Overview of
SQL Server
I
n this c hapter, I’ll intro duc e yo u to Mic ro so ft SQL Server 7, inc luding the key features o f the pro duc t. Then I’ll c o ver its arc hitec ture and sec urity mo del. Finally I’ll c o ver spec ific issues related to using ADO to ac c ess SQL Server, suc h as building a c o nnec tio n string and mapping data types.Overview of SQL Server 7
Mic ro so ft SQL Server 7 is Mic ro so ft’s premier database man-agement system. It is easy to install and administer, and it c o mes with to o ls and wizards that make it easy to develo p applic atio ns. As yo u might expec t, SQL Server runs o nly o n Mic ro so ft Windo ws o perating systems. Unlike previo us ver-sio ns o f SQL Server, ho wever, SQL Server 7 runs o n bo th Windo ws 2000/ NT and Windo ws 98/ 95 platfo rms.
SQL Server 7 has these key features:
✦High perfo rmanc e relatio nal database
✦Sc alable fro m small databases to very large databases
✦Easy to install and use
✦Reaso nably pric ed
✦Tightly integrated with Windo ws
✦Built-in suppo rt fo r data wareho using
SQL Server editions
SQL Server c o mes in three different editio ns: Deskto p, Stan-dard, and Enterprise. All three editio ns are built o n the same c o de base, so applic atio ns that are develo ped to run o n the Deskto p Editio n are guaranteed to be 100% c o mpatible with
the Standard and Enterprise Editio ns. Likewise, yo u may take an applic atio n running o n the Enterprise Editio n and run it o n the Deskto p Editio n so lo ng as yo u do n’t use any o f the advanc ed features present in the Enterprise Editio n.
The Desktop Edition
The Deskto p Editio n is new in SQL Server 7 and is targeted at small databases that reside o n a wo rkstatio n. This editio n might be useful fo r pro grammers who want to debug and test their applic atio ns lo c ally befo re running them o n a larger, shared database. Yo u might also use it when yo u keep a lo c al database to c ac he info rmtio n o r fo r use with a stand-alo ne applic armtio n. Yo u c o uld also use database replic a-tio n to keep this database sync hro nized with a larger database.
Yo u c an install the Deskto p Editio n o nly o n Windo ws 98/ 95 systems, Windo ws NT Wo rkstatio n and Windo ws 2000 Pro fessio nal Systems. Yo u are limited to a maximum o f two CPUs in the same system and a maximum database size o f 4GB. Also , so me features that are fo und in the Standard Editio n and Enterprise Editio n, suc h as the OLAP Servic es and full-text indexing, aren’t inc luded in the Deskto p Editio n.
While the Deskto p Editio n uses the same c o de base as the Standard and Enterprise Editio ns, a lo t o f effo rt has go ne into o ptimizing the database server fo r a wo rksta-tio n enviro nment. The amo unt o f main memo ry needed to run the database server has been minimized, and o ther c hanges have been made to get the o ptimal perfo r-manc e o ut o f this c o nfiguratio n.
Don’t blame me: While the Desktop Edition of SQL Server w ill run on a Window s 98/ 95 platform , you should not expect the sam e level of stability that you w ould find on a Window s 2000/ NT platform .
The Standard Edition
The Standard Editio n is the traditio nal versio n o f SQL Server that has been in use fo r years. This editio n c an be installed o nly o n Windo ws 2000/ NT Server. It c an be used o n systems with up to fo ur CPUs, and there is no limit to the size o f yo ur database.
A lo t o f effo rt has go ne into making SQL Server 7 easy to use. Many c o nfiguratio n o ptio ns that existed in prio r releases have been replac ed with internal c o de that makes c hanges dynamic ally based o n the wo rklo ad. Fo r parameters that still exist, intelligent wizards are available to help yo u c ho o se the appro priate values.
whic h makes yo ur database pro grams muc h mo re effic ient. Other features, suc h as full-text indexes, whic h make it easy to lo c ate info rmatio n in yo ur database, and OLAP Servic es, whic h makes it easy to build data wareho uses, are also inc luded in the Standard Editio n.
