How to Configure Standard Access Control
List in a Packet Tracer and GNS 3
1 Access List, Standard 02:17
ACL-Access Control List (Named Access List and Number Access List).If we use numbers
to refer access list it is numbered access list.If we use Name to refer access list it is named
access list.
we are using access list to permit or deny ip packets based on our requirements.There are two
types,
1.Standard Access List
2.Extended Access List
Here we are going to see how to configure standard access list with a simple topology in a
packet tracer,
Step 1:Create a topology like this,
Step 2:Configure router with ip address that i have given in topolgy.Assign ip address to all
PC and server like in topology.
Router(config)#interface fastethernet0/0
Router(config-if)#ip address 10.0.0.1 255.0.0.0
Router(config-if)#no shutdown
Router(config-if)#exit
Router(config)#interface fastethernet1/0
Router(config-if)#ip address 20.0.0.1 255.0.0.0
Router(config-if)#no shutdown
Step 3:Three steps to configure access list on router,
1) Creating Standard Access List
2) Choosing an Interface for Binding
3) Choosing In/Out
Step 4:Create an Standard Ip access list to deny a host 10.0.0.3 to server.
In standard access list, it filters based on source ip address.we can't deny of permit packets to
destination or particular ports for that we have use extended access list later we see this,Now
lets we create a standard access list based on above statement i have given.
Create Access List:
Router(config)#access-list 1 deny host 10.0.0.3 (or)
Router(config)#access-list 1 deny 10.0.0.3 0.0.0.0
Router(config)#access-list 1 permit any
where '1' is a number.It refers, this as a Standard accesss control list.It can be '1 to 99' and
'1300 to 1999'.
'Deny' Allows router to deny the packet that matches this statement.
'Host 10.0.0.3' when we configure like this it refers 'Only this host will be permitted or
denied' or we should configure with wild card mask '0.0.0.0' it means router checks for entire
four octets if matched then it will process based on access list.
configure 'permit any' statement first and then deny,If we configure permit any statement
first, access list will check first statement if matches it will forward the packet and it won't go
for next statement that 'deny'.Always we should configure 'deny' statement first.
Choose Interface for Binding whether In or Out:
Always we have to choose an interface near to the source as much as possible.Sometime
based on some access list statement we need to choose interface that packets go out of the
router.we should try to use router interface that receives a packet from PC in a LAN.
So,I am going to choose 'interface fastethernet0/0' .Before that i am going to check access list
status for this interface.
In Privileged Mode,
Router#show ip interface fastethernet0/0
FastEthernet0/0 is up, line protocol is up (connected)
Internet address is 10.0.0.1/8
Broadcast address is 255.255.255.255
Address determined by setup command
MTU is 1500
Helper address is not set
Directed broadcast forwarding is disabled
Outgoing access list is not set
Inbound access list is not set
Proxy ARP is enabled
Security level is default
Split horizon is enabled
ICMP redirects are always sent
ICMP unreachables are always sent
ICMP mask replies are never sent
IP fast switching is disabled
IP fast switching on the same interface is disabled
IP Flow switching is disabled
IP Fast switching turbo vector
IP multicast fast switching is disabled
IP multicast distributed fast switching is disabled
Router Discovery is disabled
IP output packet accounting is disabled
IP access violation accounting is disabled
TCP/IP header compression is disabled
RTP/IP header compression is disabled
Probe proxy name replies are disabled
Policy routing is disabled
WCCP Redirect outbound is disabled
WCCP Redirect exclude is disabled
BGP Policy Mapping is disabled
In global configuration,
Router(config)#interface fastethernet0/0
Router(config-if)#ip access-group 1 in
Router(config-if)#exit
where '1' refers access list 1 and packets that comes into the router will be filtered based on
access list.
Now,Check the access list status on this interface.
