Free ebooks ==> www.Ebook777.com
Encyclopedia of
Information Ethics
and Security
Marian Quigley
Monash University, Australia
Hershey • New York
I N FORM AT I ON SCI EN CE REFEREN CE
Acquisitions Editor: Kristin Klinger Development Editor: Kristin Roth Senior Managing Editor: Jennifer Neidig Managing Editor: Sara Reed Assistant Managing Editor: Diane Huskinson Copy Editor: Maria Boyer Typesetter: Sara Reed Cover Design: Lisa Tosheff Printed at: Yurchak Printing Inc.
Published in the United States of America by
Information Science Reference (an imprint of IGI Global) 701 E. Chocolate Avenue, Suite 200
Hershey PA 17033 Tel: 717-533-8845 Fax: 717-533-8661 E-mail: cust@igi-pub.com
Web site: http://www.igi-pub.com/reference
and in the United Kingdom by
Information Science Reference (an imprint of IGI Global) 3 Henrietta Street
Covent Garden London WC2E 8LU Tel: 44 20 7240 0856 Fax: 44 20 7379 0609
Web site: http://www.eurospanonline.com
Copyright © 2008 by IGI Global. All rights reserved. No part of this publication may be reproduced, stored or distributed in any form or by any means, electronic or mechanical, including photocopying, without written permission from the publisher.
Product or company names used in this set are for identification purposes only. Inclusion of the names of the products or companies does not indicate a claim of ownership by IGI Global of the trademark or registered trademark.
Library of Congress Cataloging-in-Publication Data
Encyclopedia of information ethics and security / Marian Quigley, Editor. p. cm.
Topics address a wide range of life areas affected by computer technology, including: education, the workplace, health, privacy, intellectual property, identity, computer crime, cyber terrorism, equity and access, banking, shopping, publishing, legal and political issues, censorship, artificial intelligence, the environment, communication.
Summary: “This book is an original, comprehensive reference source on ethical and security issues relating to the latest technologies. It covers a wide range of themes, including topics such as computer crime, information warfare, privacy, surveillance, intellectual property and education. It is a useful tool for students, academics, and professionals”--Provided by publisher.
Includes bibliographical references and index.
ISBN 978-1-59140-987-8 (hardcover) -- ISBN 978-1-59140-988-5 (ebook)
1. Information technology--Social aspects--Encyclopedias. 2. Information technology--Moral and ethical aspects--Encyclopedias. 3. Computer crimes--Encyclopedias. 4. Computer security-crimes--Encyclopedias. 5. Information networks--Security measures-crimes--Encyclopedias. I. Quigley, Marian.
HM851.E555 2007 174’.900403--dc22
2007007277
British Cataloguing in Publication Data
A Cataloguing in Publication record for this book is available from the British Library.
Editorial Advisory Board
Kathy Blashki
Deakin University, Australia
Matthew Butler
Monash University, Australia
Heather Fulford
The Robert Gordon University, UK James E. Goldman
Purdue University, USA
Katina Michael
University of Wollongong, Australia
Bernd Carsten Stahl
Free ebooks ==> www.Ebook777.com
List of Contributors
Abdallah, Salam / Amman Arab University for Graduate Studies, Jordan ...355
Abdolmohammadi, Mohammad / Bentley College, USA ...440
Al-Fedaghi, Sabah S. / Kuwait University, Kuwait ...513, 631 Ali, Muhammed / Tuskegee University, USA ...507
Arbore, Alessandro / Bocconi University, Italy ...655
Averweg, Udo Richard / eThekwini Municipality andUniversity of KwaZulu-Natal, South Africa ...297
Barger, Robert N. / University of Notre Dame, USA ...445
Becker, Reggie / Emerson Electric, USA ...451
Beggs, Christopher / Monash University, Australia ...108
Blashki, Kathy / Deakin University, Australia ...194
Bourlakis, Michael / Brunel University, UK ...15
Boyle, Roger / University of Leeds, UK ...208
Buchanan, Elizabeth / University of Wisconsin – Milwaukee, USA ...397
Busuttil, T. B. / Deakin University, Australia ...609
Butler, Matthew / Monash University, Australia ...96
Cazier, Joseph A. / Appalachian State University, USA ...221
Chapple, Michael J. / University of Notre Dame, USA ...291
Chatterjee, Sutirtha / Washington State University, USA ...201
Chen, Irene / University of Houston – Downtown, USA ...130
Chen, Jengchung V. / National Cheng Kung University, Taiwan ...102
Chhanabhai, Prajesh / University of Otago, New Zealand ...170
Chin, Amita Goyal / Virginia Commonwealth University, USA ...273
Chu, Chao-Hsien / The Pennsylvania State University, USA ...89
Cole, Robert J. / Pennsylvania State University, USA ...89
Cote, Jo Anne / Reginald J. P. Dawson Library, QC, Canada ...136
Countermine, Terry / East Tennessee State University, USA ...507
Crowell, Charles R. / University of Notre Dame, USA ...291, 445 Currier, Dianne / Columbia University, USA ...384
Dark, Melissa / Purdue University, USA ...507
Doherty, Neil / Loughborough University, UK ...377
Douma, Michael / Institute for Dynamic Educational Advancement, USA ...362
Drake, John R. / Auburn University, USA ...486
Du, Jianxia / Mississippi State University, USA ...49
Dunkels, Elza / Umeå University, Sweden ...403
Dyson, Laurel Evelyn / University of Technology Sydney, Australia ...433
Ellis, Kirsten / Monash University, Australia ...235
Enochsson, AnnBritt / Karlstad University, Sweden ...403
Epstein, Richard / West Chester University, USA ...507
Etter, Stephanie / Mount Aloysius College, USA ...214
Fedorowicz, Jane / Bentley College, USA ...440
Fulford, Heather / The Robert Gordon University, UK ...377
Gamito, Eduard J. / University of Colorado Health Sciences Center, USA ...362
Gasmelseid, Tagelsir Mohamed / King Faisal University, Kingdom of Saudi Arabia ...187
Gray, Kathleen / University of Melbourne, Australia ...164
Grillo, Antonio / Università di Roma, Italy ...55
Guan, Sheng-Uei / Brunel University, UK ...556,571 Gupta, Manish / State University of New York at Buffalo, USA ...520
Gupta, Phalguni / Indian Institute of Technology Kanpur, India ...478
Gurău, Călin / GSCM – Montpellier Business School, France ...542
Halpert, Benjamin J. / Nova Southeastern University, USA ...492
Handy, Jocelyn / Massey University, New Zealand ...534
Harter, Nathan / Purdue University, USA ...507
Hiltbrand, Robert K. / University of Houston, USA ...411
Hirsch, Corey / Henley Management College, UK ...370
Hocking, Lynley / Department of Education, Tasmania, Australia ...470
Holt, Alec / University of Otago, New Zealand ...170
Huang, ShaoYu F. / National Cheng Kung University, Taiwan ...102
Hunter, Inga / Massey University, New Zealand ...534
Im, Seunghyun / University of Pittsburgh at Johnstown, USA ...114
Irons, Alistair / Northumbria University, UK ...208
Isenmann, Ralf / University of Bremen, Germany ...622
Jasola, Sanjay / Indira Gandhi National Open University, New Delhi ...594
Johnston, Allen C. / University of Louisiana Monroe, USA ...451
Jourdan, Zack / Auburn University, USA ...68
Kamthan, Pankaj / Concordia University, Canada ...266
Kao, Kai-Ti / Monash University, Australia ...326
Kats, Yefim / Southwestern Oklahoma State University, USA ...83
Kawash, Jalal / American University of Sharjah, UAE ...527
Kiau, Bong Wee / Universiti Utara Malaysia, Malaysia ...157
Kidd, Terry T. / University of Texas Health Science Center, USA ...130,411 Korb, Kevin B. / Monash University, Australia ...279
Kotlarsky, Julia / University of Warwick, UK ...370
LaBrie, Ryan C. / Seattle Pacific University, USA ...221
