57
LAMPIRAN 1
DAFTAR PUBLIKASI
ILMIAH PENULIS (TESIS)
No. Judul
Artikel
Penulis
Publikasi
(Seminar – Jurnal)
Tahun Tempat
1. Generating
strategic IS:
Towards the
winning strategy
Maria Elfida,
dan
Mahyuddin K.
M. Nasution
Cornell University
Library
(CUL) –
(Jurnal)
Diindeks oleh
arXiv:1212.1882
dan DBLP
2012 USA
3. Pemodelan
sistem pakar
untuk
mendeteksi
kerusakan pada
komputer
dengan metode
forward
chaining
Maria Elfida,
dan
Mahyuddin K.
M. Nasution
Prosiding Seminar
Nasional Teknologi
Informasi &
Komunikasi
(SNASTIKOM),
Vol. 1: 3-15-3-18.
ISBN
978-602-19837-2-0
2013 Medan
3. Terrorist
network:
Towards an
analysis
Mahyuddin K.
M. Nasution
dan Maria
Elfida
Cornell University
Library
(CUL)
(Jurnal)
Diindeks oleh
arXiv:1302.1727
dan DBLP
58
LAMPIRAN 2
TABEL-TABEL KONTINGENSI
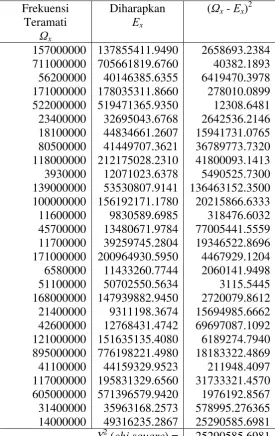
Tabel B2.1.
Hitungan chi-square untuk faktor organisasi.
Frekuensi
59
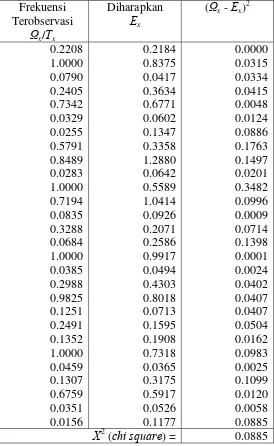
Tabel B2.2.
Hitungan chi-square untuk faktor organisasi secara probabilitas relatif.
LAMPIRAN 3
TABEL HASIL MESIN CARI YAHOO!
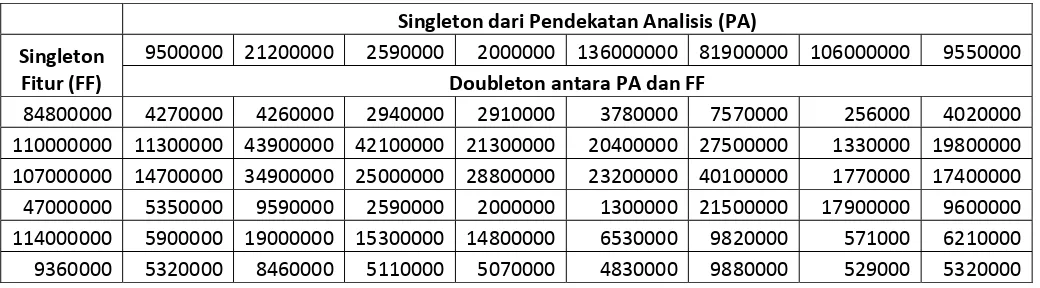
Tabel C3.1.
Singleton dan doubleton untuk Pendekatan Analisis dan Fitur
Singleton
dari
Pendekatan
Analisis
(PA)
Singleton
Fitur
(FF)
9500000
21200000
2590000
2000000
136000000
81900000
106000000
9550000
Doubleton
antara
PA
dan
FF
84800000
4270000
4260000
2940000
2910000
3780000
7570000
256000
4020000
110000000
11300000
43900000
42100000
21300000
20400000
27500000
1330000
19800000
107000000
14700000
34900000
25000000
28800000
23200000
40100000
1770000
17400000
47000000
5350000
9590000
2590000
2000000
1300000
21500000
17900000
9600000
114000000
5900000
19000000
15300000
14800000
6530000
9820000
571000
6210000
61
LAMPIRAN 4
SURVEI
1.
Pelaksanaan survei:
Survei tentang sistem informasi dilakukan pada
Tempat
: Jurusan Sistem Informasi Strata 1
Sekolah Tinggi Teknik Harapan (STTH)
Medan
Bulan
:
Oktober
2013
2.
Metode Pelaksanaan:
Pelaksanaan dilakukan pada setiap kelas kuliah yang asuh oleh penulis. Kelas
kuliah adalah kelas tingkat akhir, yang telah melewati mata kuliah yang
berkaitan dengan sistem informasi seperti
a.
Konsep Sistem Informasi
b.
Analisis dan Rancangan Sistem
c.
Manajemen Projek Sistem Informasi
d.
Dan beberapa mata kuliah yang berkaitan dengan internet dan Web.
Tabel D4.1.
Jumlah responden setiap kelas.