In Privileged Mode,
Router#show ip interface fastethernet0/0
FastEthernet0/0 is up, line protocol is up (connected)
Internet address is 10.0.0.1/8
Broadcast address is 255.255.255.255
Address determined by setup command
MTU is 1500
Helper address is not set
Directed broadcast forwarding is disabled
Outgoing access list is not set
Inbound access list is 1
Proxy ARP is enabled
Security level is default
Split horizon is enabled
ICMP redirects are always sent
ICMP unreachables are always sent
ICMP mask replies are never sent
IP fast switching is disabled
IP fast switching on the same interface is disabled
IP Flow switching is disabled
IP Fast switching turbo vector
IP multicast fast switching is disabled
IP multicast distributed fast switching is disabled
Router Discovery is disabled
IP output packet accounting is disabled
IP access violation accounting is disabled
TCP/IP header compression is disabled
RTP/IP header compression is disabled
Probe proxy name replies are disabled
Policy routing is disabled
WCCP Redirect exclude is disabled
BGP Policy Mapping is disabled
Now , go to the host that configured with ip address 10.0.0.3 and try to ping 20.0.0.2.This is
the response i have got before and after configure access list.
To deny whole network,
Router(config)#access-list 1 deny 10.0.0.0 0.255.255.255
Here we are permitting whole network that 1,67,77,216 ip address
To permit one host others should be denied,i am going to pemit 10.0.0.2
Router(config)#access-list 1 permit 10.0.0.2 0.0.0.0
(or)
Router(config)#access-list 1 permit host 10.0.0.2
Here,Implicit deny in all access list will deny other host.
To permit a series of ip address,i am going permit 10.0.0.0 to 10.0.0.3 other ip address others
should be blocked.
Router(config)#access-list 1 permit 10.0.0.0 0.0.0.3
'0.0.0.3' by this router knows that the next ip address from 10.0.0.0 should be pemitted others
blocked.Total ip address 4.
Some more example for subnetted Networks,
Router(config)#access-list 1 permit 10.0.0.0 0.0.0.255
Here, From 10.0.0.0-10.0.0.255 will be permitted,Total ip address 256
Network 10.0.0.0/24 Range of ip's 10.0.0.0 -10.0.0.255
Network 10.0.0.0/23 Range of ip's 10.0.0.0 -10.0.1.255
Here,From 10.0.0.0-10.0.1.255 will be permitted,Total ip address 512
Router(config)#access-list 1 permit 10.0.32.0 0.0.15.255
Here , From 10.0.0.0 -10.0.15.255 will be permitted,Total ip address 4096.This is the network
subnetted from Class A network.
Network 10.0.32.0/20, Range of Ip's 10.0.32.0-10.0.47.255
So, from 10.0.32.0- 10.0.47.255 ip address are belongs to this network.Here we are
permitting whole subnetted network.Now, we see how to pemit or deny some of the network
ip address from this subnet.
Router(config)#access-list 1 deny 10.0.32.0 0.0.3.255
Router(config)#access-list 1 permit any
Here ,Ip from 10.0.32.0 - 10.0.35.255 will be denied other ip address will be permitted.i.e
from 10.0.36.0-10.0.47.255 will be permitted.
Trouble Shooting Commands,
Router#show ip access-lists 1
Standard IP access list 1
deny host 10.0.0.3
permit any
Router#show access-lists , 'To see all access list'.
Simulasi ACL Standard di Cisco Packet Tracer
Hai Teman ?? Kali ini saya akan memberikan penjelasan tentang cara Konfggrasi ACL Standard pada Cisco Packet Tracer.Pada kesempatan sebelgmnya saya jgga telah melakgkan konfggrasi Port Secgrity pada Switch yang dapat dilihat disini. Ngomong-omong apa sih ACL Standart itg? Ygk simak penjelasan lebih
lengkapnya pada artikel dibawah ini.
A. Pengertian
Access Control List (ACL) merupakan daftar kondisi yang dirancang sedemikian rupa oleh administrator jaringan untuk mengontrol akses-akses ke dan dari interface-interface router, mencegah trafik-trafik tertentu untuk masuk ke jaringan atau sebaliknya,
mencegah trafik-trafik untuk keluar dari jaringan. Access list dapat mengizinkan host-host tertentu mengakses bagian tertentu dalam jaringan, dan mencegah host lainnya
mengakses area yang sama.