Lawler, James / Pace University, USA ...549
Lazarus, Belinda Davis / University of Michigan – Dearborn, USA ...241
LeDonne, Keith / Robert Morris University, USA ...214
Lee, Zu-Hsu / Montclair State University, USA ...229
Lentini, Alessandro / Università di Roma, Italy ...55
Leonard, Lori N. K. / University of Tulsa, USA ...260
Li, Koon-Ying Raymond / e-Promote Pty. Ltd., Australia ...1
Loke, Seng / La Trobe University, Australia ...463,563 Mahmood, Omer / Charles Darwin University, Australia ...143
Manly, Tracy S. / University of Tulsa, USA ...260
Marshall, Thomas E. / Auburn University, USA ...68
Me, Gianluigi / Università di Roma, “Tor Vergata,” Italy ...55, 418
Mehrotra, Hunny / Indian Institute of Technology Kanpur, India ...478
Michael, Katina / University of Wollongong, Australia ...312
Michael, M. G. / University of Wollongong, Australia ...312
Mishra, Sushma / Virginia Commonwealth University, USA ...273
Molinero, Ashli M. / Robert Morris University, USA ...214
Molluzzo, John C. / Pace University, USA ...549
Morales, Linda / Texas A&M Commerce, USA ...507
Nestor, Susan J. / Robert Morris University, USA ...214
Ngo, Leanne / Deakin University, Australia ...319
Nichol, Sophie / Deakin University, Australia ...196
Nissan, Ephraim / Goldsmiths College, University of London, UK ...30, 36, 42, 638 Oshri, Ilan / Rotterdam School of Management Erasmus, The Netherlands ...370
Palaniappan, Ramaswamy / University of Essex, UK ...335
Papagiannidis, Savvas / University of Newcastle upon Tyne, UK ...15
Paperin, Gregory / Monash University, Australia ...602
Park, Eun G. / McGill University, Canada ...136
Pate, George H. / Mississippi State University, USA ...49
Patnaik, Lalit M. / Indian Institute of Science, India ...335
Peterson, Richard / Montclair State University, USA ...229
Phillips, Patricia G. / Duquesne University, USA ...214
Popova-Gosart, Ulia / Lauravetlan Information and Education Network of Indigenous Peoples of Russian Federation (LIENIP) and University of California in Los Angeles, USA ...645
Power, Mark / Monash University, Australia ...1
Quigley, Marian / Monash University, Australia ...235
Rainer Jr., R. Kelly / Auburn University, USA ...68
Ramim, Michelle M. / Nova Southeastern University, USA ...246
Ras, Zbigniew W. / University of North Carolina at Charlotte, USA ...114
Rattani, Ajita / Indian Institute of Technology Kanpur, India ...478
Rose, Matt / Purdue University, USA ...507
Roy, Jeffrey / Dalhousie University, Canada ...585
Ruvinsky, Alicia I. / University of South Carolina, USA ...76
Schmidt, Mark B. / St. Cloud State University, USA ...451, 579 Sharma, Ramesh C. / Indira Gandhi National Open University, New Delhi ...594
Sharman, Raj / State University of New York at Buffalo, USA ...520
Shen, Yifeng / Monash University, Australia ...7
Sherrod, Deneen / Mississippi State University, USA ...49
Shetty, Pravin / Monash University, Australia ...463, 563 Shiratuddin, Norshuhada / Universiti Utara Malaysia, Malaysia ...157
Sixsmith, Alan / University of Technology Sydney, Australia ...426
Skalicky Hanson, Jan / St. Cloud State University, USA ...579
Sofra, James / Monash University, Australia ...1
Srivastava, A. / Monash University, Australia ...179
Stafford, Thomas F. / University of Memphis, USA ...616
Stahl, Bernd Carsten / De Montfort University, UK ...348
Sugden, Paul / Monash University, Australia ...391
Third, Amanda / Monash University, Australia ...326
Thomson, S. B. / Monash University, Australia ...179
Tribunella, Thomas J. / Rochester Institute of Technology, USA ...254
Tyrväskylä, Pasi / University of Jyväskylä, Finland ...285
Walker, Christopher H. / The Pennsylvania State University, USA ...150
Wang, John / Montclair State University, USA ...229
Warren, M. J. / Deakin University, Australia ...304,609 Whiddett, Dick / Massey University, New Zealand ...534
Wickramasinghe, Nilmini / Illinois Institute of Technology, USA ...498
Xiang, Yang / Central Queensland University, Australia ...121
Xue, Fei / Monash University, Australia ...457
Yao, James / Montclair State University, USA ...229
Yu, Wei-Chieh / Mississippi State University, USA ...49
Yuan, Qing / East Tennessee State University, USA ...507
Contents
3D Avatars and Collaborative Virtual Environments / Koon-Ying Raymond Li, James Sofra,
and Mark Power ...1
Access Control for Healthcare / Yifeng Shen ...7
Advertising in the Networked Environment / Savvas Papagiannidis and Michael Bourlakis ...15
Anonymous Peer-to-Peer Systems / Wenbing Zhao ...23
Argumentation and Computing / Ephraim Nissan ...30
Argumentation with Wigmore Charts and Computing / Ephraim Nissan ...36
Artificial Intelligence Tools for Handling Legal Evidence / Ephraim Nissan ...42
Barriers Facing African American Women in Technology / Jianxia Du, George H. Pate, Deneen Sherrod, and Wei-Chieh Yu ...49
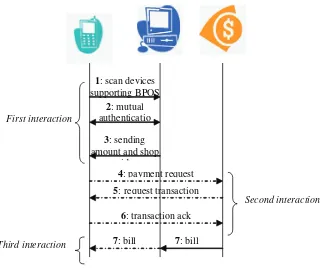
B-POS Secure Mobile Payment System / Antonio Grillo, Alessandro Lentini, and Gianluigi Me ...55
Building Secure and Dependable Information Systems / Wenbing Zhao ...62
Classifying Articles in Information Ethics and Security / Zack Jourdan, R. Kelly Rainer Jr., and Thomas E. Marshall ...68
Computational Ethics / Alicia I. Ruvinsky ...76
Computer Ethics and Intelligent Technologies / Yefim Kats ...83
Computer Worms, Detection, and Defense / Robert J. Cole and Chao-Hsien Chu ...89
Conflicting Value of Digital Music Piracy / Matthew Butler ...96
Content Filtering Methods for Internet Pornography / Jengchung V. Chen and ShaoYu F. Huang ...102
Free ebooks ==> www.Ebook777.com
Data Security and Chase / Zbigniew W. Ras and Seunghyun Im ...114
Defending against Distributed Denial of Service / Yang Xiang and Wanlei Zhou ...121
Digital Divide Implications and Trends / Irene Chen and Terry T. Kidd ...130
Digital Rights Management Metadata and Standards / Jo Anne Cote and Eun G. Park ...136
Dilemmas of Online Identity Theft / Omer Mahmood ...143
Document Security in the Ancient World / Christopher H. Walker ... 150
DRM Practices in the E-Publication Industry / Bong Wee Kiau and Norshuhada Shiratuddin ...157
Educational Technology Practitioner-Research Ethics / Kathleen Gray ...164
E-Health and Ensuring Quality / Prajesh Chhanabhai and Alec Holt ...170
Electronic Signatures and Ethics / A. Srivastava and S. B. Thomson ...179
Engineering Multi-Agent Systems / Tagelsir Mohamed Gasmelseid ...187
Ethical Approach to Gathering Survey Data Online / Sophie Nichol and Kathy Blashki ...194
Ethical Behaviour in Technology-Mediated Communication / Sutirtha Chatterjee ...201
Ethical Concerns in Computer Science Projects / Alistair Irons and Roger Boyle ...208
Ethical Debate Surrounding RFID The / Stephanie Etter, Patricia G. Phillips, Ashli M. Molinero, Susan J. Nestor, and Keith LeDonne ...214
Ethical Dilemmas in Data Mining and Warehousing / Joseph A. Cazier and Ryan C. LaBrie ...221
Ethical Erosion at Enron / John Wang, James Yao, Richard Peterson, and Zu-Hsu Lee ...229
Ethical Usability Testing with Children / Kirsten Ellis and Marian Quigley ...235
Ethics and Access to Technology for Persons with Disabilities / Belinda Davis Lazarus ...241
Ethics and Perceptions in Online Learning Environments / Michelle M. Ramim ...246
Ethics and Security under the Sarbanes-Oxley Act / Thomas J. Tribunella and Heidi R. Tribunella ...254
Ethics Education for the Online Environment / Lori N. K. Leonard and Tracy S. Manly ...260
Ethics in Software Engineering / Pankaj Kamthan ...266
Ethics in the Security of Organizational Information Systems / Sushma Mishra and Amita Goyal Chin ...273
