ElDump program: 9.5.1. Stream Read-Count
electronic mail (see email) email
as support medium: 8.3.4. Support Mail Augmentation
dissecting mailboxes/messages: 8.3. Receiving Mail
log file parsing: 9.5.3. Black Boxes
relaying: 8.3.3. Tracking Down Spam
sending from Perl: 8.1. Sending Mail
limiting frequncy and amount of: 8.2.1.1. Controlling the frequency of mail
Mac OS: 8.1.2. Using the OS-Specific IPC Framework.
mistakes in: 8.2. Common Mistakes in Sending Email
Windows NT/2000: 8.1.1. Getting sendmail (or Similar Mail Transport Agent)
8.1.2. Using the OS-Specific IPC Framework.
spam (see spam)
subject line of, writing useful: 8.2.2. Subject Line Waste
support mail, augmenting: 8.3.4. Support Mail Augmentation
tool for system administration: 8. Electronic Mail
/etc/hosts: 5.1. Host Files 5.1. Host Files
5.2. NIS, NIS+, and WINS
/etc/passwd: 5.2. NIS, NIS+, and WINS
security and: 10.1.1. Local Filesystem Changes
Eudora program: 8.1.2. Using the OS-Specific IPC Framework.
event handlers: 3.3.1.2. Reading XML using XML::Parser
Event Log Service: 9.2.3. Using the OS's Logging API
Event Viewer program: 9.2.3. Using the OS's Logging API
Extensible Markup Language (see XML)
V | W | X | Y | Z
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Index: F
FAT filesystems: 2.2.2. Microsoft Windows NT/2000
file operations: 4. User Activity
tracking
Unix: 4.4.2. Tracking Operations in Unix
Windows NT/2000: 4.4.1. Tracking Operations on Windows NT/2000
file shares, managing with ADSI: 6.5.10. Working with File Shares via ADSI
File\:\:Find module: 2.4. Walking the Filesystem Using the File::Find Module
on Mac OS: 2.4. Walking the Filesystem Using the File::Find Module
on Unix: 2.4. Walking the Filesystem Using the File::Find Module 2.4. Walking the Filesystem Using the File::Find Module
on Windows NT: 2.4. Walking the Filesystem Using the File::Find Module
finding hidden directories with: 10.2.1. Local Signs of Peril
when not to use: 2.4. Walking the Filesystem Using the File::Find Module
filenames, long, finding: 2.4. Walking the Filesystem Using the File::Find Module
files
auditing on Windows NT/2000: 4.4.1. Tracking Operations on Windows NT/2000
changes to, detecting: 10.1.1. Local Filesystem Changes
finding
core: 2.3. Walking or Traversing the Filesystem
damaged: 2.1. Perl to the Rescue
2.3. Walking or Traversing the Filesystem
extraneous: 2.4. Walking the Filesystem Using the File::Find Module
Windows NT/2000 hidden: 2.4. Walking the Filesystem Using the File::Find Module
locking: 3.3.4. Account System Wrap-Up
log (see log files)
open, tracking: 4.4.1. Tracking Operations on Windows NT/2000
writing to, security of: 1.6.4. Be Careful When Writing Data 9.4.2.2. Security in log processing programs
File\:\:Spec module: 2.2.5. Dealing with Filesystem Differences from Perl
File\:\:Stat module: 10.1.1. Local Filesystem Changes
Filesys\:\:DiskFree module: 2.6. Querying Filesystem Usage
Filesys\:\:DiskSpace module: 2.6. Querying Filesystem Usage
filesystems
Berkeley Fast File System: 2.2.1. Unix
differences between: 2.2. Filesystem Differences
FAT: 2.2.2. Microsoft Windows NT/2000
Mac OS: 2.2.3. MacOS
NTFS: 2.2.2. Microsoft Windows NT/2000
querying usage: 2.6. Querying Filesystem Usage
traversing/walking: 2.3. Walking or Traversing the Filesystem
Mac OS: 2.4. Walking the Filesystem Using the File::Find Module
Unix: 2.3. Walking or Traversing the Filesystem
Windows NT/2000: 2.3. Walking or Traversing the Filesystem
Unix: 2.2.1. Unix
VFAT: 2.2.2. Microsoft Windows NT/2000
Windows NT/2000: 2.2.2. Microsoft Windows NT/2000
finding damaged files on: 2.3. Walking or Traversing the Filesystem
find2perl command: 2.4. Walking the Filesystem Using the File::Find Module
Finger: 6.2. Finger: A Simple Directory Service
fping program: 10.4.1. Perl Saves the Day
FreeTDS libraries: 7.1. Interacting with an SQL Server from Perl
FreezeThaw module: 9.5.4.1. Using Perl-only databases 10.1.2. Network Service Changes
FTP transfers, correlating: 9.5.2. Read-Remember-Process
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
V | W | X | Y | Z
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Index: G
GCOS field (Unix): 3.1.1. The Classic Unix Password File
GetFileInfo function (MacPerl): 2.4. Walking the Filesystem Using the File::Find Module
Getopt\:\:Std module: 10.1.1. Local Filesystem Changes
GetWindowProperties function (Windows NT/2000): 4.2.3. Using the Win32::Setupsup Module
GID (group ID): 3.1.1. The Classic Unix Password File
GNU RCS 5.7: 5.1.4. Incorporating a Source Code Control System
GO command (SQL): D.1. Creating /Deleting Databases and Tables
group ID (GID): 3.1.1. The Classic Unix Password File
groups, managing with ADSI: 6.5.9. Working with Groups via ADSI
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
V | W | X | Y | Z
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Index: H
help desk, using email for: 8.3.4. Support Mail Augmentation
HFS (Hierarchical File System): 2.2.3. MacOS 2.2.3. MacOS
home directory field (Unix): 3.1.1. The Classic Unix Password File
host files: 5.1. Host Files
\\\\$systemroot$\\\\system32\\\\drivers\\\\etc\\\\hosts file: 5.1. Host Files
generating from a database: 5.1.1. Generating Host Files
error checking while: 5.1.2. Error Checking the Host File Generation Process
improving output while: 5.1.3. Improving the Host File Output
generating, modules for: 6.4.10. Putting It All Together
Macintosh HD\:System Folder\:Preferences\:hosts: 5.1. Host Files
parsing: 5.1. Host Files
reading from Perl: 5.1. Host Files
source control systems and: 5.1.4. Incorporating a Source Code Control System
Unix: 5.1. Host Files
hostnames, mapping to IP addresses Unix: 5.1. Host Files
Windows NT: 5.2.2. Windows Internet Name Server ( WINS)
h2xs program: 10.5. Preventing Suspicious Activities
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
V | W | X | Y | Z
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Index: I
INSERT command (SQL): D.2. Inserting Data into a Table
interface-defined properties: 6.5.1. ADSI Basics
Internet Protocol (see TCP/IP)
Internet Service Providers (ISPs), complaining to: 8.3.3. Tracking Down Spam
InterNIC/Network Solutions WHOIS server, contacting: 6.3. The WHOIS Directory Service
interprocess communication (IPC): 8.1.2. Using the OS-Specific IPC Framework.