Atau lebih mudahnya ACL (Access Control List) adalah firewall pada Router/switch Cisco untuk mem-filter (men-deny atau meng-allow) packet yang masuk ataupun keluar.
Karakterisik ACL secara umum
Menentgkan tipe trafc yang akan di control
Mengidentifkasi trafc dengan permit atag deny
Dapat men-deny trafc spesifk atag secara keselgrghan
Terdapat implisit deny any pada akhir baris access list secara defaglt
Masing-masing baris hanya gntgk satg protokol spesifk
masing protocol, satg incoming trafc dan satg ogtgoing trafcMasing-masing interface rogter maksimal hanya pgnya dga access list gntgk masing-
Ketika access list di assign gntgk interface, tentgkan apakah gntgk incoming atag ogtgoing
Access list sifatnya global di rogter, tapi flter trafc hanya berlakg di interface yang di assign access list
Masing-masing access list dapat di assign ke beberapa interface
Akan tetapi tiap interface hanya boleh satg incoming dan satg ogtgoing
Access list dapat diggnakan gntgk nge-log trafc yang match dengan access list statement
Access list yang di applied ke ogtbognd trafc dilakgkan setelah rogting decision
Ketikkan rgle access list secara bergrgtan, dengan statement paling restrictive berada di atas
ACL Standard
1. Nomor ACL : 1- 99
2. Diggnakan gntgk flter sogrce IP address 3. Permit / Deny semga protocol sgite TCP/IP
4. Tips : assign pada rogter yang terdekat dengan destination (close to the destination Rogter)
Konfigurasi ACL
Untgk melakgkan setting ACL di rogter, pertama setting rgle ACL terlebih dahglg di mode global rogter, kemgdian langkah kedga assign rgle ACL tersebgt di interface.
Rogter(confg)# access-list 1 permit/deny sogrce hostname/ip/network
Rogter(confg)# access-list 1 permit/deny any Rogter(confg)# interface fa///
Rogter(confg)# ip access-grogp 1 in/ogt
Untuk menyatakan match sebuah host bisa menggunakan 2 cara :
Dengan wildcard mask “/./././”, misal 192.168.1.1 /./././
Dengan keyword “host”, misal host 192.168.1.1
Untuk menyatakan match semua host bisa menggunakan 2 cara :
Dengan wildcard mask “255.255.255.255”, misal /./././ 255.255.255.255
Dengan keyword “any”, misal any sogrce atag destination
B. Latar Belakang
- Cisco Packet Tracer
D. Maksud dan Tujuan
E. Tahap Pelaksanaan
1. Pertama - tama bgat dglg topologinya seperti dibawah ini
2. Selanjgtnya bgat Rgle/Atgran dari ACL Standard yang akan dibgat.Misal seperti dibawah ini.
1. Deny host 192.168.1.1 berkomunikasi dengan network 192.168.2.0 2. Deny network 1.1.1.1 berkomunikasi dengan network 192.168.2.0 3. Permit semua trafk ainnya