Ethics of AI / Kevin B. Korb ...279
Fair Use / Pasi Tyrväskylä ...285
Federal Information Security Law / Michael J. Chapple and Charles R. Crowell ...291
Formulating a Code of Cyberethics for a Municipality / Udo Richard Averweg ...297
Hackers and Cyber Terrorists / M. J. Warren ...304
Homo Electricus and the Continued Speciation of Humans / Katina Michael and M. G. Michael ...312
IT Security Culture Transition Process / Leanne Ngo ...319
ICT Leapfrogging Policy and Development in the Third World / Amanda Third and Kai-Ti Kao ...326
Identity Verification using Resting State Brain Signals / Ramaswamy Palaniappan and Lalit M. Patnaik ...335
Individual and Institutional Responses to Staff Plagiarism / Carmel McNaught ...342
Information Ethics as Ideology / Bernd Carsten Stahl ...348
Information Ethics from an Islamic Perspective / Salam Abdallah ...355
Information Security and the “Privacy Broker” / Michael Douma and Eduard J. Gamito ...362
Information Security Policies for Networkable Devices / Julia Kotlarsky, Ilan Oshri, and Corey Hirsch ...370
Information Security Policy Research Agenda / Heather Fulford and Neil Doherty ...377
Internet and Suicide / Dianne Currier ...384
Internet Piracy and Copyright Debates / Paul Sugden ...391
Internet Research Ethics Questions and Considerations / Elizabeth Buchanan ...397
Interviews with Young People using Online Chat / Elza Dunkels and AnnBritt Enochsson ...403
Intrusion Detection and Information Security Audits / Terry T. Kidd and Robert K. Hiltbrand ...411
Investigation Strategy for the Small Pedophiles World / Gianluigi Me ...418
Managed Services and Changing Workplace Ethics / Alan Sixsmith ...426
Measuring Ethical Reasoning of IT Professionals and Students / Mohammad Abdolmohammadi
and Jane Fedorowicz ...440
Meta View of Information Ethics / Charles R. Crowell and Robert N. Barger ...445
Mitigation of Identity Theft in the Information Age / Reggie Becker, Mark B. Schmidt, and Allen C. Johnston ...451
Mobile Agents and Security / Fei Xue ...457
Modelling Context-Aware Security for Electronic Health Records / Pravin Shetty and Seng Loke ...463
Moral Rights in the Australian Public Sector / Lynley Hocking ...470
Multimodal Biometric System / Ajita Rattani, Hunny Mehrotra, and Phalguni Gupta ...478
Objective Ethics for Managing Information Technology / John R. Drake ...486
Parental Rights to Monitor Internet Usage / Benjamin J. Halpert ...492
Patient Centric Healthcare Information Systems in the U.S. / Nilmini Wickramasinghe ...498
Pedagogical Framework for Ethical Development / Melissa Dark, Richard Epstein, Linda Morales, Terry Countermine, Qing Yuan, Muhammed Ali, Matt Rose, and Nathan Harter ...507
Personal Information Ethics / Sabah S. Al-Fedaghi ...513
Pharming Attack Designs / Manish Gupta and Raj Sharman ...520
Port Scans / Jalal Kawash ...527
Privacy and Access to Electronic Health Records / Dick Whiddett, Inga Hunter, Judith Engelbrecht, and Jocelyn Handy ...534
Privacy and Online Data Collection / Călin Gurău ...542
Privacy in Data Mining Textbooks / James Lawler and John C. Molluzzo ...549
Protection of Mobile Agent Data / Sheng-Uei Guan ...556
Rule-Based Policies for Secured Defense Meetings / Pravin Shetty and Seng Loke ...563
Secure Agent Roaming under M-Commerce / Sheng-Uei Guan ...571
Secure Automated Clearing House Transactions / Jan Skalicky Hanson and Mark B. Schmidt ...579
Security Dilemmas for Canada’s New Government / Jeffrey Roy ...585
Security of Communication and Quantum Technology / Gregory Paperin ...602
Security Protection for Critical Infrastructure / M. J. Warren and T. B. Busuttil ...609
Spyware / Thomas F. Stafford ...616
Sustainable Information Society / Ralf Isenmann ...622
Taxonomy of Computer and Information Ethics / Sabah S. Al-Fedaghi ...631
Tools for Representing and Processing Narratives / Ephraim Nissan ...638
Traditional Knowledge and Intellectual Property / Ulia Popova-Gosart ...645
xiii
Preface
We create technology and choose to adopt it. However, once we have adopted a technological device, it can change us and how we relate to other people and our environment. (Quinn, 2006, p. 3)
…the computer profoundly shapes our ways of thinking and feeling…computers are not just changing our lives but our selves. (Turkle, 2000, p. 129)
Alongside the examination of technological advancements and the development of new computer software and hardware, an increasing number of scholars across a range of disciplines are researching and writing about the ethical dilemmas and security issues which the world is facing in what is now termed the Information Age. It is imperative that ordinary citizens as well as academics and computer professionals are involved in these debates, as technology has a transformative effect on all of our daily lives and on our very humanness. The Encyclopedia of Information Ethics and Security aims to provide a valuable resource for the student as well as teachers, researchers, and professionals in the field.
The changes brought about by rapid developments in information and communication technologies in the late twentieth century have been described as a revolution similar in impact to the Industrial Revolution of the nineteenth century. The development of the personal computer in the 1980s and the creation of the World Wide Web (WWW) in the early 1990s, followed by the development of low-cost computers and high-speed networks, have resulted in dramatic changes in the way humans communicate with one another and gain information. Today, more than 600 million people have e-mail accounts (Quinn, 2006, p. 2). Communication via cell phone and the Internet is now regarded as commonplace, if not indeed, essential by Westerners, yet there remain many groups both in developing countries and within developed countries who do not have access to these technologies or who lack the skills to use them. Technology has thus helped to create social divisions or to reinforce existing ones based on socio-economic and educational differences. These divisions are often described as the gap between the ‘information rich’ and the ‘information poor.’
Technology can bring harm as well as benefit. It can undermine basic human rights and values, and challenge established social or cultural norms and legal practices. While the home PC with an Internet connection may provide us with ready access to a wealth of information, it also makes us potential victims of cyber crime or subject to invasions of our privacy. Some members of society may enthusiastically embrace the new opportunities offered by new technologies, while others such as the elderly or disabled may become increasingly marginalized by the implementation of these technologies in the public domains of commerce, banking, and education.
xiv
Although the technologies may be new, many of the moral dilemmas they give rise to are longstanding. Consequently, knowledge of history is an essential accompaniment to our knowledge of current ethical issues and new technological developments. This is demonstrated by several contributors to this volume who, in ad-dressing ethical problems, draw upon the writings of earlier moral philosophers such as Aristotle and Immanuel Kant. Similarly, articles such as those by Christopher Walker concerning ancient methods of document security remind us that information security is not merely a twenty-first-century issue, but rather one to which computers have given an added dimension.
