1
Data Authentication in Network Forensic Using MD5 and CRC32 Method
Irwan Sembiring
Faculty of Information Technology, Satya Wacana Christian University
Jl Diponegoro 52-60 Salatiga
Jazi Eko Istiyanto
Physics Department Faculty of Mathematics and Natural Sciences
Gadjah Mada University
Sekip Utara Bulaksumur, Yogyakarta
1.
INTRODUCTION
Evidently, we are now living in a digital epoch. Unlike the conventional media, images provide a vivid and natural communication media for human. One of them is CFAC (Computer Forensics, Autopsy and Coroner) or more often with computer forensic. (Barry A. J. Fisher, 2003).
Data authentication is very important, because of the high level of computer crime, particularly those related to counterfeiting of data, such as changing or deleting some of the contents of data. To be able to drag the perpetrators before the law, then the police should be able to prove it with the tools of evidence, and expertise required obtain digital evidence. Digital evidence is fragile evidence. Contamination of digital evidence is apt to occur, either accidentally or intentionally. Small errors in the handling of digital evidence can create digital exhibits changes. If the data changes it can be said is not the original data. The application is expected to assist the process of detecting the authenticity of the data. Detection process is referred to the authenticity here is to detect whether the data provided in accordance with the data obtained from the search.[2] One way that can be used to resolve the issue is the hash value of data that are considered problematic, so the data can be compared to the truth. Data are still easy to manipulate, but by using two hash at once to manipulate the data very difficult.
2.CYCLIC REDUNDANCY CHECK (CRC)
CRCs are specifically designed to protect against common types of errors on communication channels, where they can provide quick and reasonable assurance of the integrity of messages delivered. However, they are not suitable for protecting against intentional alteration of data. Firstly, as there is no authentication, an attacker can edit a message and recalculate the CRC herself, without the substitution being detected.
Data authenticity detection system built using two methods at once. The method used is the method of MD5 and CRC32 method. This is intended to minimize the data error. If only one method, then the checksum value in common place or manipulate the data are still likely to occur, but by using two methods and the errors or to manipulate the data is very small. This causes the data that has to be more reliable if it has a value of MD5 and CRC32 values the same.
2
A cyclic redundancy check (CRC) is a non-secure hash function designed to detect accidental changes to raw computer data. Its computation resembles a long division operation in which the quotient is discarded and the remainder becomes the result, with the important distinction that the arithmetic used is the carry-less arithmetic of a finite field. The length of the remainder is always less than or equal to the length of the divisor, which therefore determines how long the result can be. Cyclic redundancy checks have favorable properties in that they are specifically suited for detecting burst errors. CRCs are easily implemented in hardware, and are commonly used in digital networks and storage devices such as hard disk drives. Even parity is a special case of a cyclic redundancy check, where the single-bit CRC is generated by the polynomial x+1. Cyclic Redundancy Check (CRC) is based on division in the ring of polynomials over the finite field GF(2) (the integers modulo 2), that is, the set of polynomials where each coefficient is either zero or one, and arithmetic operations wrap around (due to the nature of binary arithmetic). Any string of bits can be interpreted as the coefficients of a message polynomial of this sort, and to find the CRC, we multiply the message polynomial by xn and then find the remainder when dividing by the degree-n generator polynomial. The coefficients of the remainder polynomial are the bits of the CRC. In general form[1]:
……
..[1]
Here M(x) is the original message polynomial and G(x) is the degree-n generator polynomial. The bits of are the original message with n zeroes added at the end. The CRC 'checksum' is formed by the coefficients of the remainder polynomial R(x) whose degree is strictly less than n. The quotient polynomial Q(x) is of no interest. In communication, the sender attaches the n bits of R after the original message bits of M, sending out
….[
2]
The receiver, knowing G(x) and therefore n, separates M from R and repeats the calculation, verifying that the received and computed R are equal. If they are, then the receiver assumes the received message bits are correct. In practice CRC calculations resemble long division in binary, except that the subtractions involved do not borrow from more significant digits, and thus become exclusive or operations. A CRC is a checksum in a strict mathematical sense, as it can be expressed as the weighted modulo-2 sum of per-bit syndromes, but that word is generally reserved more specifically for sums computed using larger moduli, such as 10, 256, or 65535. CRCs can also be used as part of error-correcting codes, which allow not only the detection of transmission errors, but the reconstruction of the correct message. These codes are based on closely related mathematical principles.
