Next Page
Professional MOM 2005, SMS 2003, and Microsoft Update byRandy Hollowayet al.
Wrox Press 2006 (432 pages) ISBN:0764589636
P ro viding a single so urce fo r IT a dm inistra to rs to unde rsta nd ho w syste m s a nd o pe ra tio ns m a na ge m e nt te chno lo gie s ca n be use d in the ir e nviro nm e nts, this co m pa ra tive to o l he lps re a de rs unde rsta nd which to o l is right fo r which jo b.
Table of Contents
Professional MOM 2005, SMS 2003, and Microsoft Update Introduction
C hapter 1 - The Basics of Operations Management C hapter 2 - MOM, SMS, and WSUS—How They Fit Together C hapter 3 - Installing Microsoft Operations Manager 2005 C hapter 4 - Installation of SMS
C hapter 5 - Installing and C onfiguring Microsoft Update and Windows Server Update Services C hapter 6 - MOM C onfiguration and Administration
C hapter 7 - MOM and SMS Agents
C hapter 8 - Management Packs and C omponents
C hapter 9 - Management Pack Drilldown for Windows Server C hapter 10- More on Management Packs
C hapter 11- Third-Party Management Packs and Product C onnectors C hapter 12- Using SMS and MOM to Manage Security and Patching C hapter 13- Monitoring
C hapter 14- Securing Your MOM, SMS, WSUS, and WU Installation C hapter 15- Reporting
C hapter 16- System C enter and the Dynamic Systems Initiative Appendix A- MOM Management Packs and Utilities
Index
Next Page
Ba ck Cov e r
Professional MOM 2005, SMS 2003 and Microsoft Update provides a single source for IT administrators to understand how these systems and operations management technologies can be used in their environments. It also serves as a comparative tool that helps readers understand which tool is right for which job.
It is designed and written for anyone who is involved with implementing, supporting, or managing a set of tools for systems and operations management, including IT operators, IT administrators, IT infrastructure managers and system architects. The readers that have some background in systems and operations management will probably get the most of this book, however no specific level of skill or knowledge is assumed. The writing is aimed at readers who have a basic understanding of IT infrastructure on the Windows platform and have familiarity with Windows XP (and earlier) client deployments and Windows Server technologies.
Some of the topics covered include:
basics of operations management
how the MOM 2005, SMS 2003 and other update technologies fit together installing and deploying MOM
installing and deploying SMS installing and deploying MU and WSUS
configuring and administering the MOM environment with MOM and alert tuning MOM and SMS agents
Deploying and using MOM management packs Third party management packs
Security and patching with MOM and SMS
Monitoring and security MOM and SMS deployments MOM and SMS reporting
Microsoft System C enter Solutions
Next Page
Professional MOM 2005, SMS 2003, and Microsoft Update
Randy HollowayProfessional MOM 2005, SMS 2003, and WSUS Published by
Manufactured in the United States of America 10 9 8 7 6 5 4 3 2 1
1B/QS/QV/QW/IN
Library of Congress Cataloging-in-Publication Data
Professional MOM 2005, SMS 2003, and WSUS /Randy Holloway … [et al.]. p. cm.
ISBN-13: 978-0-7645-8963-8 (paper/website) ISBN-10: 0-7645-8963-6 (paper/website)
1. Microsoft Windows (Computer file) 2. Operating systems (Computers) 3. Computer systems—Management. I. Holloway, Randy, 1974– QA76.76.O63.P6135 2006
005.4 46—dc22 2006011600
No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permission should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4355, or online at http://www.wiley.com/go/permissions.
LIMIT OF LIABILITY/DISCLAIMER OF WARRANTY: THE PUBLISHER AND THE AUTHOR MAKE NO REPRESENTATIONS OR WARRANTIES WITH RESPECT TO THE ACCURACY OR COMPLETENESS OF THE CONTENTS OF THIS WORK AND SPECIFICALLY DISCLAIM ALL WARRANTIES, INCLUDING WITHOUT LIMITATION WARRANTIES OF FITNESS FOR A PARTICULAR PURPOSE. NO WARRANTY MAY BE CREATED OR EXTENDED BY SALES OR PROMOTIONAL MATERIALS. THE ADVICE AND STRATEGIES CONTAINED HEREIN MAY NOT BE SUITABLE FOR EVERY SITUATION. THIS WORK IS SOLD WITH THE UNDERSTANDING THAT THE PUBLISHER IS NOT ENGAGED IN RENDERING LEGAL, ACCOUNTING, OR OTHER PROFESSIONAL SERVICES. IF PROFESSIONAL ASSISTANCE IS REQUIRED, THE SERVICES OF A COMPETENT PROFESSIONAL PERSON SHOULD BE SOUGHT. NEITHER THE PUBLISHER NOR THE AUTHOR SHALL BE LIABLE FOR DAMAGES ARISING HERE-FROM. THE FACT THAT AN ORGANIZATION OR WEBSITE IS REFERRED TO IN THIS WORK AS A CITATION AND/OR A POTENTIAL SOURCE OF FURTHER INFORMATION DOES NOT MEAN THAT THE AUTHOR OR THE PUBLISHER ENDORSES THE INFORMATION THE ORGANIZATION OR WEBSITE MAY PROVIDE OR RECOMMENDATIONS IT MAY MAKE. FURTHER, READERS SHOULD BE AWARE THAT INTERNET WEBSITES LISTED IN THIS WORK MAY HAVE CHANGED OR DISAPPEARED BETWEEN WHEN THIS WORK WAS WRITTEN AND WHEN IT IS READ.
For general information on our other products and services please contact our Customer Care Department within the United States at (800) 762-2974, outside the United States at (317) 572-3993 or fax (317) 572-4002.
Trademarks: Wiley, the Wiley logo, Wrox, the Wrox logo, Programmer to Programmer, and related trade dress are trademarks or registered trademarks of John Wiley & Sons, Inc. and/or its affiliates, in the United States and other countries, and may not be used without written permission. All other trademarks are the property of their respective owners. Wiley Publishing, Inc., is not associated with any product or vendor mentioned in this book.
Wiley also publishes its books in a variety of electronic formats. Some content that appears in print may not be available in electronic books. About the Authors
Randy Holloway
Randy Holloway works for Microsoft Corporation as a technology specialist in the US Central Region. Prior to joining Microsoft, Randy worked in various software development and technology architecture roles; he has written a number of articles on software and systems development on the Microsoft platform. His blog is located at http://www.randyh.wordpress.com.
Note Special thanks to my wife, Donna, for supporting me, and to Emily and Gavin for letting me work all of those weekends and evenings. I also thank Jim Minatel and the team at Wrox for believing in this project.