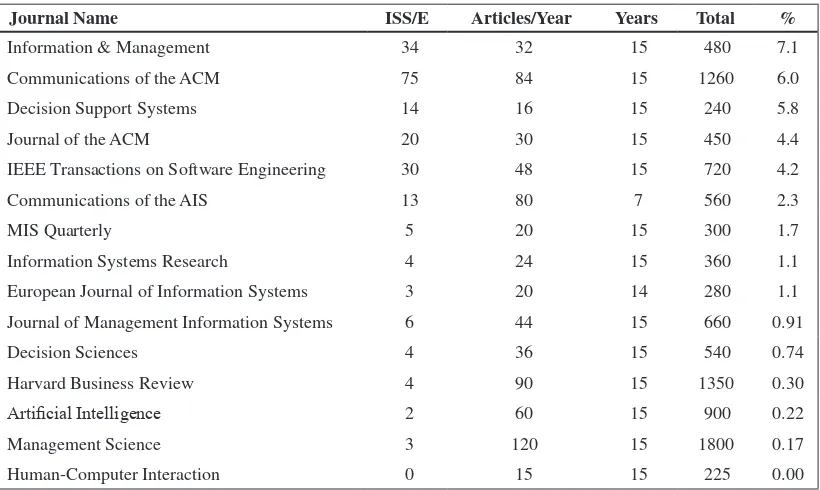
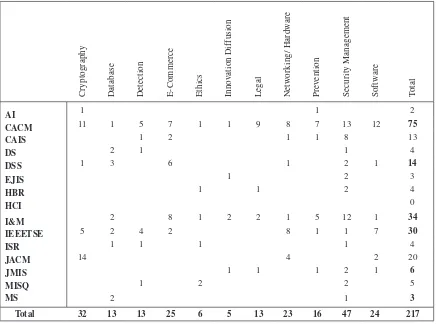
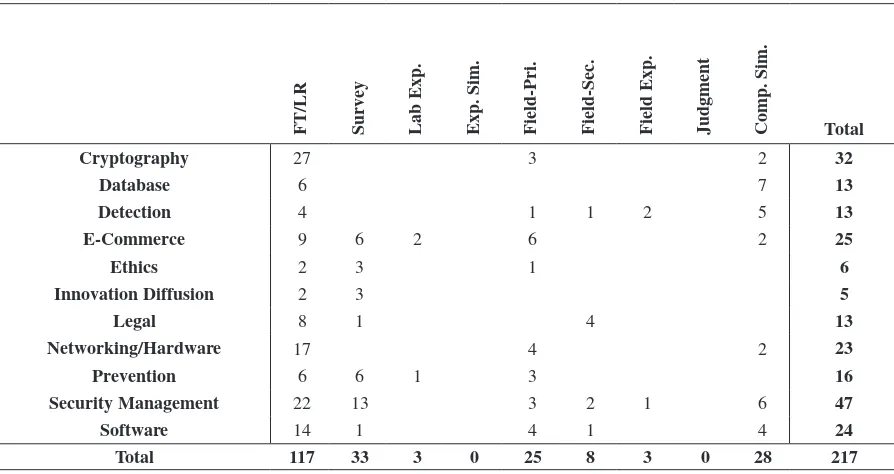
Although the area of Information Ethics is gaining increasing credence in the academic community, the recent study by Jordan, Rainer, and Marshall, which is included in this volume, reveals that there are still relatively few articles devoted to ethics in information systems journals compared with those devoted to security management. The Encyclopedia of Information Ethics and Security addresses this gap by providing a valuable compilation of work by distinguished international researchers in this field who are drawn from a wide range of prominent research institutions.
This encyclopedia contains 95 entries concerning information ethics and security which were subjected to an initial double-blind peer review and an additional review prior to their acceptance for publication. Each entry includes an index of key terms and definitions and an associated list of references. To assist readers in navigat -ing and find-ing information, this encyclopedia has been organized by list-ing all entries in alphabetical order by title.
Topics covered by the entries are diverse and address a wide range of life areas which have been affected by computer technology. These include:
• education • the workplace • health
• privacy
• intellectual property • identity
• computer crime • cyber terrorism • equity and access • banking
• shopping • publishing
• legal and political issues • censorship
• artificial intelligence • the environment • communication
These contributions also provide an explanation of relevant terminology and acronyms, together with descrip-tions and analyses of the latest technological developments and their significance. Many also suggest possible solutions to pressing issues concerning information ethics and security.
xv
In the current era of globalization which has been enabled by the revolution in communications, the renowned ethicist, Peter Singer, suggests that the developed nations should be adopting a global approach to the resolution of ethical and security issuesissues which, he argues, are inextricably linked. As he explains: “For the rich nations not to take a global ethical viewpoint has long been seriously morally wrong. Now it is also, in the long term, a danger to their security” (Singer, 2004, p. 15).
REFERENCES
Quinn, M. (2006). Ethics for the Information Age (2nd ed.). Boston: Pearson.
Singer, P. (2002). One world: The ethics of globalisation. Melbourne: Text Publishing.
Turkle, S. (2000). Who am we? In Baird et al. (Eds.), Cyberethics: Social and moral issues in the computer age (pp. 129-141). New York: Prometheus.
Williams, R. (1981). Communications technologies and social institutions. In R. Williams (Ed.), Contact: Hu-man communication and its history. London: Thames and Hudson.
Dr. Marian Quigley Monash University
xvi
Acknowledgment
I wish to thank all of those involved in the collation and review process of this encyclopedia, without whose support the project could not have been satisfactorily completed.
As well as providing articles for this volume, most of the authors also served as referees for other submissions. Additional reviews were undertaken by my colleagues at Monash University: Mark Szota, Grace Rumantir, Tom Chandler, Joachim Asscher, and by Tim van Gelder of Melbourne University and Allison Craven at James Cook University. Thanks go to all for their constructive and comprehensive reviews.
I am also indebted to Bianca Sullivan, Cheryl Ely, Carmel Dettman, Michelle Jones, and Melanie Smith of the Berwick School of Information Technology, Monash University, who assisted with collating the final submis -sions and assembling the final document at a time which, due to unforeseen circumstances, was a particularly trying period for me.
Special thanks also go to the publishing team at IGI Global for their invaluable assistance and guidance throughout the project, particularly to Michelle Potter and Kristin Roth, who promptly answered queries and kept the project on track, and to Mehdi Khosrow-Pour for the opportunity to undertake this project.
This has been a mammoth task, but one which I have found most rewarding. I am particularly grateful to the authors for their excellent contributions in this crucial and growing area of research and to the Editorial Advisory Board members who, in addition to their contributions as reviewers and authors, helped to promote interest in the project.
Dr. Marian Quigley Monash University
xvii
About the Editor
Marian Quigley, PhD (Monash University); B.A. (Chisholm Institute of Technology); Higher Diploma of
Free ebooks ==> www.Ebook777.com
1
3 D
3D Avatars and Collaborative Virtual
Environments
Koon-Ying Raymond Li e-Promote Pty. Ltd., Australia
James Sofra
Monash University, Australia
Mark Power
Monash University, Australia
Copyright © 2008, IGI Global, distributing in print or electronic forms without written permission of IGI Global is prohibited.
