They analyzed the recognition performances of the image layers in the Gaussian scale space. Furthermore, the authors investigated different architectures of the transferred VGG19-based CNN model, including the shallow model.
Introduction
The chapter illustrates that the detailed analysis of the fingerprint helps people to find the innate talents. Although fingerprint recognition was implemented from decade, it became one of the most common biometric today.
Literature survey
21]Detail-Based Fingerprint Verification System• Solve the grayscale profile near potential details. Difficult to non-linear fingerprint distortions [16]Minute Matching Algorithms__Not enough matching points in the input images.
Data analysis
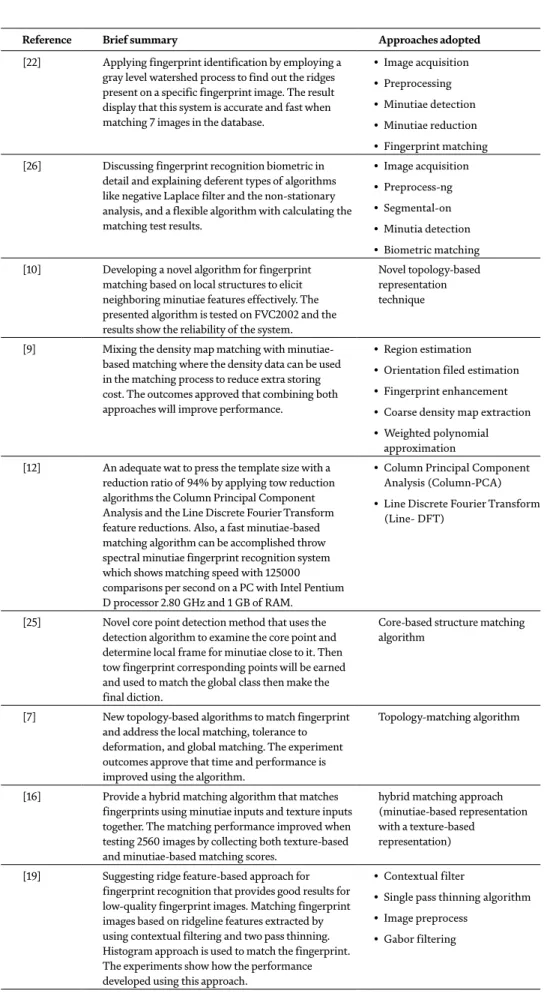
In the field of fingerprint recognition, conducting tests and experiments is important to approve and evaluate the quality and accuracy of the proposed work. Many different databases have been used to test the performance of the proposed matching algorithms.
Conclusion
Implementing fingerprint recognition technology is not only useful for the government, but other organizations and communities can also think along and benefit by applying fingerprint recognition techniques to identify themselves. For example, in the health sector, it is very important to use fingerprint recognition to identify the person injured in an accident.
Fingerprinting
On the other hand, the Department of Homeland Security's IDENT—the automated biometric identification system that incorporates fingerprint records and limited biographical information—was created in 1994 to help the U.S. In this post-9/11, globalized world, the Department of Justice (DOJ) and the FBI, the Department of Homeland Security (DHS), and the Department of Interoperability between these two years have been working hard to establish fingerprint databases.
Retina recognition
Voice recognition
What is an ECG?
The eye is placed in front of the system at a capture distance from 8 cm to 1 m. The retina is scanned with the near-infrared (NIR 890 nm) radiation, and the unique pattern of the blood vessels is captured.
ECG-based biometric identification structure
Several patents have been published suggesting the use of ultra-wideband radars to perform banking operations without a credit card, as well as for the control of premises during confidential meetings (Figure 2). As it turns out, it is possible to restore not only the EKG, but also speech with the help of ultra-wideband radars.
Registration of an electrocardiogram
If the characteristics received from an unknown person coincide with the characteristics from the database according to a certain criterion, a decision is made about the success of the identification. During the implementation of the project, we investigated the influence of various factors on the accuracy of biometric identification using electrocardiograms. We have shown that the quality of the electrocardiograph affects the accuracy of biometric identification.
Signal preprocessing
Further, the R peaks are detected on the ECG, with their help the signal is cut into cardiocycles, after which the R peak is synchronized. Thus, the recognition accuracy during ECG classification using mixed Gaussian models of subjects from the ECG-ID database was 0.66, while for PTB this indicator was 0.8 [14].
Biometric features extraction
Some authors propose the use of geometric characteristics of the cardiac cycle, such as the amplitude and temporal characteristics of the peaks of the cardiac cycle. The number of features in this case depends on the sampling frequency of the signal. Estimating the informative value of biometric features and selecting the most informative features.
