GNU/LINUX WITH TEXT USER INTERACE
FOR STUDENT LEARNING
Indira Cempakasari
107091100142
INFORMATICS ENGINEERING
FACULTY OF SCIENCE AND TECHNOLOGY
STATE ISLAMIC UNIVERSITY
SYARIF HIDAYATULLAH
JAKARTA
ii
by:
Indira Cempakasari
107091100142
Thesis
As one of requirement to get bachelor degree of
Computer Science
Faculty of Science and Technology
State Islamic University Syarif Hidayatullah Jakarta
INFORMATICS ENGINEERING
FACULTY OF SCIENCE AND TECHNOLOGY
STATE ISLAMIC UNIVERSITY
SYARIF HIDAYATULLAH
JAKARTA
iii Thesis
As one of requirement to obtain a bachelor degree in computer science Faculty of Science and Technology
State Islamic University Syarif Hidayatullah Jakarta
By:
Indira Cempakasari 107091100142
Approved,
Supervisor I Supervisor II
Asep Fajar Firmansyah Iwa Airlangga, MTI Feri Fahrianto, M.Sc NIP. 198008292011011002
Head of Informatics Engineering Program
iv
”, has passed the examination held in Faculty of Science
and Technology, State Islamic University Jakarta, on Tuesday August 23rd 2011. The owner of this thesis is therefore awarded a bachelor degree in computer science.
Jakarta, September 2011
Examiner I, Examiner II,
Husni Teja Sukmana, Ph.D Arini, MT
NIP. 19731209 200501 1 002 NIP. 197601312009012001
Supervisor I Supervisor II
Asep Fajar Firmansyah Iwa Airlangga, MTI Feri Fahrianto, M.Sc NIP. 198008292011011002
Dean Faculty of Science and Technology, Head of the study program
DR. Syopiansyah Jaya Putra, M.Sis
Yusuf Durachman, M.Sc, MITv
THESIS. NO WORK OF OTHERS IS INCLUDED WITHOUT REFERENCING OR ASKING FOR PERMISSION FROM THE AUTHORS OR PUBLISHERS.
Jakarta, September 2011
vi
There are some routers such as Cisco, Mikrotik, Freesco router and RouSer. Every router has their advantages and weaknesses. Almost routers that are exist do not use open source applications and less portability, only few routers that are portable and open source. So that it is developed a portable router GNU/Linux that is all applications are open source, portable, simple, provides Text User Interface inside the system and provide Text User Interface for installing the router to flash disk or portable storage. The function of router is to route the packets in different network. This portable router in this research uses Slackware core, open source applications for routing, and interfaces that are built use bash scripting. The interfaces consist of installation interface and configuration interface. Methodology for the development of router is prototype model. In every prototype, there is feedback from the customer so that the prototype is developed more. In prototyping model, there is no limit time. There are three prototypes to develop the router. The development of the first prototype followed the user requirement from the customer and the next prototype followed the feedback customers. The router testing consists of installation interface (hard disk and flash disk) and configuration interfaces. After doing analysis and implementation, to develop portable router GNU/Linux can use Slackware core, packets needed for routing, boot live for booting live CD in order this router can be installed and boot. To make easy and to help students and lectures as end users in the usage of this router, this router is provided user interface for configuration and installing the router. User interface used in this router is Text User Interface. In the next development, the router should be able to do dynamic routing, firewall, and they should work with interface to ease the students and lectures as the end users.
vii
“Developing Portable Router GNU/Linux with Text User Interface”. Furthermore, my
regards to our beloved Prophet Muhammad SAW.
In this opportunity, I would like give my thanks to:
1. Dr. Ir. Syopiansyah Jaya Putra, M.Sis. as the Dean of the Faculty of Science and Technology, UIN Syarif Hidayatullah Jakarta.
2. Mr. Yusuf Durraachman, M.Sc, MIT as a Chairman of the Information Technology Program, Faculty of Science and Technology, UIN Sharif Hidayatullah Jakarta.
3. Mr. Asep Fajar Firmansyah Iwa Airlanggi, MTI and Mr.Feri Fahrianto, M.Sc, as my supervisors. Thank for the correction and suggestions for my thesis.
4. Mr. Husni Teja Sukmana, Ph.D and Mrs.Arini, MT as my examiners. Thank for the correction for my thesis.
5. Mrs. Ria who guides me in Interntional Program.
6. All lectures in International Program for the lessons and the knowledges. 7. My Mom and my Dad who always support and doa for me.
8. Kak Ibnu who always helps and support me.
9. My sisters, dek ulan and mba iken, who helped in shooting video.
10. Nilam, atin, yuni, alex, galih, mahar and my friends in international program that learn and study together.
11. Junior in International program, thank for coming in my seminar. 12. Mba mita that help in writing letters.
viii
Jakarta, August 2011
ix
“Maka nikmat Rabb kamu yang manakah yang kamu dustakan?” (Q.S Ar-Rahman) Alhamdulillah skripsi ini dapat diselesaikan
Skripsi ini saya persembahkan untuk:
Kedua orang tua saya yang telah mendidik dan membesarkan saya, serta memberi dukungan kepada saya. I love you mom n dad . Terima kasih untuk semuanya.