Kelas Jumlah
responden
I
II
III
IV
12 orang
13 orang
23 orang
13 orang
62
terhadap jumlah peserta setiap kelas untuk setiap butir pertanyaan dari
konstruk. Jumlah peserta setiap kelas seperti Tabel D4.1 (Lampiran 4).
arXiv:1212.1882v1 [cs.OH] 9 Dec 2012
Generating Strategic IS: Towards the Winning
Strategy
Maria Elfida1⋆ and Mahyuddin K. M. Nasution1,2
1Program S2 Teknik Informatika, FASILKOM-TI,
Universitas Sumatera Utara, Padang Bulan 20155 USU, Medan, Indonesia. 2Departemen Teknologi Informasi, FASILKOM-TI,
Universitas Sumatera Utara, Padang Bulan 20155 USU, Medan, Indonesia. [email protected],[email protected]
Abstract. In modern era, the role of information system in organiza-tion has been taken many discussions. The models of informaorganiza-tion system are constantly updated. However, most of them can not face the chang-ing world. This paper discusses an approach to generatchang-ing of strategic information system based on features in organization. We proposed an approach by using disadvantages in some tools of analysis whereby the lack of analysis appear as behaviour of relation between organisation and the world.
Keywords: Information system, information technology, feature, orga-nization, knowledge
1
Introduction
The success of information system (IS) has been one of themes in many discus-sions in the past two decades [1,2]. The rapid growth in the use of information systems has led to several changes in the workflow of both the private and public sectors, mainly about providing the units for working, servicing, implementing all works in environment of information technology [3]. A change is to compete with one another. The changes are as attempts to develop efficiency services, improved products, and better systems. The change for other changes, that to be the implementation of and use for what do the information technology is constantly changing. An information system is always by means of the concept, planning, design, implementation, and use of advanced technology either from the beginning or the capacity for self-upgrading and self-updating. Why are so many implementations and information systems created and so few used? Should information system be something strategic, so how?
A strategic information system is an information system for helping to over-come the problem of inefficient public service and information delivery in the public sector [4] by using the information technology effectively. The informa-tion system thus has been identified as vital in order to avail continually be
2 M. Elfida dan M. K. M. Nasution
available to generate the services. The Information system is critical in this age whereby the knowledge has been a part of ubiquitous of environments and their strategies, the knowledge as resources of competence. However, there is little attention about the study of information system as strategic factor to an en-vironment such as enterprise, organization, or special in Indonesia. We assure that the competence will become an important part of information system, and to support the achievement towards ”the winning strategy”. This paper aims to address an approach to identify strategic information system for an organization in a changing world.
2
Related Work
Generating Strategic IS: Towards the Winning Strategy 3
gray (from dark to light or light to dark) is as the contribution levels. There-fore, we proposed an approach to address the changing an information system becomes strategic information system.
3
The Proposed Approach for Generating Strategic
Information System
Each organization as a system exists in an environment, i.e., a world that consists of classes of knowledge [15]. Therefore, an organization has something in isolation and also things in sharing. An organization starts with idea, concept, vision and mission, whereby the organization achieves its objectives, but an organization is always in a predictable path, going on achievements and performances. A world can be considered a space of event whereby an organization will connect to any event, each event can measure in either discrete or continue. An event can be recognized clearly as a number, a count, or a value, but sometimes it can not identified. An event sometimes depends on another event. The both events have any relation. Let us model an organization as a set of entities, then entities exists in both an organization and a world, and therefore each entity has the stable attributes and the flexible attributes. Thus, the event can be considered as uncertainty for some situations and can be measured by the probability [16]. Therefore, we group the features of information system into six categories as the beginning of analysis, i.e. an approach that classifies the features into internal, external, quantitative, qualitative, history, and forecasting categories, where each feature is potentially same opposition to core, to generate a strategic information system, based on a comprehensive view, scope of data/information, mechanisms, definiting requirements, high level goal and knowledge-oriented paradigm.
Some features internally in organisation as the advantage and if we confront them to organisation’s environment will be the complex situation. Size of or-ganization become bigger if the oror-ganization was expanded area of its colonies, the branches is needed to represent organization, and then information system is one panacea to control all resources in organization, but when the organiza-tion take a system to supervise all, the organizaorganiza-tion increasingly exposed to the world and it is most difficult to control them. In strategic information system, the system needs to define the internal features of organization as a basic modal in information system for facing an environment and also the system needs to identify the external features from outside as input for defending own self from an attack. As a strategy, the organization must know that the internal and the external features have relationship, and the relation between them always hidden in background of organization or the features. Each feature has the latent threat in relations. Therefore, each strategic information system requires the support in multi level analysis, the information/data modelling, and the background of knowledge in having sound theoretical basis. In this case, a comprehensive view of organization requirements will capture requirements of information system.
4 M. Elfida dan M. K. M. Nasution
other infrastructures of multimedia. However, other features we can identify only through stable attributes of another feature in their relations. An information model should take an embraced view to conceptualize the requirements from data to knowledge in order to an environment can be determine existing organi-zation uniquely with information system. There are many features in qualitative condition and this is most subjective, because the values of them depend on the exercise of members in organization or they are outside. Therefore, requirements about data/information must cover in wider scope.
The important feature comes and goes based on time in a timeline of organi-zation. The robust feature always exist, and it as a core in information system. The core of feature is a benchmark for evaluating the information system while other features are the constraints for supporting the forecasting. Some tools in statistic and optimization are the best assistants to measure the importance of features and their relations. The strategic information system must enable to generate the temporary situations of organization and predictable some the choices as solution. In the system therefore there is a mechanism to address the complex situation of an organization whereby the organization regenerate high level goal for learning to the strategic information system.
The features are phenomena about organization and information system is a paradigm for understanding the phenomena, but in some conditions not each paradigm enable we use to understand any phenomena, there is a bridge the gap always exists between them. Anyway, everything has limitations, only hu-man with their knowledge has a container of the strategy making. A strategic information system therefore must support knowledge-oriented paradigm, i.e. a system based on knowledge in overall of system as a winning strategy.
