Another problem with studying operating systems is that there is a lack of material to understand the design of a kernel. This dissertation/thesis titled “DEVELOPMENT OF KERNEL FOR RISC ARCHITECTURE SYSTEM” was prepared by Ng Chun Hong and submitted in partial fulfillment of the requirements for the degree of Master of Computer Science at Universiti Tunku Abdul Rahman.
INTRODUCTION
Introduction
Problem Statement
On the other hand, we have full chip level functional verification, where the entire chip is verified at the transaction level. It also indirectly verifies the integration of modules that make up the entire chip or processor.
Project Scope
We can use a single standalone program as in embedded application programs, but this type of program is not as extensible and complete as in a core function that more thoroughly tests the processor at the full-chip level. After the full-chip verification is complete, the core can be further expanded into a more complete software with customizable features that the processor supports.
Project Objective
LITERATURE REVIEW
Computer Architecture and Operating System
Their aim is to introduce a new architecture and further improve the understanding of an operating system. Such an approach is identical to the microkernel design, but their approach allowed the operating system to be more extended.
Application Binary Interface
In their work, they used a component-oriented design to separate the modules of the operating system.
Object File Format
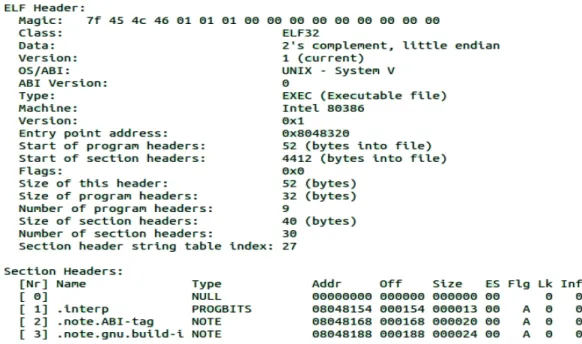
Executable and Linkable Format (ELF)
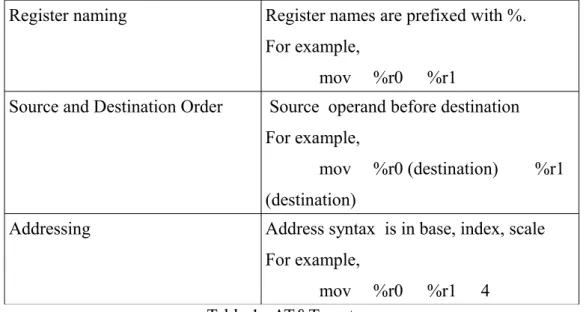
Assembly for Arm
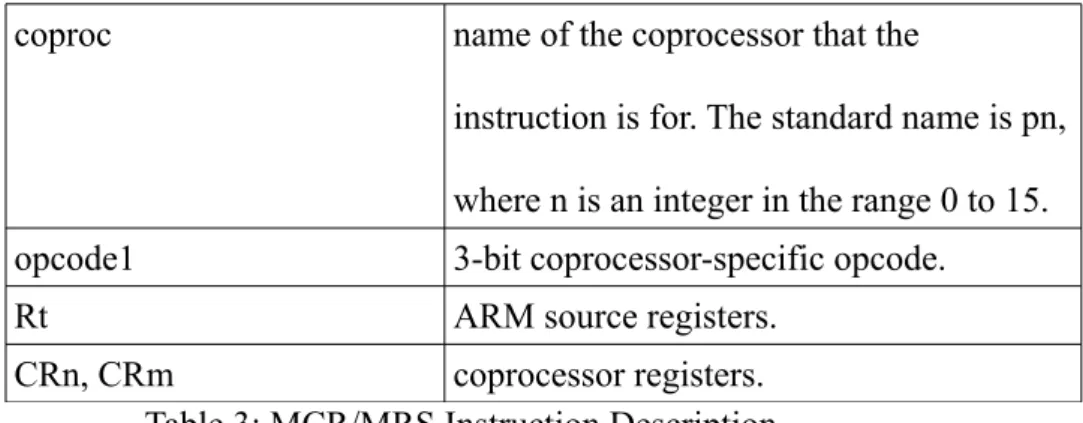
To access the program status register, the MSR/MRS instruction is used to read or write values in status registers. To access the coprocessor, the move ARM register to the coprocessor (MCR) and move the ARM register from the coprocessor (MRC) instructions are used.