ix
APPENDIX LISTS ... xviii
CHAPTER I INTRODUCTION ... 1
2.1.2 Components of Operating System ... 11
2.1.3 Operating System Structure ... 13
2.1.4 GNU/Linux System ... 16
2.2 Core ... 19
x
CHAPTER III RESEARCH METHODOLOGY ... 37
3.1 Research Method ... 37
3.2 Collecting Data Method ... 39
3.2.1 Method of Collecting Primary Data... 39
3.2.2 Method of Collecting Secondary Data... 40
3.3 Analysis Method ... 42
3.4 Testing Method ... 43
CHAPTER IV DISCUSSION AND IMPLEMENTATION ... 44
4.1 First Prototype ... 44
xi
4.1.2.2 Quick Design ... 54
4.1.3 Construction Prototyping ... 59
4.1.4 Deployment Delivery and Feedback... 63
4.1.4.1 Deployment Delivery ... 63
4.2.3. Construction Prototyping ... 89
4.2.4. Deployment Prototyping and Feedback ... 90
4.2.4.1 Deployment Prototyping ... 90
4.2.2.2 Feedback ... 102
4.3 Third Prototype ... 102
4.3.1 Communication ... 102
4.3.2. Quick Plan and Quick Design ... 103
4.3.2.1 Quick Plan ... 103
4.3.2.2 Quick Design ... 112
4.3.3 Construction Prototyping ... 120
4.3.4 Deployment Prototyping and Feedback ... 121
4.3.4.1 Deployment Prototyping ... 121
4.3.4.2 Feedback ... 129
CHAPTER V SUMMARY ... 130
5.1 Conclusion ... 130
5.2 Suggestion ... 130
xii
Figure 4.1 Quick Plan ... 45
Figure 4.2 Topology ... 46
Figure 4.3 Hard disk Installation Flowchart ... 48
Figure 4.4 Flash Disk Installation Flowchart ... 44
Figure 4.5 Setting IP Flowchart ... 46
Figure 4.6 Routing Flowchart ... 48
Figure 4.7 Choosing installation ... 55 Figure 4.8 prototype1 model harddisk-1 ... 55 Figure 4.9 prototype1 model hard disk-2 ... 56 Figure 4.10 prototype1 model hard disk-3 ... 56
xiii
Figure 4.31 Test1 install Flash Disk-2 ... 67
Figure 4.32 Test1 install Flash Disk-3 ... 68
Figure 4.33 Test1install Flash Disk-4 ... 68
Figure 4.34 Test1 install Flash Disk-5 ... 69
xiv
xv
Figure 4.91 Hard disk installation Flowchart 3 ... 104
Figure 4.92 Flash disk Installation Flowchart 3 ... 105
Figure 493 SettingIP 3 Flowchart ... 107
Figure 4.94 Setting DNS Flowchart 3 ... 108
Figure 4.95 Routing Flowchart 3 ... 109
Figure 4.96 Disable Routing Flowchart ... 110
Figure 4.97 DHCP Flowchart ... 111
Figure 4.98 Prototype3 Model hard disk-1 ... 112
Figure 4.99 Prototype3 Model hard disk-2 ... 113
Figure 4.100Prototype3 Model hard disk-3 ... 113
Figure 4.101 Prototype3 Model hard disk-4 ... 113
Figure 4.102 Prototype3 Model flash disk-1 ... 114
Figure 4.103 Prototype3 Model Flash disk-2 ... 114
Figure 4.104 Prototype3 Model Flash disk-3 ... 114
Figure 4.105 menu Model 3 ... 115
Figure 4.106 Prototype 3 Model setting IP-1 ... 115
Figure 4.107 Prototype 3 Model Setting IP-2 ... 116
Figure 4.108 Prototype3 Model Setting IP-3 ... 116
Figure 4.109 Prototype3 Model Setting IP-4 ... 116
Figure 4.110 Prototype 3 Model Setting IP-5 ... 117
Figure 4.111 Prototype 3 Model DNS-1 ... 117
Figure 4.112 Prototype 3 Model DNS-1 ... 117 Figure 4.113 Prototype3 Model routing 1 ... 118
Figure 4.114 Prototyp3 Routing-2 ... 118
Figure 4.115 Prototype3 Routing-3 ... 119
Figure 4.116 Disable routing ... 119
xvi
Figure 4.121 Test3 Flash disk-2 ... 122
Figure 4.122 Test3 Flash disk-3 ... 122
Figure 4.123 Test3 Flash disk-4 ... 123
Figure 4.124 Test3 Flash disk-5 ... 123
Figure 4.125 Configuration Interface Test ... 124
Figure 4.126 Menu Configuration Interfaces ... 124
Figure 4.127 Test3 Setting IP-1 ... 125 Figure 4.128 Test3 Setting IP-2 ... 125
Figure 4.129 Test3 DNS-1 ... 126
Figure 4.130 Test3 DNS-2 ... 126
Figure 4.131 Test DHCP-1 ... 127
Figure 4.132 Test DHCP-2 ... 127
Figure 4.133 Test Routing-1 ... 128
Figure 4.134 Test Routing-2 ... 128
Figure 4.135 Test Routing-3 ... 129
xvii
Table 2.2 Operations in Iptables ... 26
Table 2.4 Parameters in iptables ... 26
xviii
1 1.1 Background
Internet is important for most people today. Most people might not know the stand for Internet. Internet stands for interconnected-networking. Everyone in everywhere usually use Internet for completing their task, communicating with their family and friends or getting information. To connect Internet, every computer or end device needs IP address.
Based on Iwan (2009:255), Internet Protocol (IP) is a protocol that is connectionless and unreliable. In IP header, there is a field that contains of IP address. IP address is as sign in packet source and destination sources. And based on Dede (2008:63), Internet Protocol is a method or protocol to transmit the data to internet. Every computer in networks has to a unique IP address that identified a computer to other computers. Anjik and Rianto (2008:99) said that IP address is used as logical identity in a host in the network. An IP address consists of network-id and host-id. If a network did subnetting, so an IP address becomes consist of network-is, subnet-id, and host-id.
255.255.255.0 as netmask and network C is set 192.168.13.1 as ip address and 255.255.255.0 as netmask. Host A and host B can communicate directly because they have same network-id, but host A and host B cannot connect and communicate with a host C because host C has different network-id with host A and host B though they have same netmask. To make host C be able communicate with host A and B, router is needed.
Routing is performed by a router. It means the router could know the route that will be passed by the packet. The packet will be sent whether to host in same network or host in different networks. If the packet is for a host in another network, router will forward the packets to that network. Otherwise, if the packets is for a host in same network, router will block packet so the packet cannot go out and will not flood others networks (Iwan, 2009:58).
There are some routers, such as Cisco router, Mikrotik, Freesco and RouSer router.
1. Cisco. Based on information from a www.cisco.com, Cisco is a big vendor that produces and sells the network devices. One of its products is Cisco router. Cisco routers are highly secure, flexible, and built to be compatible with future technologies. There are kinds of Cisco router products and every product has their advantages. The price of one of wireless routers is $89.99.
utilities in Mikrotik routerOS have licenses. The price of license Mikrotik routerOS (without DOM) is Rp.400.000, 00.
3. Freesco. Based on the website www.freesco.org, Freesco was developed in the open source tradition as an alternative to routing products offered by Cisco, 3-Com, Accend, Nortel etc. Freesco is open source, stable, inexpensive, easy to use, extremely versatile and flexible and free. Freesco is based on the Linux operating system. And incorporates many of the features of other Linux distributions into software that fits onto a single 1.44 meg floppy diskette.
4. RouSer. According to Zulfikri Ali, RouSer is a mini Linux distribution that is able to transform a computer into a PC router. The feature of RouSer are routing, firewall, and bandwidth management. It uses Command Line Interface. The license is GNU GPL.