3.
NETWORK FORENSIC
The definition of network forensics is the use of scientifically proven techniques to collect, fuse, identify, examine, correlate, analyze, and document digital evidence from multiple, actively processing and transmitting digital sources for the purpose of uncovering facts related tothe planned intent, or measured success of unauthorized activities meant to disrupt, corrupt, and or compromise system components as well as providing information to assistin response to or recovery from these activities. Network forensic process life cycle is described (Martin, 2006):
figure2. Network forensic life cycle forentech (2005)
a.
Prepare
Case briefings, engagement terms, interrogatories, spoliation prevention,
disclosure and discovery planning, discovery requests
b.
Record
Drive imaging, indexing, profiling, search plans, cost estimates, risk analysis
c.
Investigate
Triage images, data recovery, keyword searches hidden data review,
3
d.
Report
Oral vs. written, relevant document production, search statistic
e.
Reports
chain of custody reporting, case log reporting
f.
Testify
Testimony preparation, presentation preparation, testimony
4.
MD5 ALGORITHM
Figure3. Message Digest MD5 Algorithm
The procedure that yields the checksum from the data is called a checksum function or checksum algorithm. A good checksum algorithm will yield a different result with high probability when the data is accidentally corrupted; if the checksums match, the data is very likely to be free of accidental errors. MD5 processes a variable-length message into a fixed-length output of 128 bits. The input message is broken up into chunks of 512-bit blocks (sixteen 32-bit little endian integers); the message is padded so that its length is divisible by 512. The padding works as follows: first a single bit, 1, is appended to the end of the message. This is followed by as many zeros as which are required to bring the length of the message up to 64 bits less than a multiple of 512. The remaining bits are filled up with a 64-bit integer representing the length of the original message, in bits. The main MD5 algorithm operates on a 128-bit state, divided into four 32-bit words, denoted
A, B, C and D. These are initialized to certain fixed constants. The main algorithm then operates on each 512-bit message block in turn, each block modifying the state. The processing of a message block consists of four similar stages, termed rounds; each round is composed of 16 similar operations based on a non-linear function
F, modular addition, and left rotation. Figure 1 illustrates one operation within a round. There are four possible functions F; a different one is used in each round:
denote the XOR, AND, OR and NOT operations respectively
The message digest is computed using the final padded message. The computation uses two buffers, each consisting of five 32-bit words, and a sequence of eighty 32-bit words. The words of the first 5-word buffer are labeled A,B,C,D,E. The words of the second 5-word buffer are labeled H0, H1, H2, H3, H4. The words of the
80-word sequence are labeled W0, W1,..., W79. A single word buffer TEMP is also employed.
To generate the message digest, the 16-word blocks M1, M2,..., Mn defined in Section 4 are processed in order.
The processing of each Mi involves 80 steps. Before processing any blocks, the {Hi} are initialized as follows:in
hex,
H0 = 67452301
H1 = EFCDAB89
H2 = 98BADCFE
H3 = 10325476
H4 = C3D2E1F0.
4
a. Divide Mi into 16 words W0, W1, ... , W15, where W0 is the left-most word.
b. For t = 16 to 79 let Wt = S1(Wt-3 XOR Wt-8 XOR Wt- 14 XOR Wt-16).
c. Let A = H0, B = H1, C = H2, D = H3, E = H4.
d. For t = 0 to 79 do
TEMP = S5(A) + ft(B,C,D) + E + Wt + Kt;
E = D; D = C; C = S30(B); B = A; A = TEMP;
e. Let H0 = H0 + A, H1 = H1 + B, H2 = H2 + C, H3 = H3 + D, H4 = H4 + E.