INTRODUCTION
With the exponential growth in desktop computing power and advancements in Web-based technologies over the past decade, the virtual community is now a reality. The latest derivative of the virtual community, made possible by 3D avatars, is called the collaborative virtual environment (CVE). These CVEs often provide “fantasy-themed online worlds” for participants to socially interact. Instead of placing emphasis on team-playing, the sharing of information, and collaborative activities, a CVE focuses on social presence and com-munication processes. Unlike virtual environments which allow participants to discuss what is going on in the real world, the participants’ experiences of the virtual world provided by the CVE are often the main topics for discussion. These CVEs, just like their real counterparts, have their own issues and problems. This article will analyze the potential benefits of avatars, helping to build virtual communities and explore the possible issues that are associated with the CVE.
A virtual community (VC) is a computer-mediated communication environment that exhibits characteris-tics of a community. Unlike the physical community, the participants in a virtual community are not con-fined to a well-decon-fined physical location or to having distinctive characteristics. Members of most VCs (for example, the Final Fantasy game community or a newborn baby support group) are often bounded only by a common interest.
A VC can be a simple message board with limited or no visual identifiers for its users to utilize when posting and sharing their text messages with others. Conversely, it can also be a sophisticated 3D environ-ment with interactive objects and fully detailed
human-oid character animations. The ARPANET, created in 1978 by the U.S. Department of Defense’s Advanced Research Projects Agency, is often said to be the first virtual community (Rheingold, 2000). Other signifi -cant landmarks in the evolution of VCs, as noted by Lu (2006), are: Multi-User Domain/Dungeon (MUD) (1979), Internet Relay Chat (IRC) (1988), America On-Line (AOL) (1989), Doom (online games) (1993), ICQ (instant messaging) (1996), Everquest (Massively Multi-player Online Role-Playing Game (MMORPG)) (1999), and Friendster (social networks) (2003). While the earlier VCs emphasized team-playing, the sharing of information, and collaborative activities, the latest ones (the social networks) focus on social presence and communication processes (Kushner, 2004).
These social networks may be referred to as col-laborative virtual environments (Brown & Bell, 2004). They provide a “fantasy-themed online world” for participants to socially interact and collaborate. There is also a distinctive difference between the two types of VCs in terms of the contents of their discussion: the ear-lier VCs provide an online media to allow participants to discuss what is going on in the real world, while the inhabitants’ experiences within the virtual world are the main topics for conversations in a CVE.
Anonymity of its members is one of the important features of VCs. Avatars are often employed by their members to identify each other. The word ‘avatar’ comes from ancient Sanskrit and means “a manifes-tation of the divine in human form or reincarnation” (Parrinder, 1982). In other words, it is the earthly manifestation of God. The term ‘avatar’ is now used to describe a person’s alter ego in a virtual world. Avatars, such as those used in an online chat environment like ICQ, are 2D image based. The users in these
3D Avatars and Collaborative Virtual Environments
ments select a name or a 2D image so other members may identify them.
Avatars can also be 3D. With 3D avatars, users can project a certain amount of their own personality through the appearance of the avatars chosen to repre-sent them, while remaining anonymous. A majority of the current 3D avatars are humanoid in form and many allow for gestures and facial expressions.
This article focuses only on 3D avatars and their 3D virtual worlds. The benefits of 3D avatars helping to build virtual communities will be explored and the associated issues, particularly those relating to CVE, will be analyzed and discussed.
3D AVATARS AND THE
VIRTUAL WORLD
Users can use their 3D avatars’ appearance to project their chosen personalities and characteristics to others within a virtual world (see Figure 1) and, at the same time, can maintain their chosen degree of anonymity. Anonymity helps open communication channels, en-courages users to voice more freely, and removes social cues. As such, avatars can help to promote the better sharing of information. With the freedom of choice in both representation and anonymity, users will acquire a more comfortable version of themselves, which would help them to increase their levels of confidence in dealing with others. According to Brown and Bell (2004), anonymity encourages interactions between strangers which do not happen in the real world. Avatars can also be used to help businesses and large corporations conduct successful meetings (Exodus,
2003). Avatars, including the text- and 2D-based types, can help to remove human inequalities, such as racism and sexism, as well as biases against mental deficien -cies and handicaps (Castronova, 2004). Victims who are troubled by “issues of secrecy, hyper vigilance, sexuality and intimacy” can now gain comfort from other virtual world inhabitants and online therapists. Victims, having been physically or sexually abused, who feel ashamed to discuss their situations, can use their avatars to enter the virtual world to commence treatment (Fenichel et al., 2002).
In text-based chat virtual environments, meanings are sometimes lost due to lack of supporting cues such as body language and facial expression. Emoticons, such as smileys ( ), can help to partially solve this issue. 3D avatars in humanoid form can now provide gestures, postures, body languages, as well as facial expressions. Gestures include handshakes, nodes, and even dancing with joy. According to Brown and Bell (2004), “emotional communication enhances com-munication.” 3D avatars can help to express emotions through facial expressions and gestures, thus enhancing the communication process. They help to provide a better environment for collaborative activities.
In text-based virtual communication, posted mes-sages are often not specific for a particular participant. Conversations within a 3D avatar world, however, can be targeted at a particular audience, similar to what is happening in the real world. 3D avatars’ gestures and gazes can assist in the communication process within a crowded virtual room and identify who is currently engaged in a conversation. It also helps to identify those who are in private communication and thus al-lows conversations to remain undisturbed (Salem & Earle, 2000).
Besides being more aesthetically appealing to users, 3D avatars can be more engaging as the users can have a choice in their perspective: a first- or third-person view of the virtual world. These avatars not only rep-resent the presence of their users in a virtual space, but also display the users’ orientations and locations (Salem & Earle, 2000). The users can now interact with other objects or avatars within the virtual world similar to what is happening in the real world. Some 3D virtual worlds are now enhanced with 3D sound (with distance attenuation and stereo positioning) to provide feedback as to the spatial positioning of other participants and elements within the virtual world. As such, 3D avatars do not only have the potential to assist
Figure 1. Avatar’s eyelashes shape and fingernail
3 3D Avatars and Collaborative Virtual Environments
3 D
in building and reinforcing virtual communities; they can also motivate and encourage all users to enter a VC for a longer period of time.
3D avatars provide compelling experiences to users by transforming VCs from the traditional environment for collaborative/competing activities and sharing in-formation, into fantasy-theme-based online hangout spots (Kushner, 2004). 3D avatars now enable millions to experience life in a digital landscape and allow them to engage in novel experiences (see Figure 2).
A CVE inhabitant can now experience what it is like to have another career. He or she can now take on the opposite gender. This would allow him or her to explore the ways in which one gender interacts with the other and learn to appreciate the opposite sex. Socialization and experience within the virtual world take precedence over the discussion of real-world issues. “The virtual world feeds upon itself, providing shared experiences that its inhabitants can chat about” (Kushner 2004). For example, a glitch in the system provides exciting news within a virtual world for its inhabitants to be excited for a few days (Brown & Bell, 2004).
Avatars can now be customized with extra virtual items to reflect the chosen status of the persons they represent. Users of virtual worlds can now use real mon-ies to purchase real-life fashion-branded (for example, Nike and Levi) virtual items. This helps to create a virtual economy that ultimately will consolidate and provide further growth to the virtual communities (Kushner, 2004).
POTENTIAL PROBLEMS
An avatar allows its user to retain a chosen degree of anonymity. Therefore, no one can be assured as to whether the user is disclosing his or her true identity. An avatar’s appearance and name can easily be changed by its user, and therefore, consistency in identification can never be assured (Taylor, 1999). This removes accountability for ones’ actions and can thus prompt users to behave badly and rudely or to act irresponsibly (Sulers, 1997). Users may even commit offences that they would not otherwise do in the real world. There are already reported cases of rape in cyberspace. For example, the owner of a male avatar used some coding trick to control female avatars and then sodomized them in a public room in front of a large “crowd.” It was also reported that some of these victims felt that they had been violated personally, despite the fact that the events were virtual; they carried such feelings over to the real world (Dibbell, 1993)! Cyber bullying, online harassment, and cyber stalking are other examples of offences. Countermeasures such as user IP tracking and possible prosecution in the real world are being developed. Nevertheless, the incidence of these offences are on the rise (ABC, 2006).