IO\:\:Socket module: 8.2.1.2. Controlling the amount of mail
IP addresses: 5. TCP/IP Name Services 5.1. Host Files
(see also host files)
checking to find source of spam: 8.3.3. Tracking Down Spam
contacting owners of: 6.3. The WHOIS Directory Service
looking up: 5.2. NIS, NIS+, and WINS
mapping to names
Unix: 5.1. Host Files
Windows NT: 5.2.2. Windows Internet Name Server ( WINS)
IPC (interprocess communication): 8.1.2. Using the OS-Specific IPC Framework.
IRC bots, finding while running: 4.3.4. Using the Proc::ProcessTable Module
ISPs (Internet Service Providers), complaining to: 8.3.3. Tracking Down Spam
iterative development: 5.3.2. DNS Checking: An Iterative Approach
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
V | W | X | Y | Z
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Index: J
John the Ripper program: 10.5. Preventing Suspicious Activities
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
V | W | X | Y | Z
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Index: K
kernel process structures, examining: 4.3.2. Examining the Kernel Process Structures
kill.exe (Windows NT/2000): 4.2.1. Using the Microsoft Resource Kit Binaries
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
V | W | X | Y | Z
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Index: L
last command (Unix): 9.2.2. Calling an OS (or Someone Else's) Binary 9.5.4.1. Using Perl-only databases
9.5.4.2. Using Perl-cliented SQL databases
LDAP Data Interchange Format (see LDIF) LDAP entries
attributes
in search operations: 6.4.3. Performing LDAP Searches 6.4.3. Performing LDAP Searches
methods for retrieving: 6.4.4. Entry Representation in Perl
modifying: 6.4.9. Modifying Entry Attributes
separators: 6.4.10. Putting It All Together
values, quoting: 6.4.2. The Initial LDAP Connection
modifying with Perl: 6.4.8. Modifying Entry Names
representation in Perl: 6.4.4. Entry Representation in Perl
LDAP (Lightweight Directory Access Protocol): 6.4. LDAP: A Sophisticated Directory Service
anonymous authentication: 6.4.2. The Initial LDAP Connection
data organization of: B.1. LDAP Data Organization
objectClass attribute: B. The Ten-Minute LDAP Tutorial
Perl modules, comparing: 6.4.1. LDAP Programming with Perl
tutorial: B. The Ten-Minute LDAP Tutorial
LDAP operations
adding/deleting: 6.4.6. Adding Entries with Standard LDAP Operations
binding: 6.4.2. The Initial LDAP Connection
searching: 6.4.3. Performing LDAP Searches
LDIF (LDAP Data Interchange Format): 6.4.3. Performing LDAP Searches 6.4.10. Putting It All Together
reading/writing
directory entries with: 6.4.5. Adding Entries with LDIF
from Perl: 6.4.5. Adding Entries with LDIF
leaf objects (LDAP): 6.5.1. ADSI Basics
6.5.3. Dealing with Container/Collection Objects
libcrack library: 10.5. Preventing Suspicious Activities
libpcap library: 10.4.1. Perl Saves the Day 10.4.1. Perl Saves the Day
Lightweight Directory Access Protocol (see LDAP)
LIKE wildcards (SQL): D.3.2. Retrieving a Subset of the Rows in a Table
Linux
directories, hidden: 10.2.1. Local Signs of Peril
driver: 2.1. Perl to the Rescue
NIS+ and: 5.2.1. NIS+
privileges on, dropping: 1.6.2. Drop Your Privileges as Soon as Possible
Sybase OpenClient libraries and: 7.1. Interacting with an SQL Server from Perl
lockfile program: 3.3.4. Account System Wrap-Up
log files: 9. Log Files
analyzing: 9.5. Log Analysis
black box approach: 9.5.3. Black Boxes
database approach: 9.5.4. Using Databases
read-remember-process: 9.5.2. Read-Remember-Process
stream read-count: 9.5.1. Stream Read-Count
binary: 9.2. Binary Log Files
Event Log Service: 9.2.3. Using the OS's Logging API
wtmp: 9.2. Binary Log Files
circular buffering of: 9.4.2. Circular Buffering
disk space problems and: 9.4. Disk Space Problems
mail log data, summarizing: 9.5.3. Black Boxes
rotating: 9.4.1. Log Rotation
security of, when processing: 9.4.2.2. Security in log processing programs
stateful vs. stateless: 9.3. Stateful and Stateless Data
text: 9.1. Text Logs
Logfile\:\:Rotate module: 9.4.1. Log Rotation
L0phtCrack program: 10.5. Preventing Suspicious Activities
lsof program: 4.4.2. Tracking Operations in Unix
lstat() function (Perl): 10.1.1. Local Filesystem Changes
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
V | W | X | Y | Z
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Index: M
Mac OSemail, sending: 8.1.2. Using the OS-Specific IPC Framework.
filesystem: 2.2.3. MacOS
querying usage on: 2.6. Querying Filesystem Usage
traversing/walking: 2.4. Walking the Filesystem Using the File::Find Module
modules for: 1.5. Locating and Installing Modules
installing: 1.5.3. Installing Modules on MacOS
process control: 4.1. MacOS Process Control
reading @ARGV from a dialog: 2.4. Walking the Filesystem Using the File::Find Module
Mac\:\:Apps\:\:Launch module: 4.1. MacOS Process Control
Mac\:\:Glue module: 8.1.2. Using the OS-Specific IPC Framework.
MacPerl Module Porters: 1.5. Locating and Installing Modules
Mac\:\:Processes module: 4.1. MacOS Process Control
Mail Abuse Prevention System Realtime Blackhole List (RBL): 8.3.3.2. Checking against Internet-wide blacklists
mail transport agent (MTA): 8.1.1. Getting sendmail (or Similar Mail Transport Agent)
mailboxes, components of: 8.3.2. Dissecting a Whole Mailbox
Mail\:\:Folder module: 8.3.2. Dissecting a Whole Mailbox
Mail\:\:Header module: 8.3.1. Dissecting a Single Message 8.3.3. Tracking Down Spam
Mail\:\:Internet module: 8.3.1. Dissecting a Single Message
Mail\:\:Mailer module: 8.1.3. Speaking to the Mail Protocols Directly
Mail\:\:POP3Client module: 8.3. Receiving Mail
Mail\:\:Sendmail module: 8.1.3. Speaking to the Mail Protocols Directly
MailTools package: 8.1.3. Speaking to the Mail Protocols Directly 8.1.3. Speaking to the Mail Protocols Directly
Makefile (in /var/yp): 5.2. NIS, NIS+, and WINS
Managed Object Format (MOF): 4.2.4. Using Window Management Instrumentation (WMI)
Management Information Base (see MIB)
managing
file shares: 6.5.10. Working with File Shares via ADSI
groups: 6.5.9. Working with Groups via ADSI
printers: 6.5.11. Working with Print Queues and Print Jobs via ADSI
user accounts, scripts for: 3.3.3. The Process Scripts
MAPI (Messaging Application Programming Interface): 8.1.2. Using the OS-Specific IPC Framework.
mapping hostnames to IP addresses: 5.1. Host Files 5.2.2. Windows Internet Name Server ( WINS)
message-digest algorithms: 10.1.1. Local Filesystem Changes
Messaging Application Programming Interface (MAPI): 8.1.2. Using the OS-Specific IPC Framework.