Based on information from those routers, every router has their advantages and weakness. Cisco routers are highly secure, flexible, and built to be compatible with future technologies, but the price is expensive enough for small company that only has lower cost. Besides that, there is Mikrotik routerOS. Mikrotik routerOS made Linux-based, but the utilities are not open source. The users need to buy the licenses. Moreover, there is really open source router, called Freesco. Freesco is open source, stable, inexpensive, easy to use, extremely versatile and flexible and free, but it uses floppy disk as media to install that router. Almost laptop products do not provide floppy disk now. The last is RouSer. It has the open source license and all utilities to develop the router are open source, but it still uses Command Line Interface as its interface.
about the function of router itself, but sometimes the lecture is hard to find “free” router that can be used for teaching and practicing. The students know how to setup the router, but sometimes they do not know how it works. The student cannot experiment more with the routers that already exist. Besides not knowing about the router works, the students do not how to develop the router itself and do not know how to build the interface for installing the router, even if the routers are open source router. It makes they get wrong perception about open source utilities or even about linux itself. Sometime student or even a lecture thinks that linux is an operating system. According to Stallman (1997), Linux is the kernel: the program in the system that allocates the machine’s resources to other programs that you run. The kernel is essential part of an operating system, but useless by itself, it can only function in the context of a complete operating system.
According to the examples of router and the explanation above, the writer is planning to develop a router that is simple, portable (using flash disk), open source router and can be learnt by students and used for teaching. Open source
Based on that reasons, the titled for this thesis is “Developing Small Portable Router GNU/Linux with Text User Interface For Student
Learning”.
1.2 The Problem Definition
Based on the background, there are some points to decide the problem definition. The first, almost routers do not use open source utilities to develop the router; second, the router in example are less portability, no one could install in flash disk or portable storage; the third is the interface of those routers are not inside the system; the fourth is the students cannot know how to develop a router that can be installed in portable storage because the license and the last is interface for installing the router, the students do not know how develop installer. So that the problem definition in this thesis is how to develop a portable router GNU/Linux that is simple, all utilities are open source, included interface inside the system and build interface for installing the router.
1.3 The Scope of Problem
In order to avoid deviation in this discussion, the author would like to discuss the scope of the problems:
1. The Building Interface. Interface was built with Text User Interface by using bash scripting. The interfaces consist of installation interfaces and configuration interfaces.
3. Using Linux kernel and all utilities are open source. 4. For IPv4 only.
5. For DHCP interface, it sets in subnet mask 255.255.255.0 6. Student can use the router for learning.
1.4 Aims and Objectives
The objectives of the research are:
1. To develop a portable router GNU/Linux that is open and easy to be used by end user (student and lecture).
The aims that will be got in the research are: For the writer:
1. To make understand deeper the function and how the router works. 2. To learn about how to develop open source software
For the student:
1. The students understand how the router works.
2. The students know about the developing portable operating system that has function as a router.
3. The lecture can use this portable router for teaching and practicing.
1.5 Contents of Thesis
CHAPTER I INTRODUCTION
This chapter discussed about research background, problems definition, scope of problems, research aims and objectives, and research format writing.
In this chapter is explained about literature review such as definition router, the function of router, explanation about operating system, explanation about Linux and package needed in a router, and tools used in the research.
CHAPTER III RESEARCH METHODOLOGY
This chapter discuss and give obviously explanation about research methodology which is used in router research, so it can be discovered the planning that would be done.
CHAPTER IV DISCUSSION AND IMPLEMENTATION
This chapter discuss about design of the router and that will be developed and analyze in detail about the research. This chapter also contains about the testing of what the writer will have been done in the research.
CHAPTER V SUMMARY
Conclusion and suggestion for the writer is written in this chapter.
CHAPTER II
computer itself, and application programs, which perform the actual work the user wants. The most fundamental system program is the operating system, whose job is to control all the computer's resources and provide a base upon which the application programs can be written. Operating Systems perform two basically unrelated functions, extending the machine and managing resources.a. The operating Systems as an Extended Machine.
The function of the operating system is to present the user with the equivalent of an extended machine or virtual machine that is easier to program than the underlying hardware.
b. The operating System as a Resource Manager.
and controlled allocation of the processors, memories, and I/O devices among the various programs competing for them.
According to Silberschatz, et al (2006:3), an operating system is a program that manages the computer hardware. It also provides a basic for application programs and acts as an intermediary between the computer user and the computer hardware. Mainframe operating systems are designed primarily to optimize utilization of hardware.
Still based on Silberschatz, et al (2006:3), a computer system can be divided roughly into four components: the hardware, the operating system, the application programs and the users. The hardware-the central processing unit (CPU), the memory, and the input/output devices provides the basic compiling resources for the system. The application programs-such as word processors, spreadsheets, compiler, and web browsers define the ways in which these resources are used to solve users computing problems. The operating system controls and coordinates the use of the hardware among the various application programs for the various users. The operating system' role:
a. User View.
b. System View
An operating system is as a resource allocator. A computer system has many resources that may be required to solve a problem: CPU times, memory space, file storage space, I/O device, and so on. The operating stem acts as the manager of these resources. The operating system must decide how to allocate them to specific programs and users so that it can operate the computer system efficiently and fairly.
An operating system is a control program. A control program manages the execution of user programs to prevent errors and improper use of the computer. It is especially concerned with the operation and control of I/O devices.
Based on Stalling (2008:51), an OS is a program that controls the execution of application programs and act as an interface between applications and the computer hardware. It can be thought of as having three objectives:
1. Convenience: An OS makes a computer more convenient to use.
2. Efficiency: An OS makes computer system resources to be used in an efficient manner.
2.1.2 Components of Operating System
According to Masyarakat Digital Gotong royong (2006:10), an operating system can be divided into some components.
a. System Process Management.
A process is a program that is being executed. Operating System has responsibility in activities in a process management, such as:
1. To make and to delete user process and process system 2. To delay or to continue the process.
3. Providing mechanism to synchronize the process. 4. Providing mechanism to communicate the process. 5. Providing mechanism to manage the deadlock. b. System Memory Management.
Main memory is an array that is from word or byte, the size is until hundred or million. Every byte has its own address. Main memory has function as data/instruction storage that the data access is used by CPU and input/output device. Main memory is volatile data storage. Operating System has responsibilities in memory management:
1. Keeping the track from the used memory and who used memory. 2. Choosing the program that will be loaded into memory.
3. System File Management
implements the concept from the file by managing storage mass media such as tapes and disk.
1. Creating and deleting file 2. Creating and deleting directory
3. Supporting the file and directory manipulation 4. Doing file mapping
5. Backup file to non-volatile storage c. System Management I/O
It is called device manager. Operating system components for system management I/O are:
1. Temporary storage data from and to system input/output. 2. Spooling: scheduling the usage of input/output
3. Providing drive. d. Management Secondary Storage
Data that is saved in main memory is temporary. So that why, to save a whole of data and computer program are needed permanent secondary storage that can be able store many data as backup from main memory. Examples of secondary storage are hard-disk, diskette etc. Operating system has responsibilities in management secondary storage:
e. Protection System
It is used to control access that is occurred by programs, processor, or user. Protection mechanism should be:
1. Can differ user that has privilege to access data and ordinary user. 2. Specific control
3. Providing tools to implement the system. f. Network
Distribution System is a collection of processors that has its own memory and own clock. Those processors connect via network communication. Distribution system provides user access to kind of resources. That access causes increased computing speed an increases the ability of providing data.
g. Command-Interpreter System
Operating system waits instruction from the user (command driven). Programs that read instruction and interpret control statement usually called: control-card interpreter, command-line interpreter, and sometimes it are called shell.
