Jie Wang
JieWang
Computer
Network Security
Theory and Practice
With 81 figures
IAlJTHOR'
IProf. Jie Wang
IDepartment of Computer Science IUnIverslty of Massachusetts Lowell, MA 01854, USA IE-mail: wang.uml@gmail.com
IISBN 978-7-04-024162-4Higher Education Press,Beijing ISBN 978-3-540-79697-8Springer Berlin HeidelbergNewYork e ISBN 978-3-540-79698-5Springer Berlin HeidelbergNewYork
ILlbrary of Congress Control Number: 2008925345
This work is subject to copyright. All rights are reserved, whether the whole or part of the matenal IS concerned, speCifically the nghts of translatIOn, repnntmg, reuse of Illustrations, recitation, broadcasting, reproduction on microfilm or in any other way, and storage in data banks. Duplication of this publication or parts thereof is permitted only under the provisions of the German Copynght Law of September 9, 1965, m ItScurrent version, and permission for use must always be obtained from Springer-Verlag. Violations are liable to prosecution under ItheGerman Copynght Law.
@2009 Higher Education Press, Beijing and Springer-Verlag GmbH Berlin Heidelberg Co-published by Higher Education Press, Beijing and Springer-Verlag GmbH Berlin
Hei-セ・ャ「・イァ
ISpringer is a part of Springer Science+ Business Media springer.com
The use of general descnptlve names, registered names, trademarks, etc. in thiS pubhcatlOn does not imply, even in the absence of a specific statement, that such names are exempt from Itherelevant protective laws and regulations and therefore free for general use.
Preface
People today are mcreasmgly relymg on pubhc computer networks to conduct bUSI-ness and take care of household needs. However, public networks may be insecure because data stored in networked computers or transmitted through networks can be stolen, modified, or fabricated by malicious users. Thus, it is important to know what securIty measures are aVaIlable and how to use them. Network securIty prac-trees are desIgned to prevent these potentIal problems. Networksecurity,orIgmated from meeting the needs of providing data confidentiality over public networks, has grown into a major academic discipline in both computer science and computer engineering, and also an important sector in the information industry.
The goal of network securIty IS to gIve people the hberty of enJoymg computer networks wIthout fear of compromlsmg theIr rIghts and mterests. Network secu-nty accomphshes thIs goal by provldmg confidentlahty,integrtty,non-repudIatIon, and availability of useful data that are transmitted in open networks or stored in networked computers.
Network securIty wIll remam an actIve research area for several reasons. FIrst, securIty measures that are effectIve today may no longer be effectIve tomorrow because of advancements and breakthroughsin computmg theory, algorIthms, and computer technologies. Second, after the known security problems are solved, other security loopholes which were previously unknown may at some point be discov-ered and exploited by attackers. Third, when new applications are developed or new technologIes are mvented, new securIty problems may also be created wIth them. Thus, network secunty IS meant to be a long lastmg scuffle between the offenders and the defenders.
vi Preface
This book is intended to provide a balanced treatment of network security along these two lines, with adequate materials and sufficient depth for teaching a one-semester introductory course on network security for graduate and upper-level un-dergraduate students. Itis intended to inspire students to think about network secu-rity and prepare them for taking advanced network secusecu-rity courses. This book may also be used as a reference forITprofessionals.
This book is structured into nine chapters.
Chapter 1 presents an overview of network security.Itdiscusses network secu-rity goals, describes common network attacks, characterizes attackers, and defines a basic network security model.
Chapter 2 presents standard symmetric-key encryption algorithms, including DES, AES, and RC4. Itdiscusses their strength and weaknesses. Italso describes common block-cipher modes of operations and presents key generation algorithms. Chapter 3 presents standard public-key encryption algorithms and key-exchange algorithms, including Diffie-Hellman key exchange, RSA public-key cryptosystem, and elliptic-curve cryptography.Italso discusses how to transmit and manage keys. Chapter 4 presents secure hash functIOns and message authentIcatIOn code algo-rithms for the purpose of authenticating data, including the SHA-512 secure hash functIOn, the WHIRLPOOL hash algonthm, cryptographIc checksums, and the stan-dard hash message authentication codes. Italso presents the block-cipher offset-codebook mode of operations for producing ciphertext and message authentication code.Itthen dIscusses bIrthday attacks on secure hash functIOns, and descnbes the dIgItal sIgnature standard. Fmally, thIS chapter mtroduces a dual sIgnature scheme used for electromctransactions and a blmd signature scheme used for producmg electronic cash.
Chapter 5 presents several network security protocols commonly used in prac-tice. Itfirst describes a standard public-key infrastructure for managing public-key certIficates. Itthen presents IPsec, a network-layer secunty protocol; SSLlTLS, a transport-layersecurityprotocol; and several applIcatIOn-layersecurityprotocols, including POP and S/MIME for sending secure email messages, Kerberos for au-thenticating users in local area networks, and SSH for protecting remote logins.
Chapter 6 presents common security protocols for wireless local-area networks at the data-Imk layer, mcludmg WEP for provldmg WIred-eqUIvalent pnvacy, WPA and IEEE 802. I l1IWPA2for provldmg WIreless protected access, and IEEE 802.1X for authentlcatmg WIreless users. Itthen presents the Bluetoothsecurity protocol for wireless personal-area networks. Finally, it discusses security issues in wireless mesh networks.
Chapter 7 presents firewall technologIes and basIc structures, mcludmg network-layer packet fiJtenng, transport-network-layer stateful mspectlOns, transport-network-layer gateways, applIcatIOn-layerproxies,trusted systems and bastIOnhosts, firewall configuratIOns and screened subnets, and network address translations.
Preface vii
Chapter 9 presents intrusion detection technologies, including intrusion detec-tion system architecture and common intrusion detecdetec-tion methods.Italso discusses event signatures, statistical analysis, and data mining methods. Finally, it introduces honeypot technologies.
To get the most out of this book, readers are assumed to have taken undergraduate courses on discrete mathematics, algorithms, data communications, and network programming; or have equivalent preparations. For convenience, Chapter 3 includes a section reviewing basic concepts and results of number theory used in public-key cryptography. While it does not introduce socket programming, the book contains socket API client-server programming exercises. These exercises are designed for computer science and computer engineering students. Readers who do not wish to do them or simply do not have time to write code may skip them. Doing so would not affect learning the materials presented in the book.
Exercise problems are designed to have three levels of difficulty: regular, diffi-cult (designated with "), and challenging (designated with**). This book contains a number of hands-on drills, presented as exercise problems. Readers are encouraged to try them all.
I have taught network secunty courses to graduate and senIor undergraduate students for over ten years. And I have longed for a concisetextbook WIth a bal-anced treatment of network security and sufficient depth suitable for teaching a one-semester introductory course for my students. This book is the result of this quest.
Itwas wntten based on what I learned and expenenced from teachIng these courses and on student feedbacks accumulated over the years. In partIcular, I used an early draft of this book to teach a graduate network security course in 2006 and 2008 at University of Massachusetts Lowell, which helped me revise and enhance the ma-terials presented in this book. Powerpoint slides of these lectures can be found at
ィエエーZOOキキキN」ウNオュャN・、オOセキ。ョアOn・エs・」N
Due to space lImItatIOns, some InterestIng tOpICS and matenals are not presented In thIS book. After all, one book can only accomplIsh one book's mISSIOn. I only hope that this book can achieve its objective. Of course, only you, the reader, can be the judge of it. I will be grateful if you can please offer your comments, suggestions, and corrections to me at wang@cs.um1.edu.
I have benefited a great deal from numerous dISCUSSIons over the years WIth my colleagues and teachIng aSSIstants, as well as current and former students. I
viii Preface
I thank Ying Liu at the Higher Education Press for initiating this book project and editing this book.
lowe more than I can express to my wife Helen, my son Jesse, and my daughter Sharon for their understanding that I needed to spend long hours working on this project.
