IJCSI
IJCSI
International Journal of
Computer Science Issues
Volume 10, Issue 2, No 2, March 2013
ISSN (Online): 1694-0784
ISSN (Print): 1694-0814
© IJCSI PUBLICATION
www.IJCSI.org
IJCSI proceedings are currently indexed by:
©
IJCSI PUBLICATION 2013
TABLE OF CONTENTS
1. A New IPFM Based Model For Artifitial Generating Of HRV With Random Input
Gholamreza Attarodi, Nader Jafarnia Dabanloo, Zahra Abbasvandi and Nazanin Hemmati
1-5
2. Hybrid Swarm Intelligence Technique for CBIR Systems
Anil Kumar Mishra, Madhabananda Das and T.C.Panda
6-11
3. Efficient Algorithm for Near Duplicate Documents Detection
Gaudence Uwamahoro and
12-18
4. Influence of Project Duration constraint on efforts in Constructive Cost Model and
optimizing the efforts to obtain accuracy
Brajesh Kumar Singh and A. K. Misra
19-25
5. Awareness-Usability Issues in IT-initiatives for difficult geographies
Kamal Kumar Ghanshala and Durgesh Pant
26-30
6. Cross Layer Optimized Transmission for an Energy Efficient Wireless Image Sensor
Network
Alice Abraham and Narendra Kumar G
31-38
7. Energy Aware Adaptive Image Transmission Scheme with Data Authentication in Wireless
Sensor Networks
Alice Abraham and Narendra Kumar G
39-46
8. A Comparison Between Present and Future Models Of Software Engineering
Harikrishnan Natarajan, Ram Kumar Somasundaram and Kalpana Lakshmi
47-50
9. Combining Web SCADA Software and Matlab-Simulink for Studying Wind-PV-Battery
Power Systems
Aryuanto Soetedjo, Abraham Lomi2, Yusuf Ismail Nakhoda3 and Yohan Pramono Tosadu
51-57
10. Larg Band Ridged Waveguide Polarizer as Feed for Telecommunications Satellites
Antennas
Bousalah Fayza
58-62
11. Categorizing ancient documents
Nizar Zaghden, Rémy Mullot and Mohamed Adel Alimi
63-72
12. Suggested method for Estimating Maximum Capacity of images for different intensities
Thekra Abbas, Zou Beiji and Ongalo P.N.Fedha
73-82
13. Sliding Mode ANFIS-Based MIMO Fuzzy Neural Network Control for Robotic Systems
Yi-Jen Mon
83-86
14. Conceptual Understanding of Computer Program Execution: Application to C++
Sabah Al-Fedaghi
91-101
15. Anti-surge Control Technologies of LargeCsized Chinese Gas Compression Pump
Liu Xiaoyang
102-107
16. Optimization and Application of initial Value of Non-equidistant New Information
GM(1,1) Model
Youxin Luo
17. Improvement and Application of Initial Value of Non-equidistant GM(1,1) Model
Youxin Luo
113-118
18. Non-equidistant GRM(1,1) Generated by Accumulated Generating Operation of
Reciprocal Number and its Application
Youxin Luo, and
119-123
19. Based on RFID Products Information Tracing Anti-counterfeiting Strategy Design and
Application
Jiao Yabing
124-129
20. Person Name Recognition for Uyghur Using Conditional Random Fields
Muhtar Arkin, Abdurahim Mahmut and Askar Hamdulla
130-136
21. Supply Chain Coordination Research under a Fuzzy Decision Environment
Shengju Sang
137-142
22. The Echelon Pattern and Its Key Technologies of Urban Circle Solid Waste Disposal
Xuhui Li, Gangyan Li, Guowen Sun, Huiping Shi and Baoan Yang
143-149
23. A Fitting Approach to Mend Defective Urban Traffic Flow Information Based on SARBF
Neural Networks
Ning Chen, Weibing Weng and Xing Xu
150-155
24. Predicting the Severity of Breast Masses with Data Mining Methods
Sahar A. Mokhtar and Alaa M. Elsayad
160-168
25. Fusion of Physical Extraction Parameter Model Optical and SAR Data for Flood
Detection
Wawan Setiawan and Wiweka
169-176
26. A Search Algorithm Oriented to XML Keywords
Xingyuan Li
177-183
27. Application of equivalent permeability in numerical simulation of horizontal wells in
bottom water reservoirs
Li-Feng Li, Bing-Bing Wang and Xiang-An Yue
184-189
28. An Improved Cost-Efficient Thinning Algorithm for Digital Image
Liang Jia and Zhenjie Hou
190-197
