In this rapidly changing and volatile world, the expectations required of those in the intelligence discipline are high – knowledge of the hidden and foreknowledge of the unpredictable. Thanks to Jeff Malone of the Australian Department of Defense for his thorough review of the manuscript; I incorporated virtually every one of his excellent comments to make this book more accurate to the subject and more readable to the intelligence user.
Knowledge Management and Intelligence
Knowledge in a Changing World
Upon return, the intelligence observations were delivered and the data analysis and report synthesis phase began as leaders considered the implications of the data (Numbers 13:26-33). Consider some of the key assumptions about the importance of knowledge in this information age that bring the importance of intelligence to the forefront.
Categories of Intelligence
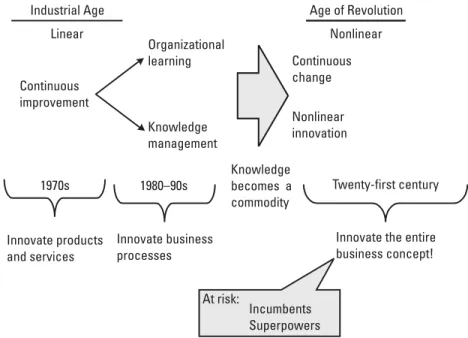
Business concept innovation is the only way for newcomers to succeed in the face of huge resource disadvantages, and the only way for incumbents to renew their lease on success [13]. Analyzes that explain current behavior and states (What is the competitor's research and development process? What is the status of development?);
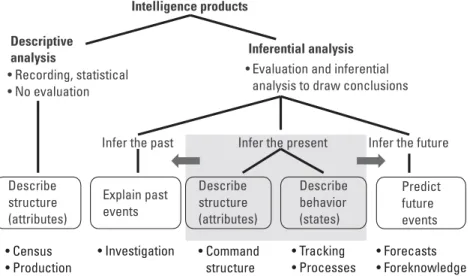
The Intelligence Disciplines and Applications
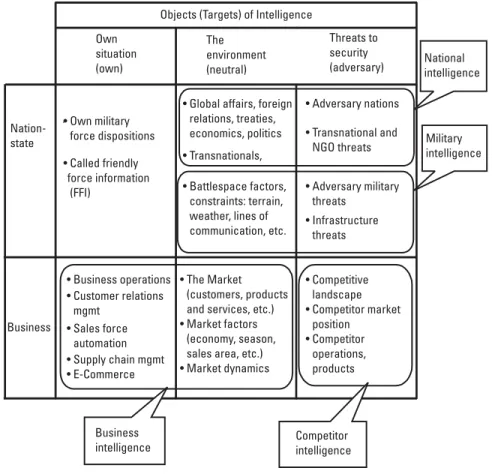
These distinctions are based on the scope of the objects (targets or subjects) of intelligence addressed by each of the four disciplines (Figure 1.3). National intelligence agencies focus on understanding the global environment (political, economic, natural environmental, scientific and technological fields) and the key participants (foreign nation states and their political organizations, non-governmental organizations [NGOs] and influential individuals). .
The Intelligence Enterprise
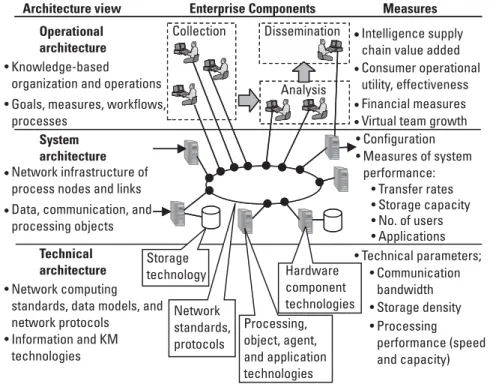
The taxonomy of business intelligence terminology (Table 1.3) distinguishes business intelligence from competitive intelligence according to the objects of their study. The operational layer is the highest (most abstract) description of the concept of operations (CONOPS), human collaboration and knowledge organization disciplines.
The State of the Art and the State of the Intelligence Tradecraft The subject of intelligence analysis remained largely classified through the
Competitive Intelligence Magazine—This is a CI resource for general application-related articles about CI, published bi-monthly by John Wiley. Journal of Knowledge Management—This is a quarterly academic journal on strategies, tools, techniques and technologies, published by Emerald (UK).