Assessment of the informative value of biometric features and the selection of the most informative features
Previously we have investigated wavelets such as Haar wavelets, Daubechies wavelets (from db1 to db38), Symlets (from sym2 to sym20), Coiflets (from coif1 to coef17), Biortogonal (from bior1.1 to bior6.8), Reverse biortogonal wavelets (1.1 to bior6.8), Reverse biortogonal wavelet (1.F to IRbiorbiot), (Meyerte, 1 and 8). Approximation) [17]. We have shown that wavelets such as Haar, Daubechies and Symlets are best suited for biometric identification. We have shown that good results can be obtained if the entire cardio cycle is used as biometric features [18].
Feature classification
Assessment of the informative value of biometric characteristics and the selection of the most informative characteristics selection of the most informative characteristics. It can be seen from the figure that the overlap of the points is much less in the S and T regions. When all eight characters are used together, the overlap of the points is not observed (Figure 11).
Conclusion and perspectives
Researchers have made extensive use of MRA methods and use various off-the-shelf designs of wavelet filters [4] for implementing isotropic 2-D DWT for facial feature extraction. The limitation of the LBP-based feature extraction method is their noise intolerance and poor discrimination ability [8]. The implementation of the 2-D IDW using seven directions together with the quadtree partitioning (QTP) scheme [19] is explained in Section 2.
Implementation of 2-D improved directional wavelet (2-D IDW) The fundamental concept of implementation of improved directional wavelet
Next, in the prediction step, odd samples xo½ �i, j are predicted from adjacent even samples with strong correlation along an optimal direction θ: The result of the prediction step and the generated high-pass signal H i, j½ �is described as [19],. The value of the Lagrangian multiplier α determines the complexity of the QTP scheme, and its value must be chosen judiciously. In order to detect the local edge details and adapt it to the adaptability of the IDW method, a face image must be further segmented into partitions with clear orientation bias.
Local binary patterns
Suppose each face image x i, j½ � is applied with QTP to obtain non-overlapping subblock xs. Also consider the initial block size Sini, the minimum block size as Smin, and the Lagrangian multiplier as α. Where Fs,n½ �i,j are the filtered answers obtained by applying the prediction filter Kpalong with the predefined directionsθ.
Implementation of LBP-based IDW method
When a sample is predicted from the nearest samples, each candidate direction from (5) is checked and the direction with the smallest ESPE is finally selected. To solve this problem, an improved QP scheme is proposed to fit the face identification problem as mentioned in [19].
Face Identification using LBP-based IDW Input: Test Image, Train image
Preprocessing)
Computation of IDW sub-bands) for a number of decomposition levels do
LBP Computation)
Dimensionality Reduction)
Identification)
Experimental results
- Experiments on the CASIA-WebFace face database
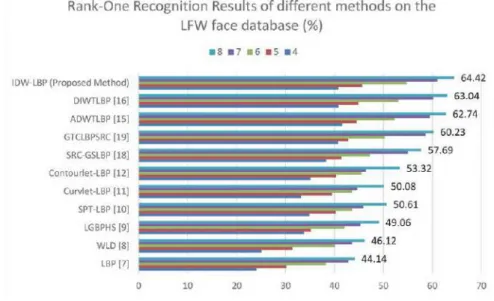
- Experiments on the labelled faces in the wild (LFW) face database The LFW [20] is a large database that contains face images of 5749 famous
In the experiments, we randomly select a few facial images for training and rest to test to get the recognition results. The face identification performance of the proposed method is performed on CASIA-WebFace [20] and LFW [21] face database with extreme face variations where all images are considered in an uninhibited environment. Since the images are selected in the uninhibited environment, the Rank-one recognition results are also low in this database.
Conclusion
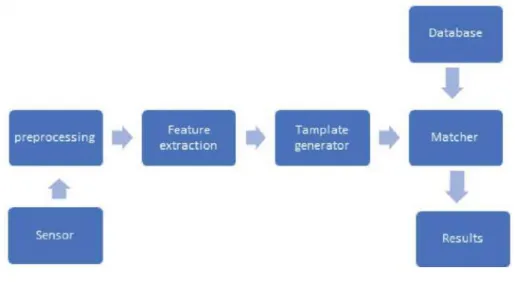
The IDW method consists of advantages such as directional lifting and direction selection adjustment according to the characteristics of the images in the sample block. This means that the palm print area must be localized based on a relative coordinate system established based on the key points of the finger valleys. Most of the current palmprint recognition algorithms are based on information about the direction of the lines and textures of the palmprint [1, 2].