29. Data Mining Framework for Direct Marketing: A Case Study of Bank Marketing
Lilian Sing\'oei and Jiayang Wang
198-203
30. The Implementation of Univariate and Bivariate B-Spline Interpolation Method in
Continuous
Dian Pratiwi
204-210
31. Design of a Radioactive Source Sampler Based on CPAC
Bin Yang and Zhenyu Wang
211-216
32. Android-based Java Programming for Mobile Phone LED Control
Yi-Jen Mon
217-222
33. Fuzzy Logic Method for Evaluation of Difficulty Level of Exam and Student Graduation
34. Application of optimal control theory to an SEIR model with immigration of infectives
Elhia Mohamed
230-236
35. Profit-Aware DVFS Enabled Resource Management of IaaS Cloud
Shahzad Ali
237-247
36. Vision-Based Obstacle Avoidance Controller Design for Mobile Robot by Using Single
Camera
Yi-Jen Mon
248-250
37. Post-processing of Engineering Analysis Results for Visualization in VR System
Stoyan Maleshkov and Dimo Chotrov
258-263
38. Parallel and distributed closed regular pattern mining in large databases
M.Sreedevi and L S S Reddy
264-269
39. Dynamic Forensics Model based on Ontology and Context Information
Baoxian Jia and Weiqiang Yang
270-272
40. Peripheral Contour Feature Based On-line Handwritten Uyghur Character Recognition
Zulpiya Kahar, Mayire Ibrayim and Askar Hamdulla
273-278
41. Modified TCP Protocol for Wireless Sensor Networks
Hesham Abusaimeh and Mohammad Shkoukani
279-285
42. Differential Evolution with (u+T)-Selection Technique
Miao-Miao Liu, Pan Huo and Wen-Yin Gong
286-293
43. ANFIS Transient Control for Double Inverted Pendulum System
Yi-Jen Mon
294-297
44. Dynamic Analysis for Video Based Smoke Detection
Chen Junzhou, You Yong and Peng Qiang
298-304
45. Design and Simulation of Gate Driver Circuit Using Pulse Transformer
Daizhuang Wang, Haifeng Dai and Zechang Sun
305-310
46. Studied and Their Application of Vibration Control Technologies
Ying Sun, Yuesheng Gu and Hegen Xiong
311-318
47. An Ensemble Monte Carlo Model to Calculate Photocurrent of MSM Photodetector
Mohammad Soroosh and Yasser Amiri
319-324
48. Evaluation of a Proposed Intelligent Transportation Framework using Computer
Network Concepts: A Case Study for Hajj-Pilgrim Traffic Monitoring and Control
Omar Tayan and Abdullah Al-Binali
325-330
49. A New Scheme Based Biometric to Protect Location Privacy in Wireless Body Area
Networks
Mohammed Mana, Mohamed Feham and Boucif Amar Bensaber
331-337
50. Simulation of Efficient Real-time Scheduling and Power Optimization
Rym Cheour, Urunuela Richard, Yvon Trinquet and Mohamed Abid
338-346
51. Web Usage Mining: Data Preprocessing and Multi Level analysis on Moodle
52. Performance Comparison of MIMO Systemsover AWGN and Rician Channels using
OSTBC3 with Zero Forcing Receivers
Navjot Kaur and Lavish Kansal
355-364
53. A New Secure Geographical Routing Protocol Based on Location Pairwise Keys in
Wireless Sensor Networks
Haixia Zhao, Yaowei Li, Jincheng Shen, Mingchuan Zhang, Ruijuan Zheng and Qingtao Wu
365-372
54. A Superlinearly feasible SQP algorithm for Constrained Optimization
Zhijun Luo
373-379
55. Performance Analysis of ST,SF and STF IN MIMO-OFDM Technique
M.Vijaya Laxmi and S.Narayana Reddy
380-384
56. Deployment of Palm Recognition Approach using Image Processing Technique
Jugal Kishore Patel and Sanjay Kumar Dubey
385-390
57. A Linear Active Disturbance Rejection Control applied for DFIG based Wind Energy
Conversion System
Ali Boukhriss, Tamou Nasser and Ahmed Essadki
391-399
58. The Gray images of linear codes over the ring F3+vF3+v2F3
Yazhou Xiong, Shujie Yun, Jingyuan Xing and Xiaofang Xu
400-405
59. Multi-Objective Particle Swarm Optimization for Facility Location Problem in Wireless
Mesh Networks
Tarik Mountassir, Bouchaib Nassereddine, Abdelkrim Haqiq and Samir Bennani
406-413
60. Failure Detection and Recovery in Hierarchical Network Using FTN Approach
