This is to confirm that the project titled, Attacks on Geographic Routing Protocol for Wireless Sensor Network posted by Rahul G. Most of the routing protocols proposed for ad-hoc and sensor networks are not designed with security as a goal. Routing protocols for wireless sensor networks are classified into three types depending on their network structure as flat routing protocols, hierarchical routing protocol, and geographic routing protocols.
Wireless Sensor Networks (WSN) is an interconnection of a large number of nodes deployed for monitoring the environment or system by means of measuring environmental parameters such as temperature, pressure, humidity. Some of the military applications of sensor networks are battlefield surveillance and detection of attack by weapons of mass destruction. Sensor networks can also be used effectively for forest fire detection, flood detection and monitoring of animal habitats. Sensor networks are usually deployed in the conditions where continuous human intervention is not possible.
Sensor networks should also be adaptable to changing connectivity due to node failure or the introduction of new nodes. Most of the routing protocols proposed for ad hoc networks and sensor networks are not designed with security in mind.
INTRODUCTION 11 conservation of nodes can be achieved by introducing and using multiple states of
Challenges in Routing for Wireless Sensor Net- worksworks
INTRODUCTION 12 to technical issues because sensing rate is different for different sensors
Applications of Wireless Sensor Networks
INTRODUCTION 13
Motivation and Challenges
Problem Statement
Background
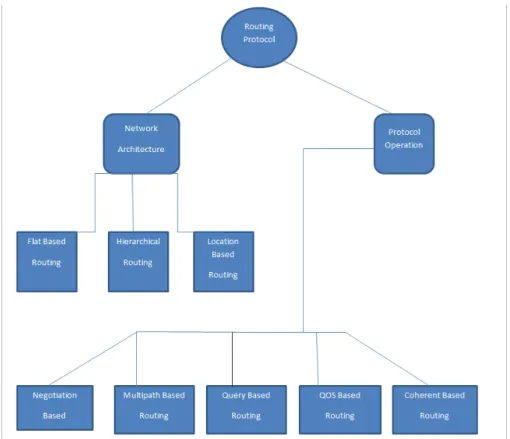
Classification of Routing Protocols
- Behavioural classification of Routing Protocols
- Network structure based Routing Protocols
BACKGROUND 15
BACKGROUND 16 5. Gradient Based Routing(GBR)[27]
COUGAR[28]
BACKGROUND 17 7. Virtual Grid Architecture routing (VGA)[21]
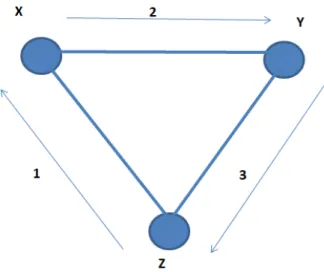
Thus, GPSR uses a combination of greedy and perimeter tracking techniques to route the data to the destination. Greedy Perimeter Stateless Routing (GPSR)[1] is a geolocation-based routing protocol that uses the geographic positions of routers and packet destinations to make packet forwarding decisions. Shortest path algorithms are state proportional to the number of hops away from destinations whereas, GPSR is a stateless protocol as it does not require the overall network topology to be maintained but only depends on the local topology maintained by each node. Each node in a sensor network keeps track of the location of its immediate neighbors using a simple signaling algorithm.
Periodically each node broadcasts a beacon to its immediate neighbors at the broadcast MAC address containing its identifier and position. The transmission interval between beacons is uniformly distributed in the interval [0.5B, 1.5B] to keep the most current neighbor positions. While not receiving any beacons from a given neighbor for a longer period of time, which is greater than the timeout interval T, the GPSR router assumes that the neighbor has failed or gone out of range and deletes that neighbor from the neighbor table. his. In GPSR each node needs to propagate topology information to all those nodes that are within a single hop distance.
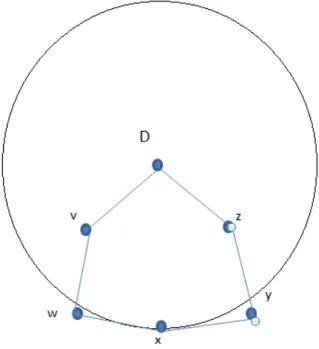
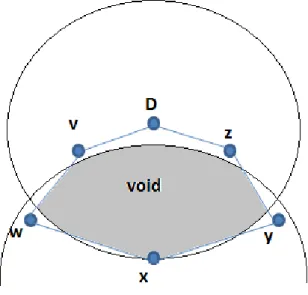
Greedy forwarding is used throughout the network whenever possible, but in those areas where greedy forwarding cannot route the packet to its destination, the packet is temporarily transmitted in perimeter mode.
GPSR AND FEASIBLE ATTACKS 20
Greedy Forwarding
GPSR AND FEASIBLE ATTACKS 21
Perimeter Mode
GPSR AND FEASIBLE ATTACKS 22
Right Hand Rule
GPSR AND FEASIBLE ATTACKS 23
GPSR AND FEASIBLE ATTACKS The candidate's next flank is ignored and the next flank, counterclockwise, is taken.