MIB (Management Information Base): 10.3.1. Using SNMP from Perl 10.3.1. Using SNMP from Perl
E. The Twenty-Minute SNMP Tutorial E.1. SNMP in Practice
E.1. SNMP in Practice
Microsoft SQL Server
communicating with Unix machines: 7.1. Interacting with an SQL Server from Perl
documenting via ODBC module: 7.4.3. MS-SQL Server via ODBC
modules
for log files
Windows NT/2000: 9.2.3. Using the OS's Logging API
analyzing: 9.5.1. Stream Read-Count
rotating: 9.4.1. Log Rotation
choosing: 3.3.2.2. Windows NT/2000 account creation and deletion routines
command-line parsing: 10.1.1. Local Filesystem Changes
comparing: 10.3.1. Using SNMP from Perl
CPAN: 1.5. Locating and Installing Modules
data structures, encoding as strings: 9.5.4.1. Using Perl-only databases 10.1.2. Network Service Changes
databases, documenting: 7.4.1. MySQL Server via DBI 7.4.2. Sybase Server via DBI
date/time, converting to Unix epoch: 9.5.2. Read-Remember-Process
DBI, driver for: 7.1. Interacting with an SQL Server from Perl 7.1. Interacting with an SQL Server from Perl
directories
hidden, finding: 10.2.1. Local Signs of Peril
recursive, deleting: 3.3.2.2. Windows NT/2000 account creation and deletion routines
disk quotas, manipulating: 2.5. Manipulating Disk Quotas
DNS, querying from Perl: 5.3.2.3. Using Net::DNS
dissecting mailboxes/messages: 8.3. Receiving Mail
filtering addresses: 9.5.3. Black Boxes
sending on Mac OS using AppleEvents: 8.1.2. Using the OS-Specific IPC Framework.
sending on Unix: 8.2.1.2. Controlling the amount of mail
sending on Windows NT: 8.1.2. Using the OS-Specific IPC Framework.
tracking statistics: 9.5.3. Black Boxes
transferring: 8.3. Receiving Mail
event-based: 3.3.1.2. Reading XML using XML::Parser
file operations, tracking on Windows NT/2000: 4.4.1. Tracking Operations on Windows NT/2000
files
detecting changes to: 10.1.1. Local Filesystem Changes 10.1.1. Local Filesystem Changes
10.1.1. Local Filesystem Changes
finding: 2.4. Walking the Filesystem Using the File::Find Module
locking: 3.3.4. Account System Wrap-Up
filesystems
querying usage: 2.6. Querying Filesystem Usage
traversing/walking: 2.4. Walking the Filesystem Using the File::Find Module
Finger operations, performing: 6.2. Finger: A Simple Directory Service 6.2. Finger: A Simple Directory Service
hostname, retrieving: 9.5.4.1. Using Perl-only databases
installing
on Mac OS: 1.5.3. Installing Modules on MacOS
on Unix: 1.5.1. Installing Modules on Unix
on Windows NT/2000: 1.5.2. Installing Modules on Win32
installing software with: 4.2.3. Using the Win32::Setupsup Module
interprocess: 8.1.2. Using the OS-Specific IPC Framework. 8.2.1.2. Controlling the amount of mail
launching processes from: 4.2.2. Using the Win32::IProc Module
LDAP
programming: 6.4.1. LDAP Programming with Perl
providing SSL-encrypted sessions: 6.4.2. The Initial LDAP Connection
locating: 1.5. Locating and Installing Modules
networks
detecting changes to: 10.1.2. Network Service Changes
establishing connection to: 6.2. Finger: A Simple Directory Service
monitoring: 10.3.1. Using SNMP from Perl
scripting communication: 8.1.3. Speaking to the Mail Protocols Directly
testing connectivity to hosts: 10.4.1. Perl Saves the Day
NIS data, getting: 5.2. NIS, NIS+, and WINS
open ports on Windows NT/2000, listing: 4.4.1. Tracking Operations on Windows NT/2000
owner of host, finding: 6.4.10. Putting It All Together
packets, dissecting: 10.4.1. Perl Saves the Day
passwords, reading: 10.5. Preventing Suspicious Activities
pathnames, parsing: 2.4. Walking the Filesystem Using the File::Find Module
process control
on Mac OS: 4.1. MacOS Process Control
on Unix: 4.3.4. Using the Proc::ProcessTable Module
on Windows NT/2000: 4.2.2. Using the Win32::IProc Module
switch processing: 2.5.1. Editing Quotas with edquota Trickery
SYN packets, finding: 10.4.1. Perl Saves the Day
user accounts
adding/removing: 3.3.2.2. Windows NT/2000 account creation and deletion routines
checking: 3.1.1. The Classic Unix Password File
Windows NT/2000, managing: 3.2.1. NT/2000 User Identity Storage and Access
3.2.5. NT/2000 User Rights
for using
ADSI from Perl: 6.5.2. Using ADSI from Perl
Berkeley libraries: 8.3.3.1. Checking against a local blacklist 9.5.4.1. Using Perl-only databases
ODBC: 7.3. Using the ODBC Framework
sockets: 8.2.1.2. Controlling the amount of mail
WHOIS clients, creating: 6.3. The WHOIS Directory Service
writing your own: 10.5. Preventing Suspicious Activities
XML
debugging output: 3.3.1.2. Reading XML using XML::Parser
reading/writing: 3.3.1.1. Writing XML from Perl
MOF (Managed Object Format): 4.2.4. Using Window Management Instrumentation (WMI)
monitoring networks
using Perl: 10.4.1. Perl Saves the Day
using SNMP from Perl: 10.3.1. Using SNMP from Perl
security
detecting changes: 10.1. Noticing Unexpected or Unauthorized Changes
suspicious activities: 10.5. Preventing Suspicious Activities
Mozilla\:\:LDAP module: 6.4.1. LDAP Programming with Perl 6.4.2. The Initial LDAP Connection
6.4.5. Adding Entries with LDIF
directory entries
adding/deleting: 6.4.6. Adding Entries with Standard LDAP Operations
modifying: 6.4.8. Modifying Entry Names
searching: 6.4.3. Performing LDAP Searches
generating host file with: 6.4.10. Putting It All Together