2.1.3 Operating System Structure
should be a well-defined potion of the system, with carefully defined inputs, outputs, and functions. How components of operating system interconnected and melded into a kernel:
a. Simple Structure.
Many commercial systems do not have well-defined structures. Frequently, such operating systems started as small, simple, and limited systems and then grew beyond their original scope. MS-DOS is an example of such a system. It was written to provide the most functionality in the least space, so it was not divided into modules carefully.
Another example of limited structuring is the original UNIX operating system. UNIX is another system that initially was limited by hardware functionality. It consists of two separable parts: the kernel and the system programs. The kernel is further separated into a series of interfaces and device drivers, which have been added an expanded over the years as UNIX has evolved. The kernel provides the file system, CPU scheduling, memory management, and other operating system functions through system calls. b. Layered Approached
A system can b made modular in many ways. One method in the layered approach, in which the operating system s broken up into a number of layers (levels). The bottom layer (layer 1) is the hardware, the highest (layer N) is the user interface.
operating system layer-layer M consists of data structures and a set of routine that can be invoked by higher-level layers. Layer M, in turn, can invoke operations on lower-level layers.
The main advantage of the layered approach is simplicity of construction and debugging. The layers are selected so that each uses functions (operations) and services of only lower-level layers.
c. Microkernels
Microkernels structures the operating system by removing all nonessential components from the kernel and implementing them as system and user-level programs. The result is a smaller kernel. Microkernls provide minimal process and memory management, in addition to a communication facility.
The main function of the microkernels is to provide a communication facility between the client program and the various services that are also running in user space. Communication is provided by message passing.
2.1.4 GNU/Linux System
According to Stallman (1997), many computer users run a modified version of the GNU system every day, without realizing it. Through a peculiar turn of events, the versions of GNU which is widely used today is often called
“Linux”, and many of its users are not aware that is basically the GNU system, developed by the GNU project.
Still based on Stallman (1997), Linux is the kernel: the program in the system that allocates the machine's resources to other programs that you run. The kernel is essential part of an operating system, but useless by itself, it can only function in the context of a complete operating system. Linux is normally used in combination with the GNU operating system: the whole system is basically GNU with Linux added, or GNU/Linux. All the so-called “Linux” distributions are really distributions of GNU/Linux.
Based on MDGR (2006:96), in Linux design, Linux is like UNIX implementation nonmicrokernel. It is a multiuser system, multi tasking system that is compatible with UNIX. Linux system consists of 3 important parts: Kernel, Libraries and utilities.
a. Kernel
Based on syafii (2004:1), at the first time, Linux is a kernel made by Linus Torvalds, a student in Helsinky University, Finland.
the programs you use so they can communicate effectively and simply with your computer hardware.
Based on Stallman (1997), Linux is the kernel: the program in the system that allocates the machine's resources to the other programs that you run. The kernel is an essential part of an operating system, but useless by itself, it can only function in the context of a complete operating system.
Based on MDGR (2006:97), the Linux kernel forms the core of Linux operating system, it provides all functions to run process and provides system services to give the setting and the access protection to hardware. Kernel implements all needed features in order to be able work as operating system. Interface from operating system that is in running application is not managed by kernel, but the application make calls to libraries, then call operating system services that are needed.
put in /usr/src/linux/arch/i386/boot directory named zImage. Make modules ; make modules_install is to make kernel file module and do installation kernel module that will be put in /lib/modules directory.
b. Libraries Systems
According to MDGR (2006:97), system libraries provide kind of functions. In the lower-level, they allow application to ask request in system kernel service. Making a system-call involve transfer control from useless user mode to used user mode. Libraries duty to collect system-call argument ad manage those arguments in special form needed to do system-call.
Still based on MDGR (2006:97), Libraries also can provide more complex version from standard system-call, example, buffered function file-handling from C language. Libraries also provide sorting algorithm, mathematic function and string manipulation. All function needed to support UNIX application or POSIX is implemented in system libraries.
c. Utilities System
2.2 Core
According to Saxena (2010), Core OS Layer contains all the middleware/OS service domains and the hardware adaptation services. It includes the Linux kernel and all the middleware needed to define hardware and usage model independent API for building both native applications and web run time applications.
According to official apple, the core OS layer contains the low-level features that most other technologies are built upon. Even if you do not use these technologies directly in your applications, they are most likely being used by other frameworks. And in situations where you need to explicitly deal with security or communicating with an external hardware accessory, you do so using the frameworks in this layer,
2.3 Linux Live
According to Tomas (2011), Linux Live is a set of shell scripts allows you to create your own Live Linux from an already installed Linux Distribution. The Live system you create will be bootable from CD_ROM or a disk device, for example USB Flash Drive, USB Pen Drive, Camera connected to USB port, and so on. People use Linux Live scripts to boot Linux from iPod as well. Interesting feature of Linux Live Script:
1. Persistent changes
2.4 Router
Based on Dede (2010:25), router has ability to forward packet IP from one network to other networks that possible to have many routes among the routers. Router also can be used to connect some LAN, so the traffic from LAN can be handled. If two or more LAN connected to the router, every LAN consider as different sub network.
According to iwan (2009:58), a router has routing function. It means, router can know the route information (called packet) will be forwarded, whether the packet for host in same network or for host in different networks. If the packet is for a host in different networks, the router will forward to that network. If the packet is for a host in the same network, the router will block the packet to go out, so the packets will not “flood” to other networks.
According to Fathul (2001:240), router is a hardware that route data from LAN to cellular. Router is used to guarantee that only machine who has authority that can transmit data to LAN. Besides that, router is also used to check the error, save statistic the usage of network, and support firewall.
2.5 IP Address
2.5.1 IP address version 4 (IPV4)
IP address is a binary number 32 bit that is separated with a dot in every 8 bit. Every 8 bit is called octet. The addressing of IP in 32 bit consists of subnet address and host. The example:
11000000000010100001111000000010
The addressing of 32 bit is divided into four octets (8 bit per section): 11000000.00001010.00011110.00000010
Every octet is changed into decimal number become: 192.10.30.2
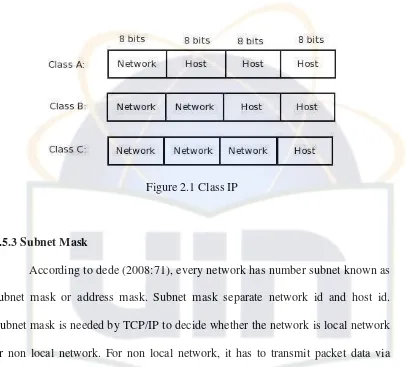
2.5.2 IP Class
According to Dede (2008:65), Ip address is grouped in 5 classes: class A, class B, class C, class D, and class E. The differences among 5 classes are in how big the network and the calculation of hosts. Class A is used in few networks, but the networks have many hosts. Class C is used in many networks but, only has few hosts. Class D and class E are not common to be used.
