SENTRA I - 61
BEHAVIOR ANALYSIS OF MALWARE IN INSTITUT
TEKNOLOGI SEPULUH NOPEMBER
SURABAYA,INDONESIA
Ejaz Karim
Information System Department Institut Teknologi Sepuluh Nopember
Surabaya, Indoensia 60111 jazzi.pisces@gmail.com
Abstrak
An almost incomprehensible amount of data and information is stored on millions and millions of computers worldwide. To be able to defend against the threat imposed by malware we need to understand both how and why the malware exists. This document presents the nature of malware today and outlines some analytical techniques used by security experts. Furthermore, a process for analyzing malware samples with the goal of discovering the behavior and techniques used by the samples is presented. An analysis is performed on malware samples, disclosing behavior, location, encryption techniques. So these samples are being analyzed by tools named as Threat Expert and Anubis. The samples will be also analyzed on real system and results will be compared with Anubis and Threat Expert. This research is expected to describe and explain how malware and other malicious software spread through internet, network and computers. The encryption techniques used by the malware programmers to encrypt malware and to hide these viruses from the users. The damage done by the malicious code to the target machine, network or computers. It should also show the techniques used by the programmers and malware vendor to spread through different platforms. The results are also expected to show that which platforms are being attacked by the malware and why.
Keywords: Malware, Encryption Technique, Threat Expert, Behavior Analysis, Anubis, Platforms.
Introduction
The story of malicious software began around 1982 when the first virus with replicating abilities and harmful intent was written by a high-school student called Rich Skrenta for the Apple II systems [1][2]. The virus was called “The Elk Cloner”. It infected a computer when the machine was booted from an infected floppy disk, copying itself to the new machine. When an uninfected floppy disk was inserted in an infected machine, it copied itself to the floppy, thus spreading itself. Its behavior was relatively harmless; it displayed a small poem every 50th boot, however it also had the unintended effect of overwriting code on particular systems.
I - 62 SENTRA
This development not only makes the malicious software more dangerous, as new ways to make use of the software are found, but it also makes the detection, analysis, and removal of the software increasingly more difficult. Examples are botnets, with the Storm botnet being the most reputed today [3], which run on machines all over the world without the user’s knowledge, rendering the machines at the vim of the botnet controllers.
Information and computer security are becoming more important as we trust computers with critical and sensitive information and functions. Malware is one of the greatest threats against the security of digital information. To be able to battle malware and malware developers we need to understand why the malware was developed and how it accomplishes its tasks. We achieve this by analyzing current malware samples, disclosing techniques and objectives of the samples, thus improving the ability to combat malware, reduce its significance and improve computer security.
Background & related work
A computer virus is a program or segment of an executable computer code that is designed to reproduce itself in computer memory and, sometimes, to damage data. Nowadays, the computer virus term is used as a general term for various harmful programs. Technically, the virus is used to describe the oldest type of harmful programs. A virus is either a stand-alone executable file or can be embedded in larger bodies of code. The virus self-replicates itself inside the same system and cannot spread to other computers without human assistant. A worm is similar to the virus (technicality) but it exploits computer networks to spread from computer to computer over the Internet. In practice, any software that replicates itself may be termed a virus, and most viruses are designed to spread themselves over the Internet and are therefore called worms. [2]
Nowadays, malicious software (malware) is the general term that is used to describe viruses, worms and other types of harmful and undesirable programs. Malware is any program that works against the interests of the system’s user or owner to the interest of other people. [3]
Most of the previous researches shows that, to check the behavior of malware the frameworks have been used either to detect or to analyze malware[5][6]. Most of the approaches and detection techniques used in the researches have their own way of checking and analyzing malware, some researches have been done in mobile platforms and most are in Windows[7].by checking all of the above papers we can say that no research is been done before like this research shows, that is two online tools(Anubis and Threat Expert) have been used to check behavior and the results from these tools will be compared with the real system which is the contribution of this thesis.
By checking previous researches done five out of twenty papers shows that frameworks have been used to detect and analyze malware on Windows and these frameworks use algorithms, machine learning, function hooking, system calls, execution and analysis[8][9]. Two systems like AMAL and Ether uses automatic analysis of malware and virtualization and emulation to check malware behavior[10][11]. One paper shows that Brower help objects has been used to check the behavior with the help of browsing behavior. Six out of twenty researches have been done in Android platforms to check the mobile malware behavior which uses recognizers systems, input output system calls, data mining and anomaly detection.one paper shows that the malware behavior is being detected from web reports and other shows that how malware will be classified and detected through system state changes.
By comparing all of the above mentioned researches, some of the researches uses frameworks to analyze and detect malware, some used tools to do the same thing, some researchers focused on mobile malware and on Android platforms and some adapt their own approaches and detection methods[12][13], so the conclusion derived from above researches is that not a single researcher has done the research like this research shows, this thesis uses two online tools and a real system, the results from these tools will be compared to the real system results to satisfy those results.