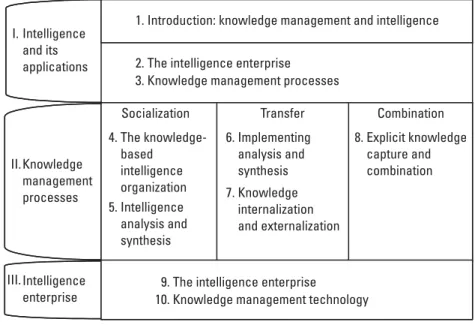
The Organization of This Book
Endnotes
8] From “Presidential Reflections on US Intelligence,” CIA Center for the Study of Intelligence, accessed online November 2001 at http://www.odci.gov/csi/monograph/firstln/. Garstka, "Network-Centric Warfare: Its Origin and Future," Naval Institute Proceedings, January 1998, accessed online November 2001 at http://www.usni.org/Proceedings/Articles98/PROcebrowski.htm.
Selected Bibliography
Johnson, L., Bombs, Bugs, Drugs, and Thugs: Intelligence and America's Quest for Security, New York: New York University Press, 2000. Gilad, B. and T. Gilad, The Business Intelligence System - A New Tool for Competitive Advantage, New York: American Management Association, 1988.
The Intelligence Enterprise
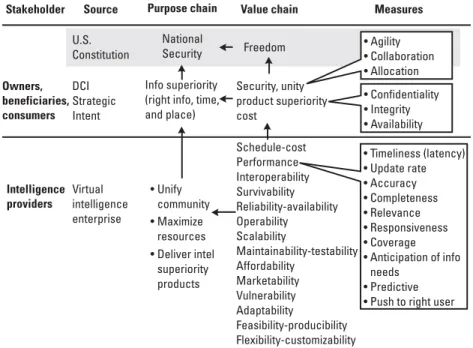
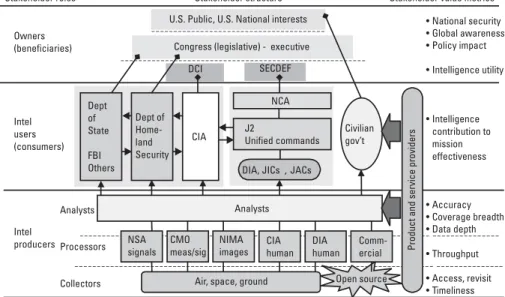
The Stakeholders of Nation-State Intelligence
Value chain – a chain of values (goals) that measure the achievement of the company's purpose. Chain of Intent – Business objectives require knowledge of internal operations and the market (BI objectives) and knowledge of competitors (CI).
Intelligence Processes and Products
Processing. The collected data is processed (eg machine translation, foreign language translation or decryption), indexed and organized in an information base. All sources analysis-synthesis and production. The organized information base is processed using estimation and inference (reasoning) techniques that combine all sources of data in an attempt to answer the requester's questions.
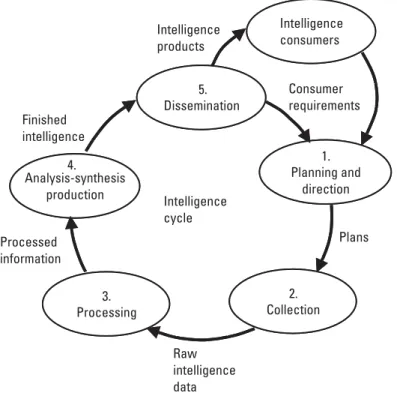
Intelligence Collection Sources and Methods
Revisit - the frequency with which a target of interest can be revisited to understand or model (trace) dynamic behavior;. Stealth - the degree of secrecy with which information is collected and the degree of intrusion required.
Collection and Process Planning
Timeliness - the time between event data collection and the delivery of a tactical targeting cue, operational alerts and alerts, or a formal strategic report; The collected data is analyzed for the existence of evidence and the synchronization of events to verify process cycles.