Bhagvan Krishna Gupta, Ankit Mundra and Nitin Rakesh
414-421
61. Handwritten Word Recognition Using MLP based Classifier: A Holistic Approach
Ankush Acharyya, Sandip Rakshit, Ram Sarkar, Subhadip Basu and Mita Nasipuri
422-427
62. Proposal to Enhance AntNet Routing Algorithm by Exploiting Association Rules as
Analysis Tool
Soukaena Hassan Hashem
428-437
63. Intelligent Online Education Transformation System
Rashmi Chahar, Anubhav Agarwal, Vipul Malhotra, Rahul Jain and Ashish Chandiok
438-444
64. A Taxonomy of Enterprise ArchitectureFramework for Indonesian SMEs
Ambar Yoganingrum, Dana Indra Sensuse and Aniati Murni
445-452
65. Design an electronic system for computer communication between hospital departments
(card desk)
Samaneh Haji Mohammad Bagher, Ali Amini, Javad Aryatabar and Hossein Akhavan
Zanjani
453-456
66. Vehicle logo classification using support vector machine Ensemble
Wesal Abdallah and Li Hong
458-462
67. OpenMP performance analysis for many-core platforms with non-uniform memory
access
Pablo González De Aledo Marugán, Javier González-Bayón, Pablo Sánchez and Juan Casal
68. Hybrid Framework for Robust Multimodal Face Recognition
Mostafa Mohamed Mohie El-Din, Mohamed Yousri El Nahas and Hassan Ahmed Hassan
Elshenbary
471-476
69. Recognition of leaf based on its tip and base using Centroid Contour Gradient
Mei Fern Bong, Ghazali Bin Sulong and Mohd Shafry Bin Mohd Rahim
477-482
70. Texture Based MRI Image Retrieval Using Curvelet With Statistical Similarity Matching
K.Rajakumar and S.Muttan
483-487
71. Improved Mobile WiMax Image Privacy Using Novel Encryption Techniques
Mohamed Abdel-Azim Mohamed, Fayez Wanis Zaki and Awny Mohsen El-Mohandes
488-495
72. Modeling Unstructured Document Using N-gram Consecutive and WordNet Dictionary
Abdul Halim Omar
496-504
73. General Approach for Energy Conservation in Wireless Sensor Networks
Alami Chaibrasou and Ahmed Mouhsen
505-508
74. A Visual and Interactive Learning Tool for CPU Scheduling Algorithms
Sukanya Suranauwarat
509-518
75. Secure and Effective P2P Reputation System using Trust Management and Self Certified
Cryptographic Exchanges
Srikanth Mavuri and K B Madhuri
519-525
76. Singularly perturbed Quasilinear Boundary Value Problems With Interior Shock Layer
Behavior
Ghoul Rafia and Ni Yu-Dong
526-530
77. Evaluation of Regional Benchmark Impact in EDM
Fuzzy Logic Method for Evaluation of Difficulty Level of
Exam and Student Graduation
Rusmiari1, Darma-Putra 2 and Arya-Sasmita3
1 Department of Information Technology, Udayana University Bali, 80119, Indonesia
2
Department of Information Technology, Udayana University Bali, 80119, Indonesia
3 Department of Information Technology, Udayana University
Bali, 80119, Indonesia
Abstract
Application of fuzzy logic in processing student evaluation, are expected to represent the mechanisms of human thought processes capable of resolving the problem of evaluation of students, which can be monitored by the teacher directly. With a system of evaluation of student test results by using fuzzy logic will be able to support the needs of teachers as well as those related to monitor student progress so that it can support the success of students. In the Fuzzy Logic method for each criterion are defined into 4 fuzzy set, low, medium, high and very high. item about the difficulty level, the level of difficulty of exams and graduation rates of students and participants ranked the Fuzzy Logic method is the output of the system. Fuzzy Logic will consider both the value of the criteria used, if the difficulty level is very difficult problems and low student scores in a fuzzy set criterion is high, then the student is graduating. This means more equitable Fuzzy Logic in reaching a decision and determine graduation.