Figure 2.1 Class IP
2.5.3 Subnet Mask
255.255.254.0 /23
According to Dewi and Arie (2004), the objective of protocol routing is to get the best way from some routers networks through packet data from source network to destination network.
Based on Anjik and Rianto (2008:99), routing concept is a process to make a route to connect a network to others networks by using router. Data from a device connected to internet, defined by IP, is transmitted in datagram. Datagram has a destination IP address that will be checked by Internet Protocol to be transmitted to destination IP address. If source address information is in same network with the destination address, so the data will be transmitted directly, but if the destination address is in different networks, so datagram will transmit to the right network.
2.6.2 Static Routing
According to Anjik and Rianto (2008:102), static route is the routes to a host or destination network that are input manually by network administrator to router routing table. Static route defines next IP address hop router and inter local used to forward packet to the destination (next router hop). Static route has the advantage to save the network bandwidth because the static route does not make traffic route update-to give information the change of route that is applicable in other routers. But the static router use needs extra time in network management. This is because the administrator h to do update route table when there is the change of network configuration.
2.6.3 Dynamic Routing
Based on iwan (2009:515), dynamic routing is using routing protocol that can decide the route by itself based on every situation and condition. Dynamic routing is used to networks that have many routes. Dynamic routing is used by networks which are built by some routers. Every router will give information to the close router and then make routing table.
2.7 Iptables
Based on netfilter, iptables is the inter space command line program used to configure the Linux 2.4.x and 2.6.x Ipv4 packet filtering ruleset. Iptables is used to Network Address Translation too. The iptables package also includes ip6tables. Ip6tables is used for configurin the Ipv6 packet filter.
Based on Ahmad and Fanny (2005:68) iptables, there are 3 main labels: a. INPUT : packet data which come from our interfaces
b. OUTPUT : packet data which go out from our interfaces c. FORWARD: packet data which pass the route.
Based on Ahmad and Fanny (2005:71) the functions of iptables are: a. To limit the access our networks to certain traffic data.
b. To filter the attack from outside. c. To limit the access to our services. Packets shoulnot be filtered are:
a. ICMP packets b. TCP to DNS c. FTP data
Packets that must be filtered: a. Ping of death
b. Teardrop and Bonk (IP Defragmetation) c. Fragment Bomb (IP Fragment)
d. IP Spoof
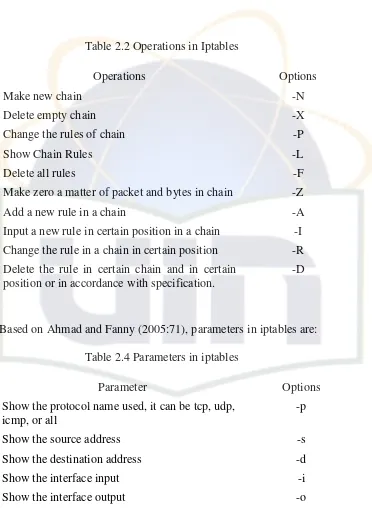
Table 2.2 Operations in Iptables
Make zero a matter of packet and bytes in chain -Z
Add a new rule in a chain -A
Input a new rule in certain position in a chain -I Change the rule in a chain in certain position -R Delete the rule in certain chain and in certain
position or in accordance with specification.
-D
Based on Ahmad and Fanny (2005:71), parameters in iptables are: Table 2.4 Parameters in iptables
Parameter Options
Show the protocol name used, it can be tcp, udp, icmp, or all
-p
Show the source address -s
Show the destination address -d
Show the interface input -i
Show the interface output -o
Example of using iptables. These commands were made in order all the first policy are DROP.
# iptables -P INPUT DROP # iptables -P OUTPUT DROP # iptables -P FORWARD DROP
The commands to forward packets from network A to network B via router are:
# echo 1>/proc/sys/net/ipv4/ip_forward
# iptables -A FORWARD -i eth0 -o eyh1 -j ACCEPT # iptables -A FORWARD -i eth1 -o eth0 -j ACCEPT The meaning of those commands are:
Make sure that forwarding table is active
Make network A can communicate with network B
Make network B can communicate with network A 2.7 Bash Scripting
2.8.1 Definition Shell
According to Rofiq (2003:7), shell is command interpreter language or a macro processor which run the command. Shell also can be a command-Interpreter that becomes user interface with the utilities and programming language. Shell can make a command or a file that contains commands itself. That new command has same status and is put in /bin directory.
2.8.2 Bourne Again Shell (/bin/bash)
According to Rofiq (2003:8), bash is one of shell. Bash is a development from Bourne Shell. Bash was developed by Brian Fox from Free Software Foundation. This shell has GNU copy left license so it is free used. Bash is more growing and it becomes as shell default for Linux operating system. Some interfaces: command line interface (CLI) and text user interface (TUI). In CLI, the user gives command with some arguments that sometimes make the user that is not used to use Linux feel afraid. In TUI, the user just run application and will face windows, dialog etc.
There are points in TUI Linux: a. Ncurses (library).
Ncurses is a library that provides API function, which is possible for a programmer to write text user interface by terminal independent. This is a toolkit to develop software “like GUI” that run in terminal emulator. Ncurses has ability to move the cursor, to make windows, to work in color, work using mouse etc. Today the ncurselibrary can be found in every almost GNU/Linux distribution.
b. Dialog (utility)
According to Jeff Tranter, dialog is a utility that provides the calling function for ncurses library, so the programmer can be easily to make a user interface in GNU/Linux system. Dialog was created by Savio Lam ad then modified by some developers. Dialog run under terminal emulator so it can be easily to use with bash scripting.
3 blue 2>/tmp/choice
3. Input boxes : to make an input box #!/bin/bash
dialog –inputbox “Enter you name:” 8 40 2>answer message box: to make message box
#!/bin/bash
dialog –title 'Messag' –msgbox 'Hello, world!' 5 20 4. text boxes
#!/bin/bash
1 386SX off \ developers can learn more about a problem or a solution to that problem. It allows users to explore and criticize proposed system before undergoing the cost of a full-scale development. The field of prototyping software system has emerged around two prototyping technologies, i.e., throwaway and evolutionary.
Still according to Aggarwal (2006:62), the benefit of developing prototype are:
1. Misunderstanding between software developers and and customers may be identified as the system functions are demostrated.