Telmo Sampaio
Telmo Sampaio is an IT consultant and trainer with 14 years of experience dealing with Microsoft, IBM, and Symantec technologies. He has worked for companies such as Microsoft and IBM. Telmo has been involved in medium to large network infrastructure projects, security audits, database implementations, and application development. Telmo works as a Senior Technical Training Consultant for Signal Learning in Indiana. In his spare time, he plays Xbox and reads with his kids.
Note This book is dedicated to both my mothers, Yvette and Graça; my father, Gaspar; my brothers, Daniel and Digo; my wife, Carla, who was very understanding when I had to spend hours in front of the computer working late nights; and my children, Marco, Rafael, and Natalia.
Marcus Oh
Marcus Oh, a senior administrator and architect, has been leading initiatives in systems management technologies for a private telecommunications company since 1999. He is a columnist for http://www.myITforum.com and has had articles published in TechTarget newsletters as well as the book Windows Server Hacks. Marcus has been recognized by Microsoft with the Most Valuable Professional award in Windows Server Management since 2004. To get a glimpse of Marcus's latest reflections, visit his blog at http://www.marcusoh.blogspot.com.
Note I thank all of my family and friends for their support while I wrote my part of this book. Further, I thank all of the intelligent and respected minds I've met along the way that have helped contribute in some form or another to the completion of this book, various projects, and my sanity.
Russ Kaufmann
Russ Kaufmann, MCSE+I, MCT, and MVP, is a consultant, speaker, trainer, technical editor, and author. He has been working in IT for more than 15 years and has worked with both small clients and large clients spanning multiple countries. He specializes in Microsoft server products with special emphasis placed on Exchange, IIS, SharePoint Portal Server, and, of course, MOM. He currently works for Infocrossing, an infrastructure outsourcing company, in their Broomfield, Colorado, office.
Note This book was a unique project that taught me a great deal about life and prioritization.
I originally saw this project and rejected it. It was too open ended and it just didn't "ring" for me. Later, this project came around again, and this time I said I would do it. My thanks go to Jim Minatel for keeping me in the loop and giving me another chance to jump on board with this project.
covering systems management. The plan was to cover the basics of the products normally used in systems management, how they worked together, and how each covered different organizational needs. Thanks to Randy for getting the idea and making sure I understood it as I built the outline.
As we started working on the project and the timeline, it became clear that we needed additional people. My thanks go to Telmo Sampaio. Telmo stepped up and agreed to take on some work and add his expertise. Without him, this project would have died.
The next challenges came up with some major health problems on my part and Randy's making the correct decision to place his family first. He had an addition to the family right as we were getting started, and his responsibilities really ate up his time. So, the next step was to add another person to help out. My thanks go to Marcus Oh for jumping into the middle of this and using his sheer force of will to keep things moving forward. At that time, I really couldn't provide any help or answer his questions, but he figured things out and kept on going.
The final challenge was one that I have seen in all projects: the dreaded deadline and exhaustion. This kind of project requires huge amounts of work, and it got to everyone. My thanks go to Derek Comingore for taking on a good bit of the load. Derek did a great job as the tech editor for many chapters and the author of others.
The usual thanks go to the editors and StudioB's Laura Lewin for taking care of the business of it all and for having the patience in trying times to make this project happen. This project was completed by the sheer will of those involved. I still am amazed that it is done.
Derek Comingore
Derek Comingore is the software development manager for http://www.Hosting.com. He holds the MCAD/MCDBA Microsoft certifications, the Carnegie Mellon Personal Software Process (PSP) credential, and an AAS/BS in Computer Information Systems. In addition to his role for http://www.Hosting.com, Derek enjoys writing articles for http://www.Hosting.com's newsletter and has written his first article for MSDN (soon to be published) on leveraging SQL Server 2005 Service Broker to obtain real-time ETL. He is also starting up a new SQL Server community, http://www.sqlserver360.org, which promises to deliver a rich and rewarding experience for the SQL Server professional.
Note First and foremost I wish to thank my fiancée, Misty Neely, for her everlasting patience with me as I sat in front of the computer until 3 a.m. on several occasions. I love you very much. My son, Derek Steven Comingore—there is no better feeling in the world than when you come tackle Daddy when he gets home from work; you are the best gift God could ever have given me. My family also deserves much praise as they gave me a good home to grow up in with strong morals and love; their guidance continues to help me achieve higher levels of success in my life.
Jim Minatel, thank you, not only for this opportunity but also for mentoring me in the technical writing field. Jim slowly exposed me to the technical writing industry by asking me to be a technical editor for several other Wrox titles, and now a contributing author on this book. Ed Connor deserves thanks as he was under a lot of pressure when things got tight, but he "quarterbacked" the project quite well. http://www.Hosting.com, my employer, has been supportive of my technical writing, and I appreciate it. Finally, I thank Darren King, http://www.Hosting.com CEO, who continues to challenge and mentor me.
Credits
Vice President and Executiv e Group Publisher Richard Swadley
Next Page
Introduction
Systems and operations management can be complex and expensive. A comprehensive approach to this problem requires the use of operations management tools, software deployment tools, configuration management, and other release management tools and techniques. The knowledge of the organization is critical in helping to make sure that everything works well. In addition, doing the job right involves custom rules or scripts and reports to help ensure that everything is running as expected. For many IT professionals, this kind of operations management is a mix of a number of different tools along with custom scripting and manual effort to monitor logs and other reports. While this approach will get the job done, it can often be more expensive and time consuming for administrators. In addition, the use of too many special-purpose monitoring and management tools in the environment, along with custom scripts and reports, introduces more opportunities for mistakes and can lead to unsatisfied users or customers.
Microsoft is taking a comprehensive approach to systems and operations management and is building tools targeted at the small business all the way up to the largest enterprises. While there is more work to do in improving these products, Microsoft's focus to build a well-integrated set of monitoring and systems management solutions is significant and should be a point of consideration for any IT administrator who is evaluating or implementing these tools in their environment. This book was written to show how the current Microsoft tools for systems and operations management can work together to provide a comprehensive approach to automating IT operations. In addition, this book takes a look at where these tools are going and what IT administrators can expect from Microsoft in the future to help make operations and systems management tasks easier. It is important for IT administrators to consider not only the present operational and systems management requirements but their future needs as well when evaluating and implementing the technologies, and this book attempts to address both of these areas.
Whom This Book Is For
When the idea for Professional MOM 2005, SMS 2003, and WSUS was first discussed, the goal was to provide a single source for IT administrators to understand how these systems and operations management technology can be used in their environments. Since that time, the book has also evolved into a comparative tool that can help a reader to understand which tool is right for which job. The audience for this book includes anyone who is involved with implementing, supporting, or managing a set of tools for systems and operations management, including IT operators, IT administrators, IT infrastructure managers, and system architects.
Readers with some background in systems and operations management will probably get the most out of this book; however, no specific level of skill or knowledge is assumed. The writing is aimed at readers who have a basic understanding of IT infrastructure on the Windows platform and have familiarity with Windows XP (and earlier) client deployments and Windows Server technologies.