4
Conclusion and Future Work
The strategic information system can be generated based on an approach with six advantages of data as basic modal of organization to face the change world. The approach implicitly covers all attributes and values of features to take the implications for getting the winning strategy. Our near future work is to develop a framework to generate the background of knowledge about strategic information system.
References
1. W. H. DeLone and E. R. McLean, Information system success: The quest for the dependent variable. Information System Research 3(1) (1992) 60-90.
2. W. H. DeLone and E. R. McLean, The DeLone and McLean Model of Information System Success: A Ten-year update. Journal of Management Information Systems 19(4) (2003) 9-30.
Generating Strategic IS: Towards the Winning Strategy 5
4. Nigel Melville, Kenneth Kraemer, and Vijay Gurbaxani, Review: information tech-nology and organizational performance: an integrative model of it business value. Journal MIS Quarterly 28(2) (2004) 283-322.
5. Dennis F. Galletta and Albert L. Lederer, Some cautions on the measurement of user information satisfaction. Decision Sciences 20(3) (1989) 419-434.
6. Mahyuddin K. M. Nasution and Shahrul Azman Noah, Superficial method for ex-tracting social network for academics using web snippets. Rought Set and Knowl-edge Technology, LNAI 6401 (2010) 483-490.
7. Mahyuddin K. M. Nasution, Shahrul Azman Noah and Saidah Saad, Social network extraction: Superficial method and information retrieval. Proceedings of Interna-tional Conference on Informatics for Development (ICID’11) (2011).
8. Luis F. Luna-Reyes, Jing Zhang, J. Ramon Gil-Garcia and Anthony M. Cresswell, Information systems development as emergent social-technical change: a practice approach. European Journal of Information Systems 14 (2005) 93-105.
9. G. N. Mentzas. Implementing as IS Strategy - A team approach. Long Range Planning 30(1) (1997) 84-95.
10. J. Rockart. Chief executives define their own data needs. Harvard Business Review 57(2) (1979) 215-229.
11. J. Ward and J. Peppard. Strategic planning for information systems. John Wiley & Sons Ltd, Chichester, 2002.
12. W. Robson. Strategic management and information systems: An integrated ap-proach. Pitman Publishing, Greate Britain, 1994.
13. G. B. Davis. Strategis for information requirements determination. IBM System Journal 27(1) (1982) 4-30.
14. M. E. Porter. Competitive strategy: Techniques for analysing industries and com-petitors. Free Press, New York, 1980.
15. Mahyuddin K. M. Nasution. Theory of sharing knowledge: An Introduction. Bul-letin of Mathematics, to print.
Seminar Nasional Teknologi Informasi dan Komunikasi (SNASTIKOM 2013) ISBN 978-602-19837-2-0
3-15 Artificial Intelligence
Pemodelan Sistem Pakar Untuk Mendeteksi Kerusakan Pada Komputer
dengan Metode Forward Chaining
Maria Elfida1)danMahyuddin K. M. Nasution2)
1)Jurusan Sistem Informasi Sekolah Tinggi Teknik Harapan Medan 2)Program Studi Teknologi Informasi Fasilkom-TI Universitas Sumatera Utara
[email protected], [email protected]
Abstrak
Sistem pakar telah menjadi bagian dari banyak pembuat keputusan, tetapi sistem pakar juga tidak bergantung kepada pakar saja, tetapi melibatkan kilas balik dari pengguna, dan melibatkan informasi yang terdapat dilingkungan sebagai basis pengetahuan. Oleh karena itu, suatu sistem pakar melibatkan semua ini untuk membangun aturan-aturan yang mungkin diberlakukan dalam pendeteksian kerusakan komputer. Aturan yang mungkin dijalankan menggunakan metode Forward Chaining.
Kata kunci : gagal-fungsi, perangkat keras, perangkat lunak.
1. Pendahuluan
Pada saat ini, komputer telah menjadi perangkat yang sangat penting untuk mendukung aktivitas manusia. Komputer tidak hanya digunakan sebagai sarana utama banyak pekerjaan, tetapi menjadi infrastruktur bagi interaksi antara manusia. Komputer berperan dalam banyak bidang, komputer digunakan sebagai sarana hiburan seperti memainkan dan mendengarkan musik, membuat dan memainkan permainan (game) atau menjalankan aplikasi yang dianggap menarik. Walaupun komputer telah diadaptasi sesuai dengan sifat dan kebutuhan manusia tetapi pada hakekatnya komputer tetap menjadi alat yang terus-menerus dipengaruhi oleh lingkungannya (Mahfudz et al. 2013), memiliki kemampuan terbatas dari sudut fisik, mengalami kemunduran, tidak up-to-date terhadap perkembangan teknologi, dan kemudian tidak dapat digunakan lagi. Gagal-fungsi suatu komputer disebabkan perangkat keras dan perangkat lunak, kemudian oleh keperluan dan keinginan pemakai sebagai brainware. Oleh karena itu, pengembangan sistem pakar memerlukan suatu pemodelan untuk mendeteksi aturan pendeteksian kerusakan yang mungkin terjadi berdasarkan konsultasi pakar dan pemakai. Dengan melibatkan, metode forward
chaining, sistem pakar diadaptasikan untuk
menentukan suatu kerusakan pada komputer.