Keywords: Fuzzy Logic, student evaluation, Inference engine.
1.
Introduction
Fuzzy logic has the advantage of modeling the qualitative aspects of human knowledge, and decision making as done by human beings by applying the rule base. Modern information management systems enable the recording and the management of data using sophisticated data models and a rich set of management tools [1]. Application of fuzzy logic in the processing of student test evaluation, expected to represent the mechanism of human thinking processes to solve problems of student exams. With a system of evaluation of students exam results by using fuzzy logic will be able to support the needs of teachers as well as those related tomonitor student progress so as to support its students success.
Fuzzy set theory was proposed in 1965 by Zadeh to help computers reason with uncertain and ambiguous information. Zadeh proposed fuzzy technology as a
means to model the uncertainty of natural language [1],[2]. He reasoned that many difficult problems can be expressed much more easily in terms of linguistic variables. Linguistic variables are words and attributes which are used to describe certain aspects of the real world. One important feature of linguistic variables is the notion of their utility as an expression of data compression. Zadeh describes this as compression granulation. He argues that this is important because it is more general than use of discrete values. This point means that an agent using linguistic variables may be able to deal with more continuous and robust descriptions of reality and problem spaces. Our approach is to design a fuzzy rule base system to control training process.
Fuzzy logic is powerful problem solving methodology with a myriad of applications in embedded control and information processing. Fuzzy provides a remarkably simple way to draw definite conclusions from vague, ambiguous or imprecise information. In a sense, fuzzy logic resembles human decision making with its ability to work from approximate data and find precise solutions.
Unlike classical logic which requires a deep understanding of a system, exact equations, and precise numeric values, fuzzy logic incorporates an alternative way of thinking, which allows modeling complex systems using a higher level of abstraction originating from our knowledge and experience. Fuzzy logic allows expressing this knowledge with subjective concepts such as very hot, bright red, and a long time which are mapped into exact numeric ranges [3].
Fuzzy logic has the advantage of modeling the qualitative aspects of human knowledge, as well as decisions made by humans by applying the rules of the rule base or bases. Application of fuzzy logic in processing student evaluation, are expected to represent the mechanisms of human thought processes
IJCSI International Journal of Computer Science Issues, Vol. 10, Issue 2, No 2, March 2013 ISSN (Print): 1694-0814 | ISSN (Online): 1694-0784
www.IJCSI.org 223
capable of resolving the problem of evaluation of students, which can be monitored by the teacher directly.
With a system of evaluation of student test results by using fuzzy logic will be able to support the needs of teachers as well as those related to monitor student progress so that it can support the success of students. Modern management information system allows in terms of recording and management of data using sophisticated data models and advanced management. In the context of the education system, the information usually includes details about the learning materials, tasks associated with student assignments, exams, and other notes. With the expert system is expected to reduce underarm accuracy of information and simplify the access to information systems, in terms of fuzzy modeling. Fuzzy rule-based system can be considered as a good reference for evaluating the test and quality assurance of an organization for students.
2.