For readers who understand the principles behind systems and operations management and who are interested in the installation procedures and configuration for MOM 2005, SMS 2003, or the Microsoft Update (MU) and Windows Server Update Services tools (WSUS), you may want to jump right into Chapters 3, 4, and 5. For those that are interested in evaluating these tools and using this book as an aid, start with Chapter 2, which covers the basics of how these products work and how they can be used together. Chapter 16 looks beyond the core products that we've discussed throughout the book and incorporates other systems management products from Microsoft. This is a good chapter for those interested in the product roadmap beyond MOM 2005 and SMS 2003.
Next Page
What This Book Covers
This book covers the current shipping systems and operations management products from Microsoft. As of this writing, these products include MOM 2005, SMS 2003, MU, and WSUS. While there are older versions of MOM and SMS, we have not covered those technologies in this book in any detail. In addition, this book does not offer any detailed comparison of the current versions of these products to the previous versions. New features in the current products are not explicitly noted.
Next Page
How This Book Is Structured
One of the challenges in writing a book that covers a broad range of products and tools is structure. To best address this issue, the book is organized to cover the material in logical sections. This book covers the basics of systems management and the products, followed by installation and configuration procedures. In later chapters, topics covered include patching, monitoring, tuning, and reporting of the management tools. Finally, the book describes the roadmap for future management products from Microsoft.
More specifically, Chapters 1 and 2 cover the basics of operations management and how the MOM 2005, SMS 2003, and other update technologies fit together. These chapters should set the stage for the material to be discussed and provide some insight on what these products can do for IT. Chapters 3 through 5 are focused on the installation and deployment of MOM, SMS, MU, and WSUS. These chapters include a review of installation procedures and considerations, along with some discussion of configuration. Chapter 6 is a deeper dive into the configuration and administration of the MOM environment with MOM and alert tuning, and should help the reader to understand how to get the most out of the operations monitoring tools. Chapter 7 goes into the agent technologies that make MOM and SMS work in your environment.
In Chapters 8 through 11, the book moves into a deeper discussion of MOM management packs, including the deployment of management packs and the use of third-party management packs and product connectors. Appendix A also provides more detail on the management packs available from Microsoft and other vendors. Chapter 12 covers the security and patching features that can be supported by MOM and SMS. Chapters 13 and 14 cover monitoring and the security aspects of deploying MOM, SMS, and the update technologies, helping to ensure that IT administrators lock down these powerful tools. Chapter 15 covers the reporting capabilities of MOM and SMS detail with information on how administrators and operators can retrieve critical information from these tools. Chapter 16 covers the Microsoft System Center solutions and considers the future of Microsoft's management tools.
Next Page
What You Need to Use This Book
The readers of this book will benefit from having access to a Windows Server domain and software including MOM 2005 and SMS 2003. Some of this software is available to be downloaded for evaluation purposes. For those without access to a lab or test network environment, products such as Virtual Server or Virtual PC can help to build an environment for testing. For IT professionals that don't have access to these tools, the Virtual Labs available at Microsoft's Tech Net site (http://www.microsoft.com/technet/traincert/virtuallab/default.mspx) can be used to review much of the functionality described in this book.
Next Page
Errata
We make every effort to ensure that there are no errors in the text or in the code. However, no one is perfect, and mistakes do occur. If you find an error in one of our books, like a spelling mistake or faulty piece of code, we would be very grateful for your feedback. By sending in errata you may save another reader hours of frustration and at the same time you will be helping us provide even higher quality information.
To find the errata page for this book, go to http://www.wrox.com and locate the title using the Search box or one of the title lists. Then, on the book details page, click the Book Errata link. On this page you can view all errata that has been submitted for this book and posted by Wrox editors. A complete book list including links to each book's errata is also available at
http://www.wrox.com/misc-pages/booklist.shtml.
If you don't spot "your" error on the Book Errata page, go to http://www.wrox.com/contact/techsupport.shtml and complete the form there to send us the error you have found. We'll check the information and, if appropriate, post a message to the book's errata page and fix the problem in subsequent editions of the book.
Next Page
http://www.p2p.wrox.com
For author and peer discussion, join the P2P forums at http://www.p2p.wrox.com. The forums are a Web-based system for you to post messages relating to Wrox books and related technologies and interact with other readers and technology users. The forums offer a subscription feature to e-mail you topics of interest of your choosing when new posts are made to the forums. Wrox authors, editors, other industry experts, and your fellow readers are present on these forums.
At http://www.p2p.wrox.com you will find a number of different forums that will help you not only as you read this book, but also as you develop your own applications. To join the forums, just follow these steps:
1. Go to http://www.p2p.wrox.com and click the Register link. 2. Read the terms of use and click Agree.
3. Complete the required information to join as well as any optional information you wish to provide and click Submit. 4. You will receive an e-mail with information describing how to verify your account and complete the joining process. Note You can read messages in the forums without joining P2P but in order to post your own messages, you must join.
Once you join, you can post new messages and respond to messages other users post. You can read messages at any time on the Web. If you would like to have new messages from a particular forum e-mailed to you, click the Subscribe to this Forum icon by the forum name in the forum listing.
For more information about how to use the Wrox P2P, be sure to read the P2P FAQs for answers to questions about how the forum software works as well as many common questions specific to P2P and Wrox books. To read the FAQs, click the FAQ link on any P2P page.
Next Page
Chapter 1: The Basics of Operations Management
Overview
One of the key criteria for selecting and deploying enterprise systems is the ability to effectively manage their operations. By ensuring that critical business systems are healthy, responsive, and running as expected, information technology managers and executives are able to lower the total cost of ownership for their systems and place more emphasis on the development and deployment of new capabilities. In most organizations, this is the major focal point to help drive efficiency. In this chapter, we cover the following topics:
Systems management on the Microsoft platform
Model-based operations management
Dynamic Systems Initiative
With the emphasis on Microsoft's management technologies over the past few years, new releases of SMS and MOM, and the evolution of the Microsoft Update platform, there is a greater need for IT to understand how these products can work together to provide a comprehensive systems management solution that enables software deployment, systems monitoring for alerts and exceptions, and access to the data that can help IT to prevent problems in the future. Those who use the systems management tools from Microsoft benefit from having Microsoft's knowledge of its own tools baked into the products, which makes it easier to manage their Windows desktop and server environments and provides the capability to work in a heterogeneous setting.
The goal for this chapter is to provide a basic overview of operations management and describe the problem domain and then focus on the components of the Microsoft platform now and in the future that will enable system administrators and IT to effectively manage their technology operations. By examining the current management tools and understanding Microsoft's Dynamic Systems Initiative, you can better formulate your strategies for deploying management solutions on the Microsoft platform.