Palmprint databases and ROI localization methods
- Comparisons of the current palmprint databases
- Related work on ROI localization
In [40], principal component analysis (PCA) is used to estimate the angle of rotation of the palm. The hand rotation angle information allows the palm image to be normalized to the standard orientation. The position of the center and side length of the ROI are both determined by the width of the palm.
The method
- The ROI localization method
- Abnormal detection and iterative localization
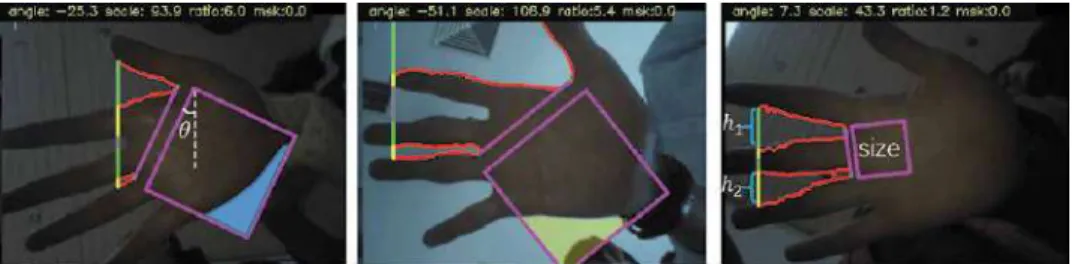
In the hand, landmarks are selected to form a shape, including 10 endpoints and 15 landmarks for the finger valleys and the palm border. The main work of landmark localization is to detect the finger valleys of the index and ring-little fingers (as shown in Figure 2(a) and (d)). The area of the ROI accounts for the scale information, so we use the tangent line lengthlti instead.
Experiments on different databases
- ROI extraction for IITD Touchless Palmprint Database
- ROI extraction for COEP Palmprint Database
- ROI extraction for PolyU Palmprint Database
Here, the angle and scale of the ROI, the background area ratio (if there are background areas in the located ROI), and the width ratio of the two finger valleys are selected as features for abnormal detection. In this section, the performance of the proposed method is tested on different palmprint databases. Image patches cut from palm skin and black box. a) spots on the surface of the palm; (b) black box patches.
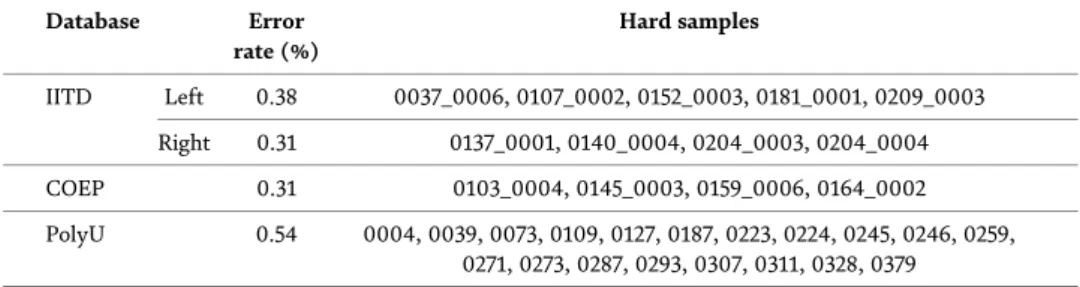
Conclusions
Available from: https://github.com/ma tkowski-voy/Palmprint-Recognition-in- the-Wild [Accessed: 29 May 2020]. With the development of image capture devices and recognition algorithms, palmprint recognition has received more and more attention recently. The purpose of this chapter is to review recent research on palmprint acquisition systems to trace the development of biometric systems based on handprint recognition.
The current palmprint recognition devices
- Touch-based devices
- Touchless devices
- Portable devices
- Key problems in device design
A well-designed capture system can capture high-quality images, which increases the efficiency of the identification algorithm. A monochrome CCD is placed at the bottom of the palmprint image capture device, and a light controller is used to control the multispectral light. The distance between the hand and the device must be within a fixed range (35-50cm) to ensure the clarity of palmprint images.
System design based on palm image sharpness
- Palm distance and recognition performance
- Image sharpness range and recognition performance
Various devices for taking palm prints and palm images generated therefrom. a) Touch-based device with a 500M pixel image sensor and a long imaging distance. The palm image captured by (b) and the corresponding local magnified regions. f) Images of palm trees obtained from (c) and corresponding local magnified regions. the palm and the optical center of the camera. However, the hardware and image model parameters are not always available in practice.
