Shorifuzzaman, ID Number of the Department of Computer Science and Engineering, Daffodil International University, has been accepted as satisfactory in partial fulfillment of the requirements for the degree of M.Sc. Department of Computer Science and Engineering Faculty of Science and Information Technology Daffodil International University. I hereby declare that this thesis has been carried out by me under the supervision of Md.
I am also certified that neither this thesis nor any part of this thesis has been submitted elsewhere for the award of any degree or diploma. First of all, I would like to express my special thanks and gratitude to Almighty Allah for His divine blessing enabling me to successfully complete the final year thesis. I am indebted to Daffodil International University for their guidance and constant supervision, as well as for providing the necessary information regarding the dissertation.
Zahid Hasan, Associate Professor, Daffodil International University for her kind cooperation and encouragement which helped me to complete this thesis. Cloud computing, Software Defined Networking (SDN) and Network Function Virtualization (NFV) are the primary technology capabilities maturing for use in 5G. However, these technologies face significant security challenges in addition to growing concerns about user privacy.
CapEx Capital Expenditure Operational Costs SDN Software Defined Networking NFV Network Functions Virtualization IDS Intrusion Detection Systems.
INTRODUCTION
- Introduction
- Motivation
- Objectives
- Thesis Outline
2 Therefore, it is important to know that not only mobile wireless networks can be dangerous, but also the technologies that can be used for 5G. The goal of 5G research and development is greater capacity than the current 4G, device-to-device (D2D) communication, a large number of mobile broadband users, as well as a large number of machine-to-machine interactions.
Introduction Chapter 2 : Literature Review
Key security challenges in 5G Chapter 4 : Discussion & Recommendation
LITERATURE REVIEW
- Introduction
- Related Works
- Scope of the problem
- Most Significant Security Challenges in 5G
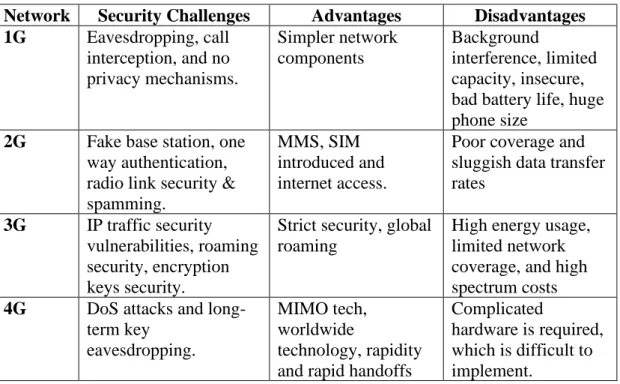
However, new concepts and large-scale IoT integration will make the security challenges of 5G more diverse than ever. 5G allows for larger and more dangerous attacks due to the increased number of connected devices. 5G is also more dependent on software, which increases the risk of network infrastructure exploitation.
With virtualization, the service model for a system can be separated from its physical implementation, allowing logical copies of the hardware to be used for different purposes. The introduction of 5G networks has replaced the use of GTP and IPsec tunnels in previous generation mobile networks for dedicated communication channels. Network slicing is an important technology in next-generation networks, enabled by software-defined networks and virtualization of network functions.
Customers' personal information can be accessed by participants in the process, with or without their consent. It is expected that users and other stakeholders will face greater risks to their privacy as a result of the introduction of new architecture, technology and services on the 5G network. Until the transition from 4G to 5G is complete, the vulnerabilities in 4G networks will persist in 5G networks.
Previous generation networks are particularly vulnerable to SMS and call interception, illegal geo-tracking and denial of service (DoS) attacks. Deliver the largest network services to 5G users in the most frictionless way possible without requiring long customer visits (eg for switching between RATs). A swarm of digitized software-defined routers has replaced conventional hardware-based security checkpoints in 5G networks, making them difficult to examine and monitor.
The risk to 5G networks comes from a wide range of devices, including seemingly innocuous home networking devices like smart thermometers and smart thermometers that can provide security holes in network armor. Enhanced encryption of user and signaling data between a user device and a base station, itself an increasingly sensitive device in 5G architecture, is mandatory to ensure data integrity, but is an optional feature to protect user privacy in 5G the specification. 5G is not backward compatible with previous generations of networks; transition to 5G requires replacement or addition of physical devices and software.
KEY SECURITY CHALLENGES IN 5G
- Introduction
- Security Challenges in Mobile Clouds
- Security Challenges in SDN and NFV
- Security Challenges in Communication Channels
- Privacy Challenges in 5G
Due to the centralized nature of cloud computing resources, malicious traffic generated by one user can easily spread to other users. The fundamentals of cloud computing will be applied to the 5G ecosystem in a mobile cloud computing system. This creates a number of security concerns, most of which stem from the architectural and infrastructural changes of 5G.
Servers and storage systems for the back-end platform and virtual machines, hypervisor and protocol software make up this part of the cloud service platform. Cloud radio access networks are another popular question when investigating security risks in the 5G mobile cloud. Viruses and other malware can take over a network if malicious applications have access to the SDN infrastructure.