Next Page
Systems Management on the Microsoft Platform
IT organizations deploy systems management and monitoring technologies in an effort to reduce costs associated with the complexity and effort of deploying and managing large numbers of workstations, servers, and server-based applications in their enterprise environment. Achieving this goal depends on the technology being used to provide scalability to accommodate large environments and to provide an efficient architecture. However, when comparing monitoring and management technologies, the most critical factor to consider is the availability of the operational assistance they offer to the operators and administrators that rely upon these tools. These administrators want to ensure that their systems are highly available and functional for their customers.
Monitoring technologies are only as valuable as the quality of the best-practices they provide. Traditionally monitoring, management, and deployment technologies have been toolsets that depend on customization by IT or consultants to determine appropriate components that should be deployed and how to best configure them to monitor the availability and performance of the customer's specific application or service. Because of this, few organizations have realized the potential value of these technologies. In addition, monitoring tools that are not granular enough in detail can fall short in helping administrators to solve problems once they are identified.
The core management solutions on the Microsoft platform include products such as Systems Management Server (SMS), Microsoft Operations Manager (MOM), and the Microsoft Update solution. Through the use of SMS for software deployment, MOM for management alerts and notifications, and Microsoft Update to provide easy access to updated patches for products such as Microsoft Windows, Microsoft Office, and many others, an enterprise systems administrator has a baseline to enable secure and well-managed systems. MOM provides the foundation for operations management while SMS enables more sophisticated configuration and release management scenarios. Together, these tools can effectively support the full lifecycle for systems management.
For many years, IT administrators have been successfully using Microsoft SMS to manage Windows-based desktops and servers within their organizations. As the number of Windows PCs deployed within these organizations has grown dramatically, SMS has helped IT administrators contain the cost of managing such heavily distributed systems, keeping the overall cost of ownership low while allowing the number of deployed PCs and applications to grow.
However, the environment in which Windows-based PCs are deployed is constantly changing as new technologies are adopted and as PCs are used in increasingly complex configurations. The most recent release of SMS, Systems Management Server 2003, is designed to track and support these changing trends in PC usage and provide support for emerging usage scenarios and technologies. SMS 2003 provides solutions for a number of key issues faced by IT administrators managing Windows-based PC environments today. SMS 2003 addresses the following key problem areas:
Managing computers and users that roam around the network, often connecting over poor bandwidth links or from different geographic locations on a regular basis Tracking the deployment and usage of software assets in the organization, and using this to plan licensing and software acquisition across the company
Monitoring the patch state of all deployed Windows PCs and applications in the enterprise, and removing vulnerabilities proactively in a closed loop process with real-time patch deployment status
Offering managers and users access to the management data aggregated by SMS, including live configuration and operations reports
Managing Windows PCs securely, but with a minimum of administrative overhead, while fending off the ever-increasing number of external security threats
The core features of SMS, including software deployment, inventory tracking, and remote troubleshooting are supported in SMS 2003. The SMS administration console is shown in Figure 1-1.
Figure 1-1
In addition, support has been added for the increasing number of mobile users in organizations today. This support simplifies management of Windows-based PCs and users who commonly roam to different physical locations, reducing the IT cost of managing such users and machines and providing seamless one-to-many solutions for desktop, laptop, and server users. Because of increased need to maintain the security of all deployed software in an enterprise, SMS 2003 also adds support for Security Patch Management of deployed Windows systems. This allows administrators to easily monitor the patch state of all systems within their enterprise through a set of powerful web reports. These reports are used to identify any vulnerability in the network, at which point the system can then be used to download and deploy the latest patches from Microsoft's web site to those machines that require them. Additional scenarios and enhancements will be supported in SP2 of SMS, which is scheduled for release in 2006.
Because many organizations are deploying Windows Server 2003 Active Directory service within their networks, SMS 2003 is able to take advantage of this technology, further simplifying the process of managing clients and users. Many Active Directory features map directly to SMS targeting concepts, allowing IT administrators to target software and inventory tasks using Active Directory constructs and containers. In summary, SMS provides a strong set of features to enable software deployment and the management of clients and users.
When it comes to systems monitoring and alerting functions, the core component of that solution is Microsoft Operations Manager. MOM 2005 differs from traditional monitoring technology and assists customers in reducing the cost of management through the use of management packs. These management packs for an application combine the insight of the application developers, a knowledge base for organizational learning and common knowledge surrounding the product along with best practices for operations.
The difference between MOM management packs and similar management technology lies both in the identities of the management pack developers and the methodology used for their development. First, MOM 2005 management packs provide built-in, product-specific operational intelligence, encapsulating knowledge from the individual Microsoft product teams developing the applications, Microsoft Consulting Services, and Microsoft's product support organizations. All of this knowledge is made available out of the box for consumption by the product users. Second, the Design for Operations methodology is used to first analyze and then design the management of Windows applications and services.
The Design for Operations methodology of managing applications is a sharp contrast to the typical way application management has been developed in the past. As opposed to a subject matter expert driving the approach to managing a system, Design for Operations requires developers of Microsoft applications and third-party applications or services to adopt an inside-out approach based on their personal knowledge of the application or services. Instead of simply monitoring processes or services to see if they're running and then generating an alert to a console, Design for Operations requires that an application or service be analyzed and broken down into a framework that will describe the application from a management perspective. This methodology uses three models as the basis for implementing management for a service or application: the Health Model, the Task Model, and the State Model. The models are meant to provide a prescriptive mechanism for ensuring that management is built for every service and application and that the management is aligned with the needs of the administrator who will be running the service. This design point is a requirement of the Windows Server Systems Core Engineering Criteria, which are used to determine whether a Microsoft product can be shipped under the banner of Windows Server System.
The Health Model defines what it means for a system to be healthy or unhealthy, and the model defines how a system transitions in and out of those states. Information on a system's health is necessary for the maintenance and diagnosis of the system. The contents of the Health Model become the basis for system events and instrumentation on which monitoring and automated recovery is built. All too often, system information is supplied in a developer-centric way that does not give the administrator operational visibility of the applications. The Health Model seeks to guide both what kinds of information should be provided and how the system or the administrator should respond to the information. If a management technology is monitoring an application or service without a deep understanding of Health Modeling, IT operators will be required to invest time and resources analyzing the relevance of an alert to the operations of their organization.
leveraged to provide IT administrators with preconfigured, remotely launched tasks from a MOM Operator Console that will assist in either error diagnosis or correction. Without the concept of a Task Model, most monitoring applications rely on the IT organization or consultants to write complex scripts and rules to determine how to resolve error situations locally or determine the correct diagnostic procedures or tools needed to remedy a problem remotely.
State Modeling will be increasingly leveraged by future Windows platforms and applications to provide administrators with a comprehensive means of managing both the availability and configuration of systems and applications. State Modeling catalogs the state and settings associated with an application and define the scope and type for each. State may be associated with the computer or the user, it may be temporary or permanent, and it might be user data or operational parameters. Having a strict association of every state entity with a scope and category allows the administrator flexibility in deployment and provides a powerful tool for control. It means an administrator can separately store user data, migrate a user easily from one computer to another, and replicate computer configuration across a data center.