SENTRA I - 63 “Since the malware samples were executed within VMware, samples that employ anti-VM evasion techniques may not exhibit their malicious behavior. To mitigate this limitation, the samples could be run on a real, non-virtualized system, which would be restored to a clean state after each simulation [14]”.
Methodology and Tools
In the first part of this paper we will outline some of the theoretical aspects of today’s malware and malware analysis to create an understanding of what malware is, its different forms, and common malware analysis techniques. Samples will be analyzed using tool called as Threat Expert and Anubis which are online tools to check the behavior of malwares and these samples will be also applied to real system to check real behavior of malware. The results from two tools will be compared to real system results for satisfactory results. The analysis will seek to map each sample’s behavior and functionality and to some extent discover techniques used to achieve their functionality. For this task we will use any good system for analysis. Following is the flow chart analysis of malware.
Figure 1: Flow chart of methodology of malware analysis.
3.1 Data Acquiring
The data acquiring step has been supported by our honorable lecturer through which access has been granted to get the data from Honeypot Server of Institut of Technology Sepuluh Nopember. The malware samples were been acquired through FileZilla software, which is a data sharing software. After that the samples were stored on the disk for further steps.
3.2 Malware Analysis
After data acquiring and storing it on the disk, the next step is to do analysis through online tools called as Threat Expert and Anubis which are free and reliable. The samples will be uploaded to the online tool server and after results will be will be saved in pdf format. To check the behavior of malware on real system, this research will do some monitoring processes with the help of Process Monitor and Wireshark. Those processes are Registry monitoring, Network monitoring, to monitor a file and File integrity Check.
3.3 Conclude the Results
I - 64 SENTRA
Analysis of Results
For
the analysis of the samples provided by the Honey pot server of Institut of
Teknologi Sepuluh Nopember this research goes through the following procedures.
The samples cannot be acquired directly from the honey pot, so for this purpose FileZilla software was used to download samples from remote server through username and password. After downloading from the server the samples were being saved on the system as a zip file.
First samples were being analyzed one by one by Threat Expert. The samples were submitted to online database in the Threat Expert website, which allows us to submit samples online to their server in .zip and .exe formats. All the samples were submitted to the server as exe format and the reports were being saved in an online account to access globally. these can be downloaded in xml format. Almost all of the samples were found to be the worms but only two samples were backdoors.
Secondly all of the samples were being analyzed by Anubis. The samples were submitted to the online database of Anubis same as Threat Expert. The same samples were submitted to the online server with same format as Threat Expert and the results were same for all the samples except two samples. The last one was difficult task to be accomplished because this research applies the malware to the real system that is the samples were being applied to a live system to check the real behavior. For this a computer system with processor speed of Core i3 with 4GB RAM and the windows 7 was used to check the behavior. To check the file system activity, registry activity and the network activity this research used Process monitor and Wireshark to check the above activities of malware. The malware cannot be executed directly, so the samples were made as exe file with the help of feature available in Windows 7 and after that those were executed to the system.
Analysis of Results
4.1 Threat Expert Analysis 4.1.1 Registry Activities
Worm: Win32/Conficker.B tries to copy itself in the Windows system folder as a hidden DLL file using a random name. If it fails, it can then try to copy itself with the same parameters in the following folders:
%ProgramFiles% \Internet Explorer
For this case the Threat Expert reports shows that it creates new process called as svchost.exe which runs the windows services which are in form of DLLs. From here it can run on the system
It creates the following registry entry to ensure that its dropped copy is run every time Windows starts: HKCU\Software\Microsoft\Windows\CurrentVersion\Run
With data: "rundll32.exe <system folder>\<malware file name>.dll, <malware parameters>"
The Threat Expert does not show such kind of registry key activity but as mentioned above it uses the various Dlls to run the windows.
It can also load itself as a service that is launched when the netsvcs group is loaded by the system file svchost.exe.
It can also load itself as a fake service by registering itself under the following key: HKLM\SYSTEM\CurrentControlSet\Services
4.1.2 Network Activities
The worm can check the vulnerable systems with Network shares with weak passwords, which tries to infect all other PCs available on the network and as it been mentioned in the reports of Threat Expert.
As shown by the Threat Expert it first tries to drop a copy of itself in a target PC's ADMIN share using the credentials of the currently logged-on user.
If this method is unsuccessful, for example, the current user does not have the necessary rights, it instead obtains a list of user accounts on the target PC. It then tries to connect to the target PC using each user name and the weak passwords.