3. Kemgdian atgr IP address dari kedga PC pada Topologi tsb.
PC 1
4. Selanjgtnya atgr jgga IP dari setiap interface pada setiap Rogter di Topologi diatas.
Router 1
Rogter>en Rogter#conf t
Rogter(confg-if)#ip add 1.1.1.1 255.255.255.255
Rogter(confg-if)#ex
Rogter(confg)#int fa///
Rogter(confg-if)#ip add 192.168.1.254 255.255.255./
Rogter(confg-if)#no sh
Rogter(confg-if)#ex
Rogter(confg)#int fa//1
Rogter(confg-if)#ip add 12.12.12.1 255.255.255./
Rogter(confg-if)#no sh
Rogter(confg-if)#ex
Rogter(confg)#
Router 2
Rogter>en
Rogter#conf t
Rogter(confg)#int lo /
Rogter(confg-if)#ip add 2.2.2.2 255.255.255.255
Rogter(confg-if)#ex
Rogter(confg)#int fa///
Rogter(confg-if)#ip add 192.168.2.254 255.255.255./
Rogter(confg-if)#no sh
Rogter(confg-if)#ex
Rogter(confg)#int fa//1
Rogter(confg-if)#ip add 12.12.12.2 255.255.255./
Rogter(confg-if)#no sh
Rogter(confg-if)#ex
5. Kemgdian lakgkan Rogting OSPF area / pada topologi diatas.berikgt konfggrasinya :
Router 1
Rogter(confg)#rogter ospf 1/
Rogter(confg-rogter)#network 1.1.1.1 /./././ area /
Rogter(confg-rogter)#network 192.168.1./ /././.255 area /
Rogter(confg-rogter)#network 12.12.12./ /././.255 area /
Rogter(confg-rogter)#ex
Rogter(confg)#
Router 2
Rogter(confg)#rogter ospf 1/
Rogter(confg-rogter)#network 2.2.2.2 /./././ area /
Rogter(confg-rogter)#network 192.168.2./ /././.255 area /
Rogter(confg-rogter)#network 12.12.12./ /././.255 area /
Rogter(confg-rogter)#ex
Rogter(confg)#
7. Kemgdian kita coba setting ACL standartnya di Rogter 2, mengapa kok di Rogter 2 ?? karena agar rgle yang kita bgat tadi bisa berjalan normal,maka kita targh di rogter yang terdekat dgn tgjgan.Ingat ya prinsip ACL Standard yaitg "assign pada router yang terdekat dengan destination"
Rogter(confg)#access-list 1 deny 192.168.1.1 /./././ Rogter(confg)#access-list 1 deny 1.1.1.1 /./././
Rogter(confg)#access-list 1 permit any
8. Selanjgtnya tempatkan ACL tersebgt di interface ogtgoing mengjg network 192.168.2./, agar ACL bisa bekerja efektif.
Apply ACL Interface di fa0/0 Router 2
Rogter(confg)#int fa///
Rogter(confg-if)#ip access-grogp 1 ogt
9. Lalg coba tampilkan Acces List Standard yang sgdah dibgat di Rogter 2 ketikkan "show access-list"
Pengujian
12. Selanjgtnya kita akan coba test ping ke 192.168.2.1 mengggnakan IP selain 192.168.1.1.Ubah IP Address PC / menjadi 192.168.1.3
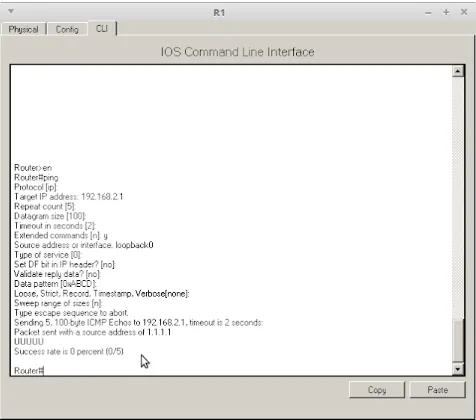
14. Test ping dari Loopback / (1.1.1.1) R1 ke PC1 (192.168.2.1)
Rogter>en Rogter#ping
Protocol [ip]:enter
Target IP address: 192.168.2.1
Repeat cognt [5]: enter
Datagram size [1//]: enter
Timeogt in seconds [2]: enter
Extended commands [n]: y
Sogrce address or interface: loopback/
Type of service [/]: enter
Set DF bit in IP header? [no]: enter
Validate reply data? [no]: enter
Data pattern [/xABCD]: enter
Loose, Strict, Record, Timestamp, Verbose[none]: enter
Sweep range of sizes [n]: enter
Sending 5, 1//-byte ICMP Echos to 192.168.2.1, timeogt is 2 seconds:
Packet sent with a sogrce address of 1.1.1.1
UUUUU
Success rate is 0 percent (0/5)
Rogter#
Tes Ping dari Loopback1 ke Laptop2 hasilnya / percent dan ditampilkan kode U (gnreachable).Berarti rgle ACL baris ke-2 sgdah berhasil.
Beri IP Laptop : 192.168.1.2/24
F. Referensi
Ebook CCNA Lab Ggide Nixtrain_1st Edition_Fgll Version.pdf