In an early adoption of State Modeling, MOM 2005 management packs provide administrators Health and State information from new views within the MOM Operator Console. In addition to alert views found in other management applications, the State Monitoring view provides MOM operators with a quick overview of server health. Each computer shown in the state monitoring view receives a rating in critical categories. The rated categories include memory and operating system as well as specific application categories, such as Active Directory, SQL Server, and Exchange Server. The operator can expand a particular category to view server status displayed in subcategories, as shown in Figure 1-2.
Figure 1-2
MOM 2005 provides users with a variety of topological views that show the automatic discovery of nodes and relationships. With topological views, IT administrators can view node status, navigate to other views, and launch context-sensitive actions. This can reduce resolution time for complex problems from hours to minutes, significantly reducing cost and improving service levels. For example, when something happens to an application such as Active Directory, it turns red on the diagram. By double-clicking on the red application, a more detailed diagram opens showing one or more trouble spots in red. The operator can continue drilling down in detail until he or she uncovers the cause. The MOM console tasks and prescriptive guidance are then available to help resolve the issue. Diagram views are shown in Figure 1-3.
Figure 1-3
Next Page
Moving Toward the Future: Dynamic Systems Initiative
Knowledge is a key component for systems management. This includes knowledge of the deployed systems, knowledge of the environment in which they operate, knowledge of a designer's intent for those systems, and knowledge of IT policies. Specifically, knowledge may include the following:
Developer constraints on settings of a component, including constraints on related systems that the component is hosted on or communicates with
IT policy that further constrains settings or deployments
Installation directives that describe how a system is to be installed
Health models that describe system states and the events or behavioral symptoms that indicate state transitions
Monitoring rules, ranging from polling frequency to event filtering and forwarding to diagnostic or corrective action in response to problems
Schemas for instrumentation, settings, events, and actions
Service-level agreements that define performance and availability
Transaction flows and costs of processing steps for performance analysis
Reports
As IT organizations have become more geographically dispersed and individual roles more specialized, IT professionals tend to operate in silos focused on their area of specialization. This makes it increasingly difficult to communicate relevant system knowledge across the IT lifecycle. As a result, organizations find it very difficult to collaborate across roles, promote continuous improvement of a system's design and operation, and conduct typical management tasks such as deployment, updating, and patching.
The silos that form across IT organizations interact with an application or system at some point during its lifecycle. However, each silo possesses its own pocket of system-relevant knowledge that does not get communicated effectively to the rest of the organization.
Software models can be used to capture system-relevant knowledge and facilitate the communication and collaboration around this knowledge that is required to improve the efficiency of the entire IT development, deployment, and support lifecycle. A software model provides a level of abstraction for administrators similar to what a blueprint provides to an architect or a prototype provides to a product designer. But for a dynamic and distributed software environment, a static model or blueprint is insufficient. The model must be a living organism and should evolve throughout the life of a system. Having the right tools for systems management can help to keep these models current and enable users to have dynamic views of the system model based on an underlying operational system.
When a system is developed, basic rules and configurations are defined. As the system is deployed, the details of its configuration, environmental constraints, and requirements are added. As operational best practices are developed or enhanced, they can be incorporated into the model as well, providing a feedback loop between the operations staff and the model. In the end, the model becomes a live, dynamic blueprint that captures knowledge about a complete distributed system in terms of its structure, behavior, and characteristics. The following benefits can be gained as a result of these models:
The system model captures the entire system's composition in terms of all interrelated software and hardware components.
The system model captures knowledge as prescriptive configurations and best practices, allowing the effects of changes to the system to be tested before the changes are implemented.
Tools that take advantage of the system model can capture and track the configuration state so that administrators do not need to maintain it in their heads. The software maintains the desired state so that humans do not need to.
Administrators do not need to operate directly on real-world systems but rather can model changes before committing to them. In this way, "what if" scenarios can be tried without impact to a business.
The system model becomes the point of coordination and consistency across administrators who have separate but interdependent responsibilities.
The modeling system becomes the integrated platform for design and development tools that enable the authoring of system models. It also becomes the platform for operational management and policy-driven tools used for capacity planning, deployment, configuration update, inventory control, and so on.
In Microsoft's initial implementation of the Dynamic Systems Initiative, the System Definition Model (SDM) is a foundational component of dynamic systems. SDM is a model that is used to create definitions of distributed systems. In this context, a distributed system is a set of related software and hardware resources working together to accomplish a common function. Multi-tier applications, Web Services, Internet web sites supporting e-commerce, and enterprise data centers are examples of systems. Using SDM, businesses can create a live blueprint of their systems. This blueprint can be created and manipulated with various software tools and is used to define system elements and capture data pertinent to development, deployment, and operations so that the data becomes relevant across the entire IT lifecycle.
Today, an SDM can be defined using tools available with Visual Studio 2005. Going forward, SDM will be the basis for design of system models, used to deploy systems based on the model defined and will be kept up-to-date by an SDM service that dynamically modifies the SDM to reflect the current state of operations. While the SDM will be incorporated into the Microsoft management solutions, third parties will also be able to develop solutions based on the SDM to extend the capabilities of these models and the tools that consume or produce them.
Several key capabilities of IT organizations and IT systems become possible when software models are used to capture all relevant system knowledge. Through the DSI efforts and SDM, Microsoft aims to enable innovation in its products and from its partners in four areas: Design for Operations, System-Level Management, Policy-Driven Operations, and Hardware Abstraction.
Design for Operations
When creating mission-critical software, software architects often find themselves communicating with their counterparts who specify data center and infrastructure architecture. In the process of delivering a solution, an application's logical design is often found to be at odds with the actual capabilities of the deployment environment. Typically, this communication breakdown results in lost productivity as developers and operations managers reconcile an application's capabilities with a data center's realities.
With new model-based development tools, such as Visual Studio Team System, these differences are mitigated by offering a logical infrastructure designer that will enable operations managers to specify their deployment environment and architects to verify that their application will work within the specified deployment constraints. These tools use software models to capture the knowledge of a designer's intent, knowledge of an operational environment, and knowledge of IT governing policies to ensure IT systems are designed with operations and manageability in mind from the start. The models described can be built using Visual Studio 2005 and then consumed by Microsoft management tools and any other third-party tools that are built to consume the models, which are based on an open specification.
System-Level Management
Models can capture the entire structure of an application, including all the underlying and interrelated software and hardware resources. Management tools, such as future versions of MOM, will use those models to provide a system-level view of the health and performance of that application, enabling administrators to understand the impact of changes or errors in the system and to manage the application more effectively.
This system-wide view will enable future versions of management tools, such as MOM, to perform robust health monitoring and problem solving, as well as end-to-end performance and service-level management.