Lowell, Massachusetts
About the Author
lIe Wang IS Professor and Chair of Computer SCIence at the University of Mas-sachusetts Lowell (UML). He is also Director of the Center for Network and Infor-mation Security of UML. His first name "lie" in Mandarin is pronounced similar to "led." He received Ph.D. degree in Computer Science from Boston University in 1990, M.S. degree in Computer Science from Zhongshan University in 1985, and B.S. degreeInComputatIOnal MathematIcs from Zhongshan University In1982. He
has over 18 years of teaching and research experience and is equipped with network security consulting experience in financial industry. His research interests include network security, algorithms and computational optimization, computational com-plexIty theory, and wIreless sensor networks. HIS research has been funded contin-uously by the NatIOnal SCIenceFoundatIon since 1991 and has also been funded by IBM, Intel, and the Natural Science Foundation of China. He has published over 95 journal and conference papers, two books and three edited books. He is active in professional service, including chairing conference program committees and
Contents
1 Network Security Overview . . . 1
1.1 MISSIOn and DefimtlOns . . . 2
1.2 Common Attacks and Defense Mechamsms 3 1.2.1 Eavesdroppmg.. . . 3
1.2.2 Cryptanalysis... 4
1.2.3 Password Pilfering. . . 4
1.2.4 IdentIty Spoofing . . . .. 12
1.2.5 Buffer-Overflow Exploitations . . . .. 16
1.2.6 Repudiation... 17
1.2.7 Intrusion... 18
1.2.8 Traffic Analysis 18 1.2.9 Denial of Service Attacks 19 1.2.10 MahclOus Software 22 1.3 Attacker Profiles . . . .. 25
1.3.1 Hackers. . . .. 25
1.3.2 Script Kiddies . . . .. 27
1.3.3 Cyber Spies. . . .. 27
1.3.4 VICIOUS Employees. . . .. 28
1.3.5 Cyber Terrorists 28 1.3.6 Hypothetical Attackers 28 1.4 Basic Security Model .. . . .. 28
1.5 Security Resources . . . .. 30
1.6 Closmg Remarks. . . .. 31
1.7 ExercIses... 31
2 Data Encryption Algorithms 39 2.1 Data EncryptIOn Algonthm DeSIgn Cntena . . . .. 40
2.1.1 ASCII Code. . . .. 40
2.1.2 XOR Encryption . . . .. 41
xii Contents
2.1.4 Implementation Criteria. . . .. 45
2.2 Data Encryption Standard. . . .. 45
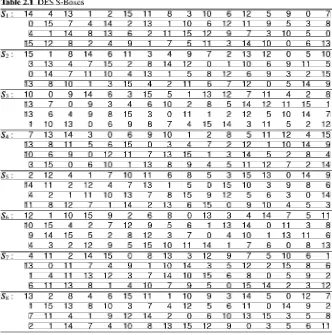
2.2.1 Feistel's Cipher Scheme 45 2.2.2 DES Subkeys 48 2.2.3 DES Substitution Boxes 49 2.2.4 DES Encryption . . . .. 51
2.2.5 DES Decryption and Correctness Proof. . . .. 53
2.2.6 DES Security Strength. . . .. 54
2.3 Multiple DES. . . .. 54
2.3.1 Triple-DES with Two Keys. . . .. 55
2 3 2 2DES and3DESL3 55 2.3.3 Meet-in-the-Middle Attacks on 2DES . . . .. 56
2.4 Advanced Encryption Standard. . . .. 57
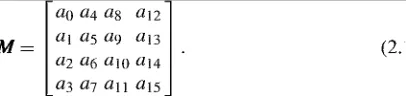
2.4.1 AES Basic Structures. . . .. 57
2.4.2 AES S-Boxes 60 2.4.3 AES-128 Round Keys .. . . .. 61
2.4.4 Add Round Keys 62 2.4.5 Substitute-Bytes... 63
2.4.6 Shift-Rows... 63
2.4.7 Mix-Columns... 64
2.4.8 AES-128 Encryption . . . .. 65
2.4.9 AES-128 Decryption and Correctness Proof. . . .. 65
2.4.10 Galois Fields. . . .. 67
2.4.11 Construction of the AES S-Box and Its Inverse ... . . . . .. 70
2.4.12 AES Security Strength. . . .. 7l 2.5 Standard Block-Cipher Modes of Operations. . . .. 71
2.5.1 Electronic-Codebook Mode 72 2.5.2 Cipher-Block-Chaining Mode. . . .. 72
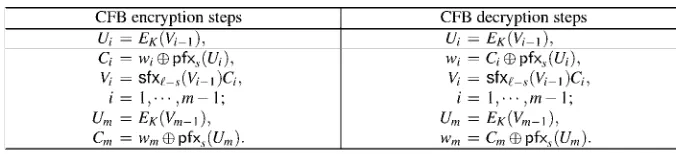
2.5.3 Cipher-Feedback Mode. . . .. 73
2.5.4 Output-Feedback Mode 74 2.5.5 Counter Mode. . . .. 74
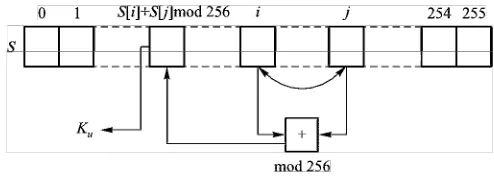
2.6 Stream Ciphers 75 2.6.1 RC4 Stream Cipher 75 2.6.2 RC4 Security Weaknesses. . . .. 76
2.7 Key Generattons 78 2.7.1 ANSIX9.17 PRNG 78 2.7.2 BBS Pseudorandom Bit Generator 79 2.8 ClOSIng Remarks. . . .. 80
2.9 ExercIses... 81
3 Public-Key Cryptography and Key Management.. . . .. . . .. 89
3.1 Concepts of Public-Key Cryptography. . . .. 89
3.2 Elementary Concepts and Theorems In Number Theory 92 3.2.1 Modular Anthmetlc and Congruence Re1attons . . . .. 92
Contents xiii
3 2 3 Primitive Roots 94
3.2.4 Fast Modular Exponentiation . . . .. 95 3.2.5 Finding Large Prime Numbers. . . .. 96 3.2.6 The Chinese Remainder Theorem 98 3.2.7 Finite Continued Fractions. . . .. 99 3.3 Diffie-Hellman Key Exchange 100 3.3.1 Key Exchange Protocol 101 3.3.2 Man-in-the-Middle Attacks 101
3.3.3 Elgamal PKC 102
3.4 RSA Cryptosystem 104
3.4.1 RSA Key Pairs, Encryptions, and Decryptions 104
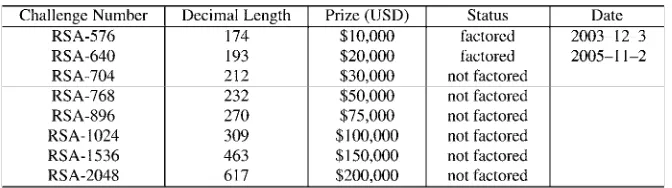
3.4.2 RSA Parameter Attacks 107
3.4.3 RSA Challenge Numbers 111 3.5 Elliptic-Curve Cryptography 112 3.5.1 Commutative Groups on Elliptic Curves 112 3.5.2 Discrete Elliptic Curves 113
3.5.3 ECC Encodings 114
3.5.4 ECC Encryption and Decryption 116
3.5.5 ECC Key Exchange 117
3.5.6 ECC Strength 117
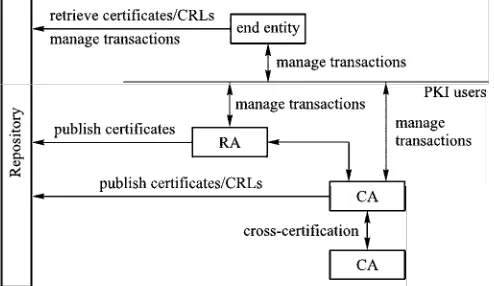
3.6 Key Distributions and Management 117 3.6.1 Master Keys and Session Keys 118 3.6.2 Public-Key Certificates 118
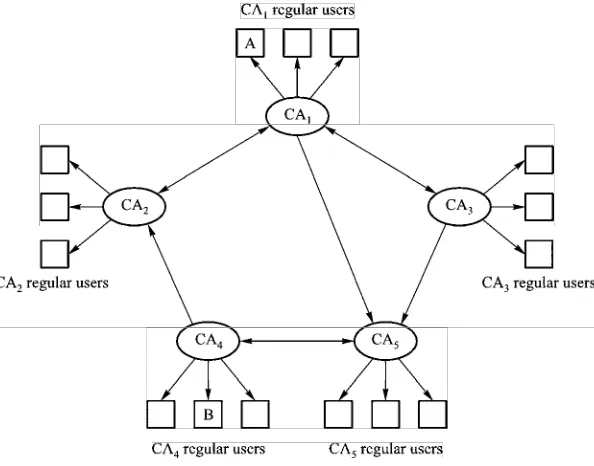
3.6.3 CA Networks 120
3.6.4 Key Rings 122
3.7 Closing Remarks 123
3.8 Exercises 123
4 Data Authentication 129
4.1 Cryptographic Hash Functions 130
4.1.1 DeSIgnCrIterIa of CryptographIC Hash FunctIOns 130
4.1.2 Quest for CryptographIC Hash FunctIOns 131 4.1.3 BaSIC Structure of Standard Hash Functions 132
4.1.4 SHA-512 133
4.1.5 WHIRLPOOL 136
4.2 Cryptographic Checksums 140
4.2.1 ExclUSIve-OR CryptographIC Checksums 140
4.2.2 Design Criteria of MAC AlgOrIthms 141 4.2.3 Data Authentication Algorithm 142
4.3 HMAC 142
4.3.1 Design Criteria of HMAC 142
4.3.2 HMAC AlgorIthm 143
4.4 Offset Codebook Mode of OperatIOns 143
4.4.1 BaSIC Operations 143
xiv Contents
4.4.3 aCB Decryption and Tag Verification 146
4.5 Birthday Attacks 146
4.5.1 Complexity Upper Bound of Breaking Strong Collision
Resistance 147
4.5.2 Set Intersection Attack 149 4.6 Digital Signature Standard 150
4.7 Dual Signatures and Electronic Transactions 153 4.7.1 Dual Signature Applications 154 4.7.2 Dual Signatures and Electronic Transactions 154 4.8 Blind Signatures and Electronic Cash 155