Anonymity may keep users of virtual communities motivated to participate, but can also lead to identity deception: the use of avatars allows participants in a virtual world to conceal their true identities and to claim to be someone that they are not. A member of a virtual community can deliberately have as many avatars or identities as he or she sees fit, with the intention to deceive others. The identity deceptions may be in the form of gender, race, or qualification. While real-world evidence of a person’s credibility is reasonably easy to determine, such assurance may not be offered in the virtual world. In the real world we are better equipped to ascertain whether what we are being told is fact or lie. Taking advice within a virtual world is therefore dangerous. In fact, it is important to Figure 2. VC inhabitants can interact as if in real life
3D Avatars and Collaborative Virtual Environments
bear in mind that “the best, busiest experts are prob-ably the least likely ones to bother registering with any kind of expert locator service” (Kautz & Selman, 1998). With the ease in changing avatar at will, it is almost impossible to ban any users who have violated their privileges. Identity deception can easily lead to virtual crimes, such as hacking into others’ accounts and selling of a virtual house and other properties to another person for real money.
Assuming a person’s gender from his or her avatars is impossible. In VC where chimeras and cyborgs are available as the choice for avatars, gender identity is often blurred. A user can also impersonate an op-posite sex. In fact, many male users log onto the VCs as women because they enjoy the sexually suggestive attention they received from other avatars. Gender blurring and gender impersonation with an intention to deceive others can be a big issue (Kaisa, Kivimaki, Era, & Robinson, 1998).
The ability to propagate ideas to individuals across the globe with probable anonymity can be alarming. Social behaviors, especially for the youth, can easily be shaped by media through propaganda and promo-tions. Behavior molding is now easy when the youths are actually “living” out their experiences through their avatars (Winkler & Herezeg, 2004, p. 337).
Because of the lack of facts about a VC member’s identity, respect and trust between members can be issues. Lack of respect and trust of others may intro-duce problems into the real world when some of the VC members carry their behaviors over to the real world.
In an online forum, it is generally accepted that those who participate are actually who they purport to be and have the desire to maintain their individuality consistently. The motivation behind this may be that a user needs to use his or her avatar’s position as a ‘status symbol’ for dissimulating his knowledge, or may merely stem from his or her wish for instant recognition by fellow members. However, within a 3D-avatar-based virtual environment, in particular the CVE, it is gener-ally accepted as fact that an avatar is a fabrication of a user’s imagination. As such, many users of VC treat “other players impersonally, as other than real people” (Ludlow, 1996, p. 327) and may carry these molded unwelcome behaviors over to the real world.
As virtual spaces can be accessed simultaneously, a user will, therefore, have the ability to take on various
identities within multiple CVEs. They can also take on various identities within one virtual world. They can exert different personalities behind their avatars simultaneously. Such a behavior would be considered in the real world as a psychiatric disorderdissociative identity disorder.
Addiction to CVEs is an issue. 3D avatars make one feel that one is really ‘there’. CVE has the elements of suspense and surprise that can be experienced in the real worldone will not know what is around the corner or the reactions from others in the shared vir-tual spaces. Those who endure loneliness, alienation, and powerlessness in the real world will look to the virtual world for comfort (Bartle, 2003; Cooper, 1997). They can now be free to leave behind the constraints of the real world and play a role in the community that they feel is more comfortable to them. They may even abandon the real world and continue to hang out at the cyber spots. CVE is also an attraction to teenagers who may have found that they can acquire their perfect self and interact with those who can only be found in their imagination. Despite the fact that some of the larger virtual worlds already have mechanisms in place for detection and prevention, a user can hop from one virtual world to another to satisfy their addiction to VC, refusing to live in the real world.
As the realism in the CVE improves, some users may find it difficult to differentiate the real world from the virtual world. Illusion of being in the cyber world while in the real world can be a problem. CVEs bring people of different cultures together. Different ethnic or national cultures, as well as religions or religious attitudes may have variations in their definitions of acceptable behaviors. These differences in perceptions about acceptable actions and behaviors can create ten-sions within the virtual world. The worst case scenario would be the lowering of the community norm to the common denominator and ultimately alter the norms in the real world.
5 3D Avatars and Collaborative Virtual Environments
3 D
CONCLUSION
Avatar technology helps to build virtual communi-ties and makes CVEs a reality. It brings compelling experiences to VC users and encourages more users to enter virtual worlds for longer periods. Just like any other emerging technology, avatars benefit humankind but also bring some negatives. Addiction to CVEs, abandonment of the real world, the blurring between the real world and the virtual world, crimes commis-sion in the pursuance of the finance of virtual items, virtual rape, gender impersonation, and personality disorders are just some of the issues. If unchecked, these problems will likely cause significant detriment to our real-world community in the future. Currently, solutions such as user-IP tracking, laws against virtual crimes and bullying, and rules of some virtual world creators forbidding users from performing certain acts (such as lying down, removing clothing from avatars, and touching without consent) have been developed to tackle some of the issues. However, due to anonymity and the fact that users can change their avatars at will, it would be difficult, if not impossible, to address all of the relevant issues. Significant cooperation efforts at the global level between the virtual world creators, law reinforcing agencies, computer security and net-working experts, user groups, and virtual community organizers are needed in the next few years to develop countermeasures and to stop problems at their roots. Above all, there should be a global agent that will over-see the conduct of virtual world creators, virtual world organizers, and users, and prosecute those who have abused their privileges within the virtual world.
REFERENCES
ABC. (2006). Cyber bullying on the rise, say experts. ABC News - Good Morning America, (February 2). Bartle, R.A. (2003). Designing virtual worlds. New Riders Publishing.
Brown, B., & Bell, M. (2004). Social interaction in ‘there’. CHI,24(19).
Castronova, E. (2004, February 10). The future of cyberspace economics. Proceedings of the O’Reilly Emerging Technology Conference, San Diego, CA. Cooper, S. (1997). Plenitude and alienation: The subject
of virtual reality. In D Holmes (Ed.), Virtual politics: Identity and community in cyberspace (pp. 93-106). London: Sage.
Dibbell, J. (1993). A rape in cyberspace. The Village Voice, (December 21).
Exodus. (2003). Avatar-based conferencing in virtual worlds for business purposes. Retrieved February 2, 2006, from http://www.exodus.gr/Avatar_Conference/ pdf/Avatar_leaflet.pdf
Fenichel, M., Suler, J., Barak, A., Zelvin, E., Jones, G., Munro, K., Meunier, V., & Walker-Schmucker, W. (2002). Myths and realities of online clinical work. CyberPsychology & Behavior, 5(5), 481-497.
Heim, M. (2000). Some observations on Web-art-writ-ing. Retrieved February 2, 2006, from http://www. fineartforum.org/Backissues/Vol_14/faf_v14_n09/ text/feature.html
Lu, K.Y. (2006). Visual identity and virtual community. Retrieved January 31, 2006, from http://www.atopia. tk/eyedentity/netid.htm
Kaisa, K., Kivimaki, A., Era, T., & Robinson, M. (1998, November 2-5). Producing identity in collaborative virtual environments. Proceedings of VRST’98. Kautz, H., & Selman, B. (1998). Creating models of real-world communities with ReferalWeb. Retrieved September 6, 2005, from http://citeseer.csail.mit.edu/ kautz98creating.html
Kushner, D. (2004). My avatar, my self. Technology Review,107(3).
Lee, O. (2004). Addictive consumption of avatars in cyberspace. CyberPsychology & Behavior,7(4). Ludlow, P. (1996). High noon on the electronic fron-tier: Conceptual issues in cyberspace. Massachusetts Institute of Technology, USA.