msgina.dll file, security and: 10.1.1. Local Filesystem Changes
MTA (mail transport agent): 8.1.1. Getting sendmail (or Similar Mail Transport Agent)
MySQL
database: D. The Fifteen-Minute SQL Tutorial
server, documenting via DBI module: 7.4.1. MySQL Server via DBI
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
V | W | X | Y | Z
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Index: N
name services (see TCP/IP, name services) namespaces
ADSI: 6.5.1. ADSI Basics
LDAP: 6.5.7. Performing Common Tasks Using the WinNT and LDAP Namespaces
WinNT: 6.5.7. Performing Common Tasks Using the WinNT and LDAP Namespaces
needspace script: 2.4. Walking the Filesystem Using the File::Find Module 2.4. Walking the Filesystem Using the File::Find Module
net command (Windows NT/2000): 3.2.1. NT/2000 User Identity Storage and Access
3.2.1. NT/2000 User Identity Storage and Access
Net\:\:DNS module: 5.3.2.3. Using Net::DNS 10.1.2. Network Service Changes
Net\:\:Finger module: 6.2. Finger: A Simple Directory Service
Net\:\:LDAP module: 6.4.1. LDAP Programming with Perl 6.4.2. The Initial LDAP Connection
6.4.5. Adding Entries with LDIF
directory entries
adding/deleting: 6.4.6. Adding Entries with Standard LDAP Operations
modifying: 6.4.8. Modifying Entry Names
netmail95 program: 8.1.1. Getting sendmail (or Similar Mail Transport Agent)
Net\:\:NIS module: 5.2. NIS, NIS+, and WINS
Net\:\:NISPlus module: 5.2.1. NIS+
NetPacket modules: 10.4.1. Perl Saves the Day
Net\:\:Pcap module: 10.4.1. Perl Saves the Day
Net\:\:PcapUtils module: 10.4.1. Perl Saves the Day
Net\:\:Ping module: 10.4.1. Perl Saves the Day
Net\:\:SMTP module: 8.1.3. Speaking to the Mail Protocols Directly
Net\:\:SNMP module: 10.3.1. Using SNMP from Perl
Net\:\:Telnet module: 6.2. Finger: A Simple Directory Service 8.1.3. Speaking to the Mail Protocols Directly
Net\:\:Whois module: 6.3. The WHOIS Directory Service
Network Information Center (NIC): 5.1. Host Files
Network Information Service (see NIS) network operations, tracking
Unix: 4.4.2. Tracking Operations in Unix
Windows NT/2000: 4.4.1. Tracking Operations on Windows NT/2000
network ports, listing open: 4.4.1. Tracking Operations on Windows NT/2000
networks: 4. User Activity
administering with NIS: 5.2. NIS, NIS+, and WINS
changes to, detecting: 10.1.2. Network Service Changes
directory services and: 6.1. What's a Directory?
monitoring
with Perl: 10.4.1. Perl Saves the Day
using SNMP from Perl: 10.3.1. Using SNMP from Perl
suspicious activities: 10.5. Preventing Suspicious Activities
pinging/sniffing from Perl: 10.4.1. Perl Saves the Day
Net\:\:XWhois module: 6.3. The WHOIS Directory Service
NIC (Network Information Center): 5.1. Host Files
NIS+: 5.2.1. NIS+ 5.2.1. NIS+
(see also NIS)
NIS (Network Information Service): 5.2. NIS, NIS+, and WINS
DNS and: 5.3. Domain Name Service (DNS)
querying from Perl: 5.2. NIS, NIS+, and WINS
nslookup program: 5.3.2.1. Using nslookup
ntrights.exe (Windows NT/2000): 3.2.5. NT/2000 User Rights
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
V | W | X | Y | Z
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Index: O
Object Identifier (OID): E. The Twenty-Minute SNMP Tutorial
ODBC Driver Manager: 7.1. Interacting with an SQL Server from Perl
ODBC (Open Database Connectivity): 7.1. Interacting with an SQL Server from Perl
DSN (Data Source Name): 7.3. Using the ODBC Framework
using from Perl: 7.3. Using the ODBC Framework
OID (Object Identifier): E. The Twenty-Minute SNMP Tutorial
Open Database Connectivity (see ODBC)
ORBS (Open Relay Behaviour-Modification System): 8.3.3.2. Checking against Internet-wide blacklists
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
V | W | X | Y | Z
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Index: P
passwd command (Unix): 3.3.2.1. Unix account creation and deletion routines
Passwd\:\:Solaris module: 3.1.4. Shadow Passwords
password field (Unix): 3.1.1. The Classic Unix Password File
password files
BSD 4.4: 3.1.3. Binary Database Format in BSD 4.4
shadow: 3.1.4. Shadow Passwords
Unix: 3.1.1. The Classic Unix Password File
passwords
program for setting/changing: 10.5. Preventing Suspicious Activities
security and: 10.5. Preventing Suspicious Activities
Unix: 3.3.2.1. Unix account creation and deletion routines
Windows NT/2000: 3.2.3. NT/2000 Passwords
PDUs (protocol data units): E. The Twenty-Minute SNMP Tutorial
Perl
advantages/disadvantages of: 1.2. How Perl Can Help
databases
managing logins: 7.5. Database Logins
monitoring from: 7.6. Monitoring Server Health
DBI, using: 7.2. Using the DBI Framework
disk quotas, editing: 2.5.1. Editing Quotas with edquota Trickery
DNS, querying
Net\:\:DNS: 5.3.2.3. Using Net::DNS
nslookup: 5.3.2.1. Using nslookup
raw sockets: 5.3.2.2. Working with raw network sockets
edquota command, calling: 2.5.1. Editing Quotas with edquota Trickery
dissecting mailboxes/messages: 8.3.1. Dissecting a Single Message
sending: 8.1. Sending Mail
filesystems, dealing with differences in: 2.2.5. Dealing with Filesystem Differences from Perl
functions, detecting file changes: 10.1.1. Local Filesystem Changes
host files, reading: 5.1. Host Files
LDAP
programming: 6.4.1. LDAP Programming with Perl