4.1.3 File System Activities
SENTRA I - 65 HKLM\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters
Disables TCP/IP tuning, stops and disables services as mentioned in the Threat Expert This worm stops several important services, like the following:
Windows Security Center Service (wscsvc) – notifies users of security settings (for example, Windows update, Firewall and Antivirus)
Windows Update Auto Update Service (wuauserv) Windows Defender (WinDefend)
Error Reporting Service (ersvc) – sends error reports to Microsoft to help improve user experience Windows Error Reporting Service (wersvc)
4.2 Anubis Analysis 4.2.1 Registry Activities
Anubis does not show or report how it copies or spreads and it also does not shows either it a worm or backdoor. Rather it just shows the registry activities starting from load time Dlls to run time Dlls and what kind of malware if being encrypted inside a single file. It shows in each step the process activities, the registry activities, network activities and the other activities.
First it copies itself to the load time and run time Dlls by opening the relevant run time and load time Dlls and after that it modifies deletes and creates the possible registry keys in the system
It creates the following registry entry to ensure that its dropped copy is run every time Windows starts: HKCU\Software\Microsoft\Windows\CurrentVersion\Run
With data: "rundll32.exe <system folder>\<malware file name>.dll, <malware parameters>"
The Anubis report shows that it invokes the dlls, after that it creates the new file in the windows folder and controls the devices needed by communicating with them.
It can also load itself as a fake service by registering itself under the following key: HKLM\SYSTEM\CurrentControlSet\Services
4.2.2 Network Activities
The worm can check the vulnerable systems with Network shares with weak passwords, which tries to infect all other PCs available on the network and Anubis reports does not shows what kind of weak passwords the worm uses or what kind of user accounts use to take control of the system, perhaps its shows the it queries the server through remotely after being executed on the system. The executable scans a range of IP addresses and also scans and identify the more potential vulnerable targets.
4.2.3 File System Activities
It also changes the system's TCP settings to let a large number of simultaneous connections, where 0x00FFFFFE is hexadecimal, this is the difference between Threat Expert and the Anubis, Anubis shows the following changes in its reports but cannot be seen in the Threat Expert reports. HKLM\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters.
Anubis reports also shows the memory being mapped by the malware which is shown as below, C:Windows\System32\regsvr32.dll
Through this dll it also creates the remotes threads to control remotely from other system or place. It also creates a lot of temporary internet files in the system windows folder to be able to control the internet and other network settings.
4.3 Real System Analysis 4.3.1 Registry Activities
As reported by the Threat Expert and Anubis the malware applied on the real system shows the similar behavior as Anubis, in the process monitor it shows the registry activities starting from load time Dlls to run time Dlls. It shows in each step the process activities, the registry activities, file system interaction.
First it copies itself to the load time and run time Dlls by opening the relevant run time and load time Dlls and after that it modifies deletes and creates the desired registry keys in the system.
I - 66 SENTRA
Real system behavior shows that it first invokes the dlls, after that it can also load itself as a fake service by registering itself under the following key:
HKLM\SYSTEM\CurrentControlSet\Services
4.3.2 Network Activities
The worm can check the vulnerable systems with Network shares with weak passwords, which tries to infect all other PCs available on the network and real system behavior also does not shows what kind of weak passwords the worm uses or what kind of user accounts use to take control of the system.
4.3.3 File System Activities
It also changes the system's TCP settings to let a large number of simultaneous connections, where 0x00FFFFFE is hexadecimal.
HKLM\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters
Real system results also shows the Dlls were successfully mapped to the malware location which is shown as below,
D:\Malware Analysis\binaries\cabinet.dll
It also creates a lot of temporary internet files in the system windows folder to be able to control the internet and other network settings..
Conclusion
The samples analyzed, proved to 95 worms and only two samples were found to be backdoor. This shows that malware authors still trust on worms to gain access and compromise systems because of self-replicating characteristics. As this research shows that the malware uses the registry keys to take control of the system. First it run itself on the system through DLLs and after that it reads, creates, modifies, deletes and edits those registry keys. Administrators and group of administrators have access rights to modify, read, write and delete these registry keys, so according to the results shown, the suggestion is to give the rights only to the administrator and group of administrators. Windows has some limited built-in protection designed to safeguard the registry. By default, normal users have only read permissions for most branches of the registry and are only able to modify registry keys that only affect their own account. Administrators should make sure that it should remain same for all users, by doing this it would limit the user to his account and it will not spread to other users. Restrict the executables by unknown users and only administrator can execute it when needed. This will also add the Restricted SID (security identifier) token to the registry access which will limit the program to read permissions and ensure that it does not alter the registry in any way. Running a program under these restrictions does more than just secure the registry. This will also block access to the folders, cookies and temporary internet files. This is useful because malware will be not able to create temporary internet files.