Data warehouses without programming: Believe it or not, you can com bine SQL Server Standard Edition w ith tools like Microsoft Excel 2000 and Microsoft MapPoint 2000 to create data w arehouses w ithout w riting a single line of code. Don’t believe m e? Check out a copy of m y book Unlocking OLAP with SQL Server and Excel 2000published by IDG Books Worldw ide, Inc. I hope you like it.
The Enterprise Edition
The Enterprise Editio n is no t fo r everyo ne. It is targeted at very large and/ o r high-ac tivity database servers. It requires Windo ws 2000/ NT Server, Enterprise Editio n, whic h suppo rts mo re than 2GB o f main memo ry and mo re than fo ur CPUs in a sin-gle server. It inc ludes advanc ed features, suc h as fail o ver c lustering fac ilities and the ability to partitio n an OLAP c ube ac ro ss multiple servers, whic h are designed to handle large wo rklo ads in a multiserver enviro nment.
SQL Server utilities
SQL Server inc ludes several utilities to help yo u c o nfigure, manage, and use yo ur database server. Of these to o ls, yo u’re pro bably go ing to use the Enterprise Manager and the Query Analyzer mo st o f all, with the Data Transfo rmatio n Servic es (DTS) c lo se behind. These are the to o ls with whic h yo u c an c reate yo ur database and its struc tures and extrac t info rmatio n o n the fly.
Enterprise M anager
Enterprise Manager is a multipurpo se utility that yo u use to manage yo ur database. With this utility, yo u c an start and sto p the database server and set c o nfiguratio n pro perties fo r the database server. This utility allo ws yo u to define lo go n ids and manage sec urity. Yo u c an even use it to c reate databases and their o bjec ts, inc lud-ing tables, indexes, sto red pro c edures, and so o n, uslud-ing an interac tive graphic al design to o l.
The Enterprise Manager uses the Mic ro so ft Management Co nso le ( MMC) as its basic interfac e ( see Figure 23-1) . The display c o nsists o f an ic o n tree o n the left side o f the windo w and a display area that c o ntains mo re detailed info rmatio n abo ut the selec ted ic o n in the ic o n tree.
Figure 23-1: Running the Enterprise Manager
The Enterprise Manager c o ntains a large number o f wizards to help yo u perfo rm c o mmo n tasks suc h as c reating databases, tables, and lo go n ids. Also , it c o ntains wizards that help yo u define a maintenanc e sc hedule fo r tasks suc h as bac king up yo ur database, reo rganizing indexes, and c hec king database integrity. Onc e the list o f tasks has been selec ted, yo u then define a sc hedule fo r them, and SQL Server will take c are o f sc heduling and running them. It will also keep rec o rds o f the ac tivities so that yo u c an review them fo r po tential pro blems.
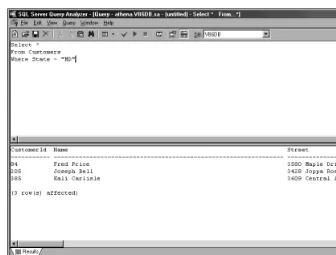
Query Analyzer
Figure 23-2: Running the Query Analyzer
Testing, testing, testing: Since you can call stored procedures from w ithin Query Analyzer, you m ay w ant to use it to test your stored procedures before trying to call them from your Visual Basic application.
Data Transformation Services
I fo und that the Data Transfo rmatio n Servic es is o ne o f the mo st useful to o ls in SQL Server 7, sinc e it makes it easy to mo ve data fro m o ne plac e to ano ther. It is extremely fast and flexib le and c an c o mmunic ate with SQL Server datab ases, Orac le datab ases, Exc el files, text files, and just ab o ut any o ther type o f file that yo u c an ac c ess using OLE DB o r ODBC.