2. Istilah, Batasan dan Karakteristik
Kecerdasan buatan salah satu bidang dari teknologi informasi yang bertujuan untuk mengadap-tasi kemampuan nalar manusia kepada mesin seperti komputer. Manusia mampu memikirkan segala hal, menstrukturisasi informasi menjadi data terstruktur, mensistematiskan melalui rumus yang bersifat abstraks dari konsep yang luas dan terdeskripsi, tetapi tidak mampu menyelesaikan persoalan dengan timbunan data yang sangat besar, sedangkan komputer sebaliknya. Jadi, aktivitas manusia yang telah dirumuskan diangkat ke dalam komputer agar komputer mampu melakukan tugas itu, menirukan kemungkinan penalaran, penglihatan, pembelajaran, pemecahan masalah, sampai kepada pemahaman tentang sesuatu secara semantik.
2.1 Komputer
Gagal-fungsi sebuah komputer berasal dari dua kemungkinan, yaitu lingkungan dan komputer itu sendiri. Lingkungan boleh jadi karena sebab pengaruh lingkungan secara fisik ataupun lingkungan pemakaian. Fisik komputer rentan terhadap berbagai faktor, air dan udara yang menyebabkan munculnya arus pendek dalam komponen komputer secara elektronik. Misalnya, lingkungan yang mengandungi kelembatan tinggi menyebabkan komputer mudah lembab, apalagi udara menghantar debu, perubahan cuaca sebagai pemicu. Lingkungan pemakaian berkaitan dengan pemakai, tatacara pemakaian yang mungkin berbenturan dengan sifat-sifat fisik dari komputer, seperti mengetik dengan komputer sambil merokok dan makan.
Seminar Nasional Teknologi Informasi dan Komunikasi (SNASTIKOM 2013) ISBN 978-602-19837-2-0
3-16 Artificial Intelligence
Pola-pola kerusakan komputer sebenarnya dapat ditentukan berdasarkan cara pemakaian dan posisi pada lingkungan. Setiap pola dapat dirumuskan ke dalam aturan tertentu yang membantu dalam implementasi (Lai et al. 2006).
2.2 Kecerdasan buatan
Banyak penerapan kecerdasan buatan telah dilakukan, saat ini hampir kepada semua bidang yang terkait dengan pengolahan data agar menjadi informasi, kemudian menjadi pengetahuan, pengetahuan digunakan untuk membuat keputusan atau suatu kebijakan, misalnya seperti sistem robot bermain sepak bola. Namun begitu, kecerdasaran buatan hanya akan menyelesaikan permasalahan kompleks dengan mendayagunakan komputer. Salah satu penerapan kecerdasan buatan untuk membuat keputusan adalah sistem pakar.
2.3 Sistem pakar
Sistem pakar adalah suatu implementasi yang dikembangkan berdasarkan strategi heuristik: aturan yang dibuat oleh manusia untuk mendekati berbagai persoalan secara khusus, dengan mempertimbangkan pengetahuan yang telah ada. Sistem pakar mempu-nyai sifat-sifat berikut: (1) Terdiri dari informasi yang handal, yang didukung adanya langkah-langkah dalam menjawab pertanyaan, termasuk pertanyaan tentang proses; (2) Fasilitasi modifikasi, dengan melibatkan operasi penambahan dan penghapusan, kemampuan yang berasal dari pengetahuan basis; (3) Heuristik dengan latar belakang pengetahuan yang tidak sempurna dengan mana penyelesaian didapatkan; (4) Fleksibel digunakan dalam berbagai jenis komputer; dan (5) Adanya adaptasi sebagai kemampuan (Cowan, 2001).
2.4 Struktur Sistem Pakar
Struktur pembangunan sistem pakar dibagi menjadi dua bagian utama yaitu lingkungan pengambangan dan lingkungan konsultasi. Struktur pertama berkaitan dengan pembangunan sistem pakar, dengan mana pengetahuan pakar dimasukkan ke dalam lingkungan sistem pakar, sedangkan struktur kedua digunakan untuk jasa konsultasi untuk mendapatkan pengetahuan pakar.
Bangunan sistem pakar terdiri dari komponen-komponen yaitu (1) antarmuka pemakai, (2) basis pengetahuan, (3) mekanisme inferensi, (4) memori kerja, (5) Kemudahan penjelasan, (6) Kemudahan akuisisi pengetahuan
Antarmuka pemakai, suatu mekanisme berkaitan dengan aktivitas komunikasi pemakai dan sistem pakar. Penerimaan informasi dari pemakai menjadi bagian utama dari antarmuka, mengubahnya menjadi bentuk yang dapat diterima, untuk selanjut-nya menyerahkanterimakanselanjut-nya dengan antarmuka agar dapat diterima oleh pemakai. Selalu bagian antarmuka didukung oleh adanya dialog, yang menjadi bagian hadapan daripada antarmuka. Oleh karena itu, informasi perlu diterima dan diberikan dengan baik dan efektif melalui antarmuka ramah pemakai
Pada era modern, pengetahuan menjadi banyak basis bagi sebarang sistem, terutama sistem pakar, karena tanpa itu sebarang sistem tidak akan dapat menghadapi tantangan perubahan dengan mudah. Bagaimanapun, suatu sistem pakar disusun dari fakta dan aturan. Setiap fakta mengandungi informasi tentang objek yang perlu dipertimbangan dan mendukung tindakan yang akan dilakukan. Aturan adalah kendali tindakan yang akan dilakukan itu. Jadi, arsitektur sistem pakar akan tergantung kepada pengetahuan sebagai kunci kekuatan, yang memerlukan kepastian dan lengkap, menyempurnakan ketidaklengkapan, mendeskripsikan hal-hal tertentu, fleksibel atau mudah diubah bergantung kepada keperluan, dan jelas.