Limitations
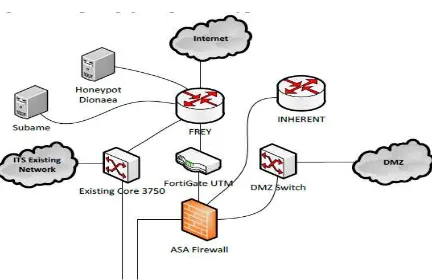
SENTRA I - 67 Figure 2: Network Topology of Honeypot ITS-Net
Further Research
As this research is done on Windows platform and using free online tools, further this research can be done on other platforms like Linux, Android and Apple Mac platforms and check behavior on these platforms by more reliable and registered tools available on the internet, more specifically on Android because almost all of the users are using services of internet on Android and smart phones which could be helpful to reveal the behavior on the latest Android cell phones.
Acknowledgment
I am deeply grateful to my advisor Sir Bekti Cahyo Hidayanto for the opportunity to work on this thesis. I would further like to thank my Supervisor Dr.Eng. Febriliyan Samopa, M.Kom for his countless suggestions and guidance during the thesis. It was a pleasure to do research in Institut of Teknologi Sepuluh Nopember Surabaya Indonesia.
Referensi
[1] Jeremy Paquette, A History of Viruses, March 2008,
http://www.securityfocus.com/infocus/1286.
[2] Ed Skoudis and Lenny Zeltser. Malware: Fighting Malicious Code. Prentice Hall, 2003. [3] Niels Provos, Panayiotis Mavrommatis, Moheeb Abu Rajab, and Fabian Monrose. All Your
iFRAMEs Point to Us. Google Technical Report, 2008.
[4] Brian Krebs, Washigton post: Hundreds of thousands of microsoft web servers hacked, April 2008,
http://blog.washingtonpost.com/securityfix/2008/04/hundreds_of_thousands_of_micro_1.html [5] A framework for behavior-based malware analysis in the cloud Lorenzo Martignoni, Roberto
Paleari , and Danilo Bruschi.
[6] An Effective Framework of Behavior Detection-Advanced Static Analysis for Malware Detection by Maya Louk, Hyotaek Lim and HoonJae Lee , Mohammed Atiquzzaman.
[7] Crowdroid: Behavior-Based Malware Detection System for Android by Iker Burguera and Urko Zurutuza and Simin Nadjm-Tehrani.
[8] Automatic Analysis of Malware Behavior using Machine Learning, Konrad Rieck, Philipp Trinius, Carsten Willems, and Thorsten Holz.
[9] Towards Automated Malware Behavioral Analysis and Profiling for Digital Forensic Investigation Purposes, Ahmed F.Shosha, Joshua I. James, Alan Hannaway, Chen-Ching Liu and Pavel Gladyshev.
[10] Ether Malware Analysis via Hardware Virtualization Extensions by Artem Dinaburg, Paul Royal, Monirul Sharif.
[11] AMAL: High-Fidelity, Behavior-based Automated Malware Analysis and Classification by Aziz Mohaisen.
I - 68 SENTRA
[13] Ontology-based Mobile Malware Behavioral Analysis by Hsiu-Sen Chiang, Woei-Jiunn Tsaur.
[14] Automated Classification and Analysis of Internet Malware by Michael Bailey, Jon Oberheide, Jon Andersen, Z. Morley Mao, Farnam Jahanian, and Jose Nazario .
[15] A Comparative Assessment of Malware Classification using Binary Texture Analysis and Dynamic Analysis by Lakshmanan Nataraj University of California, Santa Barbara, USA. [16] Malware Behavior Feature Extraction Based on Web Information Extraction by Binlin Cheng,
Jianming Fu and Ya Liu, Siyang Xiong.
[17] Automatic Behavior Bases Analysis and Classification System for Malware Detection Jaime Devesa, Igor Santos, Xabier Cantero, Yoseba K. Penya and Pablo G. Bringas.
[18] Malbehave: Classifying Malware by Observed Behavior by Connor Gilbert, Bryce Cronkite-Ratcliff, and Jason Franklin.
[19] Behavioral Analysis on IPv4 Malware on different platforms in IPv6 Network Environment by Zulkiflee M., Azirah S.A., Haniza N., Zakiah A., Shahrin S.
[20] BareBox: Efficient Malware Analysis on Bare-Metal. Dhilung Kirat, Giovanni Vigna, Christopher Kruegel University of California, Santa Barbara.
[21] Behavior-based Spyware Detection Engin Kirda and Christopher Kruegel Secure Systems Lab Technical University Vienna, Greg Banks, Giovanni Vigna, and Richard A. Kemmerer. [22] Malware behavior analysis Gérard Wagener Radu State Alexandre Dulaunoy.
[23] Behavior Classification based Self-learning Mobile Malware Detection by Dai-Fei Guo, Ai-Fen Sui, Yi-Jie Shi, Jian-Jun Hu, Guan-Zhou Lin and Tao Guo.