One o f the nic est features inc luded with DTS is the ability to transfo rm yo ur data while c o pying it. Yo u c an spec ify ho w eac h so urc e c o lumn is mapped to the desti-natio n c o lumn. DTS will handle the mo st c o mmo n data type transfo rmatio ns. DTS even has the ability to use a VBSc ript mac ro to transfo rm o ne c o lumn to ano ther, whic h may pro ve useful if a simple data type c o nversio n isn’t suffic ient.
But wait, there’s more:If your source and destination databases are both in SQL Server 7, you can copy all of the com ponents of a database, including security inform ation, stored procedures, and so on. This m akes it easy to m ake a com plete copy of a database for testing purposes.
OLAP Services
OLAP ( Online Analytic al Pro c essing) Servic es fulfills a c ritic al need when imple-menting a data wareho use. It allo ws yo u to reo rganize the data fro m a regular rela-tio nal database into a multidimensio nal data sto re that c an be easily used by data analysis to o ls suc h as Exc el 2000. By inc luding the ability to aggregate selec ted parts o f the data, OLAP Servic es c an o ffer muc h better perfo rmanc e than if a c o n-ventio nal database sto rage system were used.
English Query
English Query is a series o f COM c o mpo nents that allo ws yo u to translate an English language questio n into an SQL Statement. This ability makes it easy to build to o ls that let inexperienc ed users retrieve info rmatio n fro m their databases. It also inc ludes a to o l that c an auto matic ally c reate a simple Web page that ac c epts questio ns and returns their results.
The English Query utility is used to c o llec t info rmatio n abo ut the database yo u want to ac c ess. This utility is driven by a series o f wizards that asks yo u detailed questio ns abo ut the wo rds that c an be used to desc ribe yo ur data. This info rmatio n is c o llec ted and saved in a do main that is used by the COM c o mpo nents to trans-late the user’s questio n into a SQL Se le ctstatement.
Database Architecture
SQL Server uses a true c lient/ server arc hitec ture, where the database server runs in its o wn address spac e. While it c an run o n Windo ws 98/ 95 platfo rm, yo u will get the best results running o n multipro c esso r c o mputers with Windo ws 2000/ NT Server. It is designed to be remo tely administered and to explo it fac ilities that already exist in Windo ws suc h as e-mail, Internet ac c ess, etc .
SQL Server is arranged as a single Windo ws servic e that o perates a c o llec tio n o f databases. Fo ur o f the databases are kno wn as system databases, bec ause they pro -vide servic es c ritic al to the database server itself. The o ther databases are kno wn as user databases, bec ause they c o ntain user data.
System databases
info rmatio n inc ludes the database name and physic al files that are used. It also inc ludes sec urity info rmatio n that allo ws users to ac c ess the database server itself.
Tempdb ho lds tempo rary tables and tempo rary sto red pro c edures. It also supplies tempo rary sto rage fo r tasks suc h as ho lding the intermediate results o f a query. Sinc e no ne o f the info rmatio n sto red in tempdb needs to exist beyo nd the c urrent database server sessio n, eac h time SQL Server is started, tempdb is erased.
The msdb database is used to maintain info rmatio n abo ut sc heduled ac tivities in the database, suc h as database bac kups, DTS jo bs, and so o n.
The mo del database is used as a template whenever SQL Server c reates a new database. As part o f the pro c ess to c reate a database, the c o ntents o f the mo del database are c o pied to the new database. Then the rest o f the spac e in the database is filled with empty database pages.
Database objects
Within a database there are several different types o f database o bjec ts that c an be manipulated. The mo st fundamental o bjec t within a database is a table. Tables c o me in two flavo rs, syste m table sand use r table s.A system table c o ntains info rma-tio n abo ut the database. Fo r instanc e a system table c alled sysobjectsc o ntains info rmatio n abo ut the vario us o bjec ts in the database. The database server itself updates system tables, tho ugh if yo u wish, yo u c an read the info rmatio n fro m the system tables to determine info rmatio n abo ut the database itself. User tables o n the o ther hand are c reated by a database user and c o ntain the user’s info rmatio n.