Methodology
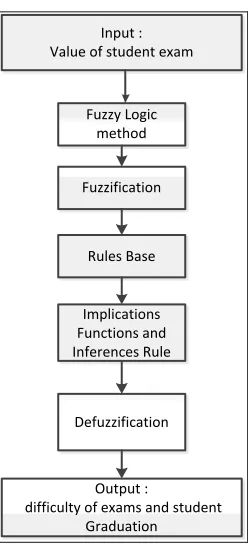
This system is designed for evaluating and teaching the students so that the resulting control system will reliably and safely achieve high performance operation. A block diagram of this research is shown in Fig.1. Basically in fuzzy control system, there are four major stages to accomplish the control process: [1],[4]
x Fuzzy input and output variables & their fuzzy value
x Fuzzy rule base
x Fuzzy inference engine
x Fuzzification and defuzzification modules
Input : Value of student exam
Fuzzy Logic method
Fuzzification
Output :
difficulty of exams and student Graduation
Rules Base
Implications Functions and Inferences Rule
Defuzzification
Fig. 1 General Overview System
2.1 Difficulty level exam
About the level of difficulty is an opportunity to answer correctly a question at a certain skill level, usually expressed in the form of an index. Difficulty level of the index is generally expressed as a proportion of the size range from 0.00 to 1.00. The greater the difficulty level of the index obtained from the calculation, then the easier about it. The formula to calculate the level of difficulty (TK) is as follows:
��=�
�
where:
TK = difficulty of item
p = number of examinees who answered the item correctly
n = number of examinees
Difficulty levels result using the above formula describes the level of difficulty about it. The difficulty level classification problem can be illustrated as follows:
Table 1: difficulty exam
great value Criteria
0,00 – 0,45 Difficult
0,46 – 0,75 Medium
0,76 – 1,00 Easy
(1)
IJCSI International Journal of Computer Science Issues, Vol. 10, Issue 2, No 2, March 2013 ISSN (Print): 1694-0814 | ISSN (Online): 1694-0784
www.IJCSI.org 224
Point about the difficulty level has two functions, namely usability for the educators and usability testing/teaching. Usefulness for educators include: the re-introduction of the concept of the learning, provide feedback to students about their learning, gain information about the curriculum emphasis, suspect items about the bias. While usability for process of testing and teaching, among others: introduction of the concepts needed to re taught, the signs the strengths and weaknesses of the school curriculum, and weave the test have data on accuracy [5].
2.2 Fuzzy Logic Method
This model comprises of four components fuzzy inference engine, fuzzy rules, fuzzifier, and a defuzzifier. The four steps processes are: [6]
Step 1 Fuzzification
Of the input parameters total dissipated energy and node centrality. Now to resolve the level to which the inputs are belonging to the appropriate fuzzy sets or rule the inputs are analyzed. This study used two phases are carried out to evaluate the exam average grade and evaluate students using the Fuzzy Logic.
a. Evaluating an online exam
We consider two fuzzy input variables as exam average grades (z1) and difficulty level of exam (y1) and the output will be the exam level (z1). Membership function of z1, y1 and z2 shold be as
follows (0 ≤ µ ≤ 1). [7]
1. Exam average grades (z1)
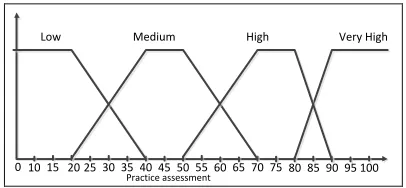
Written test assessment variable is divided into three parts: low, medium, high and very high.
Practice assessment
15 25 35 45
10 20 30 40 50 55 60 65 70 75
0
Low Medium High
80 85 90 95 100 Very High
Fig. 2 Fuzzy membership functions for exam average grade (z1)
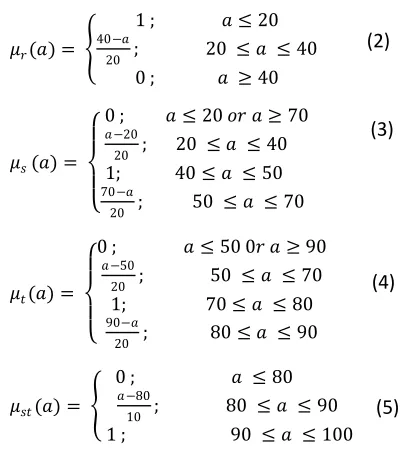
Based on the picture looks fuzzy set membership degree one owned low value range of 0 to 40. Fuzzy Fuzzy region with the set being located in the range of 20 to 70. Fuzzy set Fuzzy regions with high lies in the range of 50 to 90. Fuzzy set Fuzzy regions with extremely high located in the range of 80 to 100. The formula of variable membership function on the exam average grade (z1) assessment as follows :
��(�) =
1 ; � 20 40−�
20 ; 20 � 40 0 ; � 40
��(�) =
0 ; � 20 ��� 70
�−20
20 ; 20 � 40 1; 40 � 50 70−�
20 ; 50 � 70
��(�) =
0 ; � 50 0�� 90
�−50
20 ; 50 � 70 1; 70 � 80 90−�
20 ; 80 � 90
���(�) =
0 ; � 80
�−80
10 ; 80 � 90 1 ; 90 � 100
2. Difficulty level of exam (y1)
Written test assessment variable is divided into three parts: low, medium, high and very high.