Penalaran atau kemampuan berpikir dari sistem pakar melibatkan strutur endali, penafsiran aturan, atau mesin pemikir, yang disebut sebagai otak suatu sistem pakar. Otak ini melibatkan konsep runut balik, suatu metodologi pelaksanaan suatu penyelesaikann berdasarkan pengetahuan ke dalam tempat kerja, untuk kemudian disimpulkan. Setiap bagian ini mempunyai perintah yang dipatuhi oleh sistem. Oleh karena itu, pemilikan tindakan didasarkan kepada penjenjangan yang diagendakan.
Fakta memerlukan tempat, seperti halnya data memerluan storage. Fakta dapat dijadian rujukan, tapi juga memerlukan proses, dan menghasilkan fakta baru. Fakta baru ini sebagai hasil diagnosis, boleh berupa tindakan atau hanya akibat.
Penjelasan dilakukan oleh otak sistem pakar, dan mencerminkan proses penalaran seorang pakar. Dalam hal ini, konsultasi terjadi bagi pemakai yang bukan pakar, tetapi sistem kemudian menjadi lebih cerdas dengan melakukan pembelajaran terhadap fakta lama dan baru.
Seminar Nasional Teknologi Informasi dan Komunikasi (SNASTIKOM 2013) ISBN 978-602-19837-2-0
3-17 Artificial Intelligence
Adanya, fungsi yang melakukan perubahan atau transformasi dari sesuatu yang tidak dimengerti komputer menjadi dapat diolehnya, sesuatu yang tidak dikenali oleh manusia, menjadi bagian darinya dengan baik.
2.5 Metode Forward Chaining
Metode ini adalah salah satu dari dua metode utama dalam kecerdasan buatan, yang dapat dideskripsikan secara logika. Misalnya, untuk aturan sederhana tentang kerusakan komputer: Jika x adalah kerusakan dan arus listrik tidak ada – lalu x adalah komponen. Jika x adalah kerusakan dan arus listrik ada – lalu x
adalah bukan komponen. Jika x adalah komponen – lalu x diganti. Jika x adalah bukan komponen – lakukan deteksi lain.
Aturan penyimpulan ditentukan dengan strategi implementasi forward chaining, yaitu data disediakan dan aturan kesimpulan digunakan untuk mengekstrak data lain hingga dicapai sasaran.
3. Pemodelan Sistem Pakar
Sistem pakar adalah sistem yang berkaitan dengan pakar dan objek yang menjadi sasaran dari sistem pakar. Oleh karena itu, sistem pakar untuk objek pendeteksian kerusakan komputer berkaitan dengan dua borang yang digunakan untuk konsultasi: Borang pakar dan borang pemakai.
Borang pakar digunakan oleh pakar dengan tujuan memperbaharui fakta dasar di dalam pangkalan data, sedangkan borang yang lain berkaitan dengan sajian informasi fakta tetapi juga dapat menempatkan komentar dan pengalaman pemakai, sehingga pakar dapat mempertimbangkan kasus bersifat khusus, atau tidak terekam dalam fakta.
Suatu sistem pakar melibatkan pangkalan data, untuk menyimpan fakta, data dasar seperti informasi komputer tertentu, dan informasi lain yang mungkin ada dari berbagai sumber. Biasanya, informasi yang tidak terstruktur disimpan dalam berkas khusus seperti berkas teks.
Perancangan sistem pakar berbeda dari sistem informasi biasa, apalagi sistem berbasis pengetahuan. Perancangan ini tergantung kepada pemodelan, penentuan hubungan antara beberapa komponen yang melibatkan masukan dari pakar dan kilas balik dari pemakai (Mahyuddin dan Noah, 2010). Setiap komponen memiliki bobot yang kemudian menghasilkan bobot hubungan yang mungkin terjadi antara komponen itu. Model akan menjadi satu fungsi yang melibatkan peubah bebas dan peubah tetap. Namun begitu, selalu bahwa masukan dari pengguna
dibakukan dengan cara mengeliminasi beberapa hal yang tidak terkait dengan karakteristik sistem pakar, setelah itu menjadi bahan perbandingan kepada masukan dari pakar. Penilaian dapat dilakukan sehingga diperoleh presisi pemodelan dan keakuratan informasi tentang sistem pakar.
Aturan yang telah dicipta berdasarkan pakar akan dibandingkan dengan pengalaman pengguna. Tujuannya adalah untuk menilai sistem pakar yang akan dikembangkan. Namun begitu, beberapa aturan dasar juga diperoleh dan dikembangkan berdasarkan nalar yang berlaku sebagai hukum di alam. Aturan ini, menjadi umpan balik untuk mensahihkan aturan yang diberlakukan di dalam sistem pakar pendeteksian kerusakan komputer. Semua aturan ini disusun berdasarkan metode Forward Chaining.
4. Penutup
Pemodelan sistem pakar dibangun dari aturan-aturan yang berbeda: pakar, pengguna, dan lingkungan sistem pakar. Semua aturan ini dibakukan sesuai dengan metode yang akan digunakan, dan kemudian dibandingkan untuk menilai dan mensahihkan sistem pakar untuk keperluan tertentu, termasuk untuk mendeteksi kerusakan pada komputer.