Conclusions
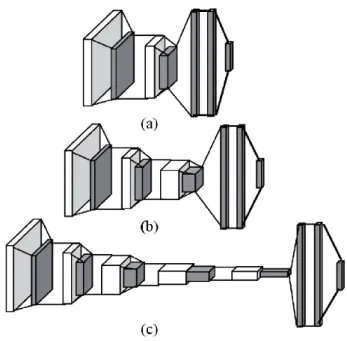
The curves of EER and eav on different databases obtained by different recognition algorithms. a) The OER is obtained by Competitive Code. b) The OER is obtained by OLOF. In: Proceedings of the IEEE Computer Society Conference on Computer Vision and Pattern Recognition (CVPR June 2005). In addition, a different architecture of the transferred VGG19-based CNN model has been investigated, including a shallow model, a medium model and a deep model.
Architecture of pre-trained VGG19 CNN model
Specifically, each base classifier in the ensemble model is trained with different subsets of the given training set. Nowadays, transfer learning is becoming a promising technique that can be applied to use and reuse a powerful pre-trained CNN models to deal with different pattern problems. A series of experiments performed to evaluate the effectiveness of the proposed approach is given in Section 3.
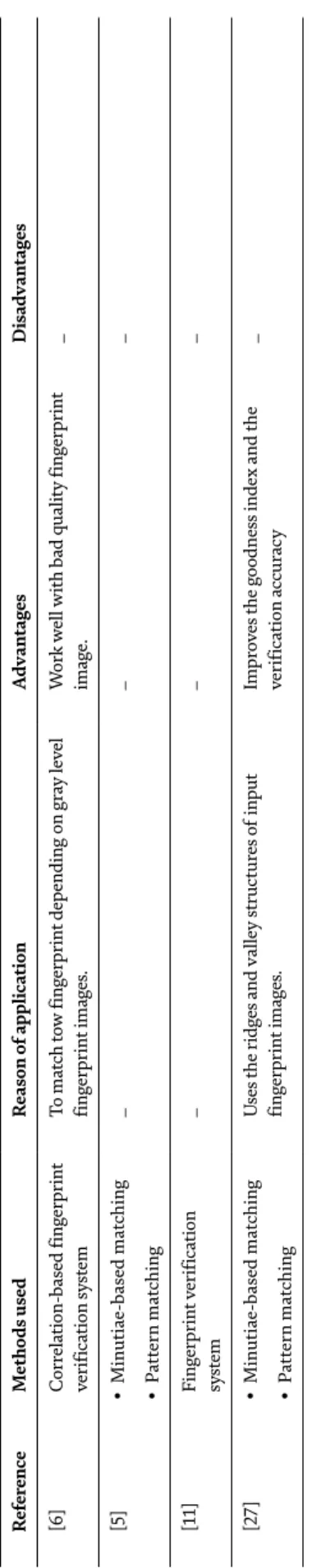
Transfer learning of pre-trained VGG-19 CNN model
Going deeper into VGG, the number of convolutional filters has increased from 64 to 512, as shown in Figure 1. It should be noted that VGG19 contains two consecutive FC layers with the same size as shown in Figure 1. The basic idea of transfer learning is to use a pre-trained network such as VGG19, and then perform a replacement for the last layer, which is a soft maximum classifier.
Experimental analysis
Besides that, a new CNN model has been made from scratch with the same architecture as a shallow model. The worst performance was produced by a CNN model created from scratch as indicated in Figure 5. As it can be demonstrated that the AUC value from the transferred models outperforms the results of the CNN model created from scratch.

Conclusion
The reported results confirmed the performance of the transferred VGG19 models compared to the CNN model generated from scratch. Visualization of intermediate layers of transferred models based on VGG19, i.e. shallow, medium and deep models. This can help the guide/mentor to recognize the inherent qualities and strong way of speaking of a man or woman.
Proposed methodology
- Right brain
In this chapter the authors had shed light on the many already existing methods and techniques for fingerprint recognition system. In this chapter, the authors provided an in-depth knowledge of fingerprint recognition and also proposed a secured fingerprint recognition payment system [8]. Examples of body features that can be used for biometric recognition (courtesy: http://images.google.co.in).
Functions of brain of different sections
- Verbal intelligence
They play a key role in integrating sensory information from multiple detectors in addition to the thing manager. The forebrain is divided into two components, the left brain and the right brain. Build a collection of favorite music clips and give them your attention every day.