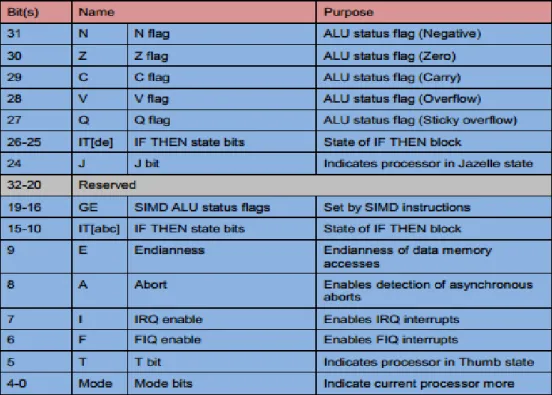
Operating Mode
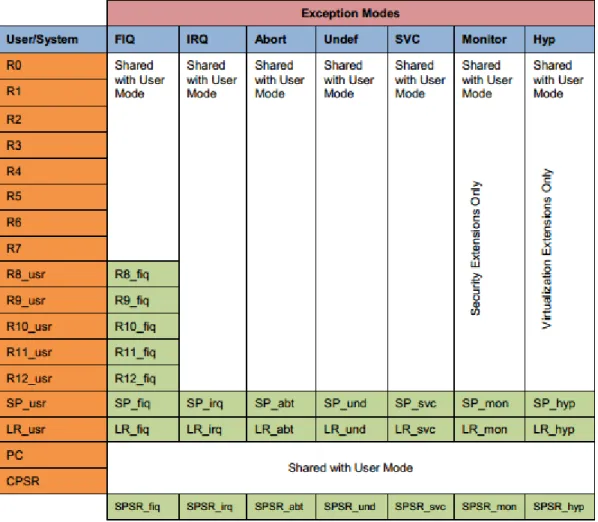
List of register in ARM architecture
On the other hand, ARM has r0-r9 for the same purpose with a large number of general purpose registers that allow the programmer flexibility in coding. R13 is typically used as a stack pointer (as specified in the ARM ABI), R14 is a link register that contains the return address for a function call, R15 is a program counter, and R16 is a CPSR. Just like CPSR, SPSR is responsible for storing the value in CPSR when the CPU changes mode.
SPSR to CPSR when the system switches back from privileged mode to non-privileged mode.
Endianess
Kernel Functionality
Type of kernel
- Micro kernel
- Monolithic kernel
It is highly recoverable as only a few services run in kernel space, so user space programs can be restarted when problems occur. Another advantage is that it is portable, with only a few services having to be changed if the core needs to be ported to other platforms. The advantage of a monolithic core is that it is faster because each service runs in the same space.
The main drawback of a monolithic kernel is that it is not possible to recover if a kernel service crashes.
Memory Map
A microkernel is a minimal kernel that performs only minimal services, such as memory and process management, that allow the operating system to function. However, operating systems like Linux are very stable and almost crash-free due to reliable code and extensive testing.
Memory Management Unit in ARM
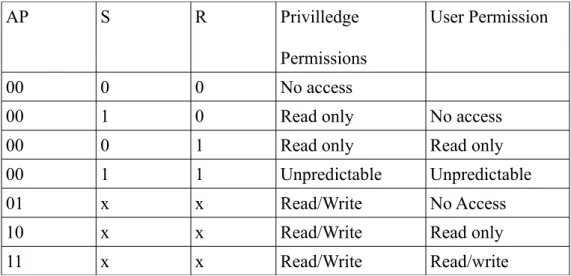
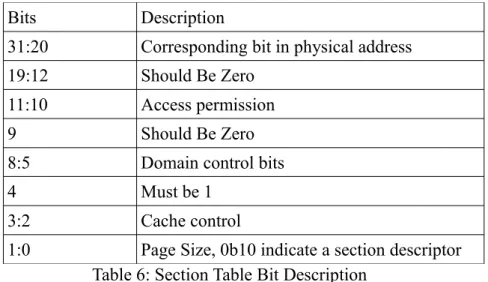
Memory access control in MMU is achieved by checking against the domain control and access permission. There are 16 domains available for use, and each of the domain roles is defined in the domain access control registry (c3) in CP15. When a page is set to a domain belonging to the manager role, the access control and control registers are ignored, meaning no access control is used.
The following table lists the access control when a page is placed in a domain that belongs to the client role.