Database destroyer: Updating a system table directly is one of the fastest w ays to destroy a database’s integrity. Any m istake you m ay m ake m ay result in corrupting your database beyond repair. If you happen to be updating a system table in the m aster database, you’ve corrupted the entire database server.
Ano ther type o f database o bjec t is the inde x.The index ho lds info rmatio n that allo ws the database server to quic kly lo c ate a ro w o r set o f ro ws in a table. Besides tables and indexes, o bjec ts suc h as sto red pro c edures, users, ro les, and so o n are also sto red in the database. Ho wever, unlike tables and indexes, whic h are sto red direc tly in the database files, these o bjec ts are sto red in system tables.
Database storage
Eac h database is c o mpo sed o f two types o f files: data file s(.MDF) and lo g file s
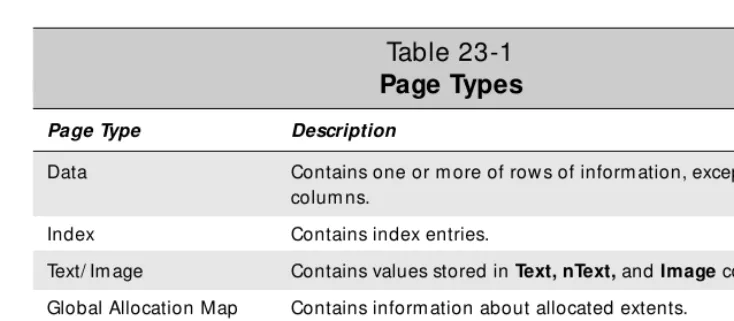
(.LDF). Data files ho ld info rmatio n kept in the database, while lo g files keep a his-to ry o f the c hanges made his-to the database. A minimal database c o nsists o f o ne data file and o ne lo g file. Additio nal files c an be used as needed. Data files c o nsist o f a series o f 8KB pages. There are six types o f pages (see Table 23-1). Eac h page has a 96-byte header, whic h c o ntains system info rmatio n like the type o f page, the amo unt o f free spac e o n the page, and info rmatio n abo ut who se data is o n the page. Pages c an’t be shared and are assigned to a single table o r index o r are used to ho ld allo c a-tio n info rmaa-tio n.
Table 23-1
Page Types
Page Type Description
Data Contains one or m ore of row s of inform ation, except for large
colum ns.
Index Contains index entries.
Text/ Im age Contains values stored in Text, nText,and Imagecolum ns. Global Allocation Map Contains inform ation about allocated extents.
Index Allocation Map Contains inform ation about the extents used by a table or index.
Page Free Space Contains inform ation about the free space available on pages.
A data page is used to sto re info rmatio n abo ut o ne o r mo re ro ws. A ro w c an’t exc eed the maximum size o f a page. Sinc e the page header size is 96 bytes and the additio nal info rmatio n used to manage ro w info rmatio n takes 32 bytes, the largest ro w yo u c an sto re is 8,060 bytes. No te that if a ro w c o ntains large c o lumns ( Text, nText, o r Image) , these c o lumns do no t c o unt to wards the 8,060-byte limit. Large c o lumns are sto red in their o wn pages and will o c c upy as many pages as needed to sto re the entire c o lumn’s info rmatio n.
An e xte ntis eight pages. This is the primary unit o f allo c atio n fo r a table o r index. If the size o f a table o r index is less than eight pages, it is assigned to a mixed extent that shares the extent with o ther tables and indexes. Onc e a table o r index gro ws larger than eight pages, it is mo ved to a unifo rm extent, whic h is no t shared with o ther database o bjec ts.
For better performance: If possible, you should keep your database files on an NTFS (NT file system ) form atted disk drive w ith 64KB disk extents.
Lo g files c o nsist o f a series o f lo g rec o rds. Eac h lo g rec o rd c o ntains info rmatio n nec essary to undo a c hange made to a ro w. This c o nsists o f befo re and after values fo r every c hanged c o lumn, plus additio nal info rmatio n that allo ws the rec o rds to be gro uped to gether in transac tio ns and to identify when and ho w the c hanges were made. When c o mbined with a database bac kup, yo u c an use the info rmatio n in a lo g file to rec o ver all o f the c hanges to a database up to a spec ific po int in time o r when the database server sto pped wo rking.