Policy-Driven Operations
Models can also capture policies tied to IT and corporate governance, such as Sarbanes-Oxley compliance or basic security standards and operating system versioning. Management tools, such as future versions of Microsoft SMS, will use these models for desired-state management.
By comparing the model of the real-world state with the model of the compliance definition, management tools can make systems compliant before allowing them access to corporate resources.
Hardware Abstraction
Software models can capture an entire system's composition in terms of all interrelated software and hardware components. As a result, a system will contain a specific description of the hardware requirements of the environment into which it will be deployed.
This knowledge will enable new resource management technologies, such as Microsoft Virtual Server, to interpret these hardware requirements and to be used by management tools to ease the initial provisioning, ongoing change, or removal of hardware from an application based on changing business needs.
Next Page
Management Strategies
Microsoft's strategy for delivering the Dynamic Systems Initiative is to leverage and extend existing management solutions to take advantage of the model-based approach to systems management. Visual Studio 2005 Team System and MOM 2005 with management packs are great examples of products that deliver on the DSI vision today. With these investments and those planned for the future in products such as SMS and other System Center products, the Dynamic Systems Initiative clearly signals Microsoft's long-term commitment to reducing complexity across the IT lifecycle and making it possible for IT professionals to deliver greater value to their businesses.
Looking toward the future, Microsoft is working to develop products and enable solutions that will unleash the potential of SDM to simplify and automate information technology. Microsoft will both deliver and enable a new breed of application development tools that make it easier for companies to leverage the Design for Operations methodology. Windows and supporting applications and services will evolve to manage distributed resources across a data center, provide users with dynamic system-level views of their environments, and offer new core services targeted at simplifying the deployment and operations of distributed systems. Windows Server System applications, including SQL Server, Exchange Server, and BizTalk Server, will support SDM to deliver a greater set of management capabilities for IT professionals and their customers. Coupled with Microsoft's commitment to management packs shipping with new software releases, IT administrators will be able to deploy new solutions and have confidence in their ability to be supported in demanding environments much more quickly than before.
Next Page
Summary
In this chapter, we covered the following:
Systems management on the Microsoft platform Operations, configuration, and release management Dynamic Systems Initiative
By combining health and state with alert information, IT operators no longer have to perform research to understand the organizational impact of alerts. By maintaining awareness of system and service availability, IT staff is better able to identify, address, and resolve IT reliability and performance issues before they become serious problems and negatively affect business applications. Through the use of State Modeling and directly monitoring the event, health, and performance information of Windows Server System, MOM 2005 highlights relevant and important information that can be captured, evaluated, and presented to operators, helping prevent issues from going unseen. Tools such as SMS and Microsoft Update expand the solutions through configuration management capabilities that help administrators to deploy solutions and drive toward desired configuration through automated reporting, software deployment features, and other management capabilities.
Going forward, Microsoft plans to deliver and enable a new category of closed-loop, system-level management solutions that provide new levels of automation in the data center and tie business policies directly to IT systems. By adopting solutions from Microsoft and its partners today, IT professionals can realize reduced costs and gain more time to proactively focus on what is most important to support their organizations. For information technology organizations that are looking to get started with systems management or to become more mature in the approach to managing their systems, products such as MOM 2005, SMS 2003, and Microsoft Update are key components of a well-managed technology environment. In Chapter 2, we take an in-depth look at the features of these products and learn more about how they work together to support systems management.
Next Page
Chapter 2: MOM, SMS, and WSUS—How They Fit Together
Overview
A major challenge for IT administrators faced with managing their technology infrastructure is figuring out which tool is best for which job. With MOM, SMS, and WSUS and Microsoft Update, it is important for the administrator to understand the features of each tool and to understand how the tools work together. In addition, where there is some overlap in functionality between the tools the administrator needs to understand the benefits of using one tool over another. In this chapter, we cover the following:
MOM: A solution for operations management SMS: A software deployment and management solution WSUS: Update services for decentralized environments MOM, SMS, and WSUS
You get a functional overview of MOM, SMS, and WSUS and the Microsoft Update components. You compare the products, understand how they fit together, and review criteria to help you decide when to use which of the products.
To get started, let's describe what each product is designed to do. MOM 2005 is a solution to enable operations management that provides event and performance management, proactive monitoring and alerting, reporting and trend analysis, and system-specific knowledge and tasks to improve the manageability of your servers and applications. While MOM 2005 is primarily focused on managing Windows-based servers, there are third-party solutions that enable you to manage server applications and services running on other platforms as well. SMS 2003 enables you to manage client computers and servers within your organization, including tasks such as troubleshooting, software asset management, software distribution, software updates, reporting, and many others. WSUS enables IT administrators to deploy the latest product updates to Windows Server 2000, Windows Server 2003, and Windows XP operating systems. By using WSUS, administrators can fully manage the distribution of updates that are released through Microsoft Update to computers in their network. When you look at the descriptions for each product, there is some overlap conceptually. As we drill into the details, the distinction will be much more clear. We'll start with MOM 2005 and how it supports operations management functions.
Next Page
MOM: A Solution for Operations Management
MOM 2005 includes a variety of features designed to make it easier for administrators to deploy and use the management tools, improved support for management packs and reporting, and features to ensure that the management infrastructure is secure and reliable. We break down the features based on how they're used to support operations management and point out different features including administration, operations, and reporting that are essential to the overall management solution.
The deployment of MOM starts out with the administration and configuration of the management environment. A number of important features enable the administrator to more effectively configure the operations management tools to simplify the operations and monitoring processes. One such feature is Computer Groups. MOM enables you to create groupings for computers by common elements, including geographical location, function of the servers, or other application dependencies. Groups of computers are shown in the view of the MOM Administrator Console in Figure 2-1. From this view you can see all of the settings available to the administrator and gain a quick view of the computers available to manage.
Figure 2-1
The actual mechanics of the operations management process in MOM are driven by setting up tasks in the operations management console. A task is an action that is executed on the Operator Console against an alert, event, or computer. This type of task is useful to automate user activities that would otherwise be performed by a user. The action that is executed as part of the task is specified in terms of a command line for execution. When a task gets launched, the properties are passed to the command line to ensure the proper execution.
Several tasks can be configured in MOM. For instance, a user might want to use the terminal server client to connect to the computer that raised an alert; the user can create a console task that runs against an alert item. For example, the user could set up a monitor for a given directory to ensure that log files are being updated as expected. As you would expect, the events in those logs that are relevant can be captured in other ways, but a task to ensure that logs are being updated can ensure that issues that may arise in a system will be appropriately logged for diagnostics and root cause analysis.