DAFTAR PUSTAKA
[1] Mahfudz, S., Nasution, M. K. M. dan Nasution, S., Knowledge sharing: a model, Cornell University Library, 2013.
[2] Nasution, M. K. M. dan Noah, S. A., Superficial method for extracting social network for academics using web snippets. Rough Set and Knowledge
Technology, LNCS Vol. 6401, Springer-Verlag:
483-490, 2010.
[3] Lai, Y., Li, X., Xiong, Y., dan Du, P., Design of an efficient intelligent instrument fault diagnosis expert system. Computational Engineering in Systems Applications (CESA), Beijing, China, 2006.
arXiv:1302.1727v1 [cs.SI] 7 Feb 2013
Terrorist Network: Towards An Analysis
Mahyuddin K. M. Nasution1)⋆ and Maria Elfida1)
1)PS Sistem Informasi, STTH, Medan, Sumatera Utara, Indonesia
[email protected] [email protected]
Abstract. Terrorist network is a paradigms to understand the terror-ism. The terrorist involves a lot of people, and among them are involved as perpetrators, but on the contrary it is very difficult to know who they are caused by lack of information. Network structure is used to reveal other things about the terrorist beyond the ability of social sciences.
Keywords: Social network, data, information structure, investigation, generator.
1
Introduction
The network is one of defining paradigms in modern era, or as concept for un-derstanding the phenomenon in world [1]. The most be noticed phenomenon is what we called as terrorism. As social phenomena, always, there is no single definition of terrorism that commands full international approval [2], but FBI define it as action of ”the use of serious violence against persons or property, or threat to use such violence, to intimidate or coerce a government, the public or any section of the public, in order to promote political, social or ideological objectives” [3].
In social network, the terrorism is a important study since 9/11 twin tower attack [4]. Social network analysis as knowledge extraction from graph is the study of mathematical models for interaction among persons, groups, or organi-zations [5]. The popularity of this study because the salience of the connections among terrorism actions. Thus, to find out the relations between actors of ter-rorism be important to do the counter of terter-rorism actions. Therefore, our goal is to describe some aspects of terrorist network. In the section of history: towards a motivation we discuss that historically the terrorist network is interaction of group people. Network Data and Investigation Section describes how to connect one with the other terrorist. Last section we describe a model of optimal network.
2
History: Towards a Motivation
Currently there is a modern issue, an intelligence agency is investigating gen-eral trends in terrorist activities all over the world. In the literature, initially
2 M. K. M. Nasution & M. Elfida
emerged as a form of political expression, terrorism dates back to 6 A.D. when Jewish patriots opposed to Roman rule in Palestine, organized under the name of Zealots and launched a terrorist campaign to drive Romans out of Palestine [6,7]. Terrorism recurred from 116-117 A.D. and again from 132-135 A.D. until the Jewish population was driven out of Rome. The term did not officially enter political vocabulary until the 18th century, when Edmund Burke criticized the ”reign of terror” following the 1792-94 French Revolution, when the French gov-ernment used systematic terror to intimidate and eliminate its enemies [8,6]. On and off, the use of terrorism can be traced to presented day. In 20th century, the activity of international terrorism increased rapidly during the late 1960s and early 1970s, but after a brief quietness, the 1980s began and ended with terrorist violence until beginning of this century. By the end of the decade, terrorism has become commonplace [9,10]. Comparatively fewer terrorist incident have been recorded for the first half of the 1990s. However, their nature and magnitude are not easily comparable to those of past years events as indicated by the US Department of State. Like that, terrorists in the modern era has always been as-sociated with Jewish and Zionist. Therefore, the US Department of State defines terrorism as ”... premeditated, politically motivated violence perpetrated against civilians and unarmed military personnel by subnational groups ... usually in-tended to influence an audience.”; and international terrorism as ”...involving citizens or the territory of more than one country” [11].
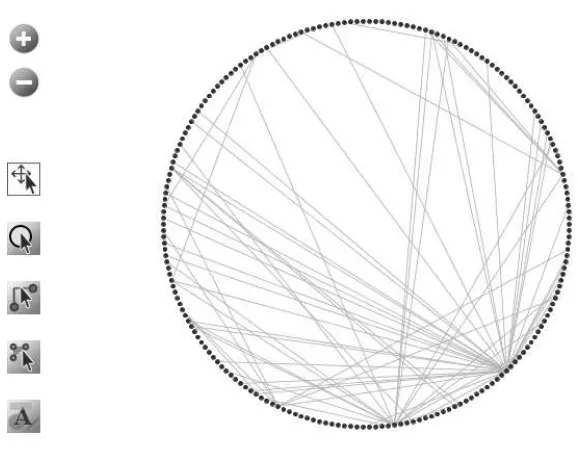
For example, as organization, Jemaah Islamiyah (JI) started as an Indonesian Islamist group and is a loosely structured organization characterized by territo-rial divisions: the peninsular Malaysia and Singapore; Java, Mindanao, Sabah, and Sulawesi; and Australia and Papua [12]. Abdullah Sungkar motivated by the need for a new organisation that could work to achieve an Islamic State in Indonesia and cause of established JI in Malaysia around 1995. During the 1990’s Al Qaeda infiltrated JI and JI subsequently developed into a pan-Asian network extending from Malaysia and Japan in the north to Australia in the south [13]. Peak in Indonesia, the tactical operation of the Bali attack was conducted by JI’s Indonesian cells until now the hunt terrorist operations continue take place. From histories, the actions of terrorism generally is not only done by a bunch of people but also the country to the people or the other country. Therefore, actions like this always to be a secret network. In modern era, the concept of the network allows us to capture the interactions of any individual unit within larger field of activity to which the unit exists, see Figure 1. The model of network based on the concept of graph. However, to construct any required network is the causes of the actors exist and related to the cluse of relations between them.
