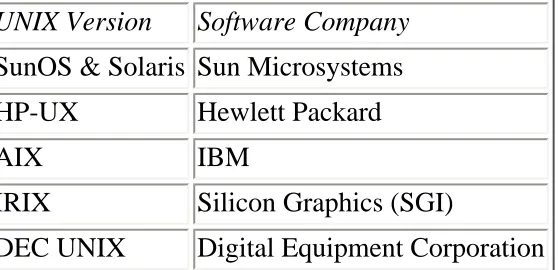
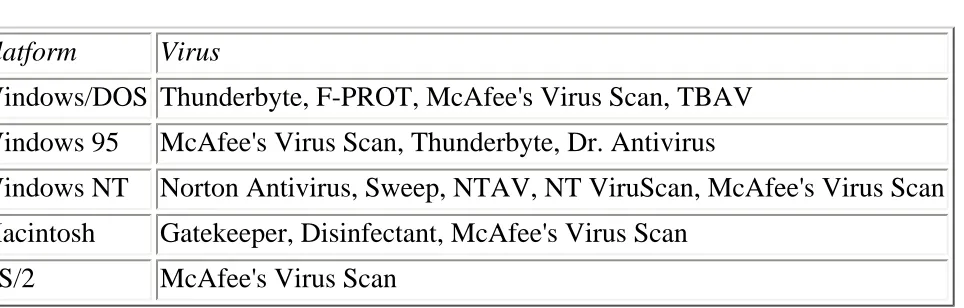
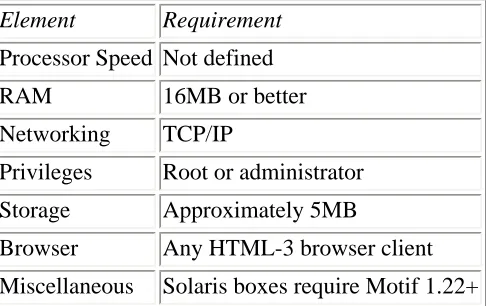
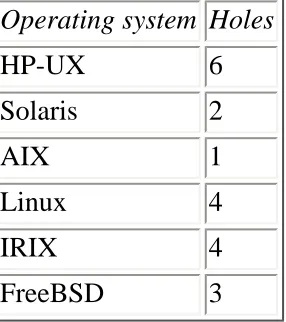
Maximum Security. 2657KB Mar 29 2010 05:03:18 AM
Teks penuh
Gambar
Garis besar
Dokumen terkait
L eft: uncontrolled dumping of waste; right: organized disposal of L eft: uncontrolled dumping of waste; right: organized disposal of waste and covering of landfill body. waste
combined with mechanical sorting of mixed waste streams combined with mechanical sorting of mixed waste streams is called mechanical biological treatment. is called
times, but it's absolutely essential.) When setting up an SNMP agent, you will want to configure its trap destination, which is the address to which it will send any traps
A known hosts file, if present, contains public host keys of known remote machines. These keys were generated on
dari dekstop komputer Anda. 2) Kemudian ketika muncul jendela XAMPP Control seperti gambar di bawah ini, klik tombol Start pada bagian modul MySQL (lihat bagian yang dilingkari). 3)
Many of t he exam ples shown in t his book can be run using script files t hat are available as part of t he accom panying recipes source dist ribut ion ( see Appendix A ).
Before we talk about the details of the XML document design and the XSLT source code, we'll review the actual HTML, zip, and PDF files we need to create. One advantage we had in