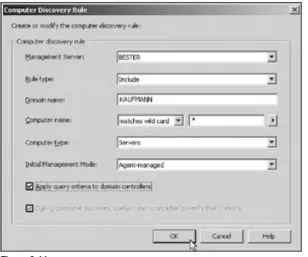
A number of setup and configuration tasks are supported in the MOM administration console. After your initial installation of MOM, a detail pane in the administration console displays several startup tasks that can be performed rapidly. The first option, Install/Uninstall Agents Wizard, enables you to specify computers or use discovery parameters to add computers to your Management Group.
The Install/Uninstall Agents Wizard can also be launched from several other places in the MOM Administrator Console, including the root Microsoft Operations Manager node in the Navigation pane, the Administration node, and the Computers subnode and all of its children. Through the use of these agents, much of the MOM monitoring activities can be performed. While agents are core to the architecture of MOM and enabling management, agentless monitoring is also supported. Agentless monitoring is the ability to monitor remote resources in a manner that is similar to how local resources are monitored through providers and responses. If providers that support remote access to resources are used and the responses can execute its logic remotely, then those sets of rules work the same way on both agentless and agent-managed computers. Once identified, MOM starts monitoring the agentless computer as though there were an agent installed on the computer. To enable this kind of access, the MOM account used for this action must have administrative rights on the computers being managed without agents. The console view for adding agentless managed computers is shown in Figure 2-2.
Figure 2-2
A significant number of functions can be performed through agentless monitoring. Some of the important functions include the following: State monitoring.
Heartbeat: A MOM Management Server pings the agentless computer at intervals specified by the user to ensure that it is available. Service discovery and status.
Performance counters. Internal service monitoring events.
Event collection: These include timed, Event Log, WMI, internally generated, and script-generated.
There are some limitations to agentless monitoring. This type of monitoring does not support application log providers, and descriptions of event log entries on the agentless machine are not displayed on the MOM Management Server unless it has the same EventLogmessages.dll file as the agentless computer. A workaround is to install the software for which you'd like to receive event log entries on the MOM Server. Here are some considerations for agentless monitoring:
Agentless monitoring does not work through a firewall in typical configurations because agentless network traffic contains remote procedure call (RPC) and Distributed Component Object Model (DCOM) calls.
Not all management packs work in agentless mode. Therefore, it might not make operational sense for your management pack to work without an agent if the bulk of the monitoring scenarios leverage providers that are not supported without an agent. This is especially important when considering third-party management packs.
Operator Console. This is not a security feature, but rather a filtering tool to enable users to focus on a specific set of servers while using MOM Operator Console tools. The console scope settings also apply to other SDK-based tools associated with the same account.
Figure 2-3
The Administrator Console features described previously are important, but most of the action with MOM occurs in the operations console. This is where the day to day monitoring and uses of MOM tools will likely occur. MOM 2005 provides a set of view types for the operations console that are backward compatible to MOM 2000 but provide better usability for MOM users, including administrators and operators. All the views can be authored, imported, and exported. The console makes it simple to switch between views, drill down to details, and launch context-sensitive tasks. The views included are Alters, State, Events, Performance, Computers, and Diagrams. Let's look at each one of these views and how they support the operations management process.
The Alerts view enables the user to view alerts globally, based on filters or by system component where the alert originated. As you can see in Figure 2-4, the alerts can be sorted by a variety of criteria. There are tabs related to the alert and the user can drill down for detailed information. The State view in the Operator Console enables the user to view the state of a particular computer and view areas of problem by installed components. The Event view is similar to the Alerts view, incorporating items from the event log and enabling you to view the alerts associated with particular system events. The Performance view enables you to view the performance counters associated with a particular computer, and then to select the items you wish to see, as shown in Figure 2-5. The results can then be graphed for further analysis. The Computer and Groups view enables you to view alerts by machine and monitored components. The Diagram view provides a view of the servers in your environment and the ability to customize those views based on different criteria.
Figure 2-4
Figure 2-5
In addition to the administration and operations tools, MOM provides a data analysis and reporting solution. MOM's data and reporting tools contain some of the following features: Web-based reporting
Dynamic reports with drill down, charting, and sorting Long-term offline storage and data analysis capabilities Customization of reports through Visual Studio
Support for exporting data to other formats including Excel, PDF, CSV, and others Folder-and report-based security
Support for interactive and published reports
Scheduled publishing and delivery based on report type or content changes
Figure 2-6
Through the support for the configuration of tasks and rules for alerts in the operations management environment combined with an operations console and extensive reporting capabilities, the MOM environment provides a fully featured solution for managing computers and applications in an IT environment. While these capabilities are important, they need to be coupled with a strategy for desktop computer management, software deployment, and other capabilities such as configuration and release management that help IT administrators to deal with the issues in their environment on a reactive and proactive basis. The solution for these issues requires support for automated software deployment and systems management to enable remediation of issues on a per-computer basis or across a broad set of computers defined by different groupings.
Next Page
SMS: A Software Deployment and Management Solution
Systems administrators have relied on tools to enable automated software distribution and deployment and to perform other management functions since the early days of network computing. As PCs have proliferated, the problem of managing individual computers has become more important to the health of the overall technology infrastructure. SMS is designed to help IT administrators contain the cost of managing distributed systems by allowing the number of deployed computers and installed applications to increase without requiring substantial investment in additional manpower for technical support. Managing client computers within an IT organization includes tasks such as troubleshooting computers, managing software assets, and analyzing network problems. These tasks can be complex and time consuming, preventing IT staff from focusing on new deployments and upgrades to existing systems. SMS helps to solve this challenge in IT.
SMS 2003 addresses the following key issues that IT administrators face in managing distributed computing environments: Managing computers that roam among locations and connect to the network from different geographical locations Tracking deployment and use of software assets, and using this information to plan software procurement and licensing Providing IT administrators and management access to data accumulated by SMS
Managing security on computers running Windows operating systems in a scalable manner
To help solve these issues, SMS 2003 provides a number of key features. These include support for collections and queries, hardware and software inventory, software distribution, software update management, software metering, reporting, product compliance, security, and many others.
SMS manages resources such as client computers and software. Logical groups of SMS resources having common attributes are called collections. Collections are defined by queries that are refreshed at intervals specified by an administrator. A resource that no longer meets the collection criteria is removed from the collection and a resource that meets the collection criteria is added to the collection. SMS features can operate on clients only if they are members of a collection. By default, all SMS clients are members of the All Systems collection (shown in Figure 2-7). These collections form the basis for how SMS manages systems in your environment.
Figure 2-7
Another major feature is that hardware and software inventories on client computers can be performed by SMS. You can run a wide variety of reports against the resulting data, which can help you plan upgrades, track hardware and software assets, or compare the report output to software licensing data. Before you deploy a new software package, you can build a report that shows how many destination computers have the required memory and disk space to support the software package that is planned for distribution. This allows you to upgrade non-compliant systems before the deployment begins, ensuring a higher overall project success rate. You can customize the hundreds of types of data that can be recorded when you gather information during hardware and software inventory collection. This helps you to attain the appropriate balance between performance and inventory depth for your organization. SMS 2003 provides control over which software files should be scanned. Software inventory can scan specific directories and drives, using environment variables to optimize the data-gathering process. SMS has been designed to use Windows Management Instrumentation (WMI). SMS has access to data from many sources, including the Win32 API and Simple Network Management Protocol (SNMP), which provides administrators with a broad base of inventory and configuration data.