3
Network Data and Investigation
For building social network is difficult if only because a clue of relation between a pair of actors as a property of the pair, i.e. anything inherent to either actor. Collecting data onnactors degenerates is to find the properties of n(n−1)
2 pairs
sci-Terrorist Network: Towards An Analysis 3
Fig. 1.The relations among entities in the salience
entists, though done carefully and reliably, are painstaking and time-consuming, is by involving questionnaires, interviews, direct observations, manual sifting through archival records, or various experiments [14].
Through investigation, there are two ways for finding the terrorist: adirect and anindirectways.
1. In particular, an independent Bernoulli random draw determines whether a particular agent is found directlyas a terrorist. The direct finding about a particular agent as terrorist at each period is independent of other terrorists. Thus, a terroristican be found directly by the authority according to some probabilityαi. This probability depends on the extent of the enforcement
agency’s scrutiny of terroristi.
2. The law enforcement authority might also find terrorists indirectly. It is based on when the agency detects a terrorist who has information about other members of the organization, the agency also finds each of these with probabilityγ∈(0,1].
(a) This implies that the enforcement agency’s ability to find terrorists in-directly based on the structure social of the terror group.
4 M. K. M. Nasution & M. Elfida
The law enforcement agency has a budgetB∈[0,1] to allocate the resources for investigating the N members of the organization and devotedαi ∈[0,1] to
investigate member i where PNi=1αi ≤B. Without loss of the generalization,
we label terrorists so that α1≤α2≤. . . αN. We refer toαi as the enforcement
agency’s level of scrutiny (or investigation) of terrorist i. Each terrorist can be found by the enforcement agency. If the terrorist is found, this imposes a direct cost to the organization of k >0. This cost may include a punishment for the individual, such as time in prison, and a cost to the organization of recruiting a new member.
In information structure, it is not just what you know, but also whom you know, that matters. What you know, say, Σ, Σ ⊂ Γ the set of all thinking. Someone has only mod(Σ) as a part of the thinking or class of knowledge K
[15].
Definition 1. Let σ be a generator as a trigger of the thinking, and {σi|i =
1, . . . , m} is a set of generator for Σ such that Σ={f(σi)|i= 1, . . . , m} is the knowledge of an actor wheref()as disseminator.
A graphGis an ordered pair (V, E), whereV 6=∅represents the finite set of verteces andErepresents the set of edges as set of all unordered pairs of vertices. The set of all graphs of ordernand sizemis denoted withG(V, E) =G(n, m). Let us defineξ and ζ as two mapping,ξ:A→V and ζ:{Σai⊓Σaj}i,j →E, we obtain a tie betweenai andbj as edge
{i, j}=ζ(|σai⊓σaj|) (1)
or brieflyij=ζij.
Definition 2. The shortest distance between verticesi, j∈Gis called the geodesic
distance betweeni andj, denoted byℓij(G), i.e.,
ℓij(G) = min(
X
ij∈E
ζij) (2)
where
1. ℓij=ℓjiifij =ji, for allij, ji∈Eorijis an undirected edge (symmmetry). 2. ℓij6=ℓjiif ij is a directed edge (assymmetric).
Definition 3. Let G(V, E)is a graph, where V 6=∅. The total distance, T(G), is
T(G) =X
i∈G
X
j∈V
ℓij(G) (3)
Definition 4. A diameter of a graph G(V, E) defined as a maximum over the
geodesic distances between all pairs of vertices, i.e.,
D(G) = max
Terrorist Network: Towards An Analysis 5
Definition 5. The community (based on fields of knowldge, or organization) is
a set neighbors at distance δof vertex i byΞi,δ(G), i.e.,
Ξi,δ(G) ={i∈V|ℓij(G) =δ}. (5)
Some researchers and goverment agencies gather information from various sources that involved computer network or the computer mediated communi-cation. They have a database of millions of new feed, minutes and e-mails and want to use these to get a detailed overview of all terrorist events in a particular geographic region in the last five years. This information not only related to the general public but also the information coming from government officials. Knowledge of terrorist networks [16] is useful in finding various other crimes. In law enforcement concerning organized crimes such as drugs and money leunder-ing [17]. Knowleunder-ing patterns of relationship in a social network is very useful for law enforcement agencies to investigate collaborations among criminals, i.e., how the perpetrators are connected to one another would assist the effort to disrupt a criminal act or to identify additional suspects.
4
Optimal Network
Any organization takes their network structure explicitly. In absence of further information, we are interested in what structure these organizations actually adopt. Theoretically, the analysis of the sharing knowledge of covert networks depends on proposed framework [18] such that the optimal network structure derived the appropriate scenarios.
Definition 6. Let Gn is a set of graphs of order n. The information measure
of g∈Gn is given by
K(g) =n(n−1)
T(G) (6)
In terrorist organizations case, for two agents, one responsible for network secrecy and the other one for information efficiency, the set Gn is connected
graphs where the bargaining as an event in time space. Then, the secrecy as the hidden knowledge, we usedmod(Σai) as a part of the class of knowledge.