GPSR AND FEASIBLE ATTACKS 24 candidate next edge is ignored, and the next edge in counter-clockwise order is taken,
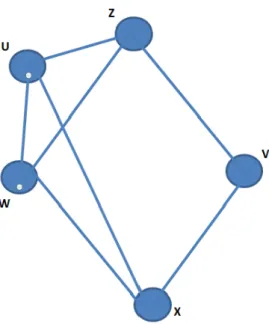
Planarized Graphs
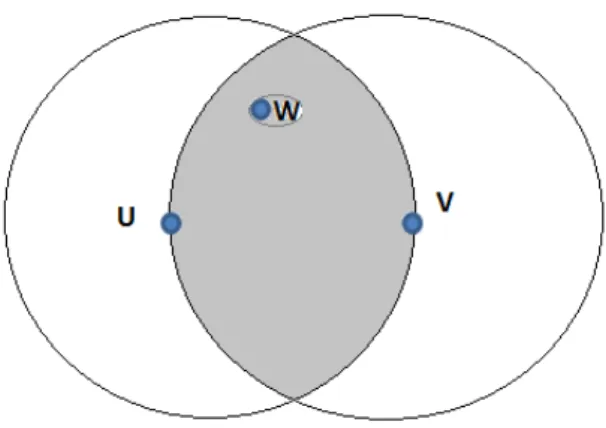
- Relative Neighbourhood Graph(RNG)
- Gabriel Graph(GG)
GPSR AND FEASIBLE ATTACKS 25
GPSR AND FEASIBLE ATTACKS 26 the RNG. Figure 3.10 shows a full unit graph corresponding to 200 nodes randomly
Attacks on Geographical Routing Protocols
GPSR AND FEASIBLE ATTACKS 27
Selective Forwarding Attack
Sybil Attack
GPSR AND FEASIBLE ATTACKS 28 adversary node in a network can initiate the Sybil attack by sending false location
Spoofed or Bogus Routing
GPSR AND FEASIBLE ATTACKS 29 the routing sources or it can produce false error messages .Spoofed or bogus routing
Defences against Sybil attacks
- Radio Resource Testing
To protect against the Sybil attack, we would like to prove that each node identity is the only identity presented by the corresponding physical node. The first type is direct authentication, in which a node directly tests whether another node's identity is valid. The second type is indirect authentication, in which nodes that have already been verified are allowed to vouch for or reject other nodes[7].
If the neighbor assigned to that channel is legitimate, it should hear the message. In that case, the probability of choosing to listen to a channel that is not being transmitted on, and thus detecting a Sybil node, is ns. If the test is repeated for r rounds, then the chance that no Sybil nodes are detected is (n−sn )r. Figure 5.1 shows the probability of not detecting the presence of some Sybil nodes using this method.
LITERATURE SURVEY 31
Random key pre distribution
LITERATURE SURVEY 32
Defence against Selective forwarding attack
- Multi-Data flow Topologies scheme
LITERATURE SURVEY 33 Locating the Faulty Sensor nodes
Simulation of GPSR
The event occurred near node 15, which acts as a source, and the event should be reported to node 9, which acts as a base station.
SIMULATION RESULTS 35
SIMULATION RESULTS 36 intervals. A beacon packet consists of the location of the node sending the beacon as
SIMULATION RESULTS 37
SIMULATION RESULTS 38
Selective forwarding attack over GPSR
SIMULATION RESULTS 39
SIMULATION RESULTS 40
SIMULATION RESULTS 41
SIMULATION RESULTS 42
Sybil attack over GPSR
SIMULATION RESULTS 43
SIMULATION RESULTS 44 total changed number of beacons sent and beacons received leads to small variations
SIMULATION RESULTS 45
SIMULATION RESULTS 46 The number of packet dropped by each node is zero as it was in case of GPSR
Conclusion
GPSR was simulated for wireless sensor network and it was found that packets switch from greedy mode to perimeter mode to encounter a gap in the routing path. The selective forwarding attack was simulated over GPSR and it was found that the packets dropped for the malicious node are increased compared to that in GPSR. The Sybil attack was implemented and it was found that malicious nodes advertising multiple geographic locations send more beacons to their neighbors as compared to GPSR, it tends to alter packet routes and waste network resources.
Future Work
In MobiCom '00: Proceedings of the 6th Annual International Conference on Mobile Computing and Networking, pages 243–254, New York, NY, USA, 2000. In Proceedings of the Seventh Annual ACM/IEEE International Conference on Mobile Computing and Networking, pages . In Proceedings of the 7th Annual International Conference on Mobile Computing and Networking, MobiCom ’01, pages 70–84, New York, NY, USA, 2001.
InProceedings of the 8th Annual International Conference on Mobile Computing and Networking, MobiCom '02, pages 148–159, New York, NY, USA, 2002. In Proceedings of the 6th Annual International Conference on Mobile Computing and Networking, MobiCom '00, pages 56–67, New York, NY, USA, 2000. InProceedings of the First ACM International Workshop on Wireless Sensor Networks and Applications, WSNA '02, pages 22–31, New York, NY, USA, 2002.