Context-Aware Service Discovery in the Internet of Things
Shiow-Fen Hwang, Guan-Yu Chen, and Chyi-Ren Dow
Department of Information Engineering and Computer Science, Feng Chia University {sfhwang, m0312301}@mail.fcu.edu.tw, crdow@fcu.edu.tw
ABSTRACT
The internet of things(IoT) has rapid de-velopment in recent years, so that it is becoming more and more important in our lives. There will be more than billions devices connected to the internet in the near future. How to find the services (or resources) we needed in the internet is an important issue. There are many researches concerning the issue and a lot of novel schemes are proposed. However, most of them do not take into account the delay time and have high control overhead.
Therefore, in this paper, we propose an efficient context-aware service discovery mechanism that employs a spanning tree and has shorter delay time, less control packets and energy consumption in the internet of things. First, a service discovery spanning tree is established according to the weights of nodes defined by the number of services, residual energy and distance. Then, an efficient service discovery mechanism is presented by using Bloom filter and the established spanning tree. Moreover, a maintenance mechanism is provided for nodes joining or leaving. Simulation results indicate that the proposed method outperforms TRENDY and CAEsAR in terms of the number of packets and average search time.
Keywords: Internet of things, service discovery, context-aware, spanning tree, weight.
1 INTRODUCTION
With the rapid development of wireless communications technology, many devices are equipped with chips to connect to the Internet or communicate with each other, and thus form a Internet of things(IoT). There are many applications of IoT, such as manufacturing, medical and heath care, transportation, environmental monitoring, smart meter, smart home, smart city, etc.
The problem of service discovery is essential in IoT. However, due to the limited power capacity of nodes, how to find the services efficiently is important. Although there are a lot of studies concerning service discovery, most of them just proposed the architecture [1] [2] [3] [4]. For those studies that have proposed protocols [5] [6] [7] [8] [9] [10] [11] [12] [13] [14], some of them are centralized which need a powerful management center, and thus have a high cost; while the decentralized protocols rely on broadcasting to search for services, so lead to packet flooding and long search time. Hence, we design a hybrid service discovery protocol to avoid these disadvantages.
and caching techniques. But there is still room for improvement.
Therefore, we propose a better service discovery method in the internet of things environments. Like TRENDY and CAEsAR, we adapt a tree architecture for discovering services. However, we define the weight of nodes by the number of services, residual energy and distance, so that the nodes with more services, high residual energy or smaller distance can be found early, and thus reduce the searching time.
2 CONTEXT AWARE SERVICE DISCOVERY
In this section, we propose an efficient service discovery and a maintenance mechanism in the internet of things networks.
2.1 Service Discovery Spanning Tree
We choose the most powerful node in received the message will return a packet with its weight to the root. The root informs the first k nodes of higher weight to be its children(if a node has no other neighbor or all its neighbors have already been in the current tree, it would have the highest priority to be When a node i returns the confirmed message to its parent, the level of i, l(i), is updated to
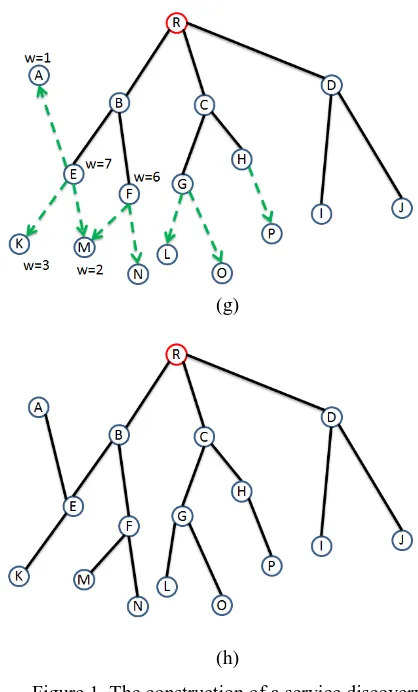