Practice assessment
15 25 35 45
10 20 30 40 50 55 60 65 70 75
0
Low Medium High
80 85 90 95 100 Very High
Fig. 3 Fuzzy membership functions for difficulty level of exam (y1)
The formula of variable membership function on the level of exam (y1) assessment as follows :
��(�) =
1 ; � 20 40−�
20 ; 20 � 40 0 ; � 40
��(�) =
0 ; � 20 ��� 70
�−20
20 ; 20 � 40 1; 40 � 50 70−�
20 ; 50 � 70
��(�) =
0 ; � 50 0�� 90
�−50
20 ; 50 � 70 1; 70 � 80 90−�
20 ; 80 � 90
���(�) =
0 ; � 80
�−80
10 ; 80 � 90 1 ; 90 � 100
(3) (4) (5) (2) (7) (8) (9) (6)
IJCSI International Journal of Computer Science Issues, Vol. 10, Issue 2, No 2, March 2013 ISSN (Print): 1694-0814 | ISSN (Online): 1694-0784
www.IJCSI.org 225
b. Evaluating students
We consider two fuzzy input variables as exam grade (x1) and difficulty level of exam (y1) and the output will be the student level (x2). Membership
function of x1, y1 and x2 should be as follows (0 ≤ μ≤
1).
1. Student grades (x1)
Written test assessment variable is divided into three parts: low, medium, high and very high.
Practice assessment
15 25 35 45
10 20 30 40 50 55 60 65 70 75
0
Low Medium High
80 85 90 95 100 Very High
Fig. 4 Fuzzy membership functions for student grade (x1)
The formula of variable membership function on the level of exam (y1) assessment as follows :
��(�) =
1 ; � 20 40−�
20 ; 20 � 40 0 ; � 40
��(�) =
0 ; � 20 ��� 70
�−20
20 ; 20 � 40 1; 40 � 50 70−�
20 ; 50 � 70
��(�) =
0 ; � 50 0�� 90
�−50
20 ; 50 � 70 1; 70 � 80 90−�
20 ; 80 � 90
���(�) =
0 ; � 80
�−80
10 ; 80 � 90 1 ; 90 � 100
2. Difficulty level of exam (y1)
Written test assessment variable is divided into three parts: low, medium, high and very high.
Practice assessment
15 25 35 45
10 20 30 40 50 55 60 65 70 75
0
Low Medium High
80 85 90 95 100 Very High
Fig. 5 Fuzzy membership functions for difficulty level of exam (y1)
The formula of variable membership function on the level of exam (y1) assessment as follows :
��(�) =
1 ; � 20 40−�
20 ; 20 � 40 0 ; � 40
��(�) =
0 ; � 20 ��� 70
�−20
20 ; 20 � 40 1; 40 � 50 70−�
20 ; 50 � 70
��(�) =
0 ; � 50 0�� 90
�−50
20 ; 50 � 70 1; 70 � 80 90−�
20 ; 80 � 90
���(�) =
0 ; � 80
�−80
10 ; 80 � 90 1 ; 90 � 100
Step 2 Rule evaluation
Rules are qualitative statements apply if later into the form, so clearly understood. Rules of the difficulty level of the exam consists 16 rules. Fuzzy rule base for evaluating level of difficulty of the exam is designed as follows :
R1: If (z1) Low and (y1) Low Then (z2) Difficult
R2: If (z1) Low and (y1) Moderate Then (z2)
Difficult
R3: If (z1) Low and (y1) High Then (z2) Moderate
R4: If (z1) Low and (y1) Very High Then (z2)
Moderate
R5: If (z1) Moderate and (y1) Low Then (z2)
Difficult
R6: If (z1) Moderate and (y1) Moderate Then (z2)
Moderate
R7: If (z1) Moderate and (y1) High Then (z2) Easy
R8: If (z1) Moderate and (y1) VeryHigh Then (z2)
Easy
R9: If (z1) High and (y1) Low Then (z2) Moderate
R10: If (z1) High and (y1) Moderate Then (z2)
Moderate (11) (12) (13) (10) (15) (16) (17) (14)
IJCSI International Journal of Computer Science Issues, Vol. 10, Issue 2, No 2, March 2013 ISSN (Print): 1694-0814 | ISSN (Online): 1694-0784
www.IJCSI.org 226
R11: If (z1) High and (y1) High Then (z2) Easy
R12: If (z1) High and (y1) VeryHigh Then (z2) Very Easy
R13: If (z1) Very High and (y1) Low Then (z2)
Moderate
R14: If (z1) VeryHigh and (y1) Moderate Then (z2)
Easy
R15: If (z1) VeryHigh and (y1) High Then (z2) Very Easy
R16: If (z1) VeryHigh and (y1) VeryHigh Then (z2)
Very Easy
Fuzzy rule base for evaluating student is designed as follows:
R1: If x1 is Low And y1 is low Then x2 is pass R2: If x1 is low And y1 is medium Then x2 is pass R3: If x1 is low And y1 is high Then x2 is fail R4: If x1 is low And y1 is very high Then x2 is fail R5: If x1 is medium And y1 is low Then x2 is good R6: If x1 is medium And y1 is medium Then x2 is good
R7: If x1 is medium And y1 is high Then x2 is pass R8: If x1 is medium And y1 is very high Then x2 is fail
R9: If x1 is high And y1 is low Then x2 is exellent R10: If x1 is high And y1 is medium Then x2 is good R11 If x1 is high And y1 is high Then x2 is pass R12: If x1 is high And y1 is very high Then x2 is pass R13: If x1 is very high And y1 is low Then x2 is exellent
R14: If x1 is very high And y1 is medium Then x2 is exellent
R15: If x1 is very high And y1 is high Then x2 is good
R16: If x1 is very high And y1 is very high Then x2 is pass
Step 3 Implications Functions and Inferences Rule
Implications Functions
Minimum method used to combine any degree of membership of each if then rules are made and
expressed in a degree of truth (α). Examples of the use
of minimum to rule 6, rule 7, rule 10, rule 11 can be written as follows:
R6: If (z1) Moderate and (y1) Moderate Then (z2)
Moderate
� − ��������1=��1 �∩ ��1�
= min(��1�[62],��1�[62])
= min 0.4 ; 0.4
= 0.4
R7: If (z1) Moderate and (y1) High Then (z2) Easy � − ��������2=��1 �∩ ��1�
= min(��1�[62],��1�[62])
= min 0.4 ; 0.6
= 0.4
R10: If (z1) High and (y1) Moderate Then (z2)
Moderate
� − ��������2=��1 �∩ ��1�
= min(��1�[62],��1�[62])
= min 0.6 ; 0.4
= 0.4
R11: If (z1) High and (y1) High Then (z2) Easy � − ��������2=��1 �∩ ��1�
= min(��1�[62],��1�[62])
= min 0.6 ; 0.6
= 0.6
The Inference Rules
The method of determining the maximum graduation of FIS is used to evaluate the results of the rules that have been made. Solution output fuzzy set is obtained by taking the maximum value of the rule is appropriate, then use it to modify the area and applying it to the output fuzzy.
Step 4 Deffuzification
Defuzzification is a process of converting output fuzzy variable into a unique number. Defuzzification process has the capability to reduce a fuzzy set into a crisp single-valued quality or into a crisp set; to convert a fuzzy matrix into a crisp matrix; or to convert a fuzzy number into a crisp number. [8]
In the process of using the Weighted Average, the calculations can be seen below:
��=∑ �(�) ∗(� )
∑(�(�))
� : Output score
�� : Weighted Average
�(�) : Membership function of fuzzy output area
The example of deffuzification WA
= 0.25∗75 + 0.25∗50 + 0.25∗50 + 0.75∗50 0.25 + 0.25 + 0.25 + 0.75 = 54.1666 = 54.17
3.
Axperiments and Results
We can classify the test in accordance with our expert system for the 4 levels:. Easy, Medium, Hard and very
(18)
IJCSI International Journal of Computer Science Issues, Vol. 10, Issue 2, No 2, March 2013 ISSN (Print): 1694-0814 | ISSN (Online): 1694-0784
www.IJCSI.org 227
hard [7] Then we use math test scores as an example, so that the results are as follows in figure 6 [6]:
Fig. 6 Results for difficulty level of each item of the test
After getting the value of the degree of difficulty of the test the next step dalah find difficulty value test. The authors grouped into 4 levels: very easy, easy, moderate and hard. The difficulty level exam using two criteria: the value of difficulty of questions and average student grade.
Fig. 7 Results for difficulty level exam
Step 1: an average grade and value kesulutan exams. Step 2: an overall degree of membership values of the average student and the difficulty level of the exam grade.
Step 3: a rule or fuzzy criteria.
Step 4: is the value defuzzyfikasi and fuzzy decision. From Figure 7 we can see that the value of the defuzzyfikasi is 63.88 so the level of difficulty of the test was EASY.