Paniaras, I. (1997). Virtual identities in computer medi-ated communication. SIGGROPT Bulletin,18(2). Parrinder, G. (1982). Avatar and incarnation: A com-parison of Indian and Christian beliefs. New York: Oxford University Press.
3D Avatars and Collaborative Virtual Environments
Rheingold, H. (2000). The virtual community: Home-steading on the electronic frontier. Cambridge, MA: The MIT Press.
Salem, B., & Earle, N. (2000). Designing a non-verbal language for expressive avatars. Proceedings of CVE 2000.
Suler, J. (1997). The psychology of cyberspace. Re-trieved September 4, 2005, from http://www.rider. edu/~suler/psycyber/psycyber.html
Taylor, T.L. (1999). Life in virtual worlds: Plural existence, multimodalities. Retrieved October 23, 2005, from http://www.cts.cuni.cz/~konopas/liter/Tay-lor_life%20in%20Virtual%20Worlds.htm
Winkler, T., & Herezeg, M. (2004). Avatarscan they help developing personality among students in school? Proceedings of IEEE 2004.
KEY TERMS
Avatar: A graphical symbol used by virtual
com-munity members in order to represent themselves in the virtual environment.
Collaborative Virtual Environment: A virtual
community usually represented in the form of a 3D environment where individuals are afforded a high
degree of interaction via their avatar with other indi-viduals and objects within the environment.
Dissociative Identity Disorder: A psychiatric
disorder of an individual projecting more than one distinct identity into his or her environment.
Emoticon: Image icon used in a text-based chat
environment to communicate emotional expression, for example, happy, sad, laughing.
First-Person View: Where visual information is
presented to the individual as though being perceived through the eyes of his or her avatar.
MessageBoard: A Web-hosted communication tool
in which individuals can correspond via the posting of text messages.
SocialNetwork: A social structure that provides a
platform where individuals may extend their personal contacts or attain personal goals.
Third-PersonView: Where visual information is
presented to the individual from a perspective external to his or her 3D avatar.
VirtualCommunity: An environment where the
7
A
Access Control for Healthcare
Yifeng Shen
Monash University, Australia
Copyright © 2008, IGI Global, distributing in print or electronic forms without written permission of IGI Global is prohibited.
INTRODUCTION
Thanks to the rapid development in the field of infor -mation technology, healthcare providers rely more and more on information systems to deliver professional and administrative services. There are high demands for those information systems that provide timely and accurate patient medical information. High-quality healthcare services depend on the ability of the health-care provider to readily access the information such as a patient’s test results and treatment notes. Failure to access this information may delay diagnosis, result-ing in improper treatment and risresult-ing costs (Rind et al., 1997).
Compared to paper-based patient data, computer-based patient data has more complex security require-ments as more technologies are involved. One of the key drivers to systematically enhance the protection of private health information within healthcare providers is compliance with the healthcare information system security standard framework and related legislation. Security standards and legislation of the healthcare information system are critical for ensuring the con-fidentiality and integrity of private health information (Amatayakul, 1999). Privacy determines who should have access, what constitutes the patient’s rights to confidentiality, and what constitutes inappropriate access to health records. Security is embodied in stan-dards and technology that ensure the confidentiality of healthcare information and enable health data integrity policies to be carried out.
Based on the investigation of security standard and legislation, we can analyze and create basic security requirements for the healthcare information system. To meet the security requirements, it is necessary to deploy an appropriate access control policy and sys-tem within the organization. As discussed elsewhere (Sandhu, Coyne, Feinstein, & Youman, 1996), role-based access control (RBAC) is a promising technology for managing and enforcing security in a large-scale distributed system. In the healthcare industry, RBAC has already been adopted by the Health Level Seven
(HL7) organization as a key access control standard (Blobel & Marshall, 2005).
HL7 was established in 1987 to develop standards for the electronic interchange of clinical, financial, and administrative information among independent healthcare-oriented computer systems. In June of 1994, HL7 was designated by the American National Standard Institute (ANSI) as an ANSI-accredited standards de-veloper. HL7, in its draft Security Service Framework (Kratz et al., 2005) categorizes healthcare information security exposures in the following manner:
• Disclosure: Exposure, interception, inference
intrusion
• Deception: Masquerade, falsification, repudia
-tion
• Disruption: Incapacitation, corruption,
obstruc-tion
• Usurpation: Misappropriation
Although RBAC has been introduced to the latest version of HL7 (version 3) for strengthening the security features, it only includes those basic functions. Due to the complexity of the healthcare process, RBAC with only basic functions may not be sufficient. More contextconstraints need to be processed in addition to traditional RBAC operations.
The major contributions we have made in this article are:
• Illustrating the detailed design of a flexible and securer RBAC model for a healthcare information system based on HL7 standard;
• Introducing the basic elements of HL7 v3 and RBAC, which are necessary for us to realize our proposed model; and
• Analyzing the potential weakness of current HL7 standard and the basic RBAC model in terms of security and flexibility.
Access Control for Healthcare
analysis of HL7 version 3. We then explain the RBAC concept model and describe our major work, and finish with our conclusion and future work.
HL7 VERSION 3
What is HL7?
Health Level Seven is one of several American National Standards Institute-accredited Standards Developing Organizations (SDOs) operating in the healthcare arena. Most SDOs produce standards (sometimes called specifications or protocols) for a particular healthcare domain such as pharmacy, medical devices, imaging, or insurance (claims processing) transactions. HL7’s do-main is clinical and administrative data (HL7, 2005). HL7 is also a non-profit volunteer organization. Its members are the providers, vendors, payers, consul-tants, and government groups who have an interest in the development and advancement of clinical and administrative standards for healthcare services. In its achievements so far, HL7 has already produced HL7 Version 2 (HL7 v2) specifications (HL7, 2005), which are in wide use as a messaging standard that enables disparate healthcare applications to exchange key sets of clinical and administrative data. However, the newer specification HL7 Version 3 (HL7 v3), still under development, pertains to all aspects of clinical and administrative data in health services. Unlike its older version, HL7 v3 specifications are completely based upon the extensible markup language (XML) standards, and so have potential to win an instant ac-ceptance by developers and vendors alike.
The target system during our research is based on HL7 v3, so only HL7 v3 will be described in this article.
The lack of data and process standards between both vendor systems and the many healthcare provider organizations present a significant barrier to design ap -plication interfaces. With HL7 v3, vendors and providers will finally have a messaging standard that can provide solutions to all of their existing problems.
HL7 v3 is based on a reference information model (RIM). Although RIM is not stabilized yet, once it is stabilized, it will be the most definitive standard to date for healthcare services. The following section will highlight some key components of RIM.
Reference Information Model
RIM is the cornerstone of the HL7 Version 3 develop-ment process. An object model created as part of the Version 3 methodology, RIM is a large pictorial repre-sentation of the clinical data (domains) and identifies the lifecycle of events that a message or groups of related messages will carry. It is a shared model between all the domains and as such is the model from which all domains create their messages. RIM comprises six main classes (Beeler et al., 2005):
1. Act: Represents the actions that are executed and
must be documented as health care is managed and provided.
2. Participation: Expresses the context for an act
in terms such as who performed it, for whom it was done, where it was done, and so forth. 3. Entity: Represents the physical things and
be-ings that are of interest to and take part in health care.
4. Role: Establishes the roles that entities play as
they participate in health care acts.
5. ActRelationship: Represents the binding of one
act to another, such as the relationship between an order for an observation and the observation event as it occurs.
6. RoleLink: Represents relationships between
individual roles.
Three of these classesAct, Entity, and Roleare further represented by a set of specialized classes or sub-types.