l(its parent) plus one. (Initially, the level of the root is zero, and the levels of the other nodes are null.) At the same time, a part of the service discovering spanning tree is constructed. Afterwards, every leaf node in the current tree does the same process as its parent until the whole service discovering spanning tree is completed. After the service discovery spanning tree is constructed, every leaf node sends a packet including its level, linked list and Bloom filter which records the service information to its parent node. A parent node collects all such packets from its children and sends it to its parent. Repeat the same process until the root node. At this time, every node has the service information of its subtree, while the root has the service information of all nodes. Figure 1 is an example of the construction of a service discovery spanning tree.(Assume that the value k of the root is 3 and the others are 2)
(a)
(c)
(d)
(e)
(f)
(g)
(h)
Figure 1. The construction of a service discovery spanning tree
2.2 Service Discovery Mechanism
With the service discovery spanning tree, if a node needs some services(resources), then it can query the root node. However, when the number of nodes is too large, there will be a numerous amount of stored data and a long searching time. In order to avoid this situation, we adapt linked lists and modify Bloom filter[16] to record service information. A Bloom filter is a bit array with predefined length and hash functions to represent a set of elements(services). Each service maps k bit positions of an array by k hash functions. And a linked list is established in the smallest of k bit positions to record the service name and the number of the service, as shown in Figure 2, the numbers of services S1, S2 and
Figure 2. A Bloom filter with linked list
In our service discovering spanning tree, each node has Bloom filters of itself, left subtree and right subtree, and applies OR operation to get the union of these Bloom filters to send to its parent for saving space. When a node is requested for searching some services, if it can satisfy the required services, then the service discovery is done. Otherwise, it will check the Bloom filters of subtrees. If a subtree has the required services, it will go down to query its child. (If there are more than one child with required services, choose the one that the maximum level of its leaves is minimum. If tie break occurs, choose the one with maximum number of the required service and the highest weight in the order of priority.) Repeat the process until the request is satisfied or no required service exist. In Figure 3, the root R receives a query for service S3. It checks the Bloom filter of right
subtree, WBF ˅ ZBF, (finds that service S3
exists) and then sends the query to its child W. Finally, service S3 is founded in Bloom filter
ZBF by W.
Figure 3. A Bloom filter with linked list for service discovery
in the cases of external request and internal request, respectively.
Figure 4. An external request for service discovery
Figure 5. An internal request for service discovery
2.3 Maintenance
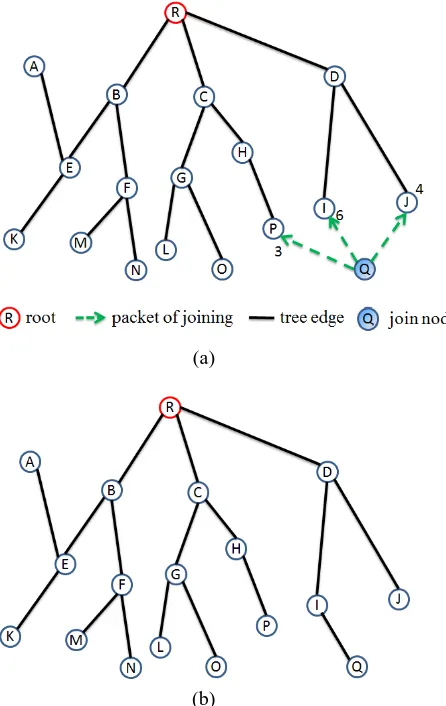
If a new node would like to join the service discovery spanning tree, it will broadcast a message to neighbors. Those which receive the message and are able to have more children return messages with their weights and levels. The new node choose the one with the smallest level(or the maximum weight if tie break) as its parent, and sends a confirmed message including its weight, level and services to its parent. After receiving the message, all information stored in its ancestors have to be updated. Figure 6 is an example of the maintenance for node joining.