After processing Mn, the message digest is the 160-bit string represented by the 5 words
H0 H1 H2 H3 H4.
5.
SYSTEM DESIGN
At the design stage of this system will be designed modules and related processes in accordance with parts and functions. Design systems to existing business processes in this system in detecting the origin of application data through the methods described DFD (Data Flow Diagram)
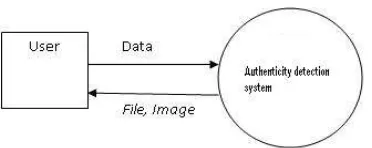
Figure 4. DFD Level 0
Figure 4 illustrates the level 0 DFD of Data Authenticity detection system. 0-level DFD shows the main processes of the origin of the data detection system is that the user provides the data to be checked and the system will process it and return the processed results obtained in the form of files, images from the data.
figure 5. DFD level 1 Authenticity Detection System
5
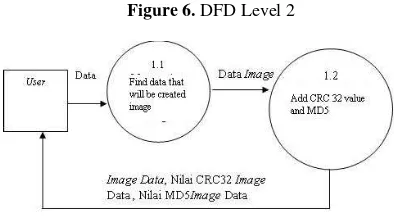
Figure 6. DFD Level 2
Figure 6 shows the DFD level 2 for the process of making images. Users specify the data to be created image. Once the image data, image data is added value of the MD5 and CRC32 values. Next image data, image data CRC32 value, and the MD5 value of the image data stored in storage media.
Figure 7. DFD Level 2 Normal checking process file
Figure 7 shows the level 2 DFD for a normal review process files. Users find the required files to normal. After normal files found, do the storage process. Before stored in the storage medium, normal file and CRC32 value added MD5 value.
Figure 8. DFD Level 2 Checking Process Hidden Files
Figure 8 shows the DFD level 2 to check the hidden files. Users looking for hidden files
required. After hidden files found, do the storage process. Before stored in storage media,
hidden files are added to the value of CRC32 and MD5 value.
Figure 9. DFD Level 2 Removed Files Checking
6
Figure 10. Flowchart Authenticity Detection System Data
Flowchart in Figure 10 can be explained as follows: Input data used are to be reviewed. The most important part of this examination is the hard disk. The disk is the main storage medium in a computer system. All the data must be stored in the hard disk. The next process is making hard disk image to be examined. The detection system of the authenticity of data, the data should not change any one bit. The virtual disk from the image was created earlier, so all of the search activity data derived from image The next process to check the files contained in the image. These files will later serve as proof. The files you are looking for is a file that have extension *. doc, *. docx, *. xls, *. xlsx and. These files are selected as the file extension type is the most frequently used in document a file. At the end of the inspection report obtained the normal form of files, hidden files, and delete files, MD5 files, and file CRC32.
6.
INTERFACE DESIGN
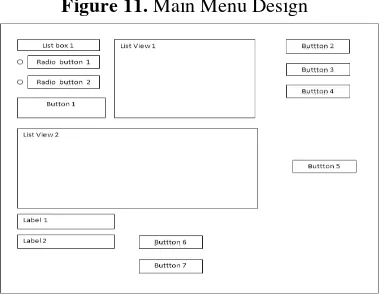
Basically, to build a graphical interface in Visual Basic.Net 2008 is very easy. This is because Visual Basic.Net 2008 in the process of building the interface using GUIDE (GUI Designer). In GUIDE, the development of an interactive interface easier and more practical to do. Components GUI component form-buttons, check boxes, labels, list view, text boxes, picture boxes, and panels. Each component in the GUI is associated with callbacks. The execution is driven by callbacks enter the user, such as mouse clicks, button presses, or shift the cursor. The main interface of this application was built using GUIDE. Figure 11 is a picture of the main interface design in the computer system detecting the authenticity of the data.