4.8.1 RSA Blind Signatures 156
4.8.2 Electronic Cash 156
4.9 Closing Remarks 158
4.10 Exercises 158
5 Network Security Protocols in Practice 165
5.1 Crypto Placements in Networks 165 5.1.1 Crypto Placement at the Application Layer 168 5.1.2 Crypto Placement at the Transport Layer 168 5.1.3 Crypto Placement at the Network Layer 169 5.1.4 Crypto Placement at the Data-Link Layer 169 5.1.5 Hardware versus Software Implementations of
Cryptographic Algorithms 170
5.2 Public-Key Infrastructure 170
5.2.1 X.509 Public-Key Infrastructure 170
5.2.2 X.509 Certificate Formats 172 5.3 IPsec: A Security Protocol at the Network Layer 173
5.3.1 Security Association 174
5.3.2 Application Modes and Security Associations 175
5.3.3 AH Format 177
5.3.4 ESP Format 179
5.3.5 Secret Key Determination and Distribution 180 5.4 SSLlTLS: Security Protocols at the Transport Layer 184 5.4.1 SSL Handshake Protocol 185
5.4.2 SSL Record Protocol 189
5.5 PGP and SIMIME: Email Security Protocols 190
5.5.1 Basic Email Security Mechanisms 191
5.5.2 PGP 192
5.5.3 S/MIME 193
5 6 Kerberos' An Authentication Protocol 194
5 6 1 Basic Ideas 194
5.6.2 Smgle-Realm Kerberos 195
5.6.3 Multiple-Realm Kerberos 198 5.7 SSH: Secunty Protocols for Remote Logms 200
Contents
5 9 Exercises
xv
201
6 Wireless Network Security 207
6 1 Wireless Communications and 802 11 WLAN Standards 207
6.1.1 WLAN Architecture 208
6.1.2 802.11 Essentials 210
6.1.3 Wireless Security Vulnerabilities 211
62 WEP 211
6 2 1 Device Authentication and Access Control 212
6.2.2 Data Integrity Check 212
6.2.3 LLC Frame Encryption 214
6.2.4 Security Flaws of WEP 215
63 WPA 218
6.3.1 Device Authentication and Access Controls 219
6.3.2 TKIP Key Generations 219
6.3.3 TKIP Message Integrity Code 222
6.3.4 TKIP Key Mixing 224
6.3.5 WPA Encryption and Decryption 227 6.3.6 WPA Security Strength and Weaknesses 229
6.4 IEEE 802.11 i/wPA2 229
6.4.1 Key Generations 230
6.4.2 CCMP Encryptions and MIC 230 6.4.3 802.11 i Security Strength and Weaknesses 231
6.5 Bluetooth Security 232
6.5.1 Piconets 232
6.5.2 Secure Pairings 233
6.5.3 SAFER+ Block Ciphers 234
6.5.4 Bluetooth AlgorithmsE1, E2l,andE22 238 6.5.5 Bluetooth Authentication 239 6.5.6 A PIN Cracking Attack 240 6.5.7 Bluetooth Secure Simple Pairing 242 6.6 Wireless Mesh Network Security 242
6.7 Closing Remarks 245
6.8 Exercises 245
7 Network Perimeter Security 249
7.1 General Framework 250
7.2 Packet Filters 251
7.2.1 Stateless Filtering 252
7.2.2 Stateful FJltenng 254
7.3 CIrCUIt Gateways 255
7.3.1 Basic Structures 255
7.3.2 SOCKS 257
7.4 Application Gateways 257
xvi Contents
7.4.2 Stateful Packet Inspections 259 7.5 Trusted Systems and Bastion Hosts 259 7.5.1 Trusted Operating Systems 259 7.5.2 Bastion hosts and Gateways 260
7.6 Firewall Configurations 261
7.6.1 Single-Homed Bastion Host System 261 7.6.2 Dual-Homed Bastion Host System 262
7.6.3 Screened Subnets 263
7 6 4 Demilitarized Zones 264
7.6.5 Network Security Topology 265 7 7 Network Address Translations 265
7.7.1 Dynamic NAT 266
7.7.2 Virtual Local-Area Networks 267 7.7.3 Small Office and Home Office Firewalls 267
7.8 Setting Up Firewalls 268
7.8.1 Security Policy 268
7.8.2 Building A Linux Stateless Packet Filter 269
7.9 Closmg Remarks 270
7.10 Exercises 270
8 The Art of Anti Malicious Software 277
8.1 VIruses 277
8.1.1 Virus Types 278
8.1.2 Virus Infection Schemes 280
8.1.3 Virus Structures 282
8.1.4 Compressor VIruses 283
8.1.5 Virus Disseminations 284
8.1.6 Win32 Virus Infection Dissection 285 8.1.7 Virus Creation Toolkits 287
8.2 Worms 287
8.2.1 Common Worm Types 288
8.2.2 The Morns Worm 288
8.2.3 The Mehssa Worm 289
8.2.4 Email Attachments 290
8.2.5 The Code Red Worm 292
8.2.6 Other Worms Targeted at Microsoft Products 293
8.3 VIrus Defense 294
8.3.1 Standard Scannmg Methods 295 8.3.2 Anti-Virus Software Products 296
8 3 3 Virus Emulator 297
8.4 Trojan Horses 298
8.5 Hoaxes 298
8.6 Peer-to-Peer Secunty 299
Contents xvii
8.6.3 Instant Messaging 301
8.7 Web Security 302
8.7.1 Basic Types of Web Documents 303 8.7.2 Security of Web Documents 304
8 7 3 ActiveX 305
8.7.4 Cookies 306
8.7.5 Spyware 307
8.7.6 AJAX Security 308
8.7.7 Safe Web Surfing 309
8 8 Distributed Denial of Service Attacks 310 8 8 1 Master-Slave DDoS Attacks 310 8.8.2 Master-Slave-Reflector DDoS Attacks 310 8.8.3 DDoS Attacks Countermeasures 311
8.9 Closing Remarks 313
8.10 Exercises 313
9 The Art of Intrusion Detection 317
9.1 Basic Ideas of Intrusion Detection 317
9.1.1 Basic Methodology 318
9.1.2 Auditing 319
9.1.3 IDS Components 320
9.1.4 IDS ArchItecture 322
9.1.5 Intrusion Detection Policies 324 9.1.6 Unacceptable Behaviors 325 9.2 Network-Based Detections and Host-Based Detections 325 9.2.1 Network-Based Detections 326 9.2.2 Host-Based Detections 328
9.3 SIgnature Detections 329
9.3.1 Network Signatures 329
9.3.2 Host-Based Signatures 330 9.3.3 OutSIder BehaVIOrs and InSIder MIsuses 332 9.3.4 SIgnature Detection Systems 333
9.4 StatIstIcal AnalySIS 334
9.4.1 Event Counter 334
9.4.2 Event Gauge 335
9.4.3 Event Timer 335
9.4.4 Resource UtIlIzatIOn 335
9.4.5 StatIstIcal Techmques 336
9.5 Behavioral Data Forensics 336
9.5.1 Data Mining Techniques 337 9.5.2 A Behavioral Data Forensic Example 337
9.6 Honeypots 338
9.6.1 Types of Honeypots 338
9.6.2 Honeyd 340
xviii Contents
9.6.4 Honeynet Projects 343
9.7 Closing Remarks 344
9 8 Exercises 344
A 7-bit ASCII code 349
B SHA-512 Constants (in hexadecimal) 351
C Data Compression using ZIP 353
D Base64 Encoding 355
E Cracking WEP Keys usingWEPCrack 357
E.l System Setup 357
E.2 Experiment Details 358
E.3 Sample Code 360
F Acronyms 365
References 371
Chapter 1
Network Security Overview
lj you know your enemies and know yourself, you will win hundred times in hundred battles. If you know yourself but not your enemies, you will suffer a defeat for every victory won. If you do not know yourselj or your enemies, you will always lose.