TOOLS AND METHODOLOGY
Development methodology
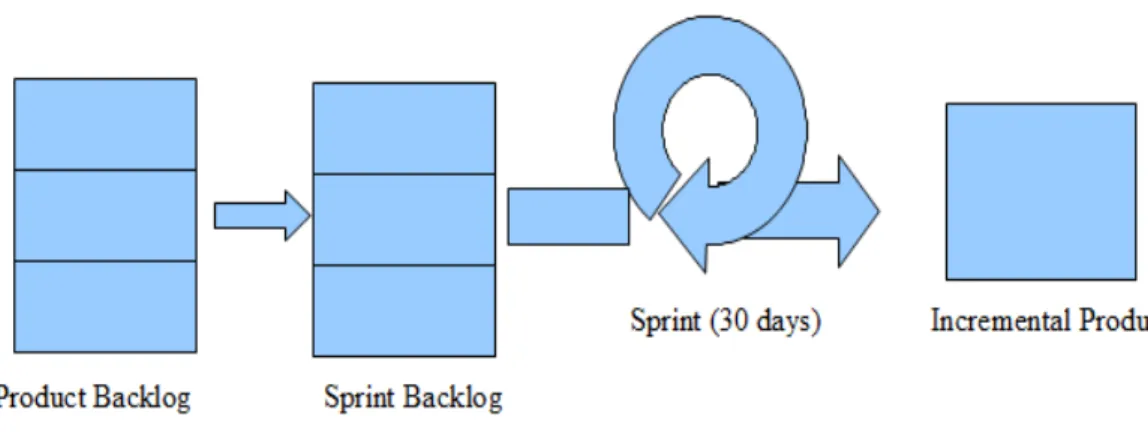
Product support is the document that lists the requirements or tasks from the product owner. Based on available capacity, the scrum master will select items from the product backlog and place them in the sprint backlog. The items in the sprint backlog indicate that these are the tasks to be completed within that particular sprint.
A sprint can be abandoned if there is a change request, or extended if the sprint task requires more time than planned.
Targeted ARM platform
This product is an incremental result of the previous sprint and is also an indicator of the development progress.
Toolchain
For example, if full C functionality is needed, the toolchain must be built with glibc. Embedded Linux Development Kit (ELDK) is the cross development tools used in this project. ELDK that supports older ARM families can also be used since the ARM toolchain is backward compatible.
However, in doing so, the toolchain will not use the new ARM feature that is available in newer architecture families.
Emulator
For example, an ARM emulator is a program that runs in an x86 environment that mimics the behavior of a real ARM system. In this project, the QEMU emulator is used because it supports the chosen ARM platform. QEMU emulator is available in 2 different modes namely user space mode and kernel mode.
When a program is compiled with the ARM toolchain, userspace mode can be used to run it.
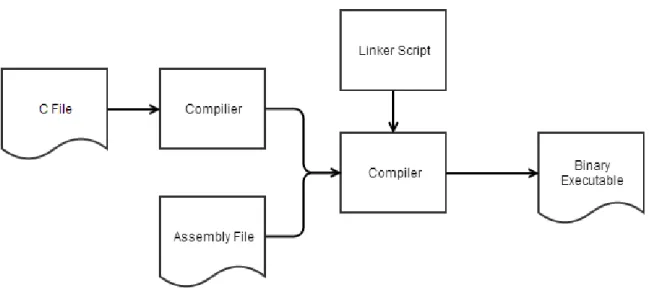
Linker/ Linker Script
The user can terminate QEMU at any time (ctrl a + x) and it will not affect the host system. The linker script can be very complex to include many other aspects of how to link a file. For example, specifying from which memory area to allocate the linker, or how to specify a program header in ELF.
If the user did not specify any of these, the linker will use the default rule to generate the binary output.
GNU Compiler Collection (GCC)
GNU Project Debugger (GDB)
Bootloader
For PC, the BIOS is responsible for loading the operating system into memory for execution. ARM on the other hand boots the bootloader from the ROM (built by the vendor). If the kernel supports device tree, the bootloader will send a device tree binary to the kernel so that the kernel can initialize the driver when a system boots.
For example, the user can choose to boot from the network or load a file from the file system.