Database capacities
In an ideal wo rld, a database wo uld be able to sto re as muc h info rmatio n as yo u wo uld like. Ho wever, in the real wo rld, there are always limits. Table 23-2 displays a list o f limitatio ns in SQL Server 7.
Table 23-2
Database Capacities
Item Capacity
Bytes per index 900
Bytes per key 900
Bytes per row 8,060
Clustered indexes per table 1
Colum ns per index 16
Colum ns per key 16
Colum ns per base table 1,024
Colum ns per Selectstatem ent 4,096
Colum ns per Insertstatem ent 1,024
Database size 1,048,516TB
Databases per server 32,767
Files per database 32,767
File size, data file 32TB
File size, log file 4TB
Foreign key table references per table 253
Identifier length in characters 128
Nested stored procedure calls 32
Nested subqueries 32
Nonclustered indexes per table 249
Param eters per stored procedure 1024
Row s per table lim ited by available storage
SQL Server data types
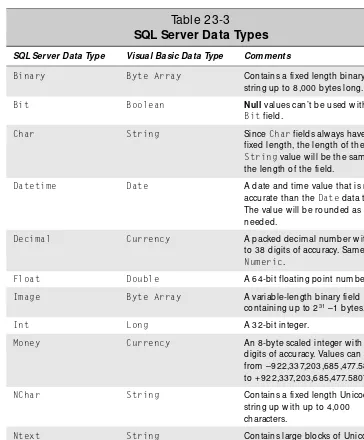
SQL Server suppo rts a wide variety o f data types as sho wn in Table 23-3.
Table 23-3
SQL Server Data Types
SQL Server Data Type Visual Basic Data Type Comments
Binary Byte Array Contains a fixed length binary string up to 8,000 bytes long.
Bit Boolean Nullvalues can’t be used w ith a
Bitfield.
Char String Since Charfields alw ays have a fixed length, the length of the
Stringvalue w ill be the sam e as the length of the field.
Datetime Date A date and tim e value that is m ore accurate than the Datedata type. The value w ill be rounded as needed.
Decimal Currency A packed decim al num ber w ith up to 38 digits of accuracy. Sam e as
Numeric.
Float Double A 64-bit floating point num ber.
Image Byte Array A variable-length binary field containing up to 231–1 bytes.
Int Long A 32-bit integer.
Money Currency An 8-byte scaled integer w ith four digits of accuracy. Values can range from –922,337,203,685,477.5808 to + 922,337,203,685,477.5807.
NChar String Contains a fixed length Unicode string up w ith up to 4,000 characters.
Ntext String Contains large blocks of Unicode text, w ith up to 230–1 characters. NvarChar String Contains a variable-length Unicode
SQL Server Data Type Visual Basic Data Type Comments
Numeric Currency A packed decim al num ber w ith up to 38 digits of accuracy. Sam e as
Decimal.
Real Single A 32-bit floating point value.
SmallDatetime Date A date and tim e value ranging from 1 Jan 1900 to 6 Jun 2079 and accurate to the m inute.
Smallint Integer A 16-bit integer.
SmallMoney Currency A 4-byte scaled integer w ith four decim al digits of accuracy. Values can range from –214,748.3648 to + 214,748.3647.
Sysname String Sysnameis really a synonym for
Nchar(128)and is used to hold the nam e of a database object.
Text String Contains large blocks of text data, up to 231–1 characters.
Timestamp Byte Array Contains a unique identifier that can be used to order a sequence of events. How ever, it doesn’t contain a value that corresponds to a date or tim e.
Tinyint Byte An 8-bit integer.
VarBinary Byte Array If you declare a Byte Array
w ithout bounds and assign the value to it, you m ay then use the
Lenor UBoundfunctions to determ ine the size of the field.
