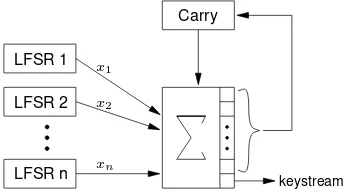
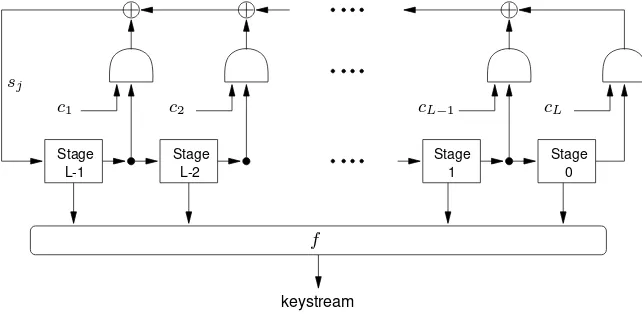
Handbook of Applied Cryptography
Teks penuh
Gambar
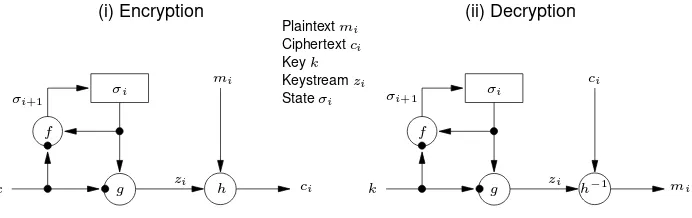
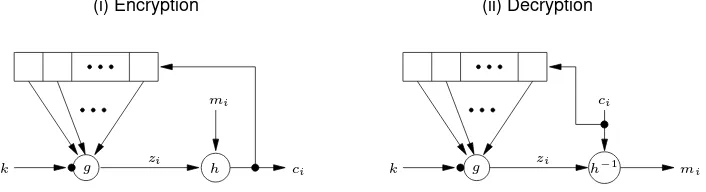
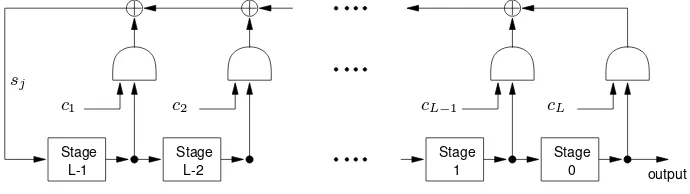
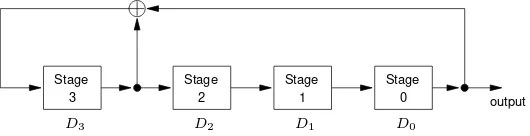
Garis besar
Dokumen terkait
Gedung H, Kampus Sekaran-Gunungpati, Semarang 50229 Telepon: (024)
Setelah dilaksanakannya budidaya ikan lele sangkuriang, diharapkan siswa dapat meningkatkan pengetahuan dan keterampilan dalam berwirausaha budidaya ikan lele
Based on a rigorous as- sessment of available temperature records, climate forcing estimates, and sources of natural climate variability, scientists have concluded that there is a
Jawapan hendaklah ditulis dengan jelas dalam ruangan yang disediakan dalam kertas soalan.... Bulatkan dua jenis makanan
The comments were taken from the following German websites: the conservative news sites Bild.de (Bild) and Welt.de (Welt), the liberal news sites Spiegel.de
In general, urban health expenditure in Indonesia was significantly different with their counterparts in rural areas, with average health cost is higher in urban
Transaksi pembuatan daftar gaji dan upah, salah saji potensialnya orang yang tidak diotorisasi masuk ke dalam daftar gaji, aktivitas pengendaliannya adalah pemisahan fungsi,
Clinical Profile of Extrapulmonary Tuberculosis Among TB-HIV Patients in Cipto Mangunkusumo Hospital.. Gurmeet Singh 1 , Anna Uyainah 1 , Evy Yunihastuti 2 , Darma