Automating Build Process
Source Code Management
DESIGN AND SPECIFICATION
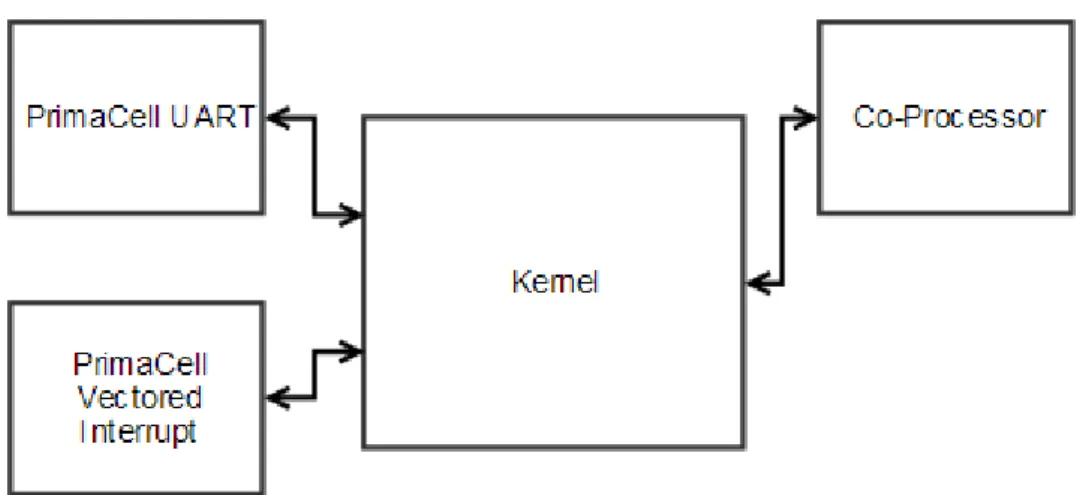
System Environment
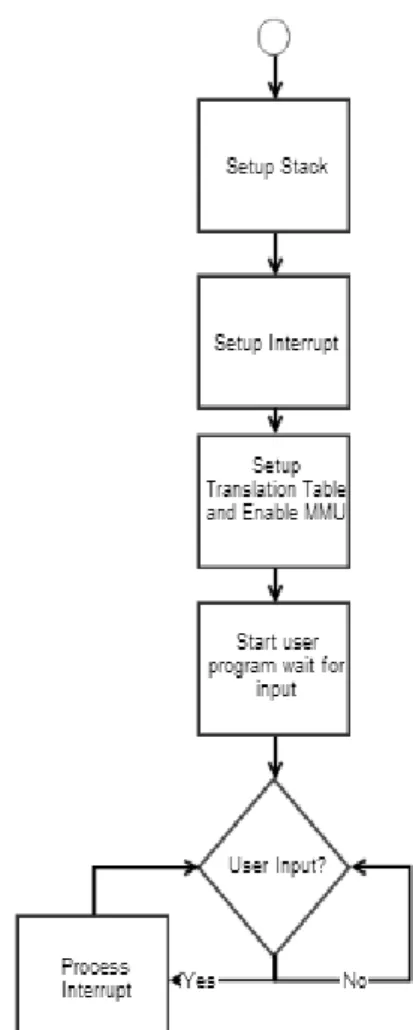
System Flowchart
Memory Layout
Product Backlog
Functional Requirement Specification
User Story 3: As a developer, I want to have a suitable development environment that can be used for kernel development. User Story 5: As a developer, I want to be able to bundle multiple object files into a single boot image. User Story 6: As a developer, I want to be able to upload my program to the development board and run it.
User Story 7: As a developer, I want to automate the compilation and run process to speed up development.
IMPLEMENTATION
Development environment (User Story 3)
Setting up toolchain
Linking option and script (User Story 5)
System Startup Script (User Story 6)
It is possible to have the ability to check the stack limit to prevent the stack from overflowing. Toolchains that conform to the ARM EABI may allow the linker to generate code that performs software stack boundary checking.
Automated Build Process (User Story 7)
Interrupt Service Routine (User Story 9)
The interrupt controller in the target development used in this project supports both vectored and non-vectored interrupts. The difference between them is that the vectored interrupt stores the address of the ISR in the interrupt controller, so the kernel can read from the VICVECTADD register in the interrupt controller to determine the ISR address. While the non-vectored interrupt on the other hand requires the kernel to read from the VICIRQSTATUS register in the interrupt controller to determine the source of the interrupt.
System Operating Mode (User Story 10)
Memory Management Unit (User Story 11)
In this project, two domains are defined, namely the manager in domain 0 and the client in domain 1. C1 in CP15 is the control register that the user can set to configure the MMU.