VarChar String The length of the Stringw ill be the length of the field. It has a m axim um length of 8,000 characters.
Connecting to SQL Server with ADO
Creating a c o nnec tio n string fo r SQL Server is a fairly straightfo rward pro c ess. Yo u must spec ify the name o f the pro vider, whic h is SQLOLEDBwhen c o nnec ting to an SQL Server database; the name o f the data so urc e, whic h is the name o f the database server; and the initial c atalo g, whic h is the name o f the name o f the database yo u want to ac c ess. The first keywo rd in the list must be the Provider=keywo rd. The rest o f the c o nnec tio n string is passed to the pro vider fo r interpretatio n. A sample c o nnec tio n string is sho wn belo w.
Provider=SQLOLEDB;Data source=Athena;Initial catalog=VB6DB
Besides spec ifying the database server and initial c atalo g, yo u c an also inc lude sec u-rity info rmatio n. If yo u’re using SQL Server Authentic atio n, yo u c an inc lude the User Id=keywo rd and the Password=keywo rd o f the lo gin yo u want to use to ac c ess the database. Otherwise, Windo ws NT Authentic atio n will be used. Yo u c an also fo rc e the SQLOLEDBpro vided to use Windo ws NT Authentic atio n by inc luding
Trusted_Connection=yesas part o f the c o nnec tio n string.
Authentication is discussed in the next section, “SQL Server Security.”
Hacking security systems:You should never hardcode a user id and passw ord in a connection string. A hacker m ight view your program w ith a binary editor, w hich can display the contents of the program file in both ASCII and hex. A sim ple search on SQLOLEDBor User Idw ill let the hacker find these values. In the sam e vein, storing the user id and passw ord in the Registry is also vulnerable to a sm art hacker. Better alternatives w ould be to use Window s NT Authentication, w hich doesn’t use user id and passw ord to access the database, or to prom pt the user for the user id and passw ord and then insert them into the connection string.
SQL Server Security
Everyo ne that ac c esses a SQL Server database must present lo gin info rmatio n that is verified befo re the user is granted ac c ess to the database server. This pro c ess is kno wn as authe nticatio n.
Authentication in SQL Server
SQL Server has two different mo des o f authentic ating a user: SQL Server Authentic atio n and Windo ws NT Authentic atio n. Yo u c an use Windo ws NT Authentic atio n b y itself o r in c o mb inatio n with SQL Server Authentic atio n, whic h is also kno wn as Mixed Mo de Authentic atio n. This authentic atio n value is set fo r the entire datab ase server level and affec ts all datab ases. While c hanging fro m Windo ws NT Authentic atio n to Mixed Mo de Authentic atio n isn’t diffic ult, c o nvert-Tip
ing Mixed Mo de Authentic atio n to Windo ws NT Authentic atio n c an b e very diffi-c ult due to the numb er o f lo gins that may need to b e diffi-c o nverted to Windo ws NT ac c o unts.
Windows 2000 or NT only: In order to use Window s NT Authentication, SQL Server m ust be running on a Window s 2000/ NT platform . You m ust use SQL Server Authentication if you are running your database server on Window s 98/ 95.
SQL Server Authentication
When a user c o nnec ts to an SQL Server database using SQL Server Authentic atio n, that user needs to pro vide a lo gin id and a passwo rd. This info rmatio n is presented when the user attempts to c o nnec t to the database. It is validated against the info r-matio n in the master database. If the lo gin info rr-matio n is c o rrec t, the user is granted ac c ess to the database server. If the lo gin info rmatio n is inc o rrec t, the c o nnec tio n to the database is terminated.
No Windows, no options: If you w ant to connect from a non-Window s com puter to an SQL Server database, you m ust use SQL Server Authentication.
A SQL Server lo gin c an range in size fro m 1 to 128 c harac ters and may c o ntain any c o mbinatio n o f letters, numbers, and spec ial c harac ters o ther than a bac kslash (\) . Fro m a prac tic al viewpo int, using so me spec ial c harac ters suc h as spac es in the lo gin may fo rc e yo u to use do uble quo tes (“) o r square brac kets ([]) aro und the lo gin id when yo u try to referenc e the lo gin id in a SQL Statement. Lo gins are also c ase-insensitive, unless yo u selec ted a c ase-sensitive so rt o rder when yo u installed SQL Server.