RIM defines all the information from which the data content of HL7 messages are drawn. It follows object-oriented modeling techniques, where the information is organized into classes that have attributes and that maintain associations with other classes. RIM also forms a shared view of the information domain used across all HL7 messages, independent of message structure.
HL7 v3 Security
9 Access Control for Healthcare
A
information and to authenticate requests for services than has been common in the past. The new functions may include, but are not limited to, limiting the right to view or transfer selected data to users with specific kinds of authorization, and auditing access to patient data, electronic signature, and authentication of users based on technologies more advanced than passwords. Version 3 will seek out and reference standards such as X.500 (Weider, Reynolds, & Heker, 1992) and RFC 1510 to support conveying the necessary information from one healthcare application system to another, so that these systems may perform the authorization and authentication functions. Version 3 will also seek out and adopt industry security standards that support con-veying the necessary information from one healthcare application system to another, so that these systems may perform the confidentiality functions.
To meet the security goals, the HL7 Secure Trans-action Special Group has created a security service framework for HL7 (Kratz et al., 2005). According to the scope of the framework, HL7 must address the following security services: authentication, authoriza-tion and access control, integrity (system and data), confidentiality, accountability, availability, and non-repudiation. The HL7 security service framework uses case scenarios to illustrate all the services mentioned above. All those case scenarios can help the readers to understand those services in a very direct way. How-ever case scenarios are not detailed enough to be an implementation guide for the security services.
In this article we are going to design a flexible model for one key security serviceaccess control. This model will extend the case scenarios to a very detailed level which can be directly used as an implementation guide for HL7 v3.
ROLE-BASED ACCESS CONTROL
RBAC has became very popular in both research and industry. RBAC models have been shown to be “policy-neutral” in the sense that by using role hier-archies and constraints (Chandramouli, 2003), a wide range of security policies can be expressed. Security administration is also greatly simplified by the use of roles to organize access privileges. A basic RBAC model will be covered in this section, as well as an advanced model with contextconstraints.
Basic RBAC Model
The basic components of the RBAC model are user, role, and permission (Chen & Sandhu, 1996). The user is the individual who needs access to the system. Membership to the roles is granted to the user based on his or her obligations and responsibilities within the organization. All the operations that the user can perform should be based on the user’s role.
Role means a set of functional responsibilities within an organization. The administrator defines roles, a combination of obligation and authority in organization, and assigns them to users. The user-role relationship represents the collection of users and roles.
Permission is the way for the role to access more than one resource.
As shown in Figure 1, the basic RBAC model also includes user assignment (UA) and permission assign-ment (PA) (INCITS359, 2003).
Theuserassignment relationship represents which user is assigned to perform what kind of role in the organization. The administrator decides the user as-signment relationship. When a user logs on, the system UA is referenced to decide which role it is assigned to. According to the object that the role wants to access, the permission can be assigned to the role referenced by the permissionassignment relationship.
The set of permissions (PRMS) is composed of the assignments between operations (OPS) and objects (OBS).
UA and PA can provide great flexibility and granu -larity of assignment of permissions to roles and users to roles (INCITS359, 2003). The basic RBAC model has clearly illustrated the concept about how role-based access control works within an organization. However it may not be dynamic enough when the business pro-cess becomes very complex. Thus the idea of context constraints is introduced to make the RBAC model more useful.
RBAC Model with Context Constraints
Access Control for Healthcare
2001). In this section we describe the contextconstraints in an RBAC environment.
A context constraint is an abstract concept. It speci-fies that certain context attributes must meet certain conditions in order to permit a specific operation. As authorization decisions are based on the permissions a particular subject/role possesses, contextconstraints are associated with RBAC permissions (see Figure 2).
The context constraint is defined through the terms context attribute, context function, and context condi-tion (Strembeck & Neumann, 2004):
• A context attribute represents a certain property of the environment whose actual value might change dynamically (like time, date, or session-data, for example) or which varies for different
instances of the same abstract entity (e.g., loca-tion, ownership, birthday, or nationality). Thus, context attributes are a means to make context information explicit.
• A context function is a mechanism to obtain the current value of a specific context attribute (i.e., to explicitly capture context information). For example, a function date() could be defined to return the current date. Of course, a context function can also receive one or more input pa-rameters. For example, a function age(subject) may take the subject name out of the subject, operation, object_ triple to acquire the age of the subject, which initiated the current access request, for example, the age can be read from some database.
Figure 1. Core RBAC
USERS ROLES
SES-SIONS
OPS OBS
(UA) User Assignment
(PA) Permission Assignment
user_sessions session_roles
PRMS
Figure 2. RBAC permissions with context constraints
Permission
Subject Role Permission
Role Hierarchy
Context
11 Access Control for Healthcare
A
• A context condition is a predicate that consists of an operator and two or more operands. The first operand always represents a certain context attribute, while the other operands may be either context attributes or constant values. All variables must be ground before evaluation. Therefore, each context attribute is replaced with a constant value by using the corresponding context function prior to the evaluation of the respective condition. • A context constraint is a clause containing one or
more context conditions. It is satisfied if and only if (iff) all context conditions hold. Otherwise it returns false.
A context constraint can be used to define condi -tional permissions. Based on the terms listed above, the conditional permission is a permission associated with one or more contextconstraints, and grants access iff each corresponding context constraint evaluates as “true.”
As we can see, a context constraint can help the organization provide more flexible and securer control for the RBAC model.
Design a RBAC Model with
Context Constraints for the
Healthcare Information System
Based on HL 7 Version 3
The access control model we are going to describe is a method to control access on a healthcare information system. It is developed to enhance the security and flexibility of traditional access control systems. The resource to be accessed in this article is limited to a patient’s electronic health record (EHR).
The primary purpose of the EHR is to provide a documented record of care that supports present and future care by the same or other clinicians. This documentation provides a means of communication among clinicians contributing to the patient’s care. The primary beneficiaries are the patient and the clinician(s) (ISO/TC-215 Technical Report, 2003).
System design will include two major phases: 1. Components design: Describes all the necessary
elements that make up the system.
2. Data flow design: Describes all the processes that make the whole system work.
Components Design
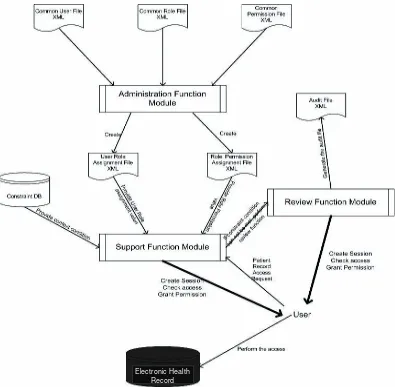
As described in the previous section, the RBAC sys-tem must include the basic elements such as user, role, permission, user-role assignment, and role-permission assignment. All those elements will be associated with real values in our system design. Figure 3 illustrates the overall structure of the system.
• User: Anybody with authenticated identity can
act as the user in the system. For example, after Tom successfully logs into the hospital’s computer system with his user ID 19245678, he becomes the user of our system.
• Role: The set of roles can be retrieved from those
functional roles that already exist in the current healthcare information system such as physician, pharmacist, registered nurse, and so forth. As the number of roles is limited in our system, we can store all the role information by simply using an XML file instead of a database. This file is named “Common Role File.xml.”
• Permission: The scope of the permissions in
our design will focus on those system operations (create, read, update, delete, execute, etc.). Similar to role information, we use another XML file with the name “Common Permission File.xml” to represent all the permission information. As shown in Figure 3, the user, role, and permission file can be used as the basic input for the whole system. To generate user-role assignment and role-permission assignment relationship, we introduce the adminis-trationfunction module. This module is designed to create and maintain the user role assignment file and role permission assignment file.
The rules of user role assignment and role per-mission assignment are referenced from the security section of HL7 v3 standard (HL7 Security Technical Committee, 2005).