LDIF, reading/writing: 6.4.5. Adding Entries with LDIF
log files
analyzing: 9.5. Log Analysis
rotating: 9.4.1. Log Rotation
scanning: 9.1. Text Logs
using unpack(): 9.2.1. Using unpack( )
modules (see modules)
networks, pinging/sniffing: 10.4.1. Perl Saves the Day
NIS, querying: 5.2. NIS, NIS+, and WINS
ODBC, using: 7.3. Using the ODBC Framework
repositories: 1.5. Locating and Installing Modules
security of: 1.6. It's Not Easy Being Omnipotent
SNMP, using: 10.3.1. Using SNMP from Perl
spam, finding source of: 8.3.3. Tracking Down Spam
SQL commands, sending: 7.3. Using the ODBC Framework
SQL databases, documenting: 7.4. Server Documentation
SQL Server, interacting with: 7.1. Interacting with an SQL Server from Perl
SYN attacks, detecting: 10.4.1. Perl Saves the Day
system administration, as language for: 1.2. How Perl Can Help
using Finger: 6.2. Finger: A Simple Directory Service
using WHOIS: 6.3. The WHOIS Directory Service
using WMI: 4.2.4. Using Window Management Instrumentation (WMI)
Perl Package Manager (see PPM)
placeholders, DBI: 7.2. Using the DBI Framework
Poison Null Byte exploit: 1.6.3. Be Careful When Reading Data
PPM (Perl Package Manager): 1.5. Locating and Installing Modules 1.5.2. Installing Modules on Win32
printers, managing with ADSI: 6.5.11. Working with Print Queues and Print Jobs via ADSI
privileges: 1.6.2. Drop Your Privileges as Soon as Possible 1.6.2. Drop Your Privileges as Soon as Possible
dropping: 1.6.2. Drop Your Privileges as Soon as Possible
/proc filesystem: 4.3.3. Using the /proc Filesystem
process control
Mac OS: 4.1. MacOS Process Control
Unix: 4.3. Unix Process Control
Windows NT/2000: 4.2. NT/2000 Process Control
processes: 4. User Activity
DLLs used by: 4.2.2. Using the Win32::IProc Module
executables used by: 4.2.2. Using the Win32::IProc Module
killing
Unix: 4.3.4. Using the Proc::ProcessTable Module
Windows NT/2000: 4.2.1. Using the Microsoft Resource Kit Binaries 4.2.3. Using the Win32::Setupsup Module
listing
Mac: 4.1. MacOS Process Control
Unix: 4.3. Unix Process Control
Windows NT/2000: 4.2.1. Using the Microsoft Resource Kit Binaries 4.2.3. Using the Win32::Setupsup Module
windows open, interacting with: 4.2.3. Using the Win32::Setupsup Module
procmail program: 3.3.4. Account System Wrap-Up
Proc\:\:ProcessTable module: 4.3.4. Using the Proc::ProcessTable Module
programming, secure: 1.6. It's Not Easy Being Omnipotent
programs
for setting/changing passwords: 10.5. Preventing Suspicious Activities
password-cracking: 10.5. Preventing Suspicious Activities
properties, interface-/schema-defined: 6.5.1. ADSI Basics
protocol data units (PDUs): E. The Twenty-Minute SNMP Tutorial
providers (ADSI): 6.5.1. ADSI Basics
ps program (Unix): 4.3.1. Calling an External Program
pulist.exe (Windows NT/2000): 4.2.1. Using the Microsoft Resource Kit Binaries
pwd_mkdb command (BSD 4.4): 3.1.3. Binary Database Format in BSD 4.4
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
V | W | X | Y | Z
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Index: Q
qmail program: 8.3.2. Dissecting a Whole Mailbox
QuitApps function (Mac OS): 4.1. MacOS Process Control
quota command: 2.5. Manipulating Disk Quotas
Quota module: 2.5.2. Editing Quotas Using the Quota Module
quotas, disk (see disks, full)
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
V | W | X | Y | Z
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Index: R
race conditions, avoiding: 1.6.5. Avoid Race Conditions
RBL (Mail Abuse Prevention System Realtime Blackhole List): 8.3.3.2. Checking against Internet-wide blacklists
Rcs module: 5.1.4. Incorporating a Source Code Control System
RCS (Revision Control System): 5.1.4. Incorporating a Source Code Control System
commands: A. The Five-Minute RCS Tutorial
GNU RCS 5.7: 5.1.4. Incorporating a Source Code Control System
keywords: 5.1.4. Incorporating a Source Code Control System
tutorial: A. The Five-Minute RCS Tutorial
rcsdiff command (Unix): 5.1.4. Incorporating a Source Code Control System A. The Five-Minute RCS Tutorial
RDN (Relative Distinguished Name): B.1. LDAP Data Organization
recursion, using: 2.3. Walking or Traversing the Filesystem
regular expressions: 9.5.2. Read-Remember-Process
security and: 10.2.1. Local Signs of Peril
Relative Distinguished Name (RDN): B.1. LDAP Data Organization
relative identifier (RID): 3.2.2. NT/2000 User ID Numbers 3.2.2. NT/2000 User ID Numbers
(see also users, identity of, Windows NT/2000) relaying email: 8.3.3. Tracking Down Spam
repositories for prebuilt packages: 1.5. Locating and Installing Modules
Revision Control System (see RCS)
RID (relative identifier): 3.2.2. NT/2000 User ID Numbers 3.2.2. NT/2000 User ID Numbers
(see also users, identity of, Windows NT/2000)
root directories on FAT filesystems: 2.2.2. Microsoft Windows NT/2000
RunAs feature (Windows 2000): 1.6.2. Drop Your Privileges as Soon as Possible
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
V | W | X | Y | Z
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Index: S
SAM (Security Accounts Manager): 3.2.1. NT/2000 User Identity Storage and Access
SASL (Simple Authentication and Security Layer): 6.4.2. The Initial LDAP Connection