(a)
(b)
Figure 6. The maintenance for node joining
(a)
(b)
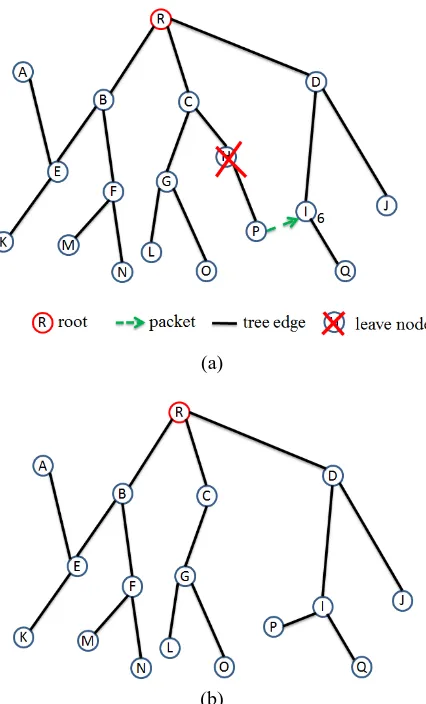
Figure 7. The maintenance for node leaving
3 SIMULATION RESULTS AND ANALYSIS
We evaluate the performance of the proposed mechanism and compare to TRENDY[9] and CAEsAR[10] according to the different transmission ranges and number of services of nodes in terms of the average search time and number of packets.
The simulator Cooja and OS Contiki are used for simulation. The simulation environment size is 50m x 100m to 100m x 200m. The number of services of a node is 2 to 6, and the average number is 3. Table 1 is the simulation parameters.
Table 1. simulation parameters
Parameters Value
Transmission Range
30m、40m、50m
Number of Nodes
10、15、20、25、30
α、 、 0.5、0.2、0.3
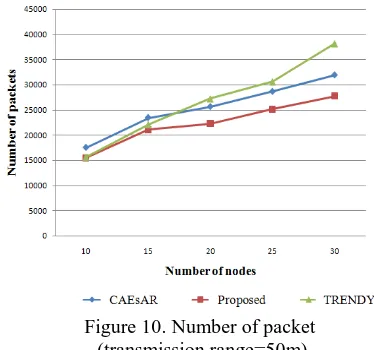
Figure 8 to Figure 10 show the number of packets for all schemes when the transmission range are 30m, 40m and 50m, respectively. The results indicate that the proposed scheme has less number of packets than the others. This is because the proposed scheme supports multiple service search by modified Bloom filter and linked list, and usually searches the services near the requester by the use of level.
Figure 8. Number of packet (transmission range=30m)
Figure 10. Number of packet (transmission range=50m)
Figure 11 to Figure 13 are the impacts of the number of nodes versus the average search time under the transmission ranges of 30m, 40m and 50m, respectively. The average search time increases obviously as the number of nodes increase in CAEsAR, while the proposed scheme and TRENDY increase slowly, especially under transmission ranges of 40m and 50m. This is because the distance and the number of services are taken into account for constructing the service discovery spanning tree in the proposed scheme, and TRENDY is centralized.
Figure 11. Average search time (transmission range=30m)
Figure 12. Average search time (transmission range=40m)
Figure 13. Average search time (transmission range=50m)
4 CONCLUSIONS
By establishing the service discovery spanning tree and modifying Bloom filter, we propose a context-aware service discovery mechanism in the internet of things. Simulation results show that our proposed mechanism has less number of packets than TRENDY and CAEsAR, and also has shorter search time than CAEsAR.
ACKNOWLEDGMENTS
This work was partially supported by the Ministry of Science and Technology, Taiwan, R.O.C. under Grants MOST-105-2221-E-035-059-.
REFERENCES
the 2006 international conference on Embedded and Ubiquitous Computing, vol. 4096, pp. 956-965, August 2006.