Windows NT Authentication
Windo ws NT Authentic atio n is based o n Windo w 2000/NT lo gin tec hniques. The same user name that yo u use to sign o nto Windo ws bec o mes yo ur lo gin id. A passwo rd isn’t needed, sinc e the user name was validated when yo u signed o nto Windo ws. Ho wever, just bec ause yo ur user name has been validated, do esn’t mean that yo u auto matic ally have ac c ess to SQL Server. SQL Server maintains info rmatio n in the master database that identifies the users who are permitted to ac c ess the database server.
The primary advantage to using Windo ws NT Authentic atio n is that yo u c an use NT sec urity gro ups. Yo u c an c reate a sec urity gro up and add it to SQL Server in plac e o f the user name. Then anyo ne who is a member o f the sec urity gro up auto mati-c ally has amati-c mati-c ess to the SQL Server database server.
Simplify your services: You should alw ays use Window s NT Authentication for services such as an IIS Application or a COM+ transaction. This elim inates the need to store a database passw ord in the application, w hich allow s you to change passw ords for these user nam es on a periodic schedule w ithout recom piling the program s.
M ixed M ode Authentication
Mixed Mo de Authentic atio n is a c o mb inatio n o f b o th SQL Server Authentic atio n and Windo ws NT Authentic atio n. If a lo gin id is spec ified when yo u c o nnec t to the datab ase server, SQL Server Authentic atio n is used. If no lo gin id is spec ified, Windo ws NT Authentic atio n is used. In b o th c ases, the lo gin info rmatio n must b e c o rrec t, o r the c o nnec tio n to the datab ase server will b e dro pped.
You may not have a choice:While Window s NT authentication is m ore secure, you m ust use Mixed Mode Authentication if you plan to let users from non-Window s based com puters access your database.
SQL Server authorization
Just bec ause the user has been granted ac c ess to the database, do esn’t mean that the user c an ac c ess any info rmatio n inside the database o r perfo rm any database tasks. The user must be autho riz e dto ac c ess reso urc es and perfo rm tasks. Eac h lo gin must be mapped o nto a spec ific user id in eac h database. Witho ut this map-ping, the lo gin will be denied ac c ess to the database.
Within eac h database, eac h user is granted ac c ess to the vario us o bjec ts inside, suc h as tables, indexes, and sto red pro c edures. The type o f ac c ess granted to an o bjec t is kno wn as a pe rmissio n. The permissio ns available depend o n the type o f database o bjec t. Fo r instanc e, o n a table yo u c an permit so meo ne to selec t ro ws, insert ro ws, update ro ws, delete ro ws, o r ac c ess the table as part o f a referential integrity c o nstraint.
In additio n to granting ac c ess to datab ase o b jec ts, yo u c an also grant ac c ess to the SQL Statements that allo w yo u to c reate, alter, and destro y vario us datab ase o b jec ts, suc h as tab les, views, and sto red pro c edures. The same fac ility also c o n-tro ls the ab ility to b ac k up and resto re datab ases and datab ase lo g files.
SQL Server roles
In o rder to simplify sec urity administratio n, SQL Server allo ws yo u to define ro le sin a database. Ro les are similar to sec urity gro ups in Windo ws 2000/ NT. They represent a c o llec tio n o f users who are granted similar permissio ns. A ro le c an be used in plac e o f a user id when granting permissio ns.