2. Missing user requirements may be detected.
3. Difficult-to-use or confusing user requirements may be identified and refined.
4. A working system is available quickly to demonstrate the feasibility and usefulness of the application to management.
5. The prototype serves as a basis for writing the specification of the system.
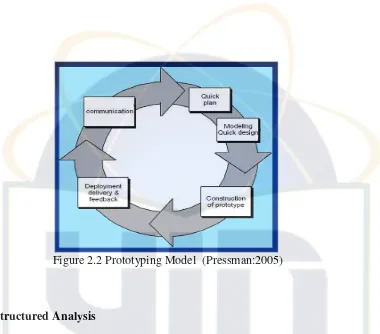
requirement. In other cases, the developer may be ensure of the efficiency of algorithm, the adaptability of an operating system, or the form that human/ machine interaction should take. In these, ad many other situations, a prototyping paradigm may offer the best approach. Prototyping process describe in four processes:
a. Communication
The software engineer and customer meet and define the overall objectives for the software, identify whatever requirements are known, and outline areas where further definition is mandatory.
b. Quick Plan and Quick Design
A prototyping iteration is palnned quickly ad modeling (in the form of a
“quick design”) occurs. The quick design focuses on a representation of those aspects of the software that will be visible to the customer/ end-user (e.g., human interface layout or output display formats)
c. Construction of prototype
The quick design leads to the construction of a prototype. d. Deployment delivery and Feedback
Figure 2.2 Prototyping Model (Pressman:2005)
2.11 Structured Analysis
The developer used structured analysis in analysis methodology. Based on Gunadarma (1995:29), structured approach need standard obvious procedure and collection data or at least need methodology that will be used in developing information system. Structured can decide the order and can increase the understanding capability in complex system. So that why structured is the main characteristic in information system. “Structured” can be related in the way and form preparation.
Jackson diagram, Warnier/Orr diagram, DFD, and structure diagram. Other tool
own data and processes). It’s common to think of software object as a robot, an
animal, or a little person: each object has certain knowledge, in the form of attributes, and it knows how to perform certain operations for the benefit of the rest of the program.
Based on O’Docherty (2005:4), object-oriented programming is programming using independent modules of data and functions that correspond to concepts in the problem domain, such as Customer or Scrollbar.
Still according to O’Docherty, an object-oriented program works by creating objects, connecting them together and getting them to collaborate by sending messages to each other.
2.13 Black-box Testing
fully exercise all functional requirements for a program. Black-box testing is not an alternative to white-box testing techniques. Ratjer, it is a complementary approach that is likely to uncover a different class of errors than white-box methods.
Still based on Pressman (2005:434), black-box testing attempts to find errors in the following categories: (1) incorrect or missing functions, (2) interface error, (3) errors in data structures or external data base access, (4) behavior or performance errors, and (5) initialization and termination errors. Black-box testing tends to be applied during later stages of testing. Because black-box testing purposely disregards control structure, attention is focused on the information domain.
2.14 VirtualBox
According to official website of VirtualBox, VirtualBox is a powerful x86 and AMD64/Intel64 virtualization product for enterprise as well as home use. Not only is VirtualBox an extreme feature rich, high performance product for enterprise customers, it is also the only professional solution that is freely available as Open Source Software under the terms of the GNU General Public License (GPL) version 2.
Server 2003, Vista, Windows 7), DOS/Windows 3.x, Linux (2.4 and 2.6), Solaris and OpenSolaris, OS/2, and OpenBSD.
CHAPTER III
RESEARCH METHODOLOGY
3.1 Research Method
This research used Prototyping Model as a system methodology. Based on study literature that has been done in chapter 2, there are some considerations why this research used Prototyping Model:
1. Misunderstanding between software developers and and customers may be identified as the system functions are demostrated.
2. Missing user requirements may be detected.
3. Difficult-to-use or confusing user requirements may be identified and refined.
4. A working system is available quickly to demonstrate the feasibility and usefulness of the application to management.
5. The prototype serves as a basis for writing the specification of the system. Prototyping Model steps are applied in the research:
a. Communication
portable router. For more details about data some routers, it put in 2.
Collecting data Method. b. Quick Plan and Quick Design
The implementation of this step in this research are design for the router itself and design for the interface that router. In the outline, the router design in this research consists of Linux kernel, system libraries, package management, system services, router application and interface.
The Linux kernel version used for the router is the Linux kernel version 2.6.27. Basic applications to build the function of router are route 1.98, iptables 1.4.10. Packages in this router must be compiled, so the developer will build the script to compile the packages in the router.
Interfaces that will be built are Text User Interface. The interfaces consist of setting IP address and routing. Those are interfaces to communicate between user and application. Beside that, interface to help user in doing installation.
Firstly, when the router will be installed, the router has to boot in hard drive, the hard drive can be flash disk or CD. The developer will build the script for booting. It still uses bash scripting.
c. Construction of prototype
In this step, the developer deployed the router and its interface based on the quick plan and quick design.
In this step in the research, the developer implement and evaluate the router that has been developed. The router will be tested to do its function and if there is error, the developer can fix the software.
Some functions of the router in this research that will be tested installation interface and configuration interface. Installation interface consist of hard disk installation and flash disk installation. Configuration installation consist of interface that has related with routing configuration.
3.2 Collecting Data Method
3.2.1 Method of Collecting Primary Data
Interview was used for collecting primary data. The developer interviewed one of lecture and one of a Cisco trainer in UIN Syarif Hidayatullah, Mr. Wahyudi, MT, CCNA. The interview was held on Tuesday, June 7th 2001. The discussion was about definition router and the function of the router in general. Mr. Wahyudi said that router is a device in layer 3. The function of router is for routing, beside that router can be used to choose the best paths. Firewall is important or not depends on the needs. In router itself, there is access list for firewall. In this router, the developer use iptables packet for firewall.
3.2.2 Method of Collecting Secondary Data
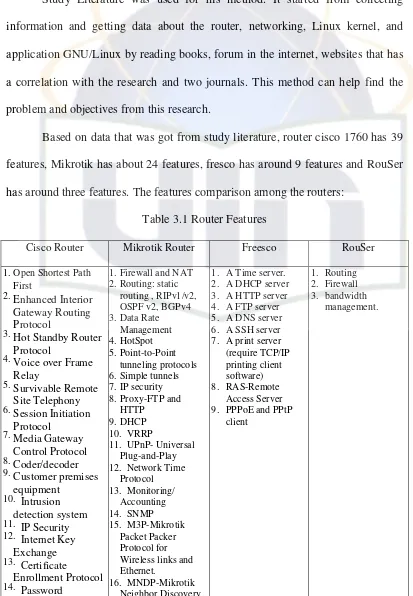
Study Literature was used for his method. It started from collecting information and getting data about the router, networking, Linux kernel, and application GNU/Linux by reading books, forum in the internet, websites that has a correlation with the research and two journals. This method can help find the problem and objectives from this research.