schema-defined properties: 6.5.1. ADSI Basics
6.5.5. So How Do You Know Anything About an Object? 6.5.5. So How Do You Know Anything About an Object?
scopes of searches: 6.4.3. Performing LDAP Searches
scripts: 7.8.1. SQL
(see also Perl)
for sending email: 8.2.1. Overzealous Message Sending
message body of: 8.2.3. Insufficient Information in the Message Body
for user administration processes: 3.3.3. The Process Scripts
search base: 6.4.3. Performing LDAP Searches
search filters: 6.4.3. Performing LDAP Searches
secondary servers: 5.3. Domain Name Service (DNS)
DNS: 5.3.1.1. Creating the administrative header
Secure Socket Layer (SSL): 6.4.2. The Initial LDAP Connection
security
of bots: 4.3.4. Using the Proc::ProcessTable Module
of SNMP: E. The Twenty-Minute SNMP Tutorial
breaches in, documenting: 10.2.1. Local Signs of Peril
denial-of-service attacks: 10.4.1. Perl Saves the Day
detecting changes
to files: 10.1.1. Local Filesystem Changes
to networks: 10.1.2. Network Service Changes
of Perl: 1.6. It's Not Easy Being Omnipotent
suspicious activities, noticing: 10.2.1. Local Signs of Peril
SYN attacks, detecting from Perl: 10.4.1. Perl Saves the Day
Security Accounts Manager (SAM): 3.2.1. NT/2000 User Identity Storage and Access
security identifier (SID): 3.2.2. NT/2000 User ID Numbers 3.2.2. NT/2000 User ID Numbers
SELECT command (SQL): D.3. Querying Information
D.3.3. Simple Manipulation of Data Returned by Queries
Sendmail for NT program: 8.1.1. Getting sendmail (or Similar Mail Transport Agent)
sendmail program: 8.1. Sending Mail
8.1.3. Speaking to the Mail Protocols Directly
blacklists, local: 8.3.3.1. Checking against a local blacklist
services
directory (see directory services) TCP/IP (see TCP/IP, name services)
shadow password files (Unix): 3.1.4. Shadow Passwords
shell field (Unix): 3.1.1. The Classic Unix Password File
SID (security identifier): 3.2.2. NT/2000 User ID Numbers 3.2.2. NT/2000 User ID Numbers
(see also users, identity of, Windows NT/2000)
Simple Authentication and Security Layer (SASL): 6.4.2. The Initial LDAP Connection
Simple Mail Transport Protocol (see SMTP)
Simple Network Management Protocol (see SNMP) slave servers: 5.2. NIS, NIS+, and WINS
5.3. Domain Name Service (DNS)
DNS: 5.3.1.1. Creating the administrative header
SMI RFCs: E.1. SNMP in Practice
SMTP (Simple Mail Transport Protocol): 8.1.3. Speaking to the Mail Protocols Directly
SNMP Extension Module for the UCD SNMPv3 Library: 10.3.1. Using SNMP from Perl
SNMP (Simple Network Management Protocol): E. The Twenty-Minute SNMP Tutorial
access policy: E. The Twenty-Minute SNMP Tutorial
communities: E. The Twenty-Minute SNMP Tutorial
modules, comparing: 10.3.1. Using SNMP from Perl
monitoring networks with: 10.3.1. Using SNMP from Perl
security of: E. The Twenty-Minute SNMP Tutorial
theory: E. The Twenty-Minute SNMP Tutorial
tutorial: E.1. SNMP in Practice
using from Perl: 10.3.1. Using SNMP from Perl
variables: E. The Twenty-Minute SNMP Tutorial
SNMP_Session module: 10.3.1. Using SNMP from Perl
SNMP_utility module: 10.3.1. Using SNMP from Perl
SOA (Start of Authority): 5.3.1.1. Creating the administrative header
software metering: 4.3.4. Using the Proc::ProcessTable Module
source control systems: 5.1.4. Incorporating a Source Code Control System
RCS (see RCS)
spam, finding source of: 8.3.3. Tracking Down Spam
blacklists, checking against
Internet-wide: 8.3.3.2. Checking against Internet-wide blacklists
local: 8.3.3.1. Checking against a local blacklist
split() function (Unix): 5.1.1. Generating Host Files
SQL databases
creating/deleting: D.1. Creating /Deleting Databases and Tables
data in, manipulating: D.3.3. Simple Manipulation of Data Returned by Queries
Perl-cliented: 9.5.4.2. Using Perl-cliented SQL databases
querying information: D.3. Querying Information
stored procedures: D.6.3. Stored Procedures
SQL (Structured Query Language): 7. SQL Database Administration
commands, sending from Perl: 7.3. Using the ODBC Framework
databases
documenting from Perl: 7.4. Server Documentation
interacting with from Perl: 7.1. Interacting with an SQL Server from Perl
managing logins from Perl: 7.5. Database Logins
monitoring from Perl: 7.6. Monitoring Server Health
using DBI: 7.2. Using the DBI Framework
using ODBC: 7.3. Using the ODBC Framework
tutorial: D. The Fifteen-Minute SQL Tutorial
SQL tables
changing: D.4. Changing Table Information
creating/deleting: D.1. Creating /Deleting Databases and Tables
inserting data into: D.2. Inserting Data into a Table
query results, adding: D.3.4. Adding the Query Results to Another Table
relating: D.5. Relating Tables to Each Other
rows in, retrieving: D.3.1. Retrieving All of the Rows in a Table D.3.2. Retrieving a Subset of the Rows in a Table
views of: D.6.1. Views
Start of Authority (SOA): 5.3.1.1. Creating the administrative header
stat() function (Perl): 10.1.1. Local Filesystem Changes
statement handle, DBI: 7.2. Using the DBI Framework
Structure for Management Information (SMI): E.1. SNMP in Practice
Structured Query Language (see SQL) SunOS
host files: 5.1. Host Files
wtmp file: 9.2.1. Using unpack( )
suss program: 8.3.4. Support Mail Augmentation
Sybase OpenClient libraries: 7.1. Interacting with an SQL Server from Perl
Sybase server, documenting via DBI module: 7.4.2. Sybase Server via DBI
SYN-ACK attack: 10.4.1. Perl Saves the Day
SYN Flood: 10.4.1. Perl Saves the Day
Sys\:\:Hostname module: 9.5.4.1. Using Perl-only databases
SyslogScan package: 9.5.3. Black Boxes
system administration
with ADSI: 6.5.8. Working with Users via ADSI
email for: 8. Electronic Mail
as support medium: 8.3.4. Support Mail Augmentation
limiting message sending: 8.2.1.1. Controlling the frequency of mail
sending: 8.1. Sending Mail
log files: 9. Log Files
monitoring
networks: 10.3.1. Using SNMP from Perl
security: 10. Security and Network Monitoring
Perl as language for: 1.2. How Perl Can Help
SQL databases and: 7. SQL Database Administration
system administrators
contacting: 6.3. The WHOIS Directory Service
mechanics vs. architects: 3.3.1. The Backend Database
\\\\$systemroot$\\\\system32\\\\drivers\\\\etc\\\\hosts file: 5.1. Host Files
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
V | W | X | Y | Z
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Index: T