In addition to drones, cloud-based reality, connected vehicles, cloud-based robotics, transportation and health will all be part of the 5G ecosystem. Mobile networks depended on specialized communication channels designed around GTP and IPsec tunnels before the introduction of 5G networks. The communication channels in a 5G mobile network based on SDN are classified as follows: data channels, control channels and inter-controller communication channels.
The physical layer of 5G mobile networks can reveal location protection via access point selection mechanisms. It is possible that the IMSI associated with the victim will be used to avoid detection by establishing a fake base station as a result of these abuses. In addition to VMNOs, CSPs and network infrastructure providers, 5G networks employ a wide range of professionals.
Carriers would lose total control of the system if 5G were solely dependent on new entrants such as CSPs. Due to the characteristics of cloud data storage and network function virtualization (NFV), 5G networks have no physical boundaries. Having user data stored in the cloud in a separate nation poses a privacy risk due to the different degrees of data protection in different countries.
DISCUSSION AND RECOMMENDATION
- Introduction
- Security Solutions for Mobile Clouds
- Security Solutions for SDN and NFV
- Security Solutions for Communication Channels
- Security Solutions for Privacy in 5G
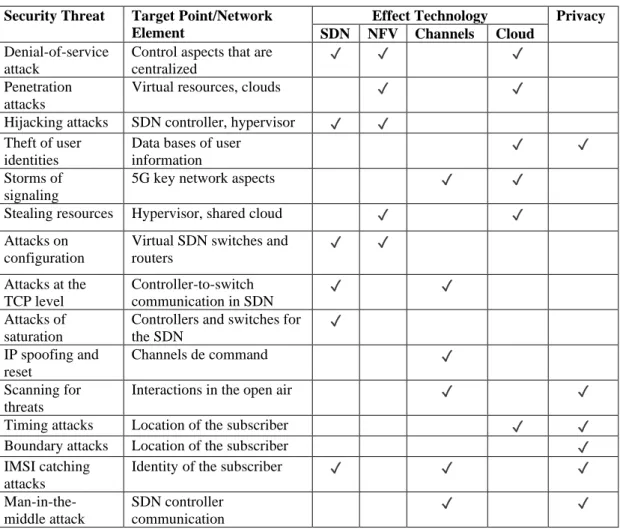
Anti-malware software can be installed on a mobile device or can be hosted and delivered via the cloud. These mechanisms will ensure that data and storage services are secure when used with public information systems and when volatile storage is released. 18 applications that can be extended on cloud computing mobile devices is one of the frameworks presented for app security, along with other ideas such as an unencrypted user authentication protocol, a private privacy device, and cloud computing.
By updating the flow table of software programmable network switches, traditional network security rules can be applied across the entire network. Security solutions such as firewalls and intrusion detection systems can be used for specific traffic. With minor modifications, IPsec tunneling can be used to protect 5G communication channels, as shown in [22] and [24].
Furthermore, various security techniques, such as authentication, integrity and encryption, are integrated to ensure security for LTE communication. RF fingerprints, asymmetric schemes and dynamically changing security settings can all be used to improve the level of security for important communications. This means that 5G must be designed with privacy in mind from the start, and many key safeguards must be built in to protect users' data.
This will allow operators to make better informed judgments about how and with whom they share their data in the future. In addition, 5G service-oriented privacy would provide more effective solutions to preserve personal data [61]. The future will require better ways to take responsibility, store small amounts of data, be transparent, open and control who has access to it.
At the second level, different industries and groups such as 3GPP, ETSI and ONF work together to come up with the best practices and principles to protect your privacy. Before you send a message to someone who provides Location-Based Services (LBS), the message can be encrypted. Location cloaking algorithms can also handle important location privacy attacks, including timing and boundary attacks [26].
CONCLUSIONS AND FUTURE SCOPE
Conclusion
Future Scope
Management and systems engineering from 5G is undergoing a sensational redesign that will increase elements and focus if security assurance and protection ideas are incorporated in time, the quality of 5G. But it will also open up new opportunities for people who want to use this new technology. To begin, it is important to understand how very different the security challenges of 5G are from those of previous generations.
Technologists, educators, vendors, operators and government are working to better understand how 5G will work, what its security concerns are and how it will be used around the world. 5G is supposed to solve many problems by having many new features, such as super high speed internet and smooth, always-on service. With 4G/3G still in development, and 5G not yet launched in many countries, what is the future of 5G.
Unlimited calls and seamless data transmission are included in the state-of-the-art mobile operating system. Thus, in the near future, more intelligent technology will be used to connect the entire world without borders. In addition, governments and regulators must work together to address the security challenges of 5G in order to reap the full benefits of 5G in the future.
Oktian, “Securing Distributed SDN with IBC,” in International Conference on Ubiquitous and Future Networks, ICUFN, 2015, vol. Wieringa, “Security Implications of Virtualization: A Literature Study,” in Proceedings - 12th IEEE International Conference on Computer Science and Engineering, CSE vol. Janicke, “Security for 4G and 5G Mobile Networks: A Review of Existing Authentication and Privacy Protection Schemes,” Journal of Network and Computer Applications, vol.
Asal, “NFV: State-of-the-art,challenges and implementation in next-generation mobile,networks (vEPC),”,IEEE Netw., vol. Liu, “A location cloaking algorithm based on combinatorial optimization for location-based services in 5G networks,” IEEE Access, vol.