[2] J. Leguay, K. Jean-Marie, M. Lopez-Ramos, and V. Conan, “An Efficient Service Oriented Architecture for Heterogeneous and Dynamic Wireless Sensor Networks,” 2008 33rd IEEE Conference on Local Computer Networks (LCN), pp. 740-747, October 2008.
[3] A. Jara, P. Lopez, D. Fernandez, J.F. Castillo, M.A. Zamora, and A.F. Skarmeta, “Mobile Digcovery: A Global Service Discovery for the Internet of Things,” 2013 27th International Conference on Advanced Information Networking and Applications Workshops, pp. 1325-1330, March 2013.
[4] S. Cirani, L. Davoli, G. Ferrari, R. Léone, P. Medagliani, M. Picone, and L. Veltri, “A Scalable and Self-Configuring Architecture for Service Discovery in the Internet of Things,” IEEE Internet Of Things Journal, vol. 1, no. 5, pp. 508-521, September 2014.
[5] D. Parlanti and F. Paganelli, “A DHT-Based Dis-covery Service for the Internet of Things,” Journal of Computer Networks and Communications, vol. 2012, pp. 1-11, September 2012.
[6] G. Oikonomou, I. Phillips, L. Guan, and T. A. Butt, “Adaptive and Context-Aware Service Discovery for the Internet of Things,” 13th International Conference, NEW2AN 2013 and 6th Conference, ruSMART 2013, vol. 8121, pp. 36-47, August 2013.
[7] A. Kovacevic, J. Ansari, and P. Mahonen, “Na -noSD: A Flexible Service Discovery Protocol for Dynamic and Heterogeneous Wireless Sensor Networks,” 2010 Sixth International Conference on Mobile Ad-hoc and Sensor Networks, pp. 14-19, December 2010.
[8] D. Schoder, K. Fischbach, and N. Schoenemann, “PβP architecture for ubiquitous supply chain systems,” 17th European Conference on Information Systems, pp. 2255-2266, June 2009.
[9] G. Oikonomou, I. Phillips, L. Guan, and T. A. Butt, “TRENDY: An Adaptive and Context-Aware Service Discovery Protocol for 6LoWPANs,” WoT '12 Proceedings of the Third International Workshop on the Web of Things, pp. 4-9, June 2012.
[10]A. Kalmár, M. Maliosz, and R. Vida, “CAEsAR : A Context-Aware Addressing and Routing Scheme for RPL Networks,” 2015 IEEE International Conference on Communications (ICC), pp. 635-641, June 2015.
[11]G. Min, L. Liu, R. Chen, and Z. Li, “Dynamic Re -source Discovery based on Preference and Movement Pattern Similarity for Large-Scale Social Internet-of-Things,” IEEE Internet Of Things Journal, vol. 3, no.4, pp. 581-589, June 2015.
[12]B. Djamaa and R. Witty, “An Efficient Service Discovery Protocol for 6LoWPANs,” 2013 Science and Information Conference, pp. 645-652, October 2013.
[13]A. ElMougy and R. Helal, “An Energy-Efficient Service Discovery Protocol for the IoT based on a Multi-Tier WSN Architecture,” 2015 IEEE 40th Local Computer Networks Conference Workshops, pp. 862-869, October 2015.
[14]D. Guinard and S. Mayer, “An Extensible Dis-covery Service for Smart Things,” WoT '11 Proceedings of the Second International Workshop on Web of Things, pp. 7, June 2011.
[15]T. Winter, P. Thubert, A. Brandt, J. Hui, R. Kelsey, P. Levis, K. Pister, R. Struik, J. Vasseur, and R. Alexander, “RPL: IPv6 Routing Protocol for Low-Power and Lossy Networks,” RFC 6550 (Proposed Standard), March 2012. [Online]. Available: http://www.ietf.org/rfc/rfc6550.txt.
[16]B.H. Bloom, “Space/Time Trade-Offs in Hash Coding with Allowable Errors,” Communications of the ACM, vol. 13, no. 7, pp. 422-426, July 1970.