- Sun Tzu, "The Art of War"
The goal of network security is to give people the freedom to enjoy computer net-works without fear of compromising their rights and interests. Network security therefore needs to guard networked computer systems and protect electromc data that IS eIther stored10networked computers or transmItted10the networks. The
In-ternet whIch IS bUIlt on theIPcomrnumcationprotocols has become the dommant computer network technology.Itinterconnects millions of computers and edge net-works into one immense network system. The Internet is a public network, where individuals or organizations can easily become subscribers of the Internet service by connectmg theIr own computers and networkmg deVIces (e.g. routers and smfters) to the Internet and paymg a small subscnptlOn fee.
2
1.1 Mission and Definitions
I Network Security Overview
The tasks of network security are to provide confidentiality, integrity, non-repudia-tion,andavailabilityof usefuldatathat are transmitted in public networks or stored in networked computers.
The concept of data has a broad sense in the context of network security. Any ob-ject that can be processed or executed by computers is data. Thus, source code, exe-cutable code, files in various formats, email messages, digital music, digital graph-ics, and digital video are each considered data. Data should only be read, written, or modified by legitimate users. That is, unauthorized individuals or organizations are not allowed to have access to data.
Just as CPU, RAM, hard disk, and network bandwidth are resources, data is also a resource. Data is sometimes referred to asinformationormessage.
Each piece of data has two possible states, namely, thetransmission stateand the
storage state. Data In the transmISSIOn state IS SImply data In the process of beIng dehvered to a network destInatIOn.Data In the storage state IS that whIch IS stored In a local computer or In a storage deVIce. Thus, the meamngs of data confidentlahty and data integrity have the following two aspects:
1. Provide and maintain the confidentiality and integrity of data that is in the trans-mISSIOn state.InthIS sense, confidentlahty means that data durIng transmISSIOn cannot be read by any unauthonzed user and integritymeans that data dunng transmission cannot be modified or fabricated by any unauthorized user. 2. Provide and maintain the confidentiality and integrity of data that is in the
stor-age state. Within this state, confidentiality means that data stored in a local device cannot be read by any unauthonzed user through a network and Integnty means that data stored In a local deVIce cannot be modIfied or fabncated by any unau-thonzed user through a network.
Data non-repudiation means that a person who owns the data has no way to convince other people that he or she does not own it.
Data avaIlablhty means that attackers cannot block legItImate users from USIng aVaIlable resources and servIces of a networked computer. For example, a computer system Infected WIth a VIruS should be able to detect and dISInfectthe VIruS WIthout much delay, and a server hit by denial of service attacks should still be able to provide services to its users.
UnIntentIOnal components In protocol speCIficatIOns, protocol ImplementatIOns, or other types of software that are explOItable by attackers are often referred to as
loopholes, flaws, or dejects. They mIght be an Imperfect mmor step In a protocol design, an unforeseen side effect of a certain instruction in a program, or a miscon-figured setting in a system.
1.2 Common Attacks and Defense Mechanisms 3
actions may be illegal. What constitutes legal actions against attackers involves a discussion of relevant laws, which is beyond the scope of this book. Therefore, even though offense may be the best defense, this tactic may not apply to network se-curity. Building a deep layered defense system is instead the best possible defense tactic in network security. Within this type of defense system, multiple layers of defense mechanisms are used to resist possible attacks.
Network security is a major part of information security. Inaddition to network security, information security deals with many other security issues, including se-curity policies, sese-curity auditing, sese-curity assessment, trusted operating systems, database security, secure code, emergency response, computer forensics, software forensics, disaster recovery, and security training. This book does not cover these issues, but it may touch certain aspects of them.
1.2 Common Attacks and Defense Mechanisms
Common network security attacks can be characterized mto a few basIc types. Al-most every known network security attack IS eIther one of these basIc types or a combination of several basic types.
1.2.1 Eavesdropping
Eavesdropping is an old and effective method for stealing private information. In network communications, the purpose of eavesdropping is to intercept data from network traffic usmg a networkmg devIce and a packet smffer. A packet smffer, a.k.a. network smffer, IS a program formomtoringmcommg network traffic. When connecting a router to the Internet, for example, one can use a packet sniffer to capture all the IPpackets going through that router. TCPdumpand Wireshark (formerly known as Ethereal) are the two most widely-used network sniffers today, whIch are aVaIlable as free downloads from theIr Websltes (see ExercIse 1.3). Usmg thIs eavesdroppmg techmque, the eavesdropper can mterceptIPpackets that go through the router he controls. To capture a partIcular IPpacket, however, the eavesdropper must first determine which communication path theIPpacket will travel through. Then he could either try to get control of a certain router on the path or try to msert a new router of hIs own on the path. ThIs task IS more dIfficult, but IS not ImpossIble. For example, the eavesdropper may try to compromIse a router on the path and mstall a packet smffer m It to mtercept theIPpackets he IS after. The eavesdropper may also use an ARP spoofing technique (see Section 1.2.4) to rerouteIPpackets to his sniffer without compromising a router.
4 I Network Security Overview
There is no way to stop eavesdropping in public networks. To counter eaves-dropping, the best thing one can do is to encrypt data. Computer cryptography is developed for this purpose, where the sender encrypts data before he transmits it. Data encryption is a major component of computer cryptography.Ituses an encryp-tion key to break the original data into pieces and mix them up into an unintelligible form, making it difficult for the eavesdropper to obtain any useful information out of it. Thus, even if the eavesdropper is able to intercept the encrypted data, he is still not able to obtain the original data without knowing the decryption key. Orig-inal data is also referred to asplaintextdata, while encrypted data is referred to as
ciphertextdata.
Ciphertext data can be converted back to plaintext data using a decryption key. The encryption (and decryption) key is a string of characters, which is also referred to as asecret key.Ina symmetric-key encryption algorithm, the encryption key and the decryption key are identical.
1.2.2 Cryptanalysis
Cryptanalysis is the art of finding useful information from ciphertext data without knowing the decryption keys. For example, in a substitution cipher that substitutes plamtext letters wIth cIphertext letters, If a cIphertext message reveals a certam sta-tIstIcal structure, then one may be able to decIpher It. To obtam a stasta-tIstIcal structure of the data one may calculate the frequency of each character m the cIphertext data and compare it against the known statistical frequency of each character in the lan-guage used in the plain text. For example, in the English lanlan-guage, the letter "e" has the highest frequency. Thus, in a substitution cipher, the character that has the hIghest frequency m the cIphertext data IS ltkely to correspond to the plamtext letter "e" (see e.g. Exercise 1.5). Analyzing statistical structures of ciphertext messages was an effective method to break encryption algorithms before the computer era.
Modern encryption algorithms can produce ciphertext without showing any sta-tistical structure. Therefore, cryptanalysis is focused on analyzing encryption algo-nthms usmg mathematIcal tools and hIgh-performance computers.
The best way agamst cryptanalysIs IS to devIse encryptIon algonthms that reveal no statIstIcal structures m cIphertext messages and use longerencryptionkeys. Us-ing longer keys makes brute force analysis more impractical.Inaddition to having stronger encryption algorithms, it is equally important to distribute and manage keys and to Implementencryptionalgonthms wIthout explOItable loopholes.
1.2.3 Password Pi{[ering
pass-1.2 Common Attacks and Defense Mechanisms 5
words. User names are public information, but user passwords must be kept secret. Only two parties should have knowledge of the password, namely, the user and the underlying computer program (e.g. an operating system or a specific application). A password is a sequence of letters, digits, or other characters, which is often selected by the user. Legitimate users enter their user names and passwords to prove their legitimacy to the computer program with their account information. An unautho-rized user may impersonate a legitimate user to "legitimately" log on to a password-protected device, if he can get hold of a legitimate user name/password pair. He can then gain a]] the "legal" rights to transmit, receive, modify, and fabricate data.