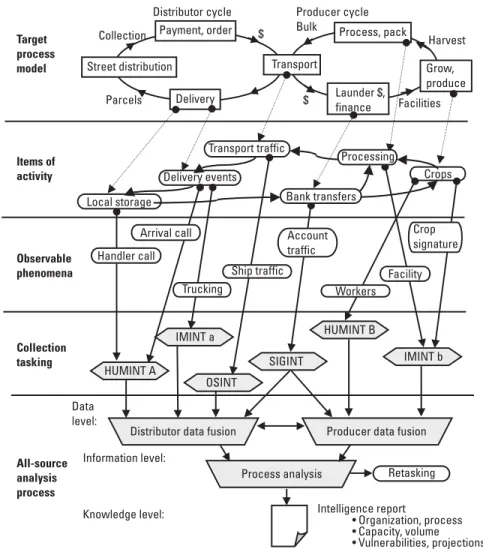
KM in the Intelligence Process
The indexing process applies standard subjects and relationships, maintained in a lexicon and thesaurus that is extracted from the analysis database. Data visualization tools present synthetic views of data and information to the analyst to allow patterns to be examined and discovered.
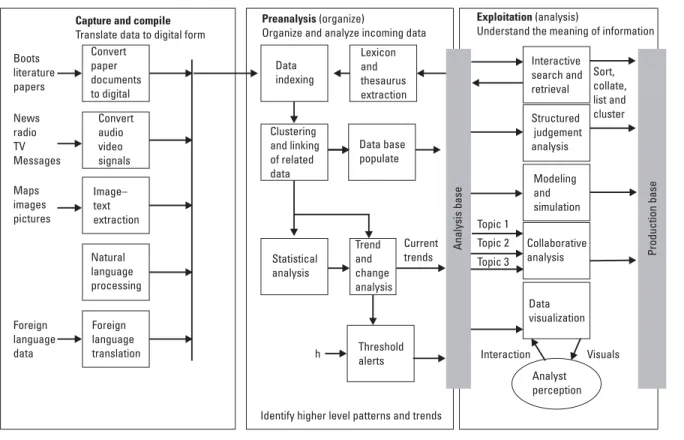
Intelligence Process Assessments and Reengineering
The expertise of individual analysts and the analyst community must be maintained at the highest possible level. Improve strategic assessments. The United States produces National Intelligence Estimates (NIEs), which provide credible statements and make judgments about the likely course of events in foreign countries and their implications for the United States.
The Future of Intelligence
Organizations need to move beyond the primary focus on classified sources and develop methods and resources to embrace and integrate open sources into analytics. TheStrategy claims: “The United States will take all necessary measures to avoid being surprised by another terrorist attack.
Knowledge Management Processes
Knowledge and Its Management
In the first chapter, we introduced the growing importance of knowledge as a central resource for competitiveness in both the nation-state and business. Note that the first four strategy areas correspond to the four knowledge contributions discussed in the previous paragraph.
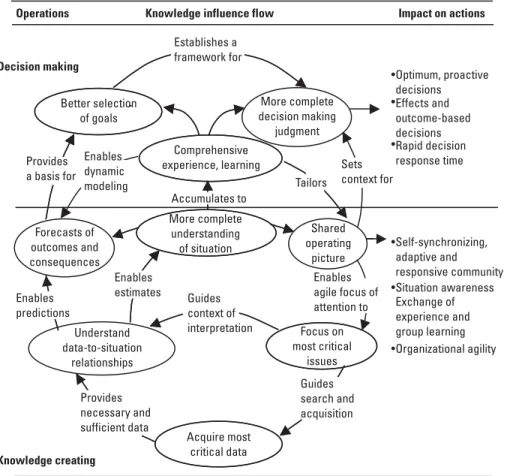
Tacit and Explicit Knowledge
The most common conception of knowledge is as an object: the accumulation of things observed, discovered, or learned. Tacit to explicit externalization. The articulation and explicit codification of tacit knowledge moves it from the internal to the external.
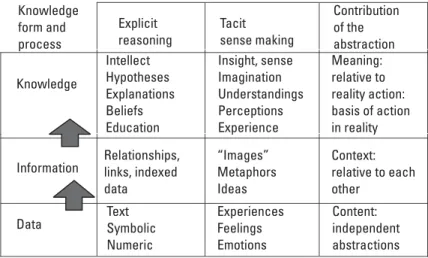
An Intelligence Use Case Spiral
This first spiral of knowledge creation (Figure 3.6) takes place within the first few days of team formation. As the evidence and explanation models are developed on the portal, the team members discuss (and argue) about the details, internally struggling with the acceptance or rejection of the validity of the various hypotheses.