Supervisor Call (User Story 12)
In the ARM instruction, the last 24 bits of the SVC call store the value passed by the SVC call. The kernel can then determine the intended SVC call by masking the irrelevant bits.
Device Driver (User Story 13)
In this project, since UART0 is taken as input and UART1 as output, the driver for these devices must provide functions like reading from UART0 and writing to UART1. If a new device is added to the hardware, for example a display device connected to GPIO, the programmer must write the driver to send or read data in the correct format to use the device. When an interrupt occurred for UART0, the ISR will branch to the UART0 interrupt handling function.
The driver writes the UART0 input to the temporary memory storage (refer to the device list).
Porting Guide
Testing and Result
Development environment test result
Linker Script Test Result
Interrupt Service Routine Test Result
Comparison On Interrupt Handling
The kernel in this project only manages devices that are already available on the system. As a result, the kernel must be recompiled whenever a new device is added to the system.
Operating Mode Test Result
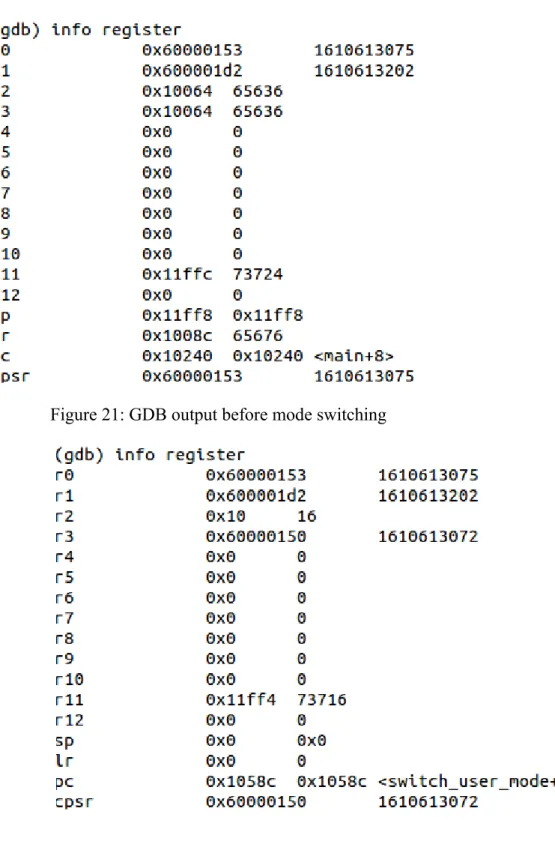
Once the system is running in user mode, the user program can no longer access special registers such as CPSR and other hardware memories. Another function that can be tested is when the system changes the operating mode, the registry value will also be replaced. It is therefore the responsibility of the kernel to copy the required value from one mode to another.
An example of these values is the lr value - when the kernel completes its initialization work and calls a switch user mode function, the kernel will have to copy the lr value manually, otherwise the system cannot continue execution.
Memory Management Unit Test Result
Memory Manaagement Unit Usage In Other Kernel
Apart from memory protection, another purpose of MMU is to allow the kernel to implement virtual memory. When virtual memory is enabled, the kernel and user program will run their own virtual memory space [15].
Supervisor Call Test Result
System Call For Device Input Output
System calls are a set of functions that provide kernel for user space application to use system resources. However, the provided system calls cannot cover all possible operations for all supported devices. To solve this problem, the kernel provides input/output control (ioctl) system call to allow the communication between user application and device driver [17].
When a user application makes an ioctl call with specified control code, the driver running in kernel space will perform the operation on the driver.
Device Driver Testing
When the user enters a character, the program will echo the character to the output of UART1. Memory-mapped devices in ARM are accessed by directly reading or writing to the memory location. In this project they are accessed via memory pointer, this approach is straight forward and mainly to demonstrate how to use a device.
When data is written into the device node, the device driver will process this data and send it to the device.
Project Time line
CONCLUSION AND FUTURE WORK
1] Zhou Qingguo, Ding Ying, McGuire, N., Li Canyu, Cheng Guanghui en Hu Bin, "'n Gevallestudie van mikrokern vir onderwys", IT in Geneeskunde &. Ahmad, "Performance Comparison of Single Board Computer: A Case Study of Kernel on ARM Architecture", Computer Science & Education (ICCSE), 2011 6de Internasionale Konferensie, pp. 4] Messer, A., Wilkinson, T., "Components for Operating System Design", Object-Orientation in Operating Systems, F.199 International Works, F.