Based on data that was got from study literature, router cisco 1760 has 39 features, Mikrotik has about 24 features, fresco has around 9 features and RouSer has around three features. The features comparison among the routers:
Table 3.1 Router Features
Cisco Router Mikrotik Router Freesco RouSer
37. Network Address
The developer uses structured analysis in analysis methodology because structured analysis is simpler and programming language that is used in this research is structured programming. Besides that, bash scripting is still not be abe to do object-oriented because bash scripting is only shell script that use sytems utilities. The developer uses flowchart as a tool in this research because the flowchart model is easy to be understand, so that the ordinary user can understand and can give the idea for the prototype in the research. The developer implemented the structured analysis as analysis methodology in this research. Firstly, the developer decided the research method. This research used prototyping as the research method. The developer had considerations why this research had to use it. Some considerations using the prototyping model were flexible, be able produce the interactive user interface, and the user can join in developing in the research.
squid 3.1.11, and then squashfs to compress the data into lzm type, and packet dialog to build the interface and installation.
The algorithm that are needed in this research are about the installation, compiler and for user interface;setting IP program, routing program, and firewall. From algorithm, the developer will make the flowchart from each algorithms. So, this research will need 5 flowchart.
3.4 Testing Method
This research uses Black-box testing in testing method. Black-box testing is chosen as this method because it can be possible to detect the error in specification and compliance to requirements.
CHAPTER IV
4.1.1.1 Objectives of this research
After collecting information from the customer (in this case the customers are the lectures), interview and study literature (detailed in 3.2.2 Method of Collecting Secondary Data), the objectives of developing this routers are to develop a router that has basic routing function, portable (using flash disk), simple, open source, and has interfaces inside the system.
4.1.1.2 User Requirements
Based on information getting from study literature and interview, the function of router is for routing. In this research, the user requirements for the router are:
1) The router can do static routing. 2) The router is for IP version 4.
a. Installation to flash disk. For the input location of flash disk, the user still needs to input the partition that he has manually. The user choose the location of flash disk automatically.
b. Hard disk PC. The user input available hard disk that will be installed manually. The router cannot detect available hard disk yet.
4) Building the configuration Text User Interfaces
a. Interface for setting ip address. Setting IP interface include DNS and setting IP. After the user set up IP address, the user will be asked to input DNS directly.
b. Interface for routing. For this interface, the algorithm is still complex for routing algorithm.
5) Developing using Linux kernel. 6) All packets needed are open source.
4.1.2 Quick Plan and Quick Design 4.1.2.1 Quick Plan
After communication, the developer was doing quick plan. In the quick plan, there are 3 steps to develop the router. There are preparation, installation interfaces, and configuration interfaces.
1. Preparation
In the preparation step, the developer prepared the network topology. The topology of router is used as a guidance to test the router.
Figure 4.2 Topology
Besides preparing network topology, the developer also prepared what tools that are needed in the developing the router. Tools that are needed in developing the router are:
a) Core. The router uses core slackware. That core can be downloaded in http://www.slax.org/modules/1/dl/001-core.lzm.
c) Toroo live tools. It is used to make ISO image for the router. It can be downloaded in http://toroo.in/tools/toroo-live-tools-6.3.0.tar.gz.
d) Dialog source code v1.1. It is used for interface. It can be downloaded in
http://linux.softpedia.com/get/System/Software-Distribution/Dialog-7923.shtml.
e) Iptables. Iptables that is used is iptables version 1.4.2. It can be downloaded in http://www.netfilter.org/projects/iptables/files/iptables-1.4.2.tar.bz2.
f) VirtualBox. VirtualBox that is used is VirtualBox version 4.0.10. 2. Installation Interfaces
There are two kinds of installation in this router, installation in hard disk/PC and installation in flash disk.
Based on flowchart in Figure 4.3 about hard disk installation, the algorithms in hard disk installation are:
The program will ask whether the user want to create new partition or not.
If the user wants to create new partition, the program will show a help to help user in partition the hard disk.
If the user does not want to create partition, the program will ask the user to input partition to install the router.
The partition will be formatted by the program b) Flash disk Installation
The developer created the flowchart first before building the flash disk text user interface.
Based on Figure 4.4 Flash disk Installation Flowchart, The flash disk installer algorithm:
The program will show where the media or flash disk mounted.
The program will ask the user to input the flash disk location.
The installation process is running. The router system will be copied into flash disk or portable device.
The program will install boot loader to flash disk.
The program will set the flash disk, so that when the flash disk plug-in in the laptop, it will run directly.
3. Configuration Interfaces
The developers build two interfaces, setting IP interface and routing interface.
a) Setting IP
The algorithm for setting IP interface:
Setting looping to process inputting ip address, netmask, and interface. Looping is set until twice looping.
Declare the variables that are needed for setting IP.
The program will ask user to input the interface, IP address and netmask that will be set for the network.
Process looping occurs.
After that the user will be asked to set gateway ad DNS. b) Routing
The algorithm for routing:
The program will input interface router, IP addess router, netmask router, inerface client, IP address client, netmask client and then process it.
After that the routing program active ip forward.
The program will ask to input DNS and then restore DNS.
After that process routing will be running. 4.1.2.2 Quick Design
Quick design is used to give description how the interfaces appear. Quick design include interfaces that are built in the router. The interfaces that are provided in quick design are:
Interface installation hat include hard disk installation and flash disk installation
Configuration interfaces that include setting IP interface and routing interface.
1. Interface Installation
Figure 4.7 Choosing installation a) Harddisk Installation
If the user choose number one, the program run installation to the laptop or hard disk.
Figure 4.8 prototype1 model harddisk-1
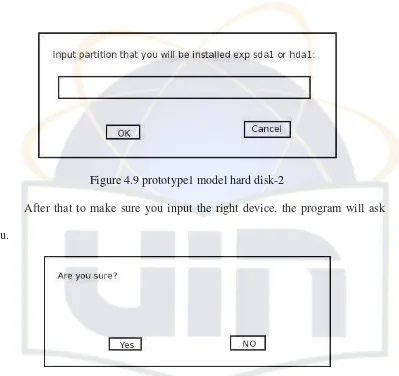
Figure 4.9 prototype1 model hard disk-2
After that to make sure you input the right device, the program will ask you.
Figure 4.10 prototype1 model hard disk-3 After that the process installation will be running. b) Flash disk Installation
When the user choose install on your flash disk, there is the information which devices that are connected into the computer.
When click Yes, the user will be asked to input the device of flash disk and when click No, it will cancel the installation.
Figure 4.12 prototype1 model flash disk-2
After input the device of flash disk, the router will be installing into flash disk.
2. Configuration Interfaces
As mentioned in quick plan, there are two configuration interfaces, setting IP and routing. After creating the flowcharts, it needed to create design how the interfaces appear to the users.
a) Setting IP
In setting IP address, firstly the user will be asked to input ethernet which will be set.
After that, the program will ask to input IP address.