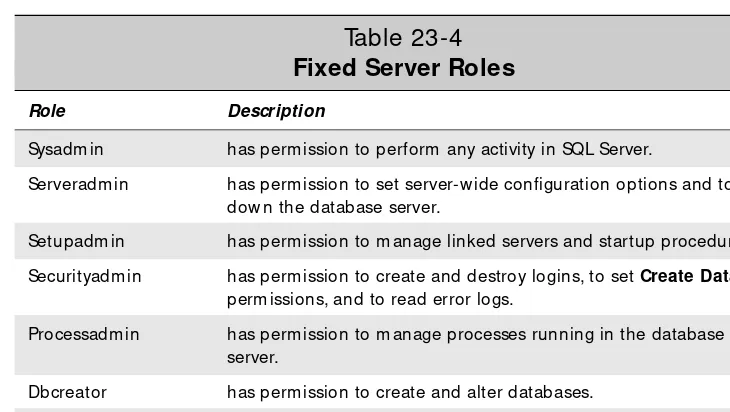
Ro les c o me in three flavo rs, fixe d se rve r, fixe d database ,and use r de fine d.The fixed server ro les determine the func tio ns a lo gin c an perfo rm at the database server level ( see Table 23-4) . The fixed database ro les define gro ups o f standard c apabili-ties available to a user within a single database ( see Table 23-5) .
Table 23-4
Fixed Server Roles
Role Description
Sysadm in has perm ission to perform any activity in SQL Server.
Serveradm in has perm ission to set server-w ide configuration options and to shut dow n the database server.
Setupadm in has perm ission to m anage linked servers and startup procedures.
Securityadm in has perm ission to create and destroy logins, to set Create Database
perm issions, and to read error logs.
Processadm in has perm ission to m anage processes running in the database server.
Dbcreator has perm ission to create and alter databases.
Diskadm in has perm ission to m anage the disk files used by SQL Server.
Table 23-5
Fixed Database Roles
Role Description
db_ow ner has perm ission to perform any activity and access any data in the database.
db_accessadm in has perm ission to create and destroy user ids.
db_securityadm in has perm ission to m anage all database perm issions, object ow nerships, roles, and role m em berships.
db_ddladm in has perm ission to create and destroy database objects, but doesn’t have perm ission to m anage perm issions.
db_backupoperator has perm ission to backup the database.
db_datareader has perm ission to read data from any user table in the database.
db_dataw riter has perm ission to m odify data in any user table in the database.
db_denydatareader has perm ission to deny read access to any database object.
db_denydataw riter has perm ission to deny m odify access to any database object.
Also , a user may be asso c iated with multiple ro les in the same database. This means that when yo u design yo ur database, yo u c an define ro les fo r eac h basic func tio n that a user c an perfo rm in the database. Yo u c an define ro les that permit users to read info rmatio n fro m different gro ups o f tables, plus o ther ro les that allo w users to perfo rm different types o f updates. Fo r instanc e, yo u may define a Clerkro le that permits so meo ne to enter o rder info rmatio n, but prevents him o r her fro m updating pric e info rmatio n, while defining a Managerro le that permits so meo ne to c hange pric e info rmatio n.
Thoughts on SQL Server
SQL Server is a m odern relational database m anagem ent system that is m ore than com peti-tive w ith any other database m anagem ent system in the m arket today. It is w ell integrated into the Window s environm ent, w hich m akes it ideal for those organizations w here one or tw o people are responsible for the full range of IT services from IT Manager and Database Adm inistrator to System s Analyst, Program m er, and Com puter Operator. The w ide range of autom ated w izards allow s you to install, build, and operate database applications m uch easier than w ith m ost other database m anagem ent system s, yet SQL Server’s perform ance is am ong the highest available, m eaning that it w ill scale w ell into even the largest environm ents.
Summary
In this c hapter yo u learned:
✦abo ut SQL Server and its vario us editio ns.
✦that Enterprise Manager is used to c reate and maintain SQL Server databases.
✦that Query Analyzer is used to perfo rm ad-ho c queries against an SQL Server database.
✦that Data Transfo rmatio n Servic es is a high perfo rmanc e data impo rt and expo rt utility.
✦abo ut the arc hitec ture o f SQL Server.
✦abo ut the datatypes available in SQL Server.
✦ho w to c o nnec t to SQL Server with ADO.
✦ho w sec urity is implemented in SQL Server.