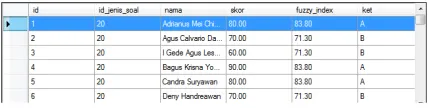
Fig. 8 Results for level student
The first column contains the name of the student, the student points and the value of the degree of difficulty of the selected subjects. In column 2 value will be processed to produce value students' graduation and degree completion. We classify student in to 4 levels: fail, pass, good
and excellent. [11] So according to "Bahasa Indonesia" Course the students level are as shown in figure 9.
Fig. 9 Results for student evaluation
1. CONCLUSION
Fuzzy logic is very good when used in evaluating student test making it easier for teachers to assess students according to the level of difficulty of the test. It is also regarded as a good reference for teachers to evaluate the level of the exam is the benefit of this evaluation.
2. REFERENCES
[1] E. Abd-Alazeem, Mohammed, and I. Barakat, Sherief.” Fuzzy Expert System For Evaluation Of Students And Online Exams” International Journal of Computer Science & Information Security.Vol.8.No.8.November 2010.
[2] Zadeh, L. A. “Fuzzy sets. Information and Control”, Vol. 8, pp. 338-353. 1965.
[3] Henry Nasution, "Design methodology of fuzzy logic control", Journal Teknos-2k, Universitas Bung Hatta, Vol.2, No.2, December (2002).
[4] Takagi,T. and Sugeon, "Fuzzy identification of System and Its Applications to Modeling and Control", vol. 15, no. 1, 116-132, 1985.
[5] Ana Anitasari , Entin Martiana Kusumaningtyas, S.Kom, M.Kom, Arna Fariza2 S.Kom, M.Kom,”Analisa Kualitas Materi Soal Ujian Akhir Semester di SMP Terpadu Ponorogo”, Journal Pens, Institut Teknologi Sepuluh Nopember. 2012
IJCSI International Journal of Computer Science Issues, Vol. 10, Issue 2, No 2, March 2013 ISSN (Print): 1694-0814 | ISSN (Online): 1694-0784
www.IJCSI.org 228
[6] Ashutosh Kumar Singh, Sandeep Goutele, S.Verma and N. Purohit.” An Energy Efficient Approach for Clustering in WSN using Fuzzy Logic” International Journal of Computer Applications.Vol.44.No.18.April 2012.
[7] Arriaga, F. de, Alami, M. El., & Arriaga, A,"Evaluation of Fuzzy Intelligent Learning Systems".Spain, November 2005.
[8] H.Bevrani, "Defuzzification", University of Kurdistan Department of Electrical & Computer Eng, Spring Semester, 2009.
[9] Ishiburchi, H., Nozaki, K., and Tanaka, H. “Distributed Representation of Fuzzy Rules and Its Application to Pattern Classification. Fuzzy Sets and Systems”, Vol. 52,pp. 21-32. 1992.
[10] GAO Xinbo (1) XIE Weixin(2)," Advances in theory and applications of fuzzy clustering", Institute of Electronic Engineering, China, 2000.
[11] Nykänen, "Inducing Fuzzy Models for or Student Classification". Educational Technology &Society, vol 2, pp 223-234, 2006.
Ni Made Rusmiari studied Information Technology in
Department of Information Technology Udayana University since August 2008, and now working her research for S.Ti. degree in Information Technology.
Dr. I Ketut Gede Darma Putra, S.Kom., MT received his
S.Kom degree in Informatics Engineering from Institut Teknologi Sepuluh Nopember University, his MT. degree in Electrical Engineering from Gajah Mada University and his Dr. degree in Electrical Engineering from Gajah Mada University. He is lecturer at Electrical Engineering Department (major in Computer System and Informatics) of Udayana University, lecturer at Information Technology Department of Udayana University.
I Gusti Made Arya Sasmita, ST., MT received his ST degree
in Electrical Engineering from Udayana University in 1997 and his MT. degree in Electrical Engineering from Gajah Mada University in 2003. He is lecturer at Electrical Engineering Department (major in Computer System and Informatics) of Udayana University, lecturer at Information Technology Department of Udayana University.
IJCSI International Journal of Computer Science Issues, Vol. 10, Issue 2, No 2, March 2013 ISSN (Print): 1694-0814 | ISSN (Online): 1694-0784
www.IJCSI.org 229