Password protection is often the first defense line, and sometimes it is the only defense mechanism available in the system. Thus, we must take measures to en-sure that user passwords are we]] protected against larcenies. For this purpose we will look at several common methods for pilfering user passwords. These meth-ods includeguessing, social engineering, dictionary attacks,andpassword sniffing. Phishingattacks have become a most common form of mass social engineering at-tacks in recent years.
Guessing
Guessing is the easiest method to i11egitimately acquire a password. The attacker may get luckyIfthe user uses a short password orIfhe forgets to change the default password created for hIm. Also, users have a tendency to use the same passwords. Accordmg to a recent survey by PC Magazme, the ten most common passwords used by users, listed in decreasing order of popularity, are as follows:
1. password 2. 123456
3. qwerty(which are keys below 123456 on standard keyboards) 4. abc123
5 Jetmein 6. monkey 7. myspace1 8. password1 9. blink182
10. the user's own first name
Ifthe user chooses a simple password such as these ten easy ones then the guesser would mdeed have an easy task.
Social Engineering
6 1 Network Security Overview
user passwords to the attackers. Impersonation may be carried out either in person or in an electronic form. Phishing is an electronic form of social engineering targeted at a large number of people.
There are other forms of social engineering attacks. For example, attackers may try to collect recycled papers from the recycle bins in a corporation's office building, hoping to find useful login information. Attackers may also make a Web browser pop up a window asking for user login information.
Physical Impersonation
Physical impersonation means that the attacker pretends to be a different person to delude the victim. For example, the following imaginary conversion between the at-tacker and a receptionist named Betty demonstrates how a social engineering attack might be carried out in person:
Attacker: (Speaking with an authoritative voice.) "Hello, Betty, this is Nina Hatcher. I am Marketing Manager of the China branch office."
Betty: (Thinking that this woman knew my name, my number, and spoke like a manager, she must be whom she said she was.) "IIello, Nina, what can I do for you?"
Attacker: "Betty, I am attending a meeting in Guangzhou to finalize an important deal with
a large corporatIOnInChina. To close the deal, I'll need to venfy certain techmcal data
pro-duced by your group that I believe is still stored in the computer at your site. This is urgent.
I tned to log on to your system today, but for some reasonItdIdn't work. I was able to log
on toItyesterday though. Is your computer down? Can you help me out here?"
Belly: "Well, I don't know what happened. But you may try the {olloWIng ... " (Thinking that she is doing the company a favor by telling the marketing manager how to get into the system.)
PhIshmg
PhIshmg attacks are mass SOCIal engmeermg attacks that take advantage of peo-ple with a tendency to trust authorities. The main forms of phishing attacks are disguised email messages or masqueraded Websites. For example, attackers (also calledphishers)send disguised email messages to people as if these messages were from banks, credIt card companIes, or other financIal mstltutlOns that people may payattentionto. People whorecervesuch messages are told that there was a secunty breach in their accounts, and so they are required to verify their account informa-tion for security purposes. They are then directed to a masqueraded Website to enter their user names and passwords (e.g. see Exercise 1.8). The following example is a real phlshmg message verbatIm:
1.2 Common Attacks and Defense Mechanisms
Subject: US Bank - Internet Online Access is Locked - October 5, 2007 at 12:23:05 PM
Dear US Bank customer,
We're sorry, but you reached the maximum number of attempts allowed to login into your US Bank account. For your protection, we have locked your account.
Consequently, we placed a temporary restriction on your account. We did this to protect your account from any fraudulent activity.
Please click below and complete the steps to Remove Limitations. This allows us to confirm your identity and unlock your US Bank online account
http://www4-usbank.com/
If we do no receive the appropriate account verification within 48 hours, then we will assume this US Bank account is fraudulent and will be suspended.
7
US Bank, Member FDIC. @2007 US Bank Corporation. All Rights Reserved.
The link in the email is of course a trap, which links to a Website set up by the phisher to capture the account information entered by the victims. Here the email and the WebsIte are the baIt. The SnIffing mechanIsms hldmg behmd the Web page are the hook. Even you do not plan to enter any mformatlOn on the WebSIte, clIck-mg the lmk m a phlshclIck-mg emaIl may alreadycompromiseyour computer, for modern phishing techniques make it possible to embed exploits in a Web page and the ex-ploits will be activated when you open the Web page.
Ingeneral, any phishing email would contain a link to a bogus Website, called a
phishing site.Phlshmg sItes look Just lIke the real ones, wIth the purpose of lurmg careless users to enter usefullogm mformatlon to be captured by the phlsher. Anti-phishing extensions of Web browsers are emerging technology for detecting and blocking phishing sites.
Dictionary Attacks
8 I Network Security Overview
file named shadows under directory /etc, which is an access-restricted system
file.
Inthe Windows NT/XP operating system, for another example, the user names and the encrypted user passwords are stored in the system's registry in a file named
SAM.They can be read using special tools, e.g.pwdump.
Dictionary attacks take advantage of the way some people use dictionary words, names, and dates as passwords. These attacks find user passwords from their en-crypted forms. A typical dictionary attack proceeds as follows:
1. Obtain information of user names and the corresponding encrypted passwords. This was done, for example, in early versions of Linux or Linux by getting a copy ofthe /etc/passwdfile.InWindows XP, it can be done usingpwdump
to read the system registry.
2. Run the encryption routine used by the underlying system on all dictionary words, names, and dates. That IS, compute the encrypted hash for each dIctIO-nary word, each name, and each date.
3. Compare each output obtained from Step 2 with the encrypted passwords ob-tained from Step 1.Ifa match presents, a user password is found.Inother words, suppose wis a word and Wi
=
crypt(w)is the output of the encryption routinecryptoninputw.SupposeuandPuare a pair of user name and encrypted
pass-word of useru.IfWi
=
Pu,thenwis useru'spassword or is equivalent to useru's password, for wmay not be unique.Step 2 is computationally intensive, for there are many words, names, and dates. To avoid carrying out this costly computation each time an encrypted hash is given, one would want to pre-compute Step 2 and store the results (i.e. password-hash pairs) m one table, so that one only needs to do a table lookup to find the corre-spondmg plamtext password from the grven encrypted hash. But such a table WIll be humongous. Constructing a Rainbow table helps to reduce the table size and make the computation at Step 2 manageable.
Rambow Tables
1.2 Common Attacks and Defense Mechanisms 9
Let WII be a given password. Apply hand ralternatively to obtain a chain of passwords that are different pairwise:
Wll, W12,'" ,WIn] ,
wherenl is a number chosen by the user, and
Wli= r(h(wl,i_J)), i
=
2,3,···,nl.(WII ,h(Wln]))
in the rainbow table, whereWll is in the first column andh(Wlnl) is in the second column.
Now choose a new password W21 (i.e. W21 has not been generated in previous chains). Repeat the same procedure for another round to obtain
wheren2is a number chosen by the user andW2i
=
r(h( W2,i-d
fori=
2,3, .. ·,n2,such that the first cham and the second cham are dlsJomt. ThatIS,for any 1
<
u<
nland 1 :::;v:::;
na.
we haveWIu-I=-W2v. Storein the rainbow table. Performing this procedurektimes will generatekrows in the rambow table as follows:
assword hash value
WIl h(Wln1)
W21 h(W2nz}
Wkl h(Wknk)
whereW jl is the first password in thejthchain,h(W jnj) is the encrypted hash of the
last password m the same cham, and the chams are dlsJomt pmrwlse.
Let j :A ----+ Bandg :B ----+A be two functIons. Lety E Band i ::;,O. Define (jog)l(y)as follows:
(Jog y)i( ) {
=
y,J(g((fog)i-l(y))),ifi::;'1.ifi=
0,10 I Network Security Overview
for somei
>
0 and some j with 1<
j<
kandi<
j,thenW is possible to appear in thejthchain ofWj1, ... ,Wjni:Thus, the following algorithm may help findw. 1. Set Q1f -Qoandt f -O. Letn= max{nl,'" ,nd.2. Check if there is a 1
:s;
j:s;
ksuch thatQl = h(Wjnj)andt:s;
n.Ifyes, goto Step 3; otherwise, goto Step 4.3. Apply randhalternatively onWj1 for 0
:s;
i:s;
j times until Wjn, =(r
0h)i (wjl)is generated such that h(wjnJ = Qo. If such aWjni is found, return W= Wjni; otherwise, goto Step 4.