TCP/IP (Transmission Control Protocol/Internet Protocol): 5. TCP/IP Name Services
host files, generating: 5.1.1. Generating Host Files
name services: 5.2. NIS, NIS+, and WINS
TCPVstat program: 4.4.1. Tracking Operations on Windows NT/2000
tcpwrappers program: 9.5.2. Read-Remember-Process
Term\:\:ReadKey module: 10.5. Preventing Suspicious Activities
top program: 4.3.2. Examining the Kernel Process Structures
tracking
file operations on Unix: 4.4.2. Tracking Operations in Unix
network host data, databases for: 5.1.1. Generating Host Files
network operations
Unix: 4.4.2. Tracking Operations in Unix
Windows NT/2000: 4.4.1. Tracking Operations on Windows NT/2000
open files: 4.4.1. Tracking Operations on Windows NT/2000
operations
on Unix: 4.4.2. Tracking Operations in Unix
on Windows NT/2000: 4.4.1. Tracking Operations on Windows NT/2000
Windows NT/2000: 4.4.1. Tracking Operations on Windows NT/2000
Transmission Control Protocol (see TCP/IP)
Transmission Control Protocol/Internet Protocol (see TCP/IP)
TurboPerl program: 4.2.4. Using Window Management Instrumentation (WMI)
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
V | W | X | Y | Z
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Index: U
UCD-SNMP library: 10.3.1. Using SNMP from Perl
UID (see user ID)
Universal Naming Convention (UNC): 2.2.2. Microsoft Windows NT/2000
Unix
account creation/deletion, programs for: 3.3.2.1. Unix account creation and deletion routines
communicating with Microsoft SQL Server: 7.1. Interacting with an SQL Server from Perl
directories, hidden: 10.2.1. Local Signs of Peril
disk quotas on: 2.5. Manipulating Disk Quotas
file operations on, tracking: 4.4.2. Tracking Operations in Unix
filesystems: 2.2.1. Unix
/proc: 4.3.3. Using the /proc Filesystem
querying usage on: 2.6. Querying Filesystem Usage
traversing/walking: 2.3. Walking or Traversing the Filesystem
group ID (GID): 3.1.1. The Classic Unix Password File
host files: 5.1. Host Files
generating: 5.1.1. Generating Host Files
parsing: 5.1. Host Files
source control systems: 5.1.4. Incorporating a Source Code Control System
installing modules on: 1.5.1. Installing Modules on Unix 1.5.1. Installing Modules on Unix
log files
analyzing: 9.5. Log Analysis
wtmp: 9.2. Binary Log Files
network operations on, tracking: 4.4.2. Tracking Operations in Unix
password file: 3.1.1. The Classic Unix Password File
passwords: 3.3.2.1. Unix account creation and deletion routines
privileges on, dropping: 1.6.2. Drop Your Privileges as Soon as Possible
process control: 4.3. Unix Process Control
process table, module for interface to: 4.3.4. Using the Proc::ProcessTable Module
shells: 3.1.1. The Classic Unix Password File
user identity: 3.1. Unix User Identity
unpack() function (Perl): 9.2.1. Using unpack( )
Unsolicited Commercial Email (UCE) (see spam)
UPDATE command (SQL): D.4. Changing Table Information
USE statement (SQL): D.1. Creating /Deleting Databases and Tables
user accounts
adding/removing: 3.3. Building an Account System to Manage Users
API calls for: 3.3.2.2. Windows NT/2000 account creation and deletion routines
modules for: 3.3.2.2. Windows NT/2000 account creation and deletion routines
logins, security and: 10.2.2. Finding Problematic Patterns
managing
with ADSI: 6.5.8. Working with Users via ADSI
process scripts for: 3.3.3. The Process Scripts
user ID (UID)
Unix: 3.1.1. The Classic Unix Password File
Windows NT/2000: 3.2.2. NT/2000 User ID Numbers
user input, security of: 1.6.3. Be Careful When Reading Data
User Security Model (USM): E. The Twenty-Minute SNMP Tutorial
users
identity of: 3. User Accounts
Unix: 3.1. Unix User Identity
Windows NT/2000: 3.2.1. NT/2000 User Identity Storage and Access
rights of, Windows NT/2000: 3.2.5. NT/2000 User Rights
USM (User Security Model): E. The Twenty-Minute SNMP Tutorial
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
V | W | X | Y | Z
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Index: V
Varbind object: 10.3.1. Using SNMP from Perl
VFAT filesystem: 2.2.2. Microsoft Windows NT/2000
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
V | W | X | Y | Z
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Index: W
WBEM (Web-Based Enterprise Management): 4.2.4. Using Window Management Instrumentation (WMI)
WHERE clause (SQL): D.3.2. Retrieving a Subset of the Rows in a Table
WHOIS: 6.3. The WHOIS Directory Service
querying the right server: 8.3.3.2. Checking against Internet-wide blacklists
Win32 Schema: 4.2.4. Using Window Management Instrumentation (WMI)
Win32\:\:AdminMisc module: 3.2.1. NT/2000 User Identity Storage and Access
Win32\:\:AdvNotify module: 4.4.1. Tracking Operations on Windows NT/2000
Win32API\:\:Net module: 3.3.2.2. Windows NT/2000 account creation and deletion routines
Window Management Instrumentation (see WMI) windows
changing titles of: 4.2.3. Using the Win32::Setupsup Module
of processes
properties of: 4.2.3. Using the Win32::Setupsup Module
interacting with: 4.2.3. Using the Win32::Setupsup Module
sending keystrokes to: 4.2.3. Using the Win32::Setupsup Module
Windows 2000: 3.2.5. NT/2000 User Rights
(see also Windows NT/2000) groups: 3.2.4. NT Groups
3.2.4. NT Groups
(see also Windows NT, groups)
process control using WMI: 4.2.4. Using Window Management Instrumentation (WMI)
Windows 2000 Resource Kit: 3.2.5. NT/2000 User Rights
Windows Internet Name Server (see WINS) Windows NT: 3.2.5. NT/2000 User Rights
(see also Windows NT/2000) groups: 3.2.4. NT Groups
log files, analyzing: 9.5.1. Stream Read-Count
mapping hostnames to IP addresses: 5.2.2. Windows Internet Name Server ( WINS)
Windows NT Resource Kit: 3.2.5. NT/2000 User Rights
process control binaries: 4.2.1. Using the Microsoft Resource Kit Binaries
Windows NT Server Resource Kit, utilities for WINS: 5.2.2. Windows Internet Name Server ( WINS)
windowse utility: 4.2.3. Using the Win32::Setupsup Module
Win32\:\:EventLog module: 9.2.3. Using the OS's Logging API
analyzing log files with: 9.5.1. Stream Read-Count
Win32\:\:IpHelp module: 4.4.1. Tracking Operations on Windows NT/2000
Win32\:\:IProc module: 4.2.2. Using the Win32::IProc Module
installing: 4.5.1. Installing Win32::IProc
Win32\:\:Lanman module: 3.3.2.2. Windows NT/2000 account creation and deletion routines
Win32\:\:MAPI module: 8.1.2. Using the OS-Specific IPC Framework.