7
The process was conducted to compare files by looking at the identity of the file. As the identity of the MD5 checksum, file creation date, last modification date of the file. Fifth Button, Save Button, Button is used to store the results of the scan. So the information obtained from the scanning process is stored in the form of report. The sixth button, browse button, Button is used to select the location where the file will be placed. Seventh Button, Button copy is used for copying the selected files. List box used to view 1 drives to be checked. List view1 used to see the folders of the drive that will be checked. List view2 used to scan the checks. Label 1 is used to indicate the name of the file is selected in the process of copying. Label 2 is used to indicate where the location of the file will be copied out.
7.
RESULT AND DISCCUSION
Figures 12. Authenticity form Detection System Data
This early form works to make sure the user will create a new folder for grouping data. Two radio buttons are used to select whether the user will create a new folder or use an existing folder. If you want to create a new folder, then the user can select the radio button on the Create a New Folder, and may continue to do click on the OK button. To exit the application can do so by doing the cancel
.
Figure13. Applications for Creating and Using Image
8
Figure 14.Form ScanFile
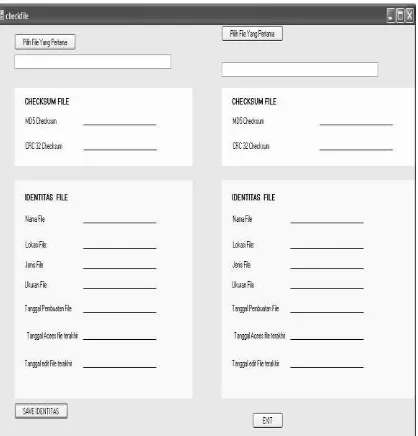
Figure 14 is an image data search form. Because of this form of the data obtained will be taken. By using the radio buttons, user can choose whether the user searches for normal files or find files hidden. Search result is displayed directly as soon as users click Scan Selected Folder button. Explore button is used to view the files directly. So this key functions such as using My Computer on the Windows operating system. Scan button delete files / recovery, this button has a utility to perform a search process that deleted files and restore deleted files. Key compare two files contained in Figure 11 is used to call a form of comparison of two files. This form aims to compare whether the same file or not. The benchmarking process uses the MD5 checksum and CRC32 checksum. As Figure 4.4 is a form of comparison of two files. Browse button is used to select the location where the file is selected to copy. The copy button functions to copy the files that have been selected earlier. Scans save button is used to store log files scan results that have been made.
Figure 15. Comparison Form Two Files
9
8.
RESEARCH RESULT
Table1.Comparative results between MD5 before data recovery in data recovery
Table2. Comparative results between CRC32 before data recovery in data recovery
From the above comparison results can be seen that the checking process of hashing the data to maintain the authenticity of the data in conducting a forensic network stage process of data recovery or drive imaging proved that there was no change still the authentic evidence.
9.
COCLUSION
The conclusion drawn from making the application of the correct data detection system is of the correct application detection system uses two methods of data checksums, CRC32 checksum method and MD5 checksum method. By comparing the value of CRC32 and MD5 values directly to the authenticity of data provided with the data obtained can be known directly. So that authentication data in the process of forensic network can be maintained.
10. REFERENCES
1. Barry A. J. Fisher, 2003, Basic Steps in Forensic Analysis of Unix Systems, CRC Press. 2. Stigge, Martin, 2006. Reversing CRC, theory and practice
3. Forentech,2005, LLC, Forensic Lifecycle
4. Arasteh Ali, Debbabi Mourad, Sakha Assaad and Saleh Mohamed. “Analyzing multiple logs for forensic
evidence”, In the Digital Investigation Journal, Volume 4, Number 1, September 2007, pp. 82-91