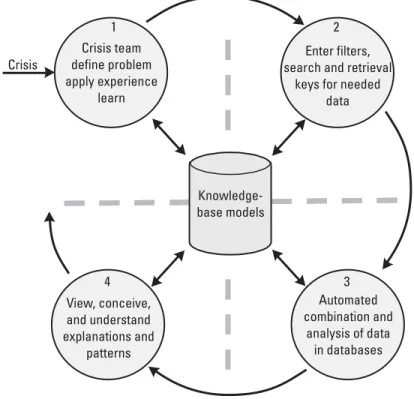
Taxonomy of KM
Note that these three areas correspond to three basic descriptive views of the enterprise which will subsequently be introduced in Chapter 9. Enterprise architects integrate people, processes and IT to implement the KM business model.
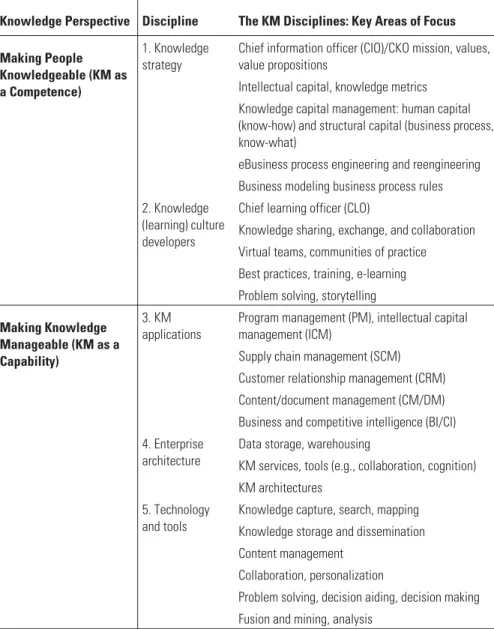
Intelligence As Capital
In this example, the difference in the market value ($100 million) of the business and the tangible assets of the business is $50 million. Human capital. The people, individually and in virtual organizations, comprise the human capital of the organization.
Intelligence Business Strategy and Models
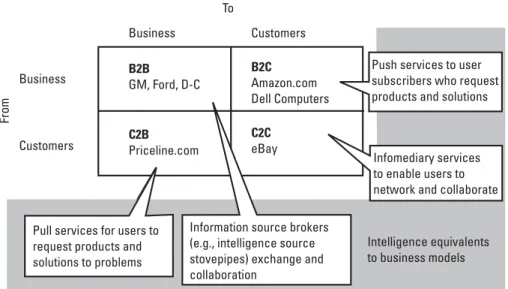
This corresponds to process models that enable efficient electronic transactions between providers of intelligence sources (eg, IMINT, SIGINT, or other stovepipes), which allow cross-source cueing, coordinated multi-source collection, data fusion, and mining. . Companies such as Priceline.com (travel services) and Lendingtree.com (financial services) use the C2B model to enable customers to secure quick quotes and secure immediate purchases on relatively volatile products (remaining airline seats and changing loan rates, respectively).
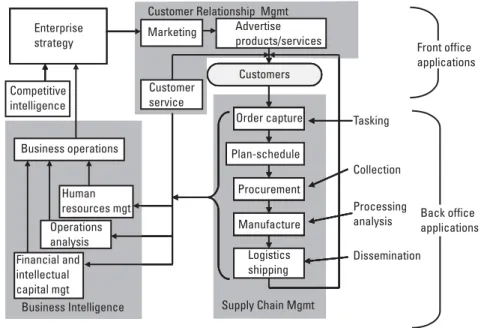
Intelligence Enterprise Architecture and Applications
Consumer transactions - specific actions that occur between the enterprise and consumers of intelligence, including urgent requests, subscriptions (standing orders) for information, sending additional and final reports, requests for clarifications and issuing alerts. Note that the supply chain in Figure 3.11 distinguishes the assignment, collection, processing, exploitation, and distribution (TCPED) phases associated with the high-volume national intelligence supply chain. The TCPED intelligence model is compared with other models in section 6.2.).