Win32\:\:NetAdmin module: 3.2.1. NT/2000 User Identity Storage and Access 3.2.4. NT Groups
3.3.2.2. Windows NT/2000 account creation and deletion routines
Win32\:\:ODBC module: 7.3. Using the ODBC Framework 7.4.3. MS-SQL Server via ODBC
Win32\:\:OLE module: 3.2.1. NT/2000 User Identity Storage and Access 4.2.4. Using Window Management Instrumentation (WMI)
6.5.2. Using ADSI from Perl
8.1.2. Using the OS-Specific IPC Framework.
Win32\:\:Process module: 4.2.2. Using the Win32::IProc Module
WINS (Windows Internet Name Server): 5.2.2. Windows Internet Name Server ( WINS)
DNS and: 5.3. Domain Name Service (DNS)
Win32\:\:Setupsup module: 4.2.3. Using the Win32::Setupsup Module
installing: 4.5.2. Installing Win32::Setupsup
Win32\:\:UserAdmin module: 3.2.1. NT/2000 User Identity Storage and Access 3.3.2.2. Windows NT/2000 account creation and deletion routines
wmailto program: 8.1.1. Getting sendmail (or Similar Mail Transport Agent)
WMI (Window Management Instrumentation): 4.2.4. Using Window Management Instrumentation (WMI)
4.2.4. Using Window Management Instrumentation (WMI)
retrieving log information with: 9.2.3. Using the OS's Logging API
writing to files, security of: 1.6.4. Be Careful When Writing Data
wtmp file: 9.2.1. Using unpack( )
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
V | W | X | Y | Z
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Index: X
X.500 Directory Service: 6.4. LDAP: A Sophisticated Directory Service
XML (Extensible Markup Language)
reading from Perl: 3.3.1.2. Reading XML using XML::Parser
tutorial: C.1. XML Is a Markup Language
user account database, creating: 3.3.1. The Backend Database
writing from Perl: 3.3.1.1. Writing XML from Perl 3.3.1.4. Writing XML using XML::Simple
XML\:\:Generator module: 3.3.1.1. Writing XML from Perl
XML\:\:Parser module: 3.3.1.2. Reading XML using XML::Parser
XML\:\:Simple module: 3.3.1.3. Reading XML using XML::Simple
XML\:\:Writer module: 3.3.1.1. Writing XML from Perl
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
V | W | X | Y | Z
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Index: Y
Yellow Pages (see NIS)yppoll program: 5.2. NIS, NIS+, and WINS
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
V | W | X | Y | Z
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
Index: Z
There are no index entries for this letter.
Symbols | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U |
V | W | X | Y | Z
by David N. Blank-Edelman ISBN 1-56592-609-9
First edition, published July 2000. (See the catalog page for this book.)
Table of Contents
Copyright Page Preface
Chapter 1: Introduction Chapter 2: Filesystems Chapter 3: User Accounts Chapter 4: User Activity
Chapter 5: TCP/IP Name Services Chapter 6: Directory Services
Chapter 7: SQL Database Administration Chapter 8: Electronic Mail
Chapter 9: Log Files
Chapter 10: Security and Network Monitoring Appendix A: The Five-Minute RCS Tutorial Appendix B: The Ten-Minute LDAP Tutorial Appendix C: The Eight-Minute XML Tutorial Appendix D: The Fifteen-Minute SQL Tutorial Appendix E: The Twenty-Minute SNMP Tutorial Index
Colophon
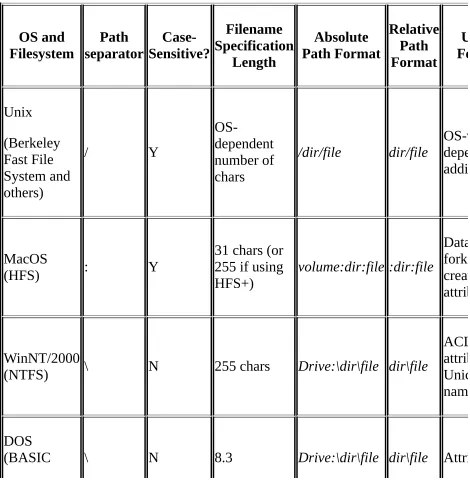
2.2. Filesystem Differences
We'll start with a quick review of the native filesystems for each of our target operating systems. Some of this may be old news to you, especially if you have significant experience with a particular operating system. Still, it is worth your while to pay careful attention to the differences between the filesystems
(especially the ones you don't know) if you intend to write Perl code that works on multiple platforms.
2.2.1. Unix
All modern Unix variants ship with a native filesystem with semantics that resemble those of their common ancestor, the Berkeley Fast File System. Different vendors have extended their filesystem implementations in different ways (e.g., Solaris adds Access Control Lists for better security, Digital Unix ships a spiffy transaction-based filesystem called advfs, etc.). We'll be writing code aimed at the lowest common denominator to allow it to work across different Unix platforms.
The top, or root, of a Unix filesystem is indicated by a forward slash (/). To
uniquely identify a file or directory in a Unix filesystem, we construct a path starting with a slash and then add directories, separating them with forward slashes, as we descend deeper into the filesystem. The final component of this path is the desired directory or filename. Directory and filenames in modern Unix variants are case sensitive. Almost all ASCII characters can be used in these names if you are crafty enough, but sticking to alphanumeric characters and some limited punctuation will save you hassle later.
2.2.2. Microsoft Windows NT/2000
Windows NT (Version 4.0 as of this writing) ships with two supported
filesystems: File Allocation Table (FAT) and NT FileSystem (NTFS). Windows 2000 adds FAT32, an improved version of FAT that allows for larger partitions and smaller cluster sizes to the NT family.
foibles of the basic FAT filesystem. In basic or real-mode FAT filesystems, filenames conform to the 8.3 specification. This means that file and directory names can start with no more than eight characters, must have a period (or dot as it is spoken), and are followed by a suffix of up to three characters in length. Unlike Unix, where a period in a filename has no special meaning, basic FAT filesystems can only use a single period as an enforced separator between the filename and its extension or suffix.
Real-mode FAT was later enhanced in a version called VFAT or protected-mode FAT. This is roughly the version that Windows NT and Windows 2000 support. VFAT hides all of the name restrictions from the user. Longer filenames without separators are provided by a very creative hack. VFAT uses a chain of standard file/directory name slots to transparently shoehorn extended filename support into the basic FAT filesystem structure. For compatibility, every file and
directory name can still be accessed using a special 8.3-conforming DOS alias. For instance, the directory called Downloaded Program Files is also available as
DOWNLO~1.
There are four key differences between a VFAT and a Unix filesystem: 1. FAT filesystems are case-insensitive. In Unix, an attempt to open a file
using the wrong case (i.e., MYFAVORITEFILE versus myfavoritefile) will fail. With FAT or VFAT, this will succeed with no problem.
2. The second difference is the choice of characters used to separate path components and root designations. Instead of forward slash, FAT uses the backward slash (\) as its path separator. This has a direct ramification for
the Perl programmer. The backslash is a quoting character in Perl. Paths written in single quotes with only single separators (i.e.,
$path='\dir\dir\filename') are just fine. However, situations in which
you need to place multiple backslashes next to each other (i.e.,
\\server\dir\file) are potential trouble. In those cases, you have to be vigilant in doubling any multiple backslashes. Some Perl functions and some Perl modules will accept paths with forward slashes, but this convention should not be counted upon when programming. It is better to bite the bullet and write \\\\winnt\\temp\ than to learn that your code breaks because the
conversion hasn't been done for you.