4. Set QIf -h(r(Q1)) andtf - t
+
1.Ift:s;
nthen goto Step 2. Otherwise, return "password not found." (The rainbow table does not contain the password whose hash value equals Qo).Note that several different reduction functions may be used in the same password chain. This may help avoid collisions that two different chains, starting from differ-ent passwords, may end up at the same password or at the same hash value at some pomt.
Remarks
ItIS worth notmg that dIctIOnaryattacks may also be used10a pOSItIVe way. For
ex-ample, Wmdows Office allows users to encrypt MIcrosoft Word documents, where secret keys used for encryption are generated based on the passwords selected by users.If,after a long while, a user forgets the password of a password-protected doc-ument, then the file will no longer be useful, for the user cannot decrypt it. To solve thIs problem, a company named Elcomsoft developed a password recovery software program usmg the dIctIOnary-attack techmques. ThIs IS apositrveapphcatlOn of dIC-tionary attacks. On the other hand, we note that if an encrypted office document is stolen, then the thief can also use this program to decrypt the document. There is a positive side and a negative side in every thing. A kitchen knife is intended to chop food, but It can also be used to harm people. Water can carry boats, but It can also topple them.
We also note that the file /etc/passwd10recentversionsof UNIX and Lmux
no longer displays the encrypted user passwords (see Exercise 1.6). This makes it more difficult for the attackers to obtain the list of encrypted passwords for
launch-109a dIctIOnaryattack.
Password Sniffing
Password sniffers are software programs, used to capture remote login informa-tIOn such as user names and user passwords. Common network apphcatlOns such as Telnet, FTP, SMTP, and POP3 often require users to type10 theIr user names
1.2 Common Attacks and Defense Mechanisms 11
programs (e.g. SSH) to encrypt alI messages, thus making it more difficult to sniff user passwords.
SSH and other programs that encrypt login information such as HTTPS, how-ever, are still vulnerable to password sniffing attacks. For example, Cain & Abel, a password recovery tool for the Microsoft Operating Systems, is a network sniffing tool that can capture and crack encrypted passwords using dictionary, brute-force, and cryptanalysis attacks. Cain & Abel can be downloaded free of charge from http://www.oxid.it/cain.html.
Password Protection
The folIowing rules and practices can help protect passwords from pilfering: 1. Use long passwords, with a combination of letters, capital letters, digits, and
other characters such as$,#,&, %.Do not use dictionary words, common names, and dates as passwords. ThIS rule makes guessmg attacks and dIctIOnaryattacks arduous.
2. Do not reveal your passwords to anyone you do not know. Do not submit to anyone who acts as if he has authority.Ifyou have to give out your password to someone you trust, do so face to face. AVOId tellmg passwords over the phone or usmg email. ThIspracticehelps prevent SOCIal engmeenng breaches.
3. Change passwords penodlcally and do not reuse old passwords. ThIS rule helps defend users against patient and persistent attackers who may keep on running dictionary attacks on alI possible strings formed using the first rule, and hope that they may get lucky. Attackers may also keep records of old passwords they have IdentIfied.
4. Do not use the same password for different accounts. Thus, evenIfa user's pass-word for a particular account is compromised, the user's other accounts would still be safe.
5. Do not use remote login software that does not encrypt user passwords and other Important personal mformatlOn. ThIS practIce makes password smffing difficult. 6. Shred alI discarded papers using a good paper shredder. This practice makes it
difficult for attackers to find useful mformatlOn from dIscarded old documents. 7. Avoid entering any information in any popup window, and avoid clicking on
links in suspicious emails. Instead, go to the legitimate Website directly using the true URL address, and follow the dIrectIOnsthere. ThISpractIce helps counter password smffing and reduce the chance of bemg caught by phlshers.
Other User-Authentication Methods
AuthentIcatIOn usmg user passwords IS so far the most WIdely used authentIcatIOn method.
12 1 Network Security Overview
features, e.g. fingerprints and retinas. The third method uses authenticating items, e.g. passes and certificates of identification. These three methods have been applied and implemented in computer applications.
The first method is implemented in the form of user names and user passwords. The second method is implemented in the form of connecting biometric devices to a computer, e.g. fingerprint readers and retina scanners. These devices are rel-atively more expensive to acquire and maintain, and so are often used in a tightly control1ed environment where high levels of security are required. For example, in-stead of using credit card readers at check-out stands to authenticate credit holders and link payments to their accounts, using fingerprint readers is just as convenient and is more secure
The third method is implemented in the form of electronic passes authenticated by the issuer. Certain authentication protocols (e.g. Kerberos) use this method to authenticate users.
Authentication using user passwords is the easiest method to implement and so far the most commonly used authentication method.
1.2.4 Identity Spoofing
IdentIty spoofing attacks allow attackers to Impersonate a vIctIm WIthoutuSing the vIctIm's passwords. Common IdentIty spoofing attacks Include man-in-the-middle
attacks,message replays, network spoofing,andsoftware exploitationattacks.
Man-in-the-middIe Attacks
Ina man-In-the-mlddle attack, the attacker tnes to comprormse a network deVIce (or instal1s one of his own) between two or more users. Using this device, the attacker can intercept, modify, or fabricate data transmitted between users. The attacker will then forward them as if they have not been touched by the attacker. For example, the attacker may Intercept an IPpacket sent by user A, modIfies ItS payload, and then send the modIfied packet to user B asIfIt comes from user A. ThIS way, both users may stIll beheve that they are dIrectly talking to each other, WIthoutreahzlng that the confidentiality and integrity of theIPpackets they receive have already been compromised (see Fig. 1.1).
1.2 Common Attacks and Defense Mechanisms
A
"
... ... ... ...
"""",
,
,,
13
B
A thinks that she is
talking to B directly The attacker intercepts ormodifies communicatio ns between A and B
B thinks that he is talking to A directly
FIg. 1.1 Man-In-the-mlddle attacks. The solid lines represent the actual cornmumcauons, and the dash line represents the perceIved commumcatIOn between user A and user B
Message Replays
Ina message replay attack, the attacker first Intercepts a legItImate message, keeps it intact, and then retransmits it at a later time to the original receiver. In some authentication protocols, for example, after user A proves herself to the system as a legitimate user, she will be given an authentication pass. With this pass, she will be able to obtaIn servIces provIded by the system. ThIs pass IS encrypted and so It cannot be modIfied. However, the attacker may Intercept It, keep a copy, and use It later to impersonate user A to get the services from the system.
Listed below are common mechanisms for thwarting message replay attacks. 1. Attach a random number to the message. This number is referred to asnonce.
When a user receives a message whose nonce appeared before, he knows that thIs message IS a replay whIch IS then dIscarded. ThIs method, however, reqUIres that users keep a record of every nonce they first encounter, whIch may not be practICal.
2. Attach a time stamp to the message. When a user receives a message whose time stamp is old, he knows that this message is a replay. This method, however, requires that all networked computers be synchronized with little error. While not a problem In local area networks, accurate synchromzatlOn IS dIfficult to achIeve In wIde area networks.
3. The best method to thwart message replay attacks is to use a nonce and a time
ウエ。ューセァ・エィ・イN Using this method, synchronization does not have to be very
14
Network Spoofing
1 Network Security Overview
IP spoofing is one of the major network spoofing techniques. Itconsists of SYN flooding, TCP hijacking, andARP spoofing. ARP spoofing is also referred to as
ARP poisoning.
SYN Flooding
SYN flooding exploits an implementation side effect of the TCP/IP network proto-cols. In a SYN flooding attack, the attacker fills the target computer's TCP buffer with a large volume of SYN control packets, making the target computer unable to establish communications with other computers. When this happens, the target computer is called amutedcomputer or asilencedcomputer. The TCP buffer is a set of contiguous memory locations allocated by the underlying network applica-tion program.Itis used to store TCP packets that have been received, but not yet processed.
To launch a SYN floodIng attack agaInst a target computer, the attacker sends to It a large number ot crafted SYN packets, eachrequestingto estabhsh TCP connec-tions. The term crafted SYN packetmeans that the source address contained in the SYN packet is a legitimate IP address, but the host computer on that address is not reachable. ThIs host computer may be powered ott or taken ott the network. We call such a computer adeadcomputer. DetectIng whether an IP address IS unreachable can be done USIng thepingcommand (or other commands In case a hve computer has been hardened to not respond to the ping command). If an IP address does not respond to ping, then it is probably unreachable. The ping command is a common network management tool based on the ICMP protocol. The attacker uses crafted SYN packets to aVOId beIng tracked down. And he uses a legItImate source IP address to ensure that the crafted SYN packets wIll be dehvered to ItS destInatIOn, because the domain name server will drop IP packets with fake IP addresses.