Summary
Technology. Chapters 8 and 9 then describe the information technologies (computing processes, processing nodes, and interconnecting network technologies) that make up the implementation of enterprise intelligence architecture. 10] Descartes published his Discourse on Method in 1637 and described his four-step method of solving problems of analysis and synthesis in "Part II - The Principal Rules of Method".
The Knowledge-Based Intelligence Organization
Virtues and Disciplines of the Knowledge-Based Organization At the core of an agile knowledge-based intelligence organization is the ability to
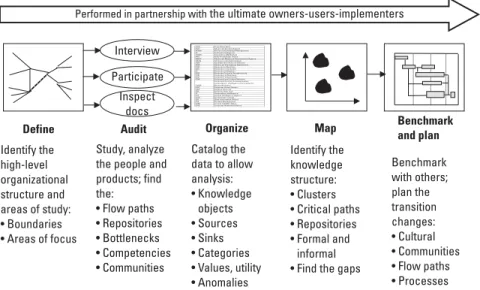
Benchmarking gathers tacit knowledge – knowledge and experience, judgments and factors – that explicit knowledge often misses [11]. Virtual collaboration. Emphasis in this field is the use of technology to create connectivity between and among communities of practice.
Organizational Learning
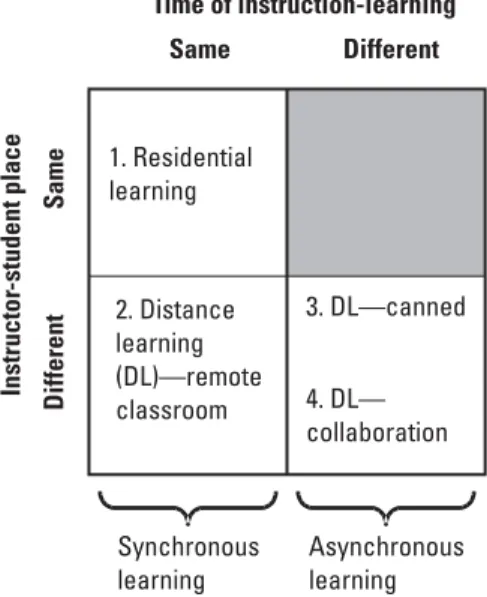
A learning organization builds shared mental models by sharing tacit knowledge in the storytelling process and the planning process. The advantages of traditional RL include face-to-face interaction between student and instructor to share tacit knowledge as the instructor adapts to the student's learning style.
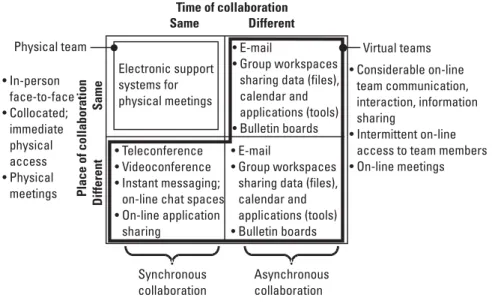
Organizational Collaboration
On the collecting side, we form close partnerships with our counterparts in the clandestine service - the Directorate of Operations - and with many other intelligence collectors. Analysis cell for all sources. The All-Source Analysis Cell, which can be a virtual team spread across different organizations, has the responsibility of producing the intelligence product and certifying its accuracy.
Organizational Problem Solving
Searching for and matching evidence against previously known hypotheses (patterns). The discovery reasoning approach is deductive in nature, testing evidence against known hypotheses.). Ellis (CINC USN Europe) went on to note that information saturation adds to the "fog of war" and that the demand for information will always outstrip the ability to provide it, but posed the question: ".how much is enough?".
Tradecraft: The Best Practices of Intelligence
Representative of the trade analytical area Types of best practices cataloged Addressing national interests Methods of looking at the analytical problem from the policy maker. These best practices summarize the characteristics of the best analyses, providing supporting examples where appropriate.
Summary
18] Barth, S., "The Organic Approach to Organization: A Conversation with KM Practitioner David Snowdon," Knowledge Management, Oct. 2000, p. By mindset, we refer to "the distillation of the intelligence analyst's cumulative factual and conceptual knowledge into a framework for making estimates on a complex subject."