Definition 7. The hidden knowledge measurement H(g) of a graphg ∈Gn is defined as the expected fraction of the network that remains hid under assumption of sharing probability of individual i ∈ V being equal to ∂i, i.e., mod(Σai), as following
H(g) =X
i∈V
∂iui (7)
where fraction of the network that individual i sharing be1−ui.
6 M. K. M. Nasution & M. Elfida
Definition 8. The balance among hidden and sharing of knowledge is an
opti-mal graph g∈Gn that maximizes
γ(g) =H(g)K(g) (8)
The optimal graph is the bargaining solution ofg∈Gn, and the probability
of exposure of an individual in the organization is uniform over all network members, i.e, αi= 1n. The fraction of the network that individualiexposes is
1−ui=
pdi+ 1
n (9)
wherepis probability identically if communication on links is detected indepen-dently, fordias degree of vertexiin graphg, i.e. ifpis a low value the complete
graph is optimal. This statement equivalence to a lemma as follows.
Lemma 1. If p ∈ [0,1
2], then µ(g
n
comp) ≥ µ(g),∀g ∈ Gn, where gcomp is a complete graph on nvertices.
And if pis a high value the star graph is optimal.
Lemma 2. if p∈ [1
2,1], then µ(g
n
star) ≥µ(g),∀g ∈ Gn, wheregcomp is a star graph onnvertices.
The actual network of operation of JI Bali bombing has been provided [12]. This network is graph that we use as basis for comparison with the theoretical framework presented earlier. The Bali Bombing cell can be split into the bom making team, the support team and the command team. Both cells adopted the structure of a complete graph and obtained the optimal graph according to the theoretical framework. The command team visited both cells and coordinated the operation. Therefore, the characteristics of the sharing knowledge, ideology of terrorism, information, etc. for the number of linked terroristsnis strictly less thanN if we take the authority’s scrutiny {α1, . . . , αN} and we study the most
efficient information structure that theN terrorists can form, as follows [19,20]. 1. The optimal structure is used to linkn < N terrorists is a hierarchy consist of the terrorist with the lowest probability of finding at the top, and the
n terrorists with the highest probability of the finding linked to him, i.e.,
N, N−1, . . . , N −n+ 1→1.
2. Ifγ= 1, the optimal information structure is as follows: (a) If N∗= 0, the optimal information structure is an anarchy.
(b) If 0< n∗ < N, the optimal structure is an individual-dominated
hier-archy for where the hub is terrorist 1 and the subordinates are terrorist
N, . . . , N−n+ 1. (c) Ifn∗
=N, the optimal structure is the mixed structure.
5
Conclusion
Terrorist Network: Towards An Analysis 7
References
1. Nasution, M. K. M. and Noah, S. A. 2010. Extracting social networks from Web documents.The 1st National Doctoral Seminar on Artificial Intelligence Technol-ogy(CAIT2010), UKM: 278-281.
2. Carlile, L. 2007. The definition of terrorism. A report by lord Cartile of Berriew Q.C. Independent Reviewer of Terrorism Legislation.Cm 7052. London: HMSO. 3. Taylor, M. 2010. Is terrorism a group phenomenon?Aggression and Violent
Be-havior, 15: 121-129.
4. Woods, J. 2011. The 9/11 effect: Toward a social science of the terrorist threat. The Social Science Journal, 48: 213-233.
5. McCallum, A., Corrada-Emmanuel, A., and Wang, X. 2004. The author-recipient-topic model for author-recipient-topic and role discovery in social networks: Experiments with Enron and Academic Email.Technical ReportUM-CS-2004-096.
6. Poland, J. M. 1988. Understanding Terrorism. Englewood Cliffs NJ: Prentice-Hall. 7. Sclagheck, D. M. 1988. International Terrorism. Lexington MA: Lexington Books. 8. Murphy, J. F. 1989. State Support of International Terrorism. San Francisco:
Westview Press.
9. D’Amore, L. J., and T. E. Anuza. 1986. International Terrorism: Implication and Challenge for Global Tourism.Business Quarterly, November: 20-29.
10. Richter, L. K. and W. L. Waugh, Jr. 1986. Terrorism and Tourism as Logical Companions.Tourism Management7: 230-238.
11. S¨onmez, S. F. 1998. Tourism, terrorism, and political instability. Annals of Tourism Research, 25(2): 416-456.
12. Koschade, S. 2006. A social network analysis of Jemaah Islamiyah: The applica-tion to counterterrorism and intelligence. Terrorism and Policical Violence, 29: 559-575.
13. Gunaratna, R. 2003.Inside Al Qaeda: Global Network of Terror. Berkley Trade. 14. Wasserman, S., and Faust, K. 1994. Social Network Analysis: Methods and
Ap-plications, Cambridge University Press.
15. Nasution, M. K. M. to appear. Theory of sharing knowledge: an introduction. Bulletin of Mathematics.
16. Krebs, V. E. 2002. Mapping networks of terrorist cells.Connections, 24: 43-52. 17. Xu, J., and Chen, H. 2004. Fighting organized crimes: using shortest-path
algo-rithms to identify associations in criminal networks.Decision Support System, 38: 473-487.
18. Lindelauf, R. H. A., Borm, P. and Hamers, H. 2008. The influence of secrecy on the communication structure of covert networks. CentER Discussion Paper, 2008-23: 1-18.
19. Baccara, M., and Bar-Isaac, H. 2008. How to organize crime. The Review of Economic Studies, 75: 1036-1067.