1.2 Common Attacks and Defense Mechanisms
TCP Hijacking
15
Suppose computer V is a company computer and user A is an employee of that company and is going to log on to computer V from home. User A's computer sends a SYN control packet to V and now suppose that an attacker intercepts this packet. The attacker then uses the SYN flooding attack to mute computer V, so that V cannot complete the three-way handshake protocol with user A's computer.
Ifthe attacker can predict the correct TCP sequence number for the ACK packet which is supposed to be sent to A from the muted computer V, then the attacker can craft an ACK packet and send it to user A's computer. The crafted ACK packet uses the correct TCP sequence number and V's IP address as the source IP address. User A's computer receives the ACK packet and verifies that it has the correct TCP sequence number.Itthen sends an ACK packet to the attacker to complete the three-way handshake procedure with the attacker. Thus, the TCP connection that user A's computer has established is with the attacker, instead of withV.
To see how this works, we note that the TCP protocol uses the sequence number m Its TCP header to IdentIfy whIch TCP packets belong to the same commUnIca-tion. FIg. 1.2 depIcts the TCPv4 header format. Since the TCP protocol header does
16-bit source port number 16-bit destination port number
32-bit sequence number
32-bit acknowledgement number
4-bit hdr
I
6 reservedI
Gcontrol bits IG-bit window size length bits16-bit TCP checksum 16-bit urgent pointer
FIg.1.2 The standard TCPv4 header format
not contain the source IP address, the TCP-layer software would not check the le-gItImacy of the IP addresses contamed m the IP header. See FIg. 1.3 for the standard IPv4 header format. The IP protocol routes the IP packet Itreceivesto the destma-tion based on the informadestma-tion contained in the IP header.Itdoes not keep track of the header information of previous IP packets it received. Thus, checking the source IP address at the IP layer does not help identify whether the source IP address in the current IP packet IS the same as those m prevIOus IP packets. ThIS shows that the workmg of the TCP/IP protocol sUIte (ItS early ImplementatIOn m partIcular) ac-tually makes TCP hlJackmg possIble. To stop TCP hlJackmg, It IS Important to use software (e.g.TCP wrappers)that checks IP addresses at the TCP layer.
16 I Network Security Overview
4-bit
I
4-bit hdI
8-bit type of service 16-bit total length (in bytes) version length (TOS)16-bit iedntification number 3-bit
I 13-bit fragmentation offset flags
8-bit time to live
I 8-bit protocol 16-bit header checksum (TTL)
32-bit source IP address
32-bit destination IP address
FIg.1.3 The standard IPv4 header format
ARP Spoofing
Computers are identified by unique MAC (media access control) addresses. MAC addresses are also called physical addresses. ARP is an address resolution protocol at the lInk layer, whIch converts the destInatIOnIPaddress In the IPheader to the MAC address of the underlYIng computer at the destInatIOn network. Inan ARP spoofing attack, the attacker changes the legItImate MAC address of an IPaddress to a different MAC address chosen by the attacker (see, e.g. Exercise 1.7).
To prevent ARP spoofing attacks, checking is the key.Inparticular, we should strengthen checking procedures of MAC addresses and domain names, and make sure that the source IPaddress and the destInatIOnaddress In anIPpacket have not been changed dUrIngtransrmssions,
1.2.5 Buffer-Overflow Exploitations
Buffer overflow, also referred to as buffer overrun, is a common software flaw. A buffer is a set of contiguous memory locations allocated to a process. The size of the buffer is fixed in its declaration in the program. A buffer overflow occurs if the process WrItes more data Into the buffer than It can hold. The follOWIng IS a SImple C program that WrItes the buffer of eIght bytes WIth astring str of 34 bytes, causingIt to overflow.
int main () { char buffer[S];
char *str - "Th1S lS a test of buffer overflow."; strcpy(buffer, str);
printf("%s", buffer);
1
1.2 Common Attacks and Defense Mechanisms 17
Fig.1.4Typicalmemory
layout for functio n call low addresses
high addresses
buffer
t
t
return address
function parameters
hcap
stack
the return address of the functIOn canIs placed In astack.The stack IS In the hIgher end of the memory space, whIle the heap IS In the lower end, where they grow to-wards each other and shrink away from each other (see Fig. 1.4). Listed below are general steps of this type of attacks:
1. Find a program that is vulnerable to buffer overflows. For example, programs that use string-based functions (e.g.strcpy () andstrcat ( ) )are vulnerable, for they do not check bounds. These functIOns would copy as many characters as pOSSIble untIl a NULL byte IS encountered.
2. FIgure out the address of the attacker's code.
3. Determine the number of bytes that is long enough to overwrite the return ad-dress.
4. Overflow the buffer that rewrites the original return address of the function cal1 wIth the address of the attacker's code.
In realIty, explOItIngbuffer overflows to breach secuntyIS often a complex and dIfficult procedure.
The best way to prevent buffer overflow attacks is to close the doors of over-flow. That is, one should always add statements to check bounds when dealing with buffers in a program. Avoid using string functions that do not check bounds.
1.2.6 Repudiation
In some SItuatIOns the owner of the data may not want to admIt ownershIp of the data to evade legal consequences. He may argue that he has never sent or receIved the data1I1question.RepudIatIon IS straIghtforwardIfthe data has not been
18 1 Network Security Overview
underlying authentication methods or the communication protocols contain loop-holes. The owner of the authenticated data may be able to convince the judge that, because of the loopholes, anyone could have easily fabricated the message and made it look like it was produced by him.
Using secure encryption and authentication algorithms can help prevent repudi-ation attacks.
1.2.7 Intrusion
Intrusion in network security means that an illegitimate user, i.e. the intruder, gains access to someone else's computer systems. The intruder may turn a victim's com-puter into his own server which may result in stolen computing resources and net-work bandwidth from the victim. The intruder may also steal useful information residing in the victim's computer.
ConfiguratIOn loopholes, protocol flaws, and software SIde effects may all be explOIted by Intruders. OpenIng TCP or UDP ports that should not be open IS a common configuratIOn loophole. TCP and UDP ports are entry pointsof network application programs.
Intrusion detection is a technology for detecting intrusion incidents. Closing TCP and UDP ports that may be explOItedby Intruders can also help reduceintrusions.
IP Scans and Port Scans
IP scans andport scans are common hacking tools. IPscans search for existing IPaddresses In the Internet, and port scans search for open ports In a computer. Attackers useIPscans to search for potentIal targets and use port scans to IdentIfy open ports that are vulnerable in the targets.
However,IPscans and port scans can also help users to identify in their own sys-tems which ports are open and which ports may be vulnerable. Several such prod-ucts are avatlable. For example, ShieldsUP! of GIbson Research CorporatIOn
andNessusof Southwest Research Institute are two such products (see Exercise
1.10).
1.2.8 Traffic Analysis
1.2 Common Attacks and Defense Mechanisms 19
the port numbers can also be obtained. This information can be used to learn which application program is used to read the message. When preparing for a big event, in-dividuals or organizations may frequently exchange messages before the event takes place. Ifthe traffic analyzer learns this information from analyzingIPheaders, an attacker may conclude that something big is about to happen.
The best way to combat traffic analysis is to encryptIPheaders. But anIPpacket with an encryptedIPheader cannot be routed to the destination. Thus, a new plain-text IPheader must be inserted in front of the encryptedIPheader for delivery. This may be done using a network gateway. A gateway is a special-purpose com-puter shared by many users in the local network. Itcan encrypt an user'sIPpacket (including its header) at the sending side, decrypt the encryptedIPpacket at the receiving side, and forward it to the destination MAC address.Ifthere are no other routers between the sending-side gateway and the sender's computer, and there are no other routers between the receiving-side gateway and the receiver's computer, then traffic analysis can only reveal that the two gateways are talking to each other (see Fig. 1.5), without gaining any information about which user behind one gate-way IS talkmg to whIch user behmd the other gategate-way.