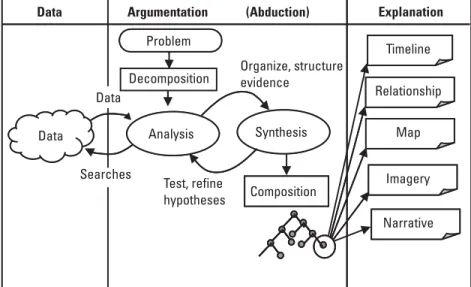
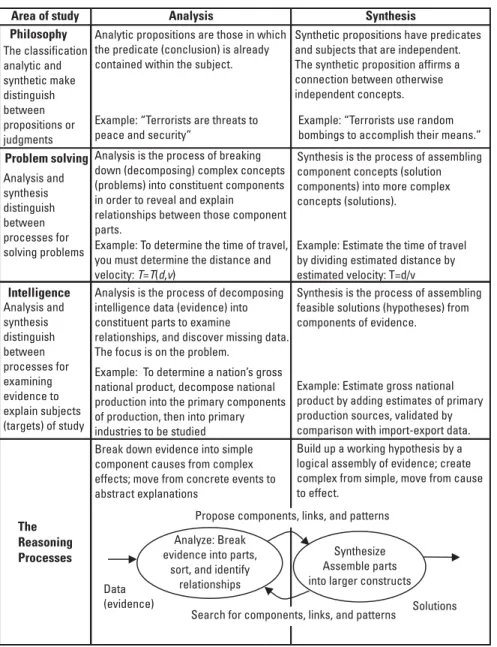
Principles of Intelligence Analysis and Synthesis
The Basis of Analysis and Synthesis
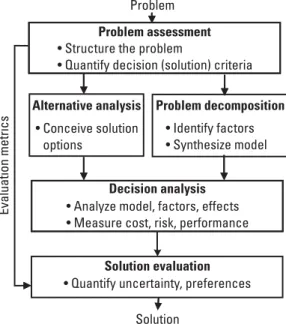
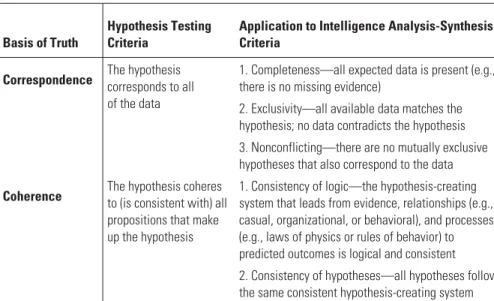
Collection planning (analysis). The analyst examines the pre-existing evidence in intelligence and open-source reports that prompted policymakers to call for the investigation. These propositions are based on the most fundamental logical principles necessary for reasoning (e.g. the identity principle: "A is A"; the non-contradiction principle: "x cannot be A and not A at the same time"; the principle of the excluded middle: "either is or is not") and their application to create propositions of truth through deductive logic.
The Reasoning Processes
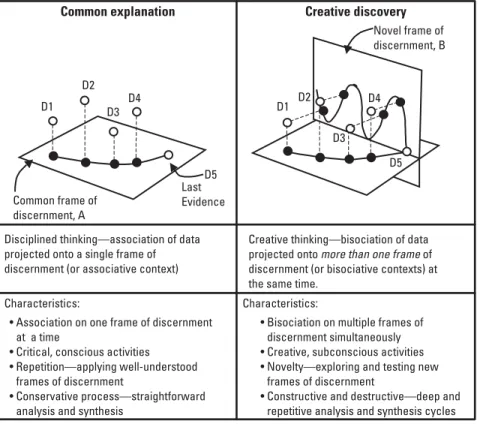
In this method, analysts extend the observations of a limited number of targets (eg, observations of money laundering tactics of several drug rings within a drug cartel) to a larger target population (eg, the entire drug cartel). In this method, an analyst can use multiple observations of behavior (eg, the repeated surveillance behavior of a foreign intelligence entity) to create a general detection template to be used to detect future surveillance activities by that or other such entities.
The Integrated Reasoning Process
Discovers new patterns in evidence – patterns of circumstances or behaviors previously unknown (learning). The path of induction considers the entire body of evidence to find general statements (hypotheses) about the evidence.
Analysis and Synthesis As a Modeling Process
We could maintain three examples of the model (legitimate company, faltering legitimate company, and illicit front organization), each of which is a competing explanation (or hypothesis) of the incomplete evidence. The shape of the hypothesis model is a function of the problem being addressed, and the model can have many views or explanatory perspectives.