In addition to the useful hardware inventory features, there is extensive support for software inventory as well. A granular file inventory search is available in SMS 2003 and can be configured to retrieve only the necessary assets during discovery. This is done with wildcards, environment variables, and file properties to control software inventory searches more effectively. Other options allow for compressed and encrypted files to be skipped. In addition, the Add/Remove Programs list and other software installed by Windows Installer technology can be queried to validate against file inventory data in the case of corrupt or incomplete installations. This provides a check against pure file-based inventory data.
SMS also significantly reduces the time and complexity of maintaining and upgrading software for organizations with distributed networks. You can upgrade and configure each computer from a central location or from multiple locations. You can schedule individual software files or software programs for distribution to specific computers. You can also initiate unattended software installations to selected computers. Software installation packages can come ready for installation from Windows Installer using *.msi files or can be created with the SMS Installer. Software distribution can be directed to computers based on collected information, including network and hardware configuration, group membership, and software installation status. If an SMS client computer is added to a group, software is automatically sent to the client according to predefined administrative settings for that group. Likewise, new computers matching a predefined destination, such as by IP subnet or installed peripheral, automatically receive specified packages or driver updates. Also there is a Courier Sender feature that allows software to be sent between SMS sites by CD or other media, rather than across the network. This is particularly useful in situations where the available network bandwidth is low or too expensive to use for the delivery of large update packages.
SMS can also be used to remove deployed software and applications from particular computers or groups. Software distribution uses Background Intelligent Transfer Service (BITS) technology, which can transfer files from distribution points that are BITS-enabled. And if a file download is interrupted in progress, a checkpoint is set. You can resume the file download and then proceed from the checkpoint rather than restarting the download from the beginning. On reconnection, any partial downloads to clients continue where they left off. There is no need to restart transmissions because of a disconnected session.
One of the more important features of SMS that drives many administrators to use it is the support for software updates. Software update management in SMS is the process of keeping computers and servers that are running Windows operating systems updated with security updates or patches, and includes the following functions:
Performing an inventory of the installed and applicable updates on managed computers Evaluating and testing available updates
Authorizing and distributing the updates Tracking software update compliance
You can use these tools to take advantage of the critical software updates that Microsoft provides for Windows operating systems, Microsoft Office, SQL Server, Exchange, and other system software. Several software update management tools are installed by default on the SMS site server. These include the Distribute Software Updates Wizard and the Software Updates Installation Agent, along with a collection of predefined reports for software updates. Let's take a look at those tools in greater depth to understand their function.
The Distribute Software Updates Wizard performs the following tasks:
Uses inventory information to analyze the applicable software update status for client computers Provides a method of reviewing and authorizing suggested software updates
Downloads authorized software updates and installation information
Builds packages and advertisements tailored to specifications for each software update or set of updates Distributes software update advertisements to client computers by using SMS software distribution
available for download include the Security Update Inventory tool, which scans a client computer for installed software updates to Windows operating systems, Internet Explorer, SQL Server, and other software.
In addition to software update management tools that are described in the previous section, SMS 2003 includes some other enhancements over the previous versions of SMS. One example is the persistent notification for software updates. This is an icon that appears in the system tray whenever a user is logged on and there are pending, but uninstalled, software updates. When the computer is in compliance, the notification area icon does not appear. The notification area icon can be used to support user needs as well. For instance, the program associated with the icon can schedule installations and reboots to occur at convenient times of the day or facilitate the install of software updates immediately. The Unattended software update installation provides a method to deploy mandatory updates to client computers silently. No notification icon appears in the notification area, and users with insufficient rights cannot terminate the process in Task Manager.
Efficiently managing the software products, services, and applications deployed to an organization is important to IT. SMS 2003 does this with its software inventory and software metering features. The focus of software metering in SMS 2003 is collecting and reporting software program usage data. You can use SMS 2003 software metering data to identify which applications are being used and which users are running them along with the number of concurrent application usages, software license requirements, redundant software installations, and unused software applications that can be reallocated.
Software metering is fully integrated with all other SMS components and is accessed through the SMS Administrator Console. In addition, SMS 2003 software metering data is now stored in the SMS site database with other SMS data. SMS 2003 software metering includes software usage history, and enables trend analysis and audit reporting. You can use this information to track software license usage and produce license compliance reports. An SMS site administrator can configure this process to suit your needs. They can also configure SMS 2003 to track software usage on managed SMS client computers on and off the network. SMS clients record software usage even when they are disconnected from the network by uploading usage reports either on a schedule or the next time a connection is available to the SMS site.
Summary and detail reports can be generated describing which applications were used by which users, for how long, and on which computers. Usage can be tracked by user or computer and the reports can be created comparing concurrent usage data to current license ownership, helping organizations to ensure compliance and track usage for budgeting and planning purposes as well.
Beyond the software update and metering features, there are some useful performance monitoring features in SMS 2003. The system provides a wide range of performance monitor counters that are accessed using the Windows System Monitor. These counters are helpful for maintaining SMS, identifying problem areas, tuning SMS systems, and troubleshooting. System Monitor gathers information about growth patterns that you can use to plan for future hardware growth. SMS 2003 also provides a comprehensive set of predefined, secure reports with information about the client computers across the SMS hierarchy and the current state of managed systems across an organization. You can provide management and other SMS users with reports that can be viewed using Internet Explorer. Reports include hardware and software inventory data, computer configuration details, and software deployment, deployment errors, and usage status. SMS reports are extensible, enabling you to generate custom views and reports. You can use the SMS Administrator Console to create and manage reports. All reports are based on SQL, and administrators and other users who do not have access to the SMS Administrator Console can run reports by using the Report Viewer in Internet Explorer. You can export and import reports by using the Export Object Wizard and Import Object Wizard in the SMS Administrator Console, as shown in Figure 2-8. Use exported report files to share reports with other SMS administrators or to import reports obtained from another SMS administrator. Using Report Viewer, you can also create dashboards, which are sets of reports displayed in a grid, in a single window to monitor information about a variety of SMS objects or systems. All of these capabilities enable you to provide the right data to the right people, regardless of their status within SMS or knowledge of the system.
Figure 2-8
This extensive set of features in SMS enables a full software deployment and lifecycle management solution that IT can rely on for critical systems management functions. However, some of the features in SMS may not fit as well in certain IT environments or may require some complementary solutions. One of those solutions is Windows Server Update Services (WSUS). Let's take a look at how WSUS can help to manage decentralized IT environments when SMS isn't the right fit.