--セ Gateway B
セt cpー 。 」ォ ・エ ャ
(3)
-
-z:
セ tc p ー 。」 ォ ・ エャ(2)
セ
ャ セ d
セ g 。 エ 」 キ 。 ケ a
Sender
Fig. 1.5 Using gateways to encrypt IP packets.(I)Sender forwards an IP packet to gateway A
at the sending side. (2) Gateway A encrypts sender's IP packet (the shaded part) and routes it to the next router m the Internet. (3) The IP packet from Gateway A IS delIvered to gateway B at the receiving side, with certain attributes (e.g. TTL) in the plaintext IP header (shown as the unshaded part) modIfied. (4) Gateway B removes Its header, decrypts the encrypted IF packet of the sender, and forwards it to the receiver
1.2.9 Denial of Service Attacks
com-20 I Network Security Overview
puter to process a large number of useless things, hoping to consume all its critical resources. A denial of service attack, denoted by DoS, may be launched from a sin-gle computer, or from a group of computers distributed in the Internet. The latter attack is called adistributed denial ofservice attackand is denoted by DDoS.
DoS Attacks
SYN flooding is a typical and effective technique used by DoS attacks. The smurf attack is another typical type of DoS attack, where smurfis the name of the soft-ware used to execute the attack. Itsends an excessive number of messages to the target computer and crashes it by consuming all its resources. In a typical smurf attack, the attacker sends crafted ping requests to a large number of computers within a short period of time, where the source IP address in the craftedping re-quest is replaced with the victim's IP address. According to the ICMP protocol, a computer that receives aping request will respond to the source IP address with apongmessage, mformmg the sender that "I am alIve". Therefore, each computer that receIves the crafted pingrequest wIll respond to the vIctIm's computer wIth a pongmessage. Forced to process a large number ofpongmessages wlthm a short period of time, the victim's computer will use up its computing resources and crash (see Fig. 1.6). Thus, the idea ofsmurfattacks is to crash a single target with a lot of borrowed hammers.
Attacker
F'lg.1.6Smurtattack
DDoS Attacks
ping ping
Nセ
ェM ⦅ MGMMM M]MM ⦅ セ i
-pong
Victim's web server
A typical DDoS attack Rroceeds according to theヲッャャッキゥョセオ・ョ」・Z
1.2 Common Attacks and Defense Mechanisms 21
2. Install special software in the compromised computers to carry out a DoS attack at a certain time later. Such software is calledzombie software and such a com-puter is called azombie computeror simply azombie. A collection of zombies is also called azombie army, which is now typically called abotnet.
3. Issue an attack command to every zombie computer to launch a DoS attack on the same target at the same time.
Fig. 1.7 depicts a DDoS attack. Upon receiving the attacker's command, each zombie computer uses SYN flooding to mute the victim's Website.
Victim's web server
SYN/ACK
dead host
B ャ ᄋ セ
i⦅[セZZBGZBG [Z
iセMMMMセ
-I _
'=.:./'il
----,
Zombiesセ S セ
セNZセMMMMMMMゥ
Attackerdead host
FIg. 1.7 A DDoS attack using SYN floodmg to mute the victim's WebsIte
Special software tools such as Zombie Zapper(see Exercise 1.11) have been developed and used to detect and stop zombIes.
In 2000, for example, a 15-year-old hIgh-school student In Montreal, Canada,
wIth an assumed name "Mafiaboy", launched a DDoS attackagainstWeb servers of several major companies and paralyzed these Web servers for a week. These com-panies, including Amazon, Cable News Network, eBay, E*Trade, Dell, and Yahoo!, suffered substantIal financIal losses because of thIs attack. Mafiaboy was sentenced to spend eIght months Ina youth detentIOncenter.
SpamMaii
22 I Network Security Overview
Standard electronic messaging systems have made it possible for individuals and companies to send unwanted bulk messages to people. Such individuals or compa-nies are often referred to asspammers.Spamming can occur in any form of network applications, but email spam is by far the most common spamming form. According to a recent statistics, about half a billion spam emails are sent in every single day. In other words, each email user is expected to receive about eight spam messages a day. Spamming also occurs in Web search engines, Instant Messaging, blogs, mobile phone messaging, and other network applications.
Spamfillersare software solutions to detect and block spam mails from reaching the user's mailbox
1.2.10 Malicious Software
Software intended to harm computers ismalicious software.Malicious software is also referred to as malware.Common forms of mabclOus software mclude virus, worms, Trojan horses, logic bombs, backdoors,andspyware.
Viruses and Worms
A computer VIruS IS a pIece of software that can reproduce Itself. However, a VIruS IS not a stand alone program. In other words, It must attach Itself to another program or another file. A program or file that contains a virus is called aninfected host.An uninfected host is also called ahealthy host. When an infected host is transmitted to another computer, the virus that lives in it also is transmitted. The execution of a VIruS IS InItIated by the mfected host. Namely, only when an mfected program IS executed or an mfected file IS opened, a VIruS contamed m It may get executed. When executed, a virus may do harm (e.g. delete system files) to the system where its host resides or replicate itself to infect other healthy hosts in the system.
A computer worm is also a piece of software that can reproduce itself. Unlike a VIruS, a worm IS a stand alone program. In other words, It does not need a host to bve m. A worm can execute Itself at any tIme It WIshes. When executed, a worm may do harm to the system where It reSIdes or repbcate Itself to other systems through networks.
There are two common measures to combat viruses and worms. One measure deploys virus scansto detect, quarantme, and delete mfected hosts and worms. The other measure, consisting of the foIIowmg rules, blocks virusesand worms from entenng a computer:
1. Do not download software (e.g. games) from un-trusted Websites or other sources. 2. Do not open any executable file gIven to you by someone you do not know. 3. Make sure software patches are mstaIIed and up to date.
1.2 Common Attacks and Defense Mechanisms 23
the Code Red worm, the Nimda worm, and the Code Red II worm. These worms made headline news and they all exploited the same loophole in lIS. Microsoft knew about this problem and provided a patch to correct it a year earlier. How-ever, many system administrators did not install this patch, and thus left wide open doors into their systems for the worms to come in and do damage.
Trojan Horses
The name Trojan horse came from a Greek legend. Legend has it that ancient Greeks, wanting to apprehend a beauty named Helen, attacked the fortified city of Troy but failed. Faking a retreat, the Greeks left behind a huge, hollow wooden horse with a number of soldiers hidden inside. Not suspecting any danger, the Tro-jans hauled the wooden horse inside the city as a trophy. At night, the Greek army returned, and the soldiers hidden inside the wooden horse went out and opened the city gates for the invasion troops to come in. The city of Troy fell.
Inthe realm of network secunty, Trojan horses are software programs that ap-pear to do one thIng, but secretly also perform other tasks. Trojan horses often dIsgUIse themselves as desIrable and harmless software apphcatlOns to lure peo-ple to download them. When they are executed by the user, the hidden functions contained in them which now have the user's access rights do harmful things se-cretly. Games and network management tools aVailable for free downloads from unknown Websltes often are Trojan horses. Trojan horses may also use appeahng names such asAntiSPYware. exeor Real_Player. exe (note that the real one isRealPlayer. exe)to trap users to use them.
The same measures of combating viruses and worms can also be used to combat Trojan horses. Virus scans can also detect, quarantine, and delete Trojan horses.
Logic Bombs and Backdoors
Logic bombs are subroutines or instructions embedded in a program. Their exe-cutIOn are tnggered by condItIOnal statements. For example, a company employee workIng on a development project may Install a logIC bomb InSIde a program. The bomb WIll be set off onlyIf the employee has not run the program In acertain pe-riod of time. When that condition is met, it would mean that the employee was fired some time before. The logic bomb in this case is used to gain revenge against the employer.
24 I Network Security Overview
We note that, with the increase of outsourcing software development projects and other vital tasks to other countries, the potential for logic bombs and backdoors also increases.
There are three measures to counter logic bombs. First, employers should always do their best to take care of their employees, so that none would be tempted to place a logic bomb. Second, project managers should hire an outside company or form a special team of reviewers from a different group of people other than the developers to review the source code. Third, relevant laws should be established so that employees who planted logic bombs will face criminal charges. With these countermeasures in place, unhappy employees would think twice before planting logic bombs in programs.
The major counter measure of backdoors is to check source code, which should be conducted by an independent team.
Spyware
Spy ware IS a type of software that mstalls Itself on the user's computer. Spyware IS often used to momtor what users do and to harass them wIth popup commer-cial messages. Browser hijackingand zombiewareare the most disastrous kinds of spyware.
Browser HIJackmg
Browser hijacking is a technique that changes the settings of the user's browsers.
Itmay replace the user's default Website with a different Website selected by the attacker. Or It may stop the user from visrtmg the Websltes he or she wants to VISIt.
Zombieware
Zombleware IS software that takes over the user's computer and tur