Figure 4.14 prototype1 model setting IP-2
After inputting IP address, the user will be asked to input netmask.
Figure 4.15 prototype1 model setting IP-3
The program will do looping, so it will repeat from input ethernet, ip address, and netmask. After looping, the user can input gateway.
The last thing that the user should input is DNS. The program will show the interface to input DNS.
Figure 4.17 prototype1 model setting IP-5 b) Routing
When the user type command to call routing setting, it will show the information that inform the user if the routing will be started.
Figure 4.18 prototype1 routing model
4.1.3 Construction Prototyping
There are four steps in developing the first prototype router: 1. Install Toroo Live Tools
2. Compile Packet
4. Make ISO bootable
Here will explain step by step develop the router. 1. Install Toroo Live Tools
Toroo live tools is the tools to make and extract packet lzm. Packet lzm is used for management in router system.
extract that packet into folder /tmp go to folder Tools
make files in folder tools become be able to read, write, and execute.
copy all files into folder /bin
Figure 4.19 Toroo Live 2. Compile packet
Some packets need to be compiled to complete the modules that are needed to the router. There are two packet that will be compiled, dialog and iptables. Firstly, it needs to extract core to place the packets:
make directory for core in temporary directory.
extract core into core directory
After extract core, the next step is compiling the packets that are needed in developing the router.
Compile Dialog:
extract the source code of packet.
change directory where the packet extracted.
customize the configuration to check the dependencies.
compile the source code into binary.
install the packet to destination directory, here dialog will be installed in core directory: #make install DESTDIR=/tmp/core
Figure 4.21 Dialog Compile Iptables:
Extract the source code of packet.
Change directory where the packet extracted.
Customize the configuration.
Compile the source code into binary.
Figure 4.22 Iptables 3. Build Installer for the router
There are three main scripts in installer. A script as menu, a script for installation in hard disk PC and script for installing in flash disk. Only a script for menu that has to be packaged.
Menu script is used for the user when the user wants to choose in which device he want to install the router. This script will be put in /bin directory.
Make directory for the directory of script.
Write he script for this menu installer, save it. Here the developer saved it as setup-BS in directory that already made.
Package the directory into .lzm.
Figure 4.23 Installer 4. Make ISO bootable
additional packets that were added in router and menu installer. Boot directory consists of installer harddisk and boot loader. Installer flash disk is put outside the router directory and boot directory.
4.1.4 Deployment Delivery and Feedback
For the first prototype, the router will be tested using VirtualBox. ISO image will be boot in VirtualBox.
4.1.4.1 Deployment Delivery
For the first prototype, the developer tested the router in two parts. There are installation interface and configuration interface. In first prototype, installation interface consists of hard disk installation and flash disk installation. Configuration interface in first prototype only consist of setting IP.
1. Installation Interface
a. The steps to install in harddisk PC are:
Prepare VirtualBox: Create new virtual machine, set virtual machine with RAM 128MB and 512MB for virtual disk size, and add router ISO image to the storage so that virtual machine can be able to boot the router using ISO image.
Run VirtualBox
Figure 4.24 Test1 install Hard disk-1
When it was chosen RouterOS Install, there were choices to install router in laptop or in flash disk.
Figure 4.25 Test1install hard disk-2
Figure 4.26 Test1install hard disk-3
When YesRun CFDISK was chosen, the user created partition.
Figure 4.27 Tes1install hard disk-4
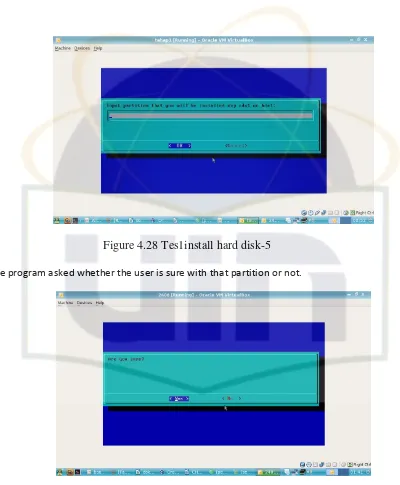
Figure 4.28 Tes1install hard disk-5 The program asked whether the user is sure with that partition or not.
Figure 4.29 Test1install hard disk-6
When Yes was chosen, the router was installing. When No was chosen, the router entered live CD mode.
b. The steps to install in Flash disk are:
storage so that virtual machine can be able to boot the router using ISO image.
Run VirtualBox
First thing that appeared was choosing whether want to install router or try live CD.
Figure 4.30 Test1 install Flash Disk-1
When it was chosen RouterOS Install, there were choices to install router in laptop or in flash disk.
When Install on you Flash disk was chosen, it showed the information what devices that connected to the laptop.
Figure 4.32 Test1 install Flash Disk-3
When No was chosen the program was out. When Yes was chosen, the program asked to input where the flash disk mount.
Figure 4.33 Test1install Flash Disk-4
Figure 4.34 Test1 install Flash Disk-5 2. Configuration Interface
Setting IP
The developer already finished build setting ip script interface, but it was not put in the router system. Setting IP script interface was tested via terminal.
Run setting IP script in terminal. The user was asked to input ethernet that want to be configured.
After that, the interface to input ip address was showed.
Figure 4.36 Test1 setting IP-2
After input IP address, the program asked to input netmask.
Figure 4.37 Test1 Setting IP-3
Figure 4.38 Test1 Setting IP-4
Figure 4.40 Test1 Setting IP-6
After that, the user was asked to input gateway.
Figure 4.41 Test1 Setting IP-7
Figure 4.42 Test1 Setting IP-8 4.1.4.2 Feedback
Based on the testing and the construction prototyping, the router still did not run based on what the customer expected in communication. For the first prototyping, the router only could run installer using Text User Interface. It could not set IP address using Text User Interfaces and still could not do routing using text User Interfaces.
According to the customers, there are some requirements for the next router:
1) The interface program has to detect the partition automatically.
2) The interface program has to be able to detect the ethernet interfaces automatically.
3) The router has to have menu so that the user can choose which configuration he wants.
4.2 Second Prototype
The second prototype was made based on the feedback from the customers.
4.2.1 Communication
In communication for second prototype, objectives of the research are still same as First Prototype. But for the user requirement, there is additional user requirement for the Second Prototype. The user requirements for the Second Prototype are:
1) The router can do static routing. 2) The router is for IP version 4.
3) Building the installation Text User Interface:
a. Installation to flash disk. In installation flash disk, the user can choose the location of flash disk automatically, so that the user does not need to type manually.
b. Hard disk PC. The program can detect the partition of hard disk automatically that will be installed for the router.
4) Building the configuration Text User Interfaces
a. Interface for setting ip address. The program can detect the Ethernet that are available in the computer installed the router.
b. Interface for routing. The user just chooses Ethernet that will be used for routing and then the routing process will be running.