MADIS SARALITA – 5112100038 Keamanan Informasi dan Jaringan (C)
PART 2 : ASYMMETRIC
CIPHERS
CHAPTER 8
INTRODUCTION TO NUMBER THEORY
CHAPTER 9
PUBLIC-KEY CRYPTOGRAPHY AND RSA
CHAPTER 10
CHAPTER 8
INTRODUCTION TO NUMBER THEORY
8.1 PRIME NUMBERS
A natural number (1, 2, 3, 4, 5, 6, etc) is called a prime number (or a prime) if it has exactly two positive divisors, 1 and the number itself. Prime numbers are curiously used in this chapter.
p = set of all prime
a = positive integer
While j ≤ n, so pn can be only divided by an integer which is less or equal fro the power of the same prime number, so we can write
To determine greatest common divisor of two positive integers, we can use
8.2 FERMAT’S AND EULER’S THEOREMS
Fermat’s Theorem
p = prime
a = positive integer than can not be divided by p
There is also an alternative formulae, the different is on a varibale.
p = prime
a = positive integer
Euler’s Totient Function
Written by Φ(n)
Is postive integers that less than n and relatively prime to n
Φ(1) = 1
where p ≠ q and n = pq
So, we can conclude that
Euler’s Theorem
Where a and n are relatively prime.
There is also an alternative formulae. This form does not require a be relatively prime to n.
8.3 TESTING FOR PRIMALITY
We need to select one or more large random prime numbers in cryptographic algorithms.
We nedd many references of algorithm for finding primes, that are :
Miller-Rabin Algorithm
We express any positive odd integer by this form
Where n ≥ 3, k > 0 and q is odd.
Two properties of prime numbers
1. If p is prime and a is positive integer less than p, then a2mod p = 1 if and only if either a mod
p = 1 or a mod p = -1 mod p = p – 1.
2. If p be a prime number more than 2, so p – 1 = 2kq with k > 0 and q is odd. And then if 1 < a <
p – 1, so one of the two following conditions is true.
A Deterministic Primality Algorithm
This algorithm known as AKS algorithm.
The algorithm determines whether a number is prime or composite within polynomial time.
Distribution of Primes
Prime number theorem, the primes near n are spaced on the average one every (ln n) integers.
Describes the asymptotic distribution of the prime numbers among the positive integers.
8.4 THE CHINESE REMA INDER THEOREM
Known as CRT, possible to retrieve integeres in certain range from thats residues modulo a set of pairwise relatively prime moduli.
mi = pairwise relatively prime
gcd(mi, mj) = 1 for 1 ≤ i, j ≤ k, and i ≠ j
A is any integer in ZM, so we can use this correspondence
In first assertion. Then let
And compute
The Powers of an Integer, Modulo n
From , we hold several ways that are :
Order of a(mod n)
Exponent which a belongs mod n
If a is primitive roots of n, then its powers
Else if a is primitive roots of p, then its powers
Logarithms for Modular Arithmetic
The inverse of exponentiation is logarithm function.
Some properties of logarithms
We also know that
We must not this following
With eular’s theorem
So we have
And then generalize
Calculation of Discrete Logarithms
y, g , and p in general is very difficult to calculate x, so we must find algorithm to take discrete algorithms modulo a prime number fastly which is not wortly for large primes with
SOURCE
W. Stallings, Cryptography And Network Security Principles And Practice Fifth Edition, New York: Prentice Hall, 2011.
http://en.wikipedia.org/wiki/AKS_primality_test diakses pada 5 April 2015
http://en.wikipedia.org/wiki/Prime_number diakses pada 5 April 2015
CHAPTER 9
PUBLIC-KEY CRYPTOGRAPHY AND RSA
9.1 PRINCIPLES OF PUBLIC-KEY CRYPTOSYSTEMS
Public-key cryptography, also known as asymmetric cryptography.
In symmetric encryption, key distribution need : o A key sharing from two communcications.
o Use of key distribution center.
An important element to the public key system is that the public and private keys are related in such a way that only the public key can be used to encrypt messages and only the corresponding private key can be used to decrypt them.
Public-Key Cryptosystems
Asymmetric algorithms hold on one key for encryption.
For decryption, asymmetric algorithms use a different key but still related.
Characteristics of the algorithm is infieasible to determine decription and encryption key.
Plaintext, data that can be read which is used as input in the algorithms.
Encryption algorithms, present various transformation on the plaintext.
Public and private key, a pair key which is used for encryption and decryption.
Ciphertext, output of the algorithms that contains of scrambled message.
Decryption algorithm, accept the ciphertext and match it to produce the plaintext.
Using algorithms that requires two separate keys, secret (or private) and public.
The public key is used, for example, to encrypt plaintext or to verify a digital signature.
The private key is used for the opposite operation, in these examples to decrypt ciphertext or to create a digital signature.
Convemtional key cryptography involves 2 people using the same private key to both encrypt and decrypt information. Public key cryptography, on the other hand, is where 2 different keys are used a public key for encryption and a private key for decryption.
Applications for Public-Key Cryptosystems
The sender uses it’s private key or receiver’s public key or both to present type of cryptographic function.
Three categories to clasifiy the use of cryptographic function :
o Encryption/decryption, sender uses receipent’s public key to encrypt the message.
o Digital signature, sender signs a message with it’s private key.
o Key exchange, exchange a session key from collaborate of two sides.
Requirements for Public-Key Cryptography
To calculate the inverse, we must match the condition, is that easy or infeasible.
Trap-door one-way function, can be easily to calculate in one direction and will be infeasible tp calculate in the pther direction unless know additional information.
Trap-door one-way function, we can calculate
Public-Key Cryptanalysis
A public key encryption is weak, so it can be atacked by brute force.
Public key systems depend on the use of invertible mathematical function.
To make brute-force attack, the key size must be large.
Public key encryption is limit in key management and signature applications.
With using some random bits, the attack can be aborted.
9.2 THE RSA ALGORITH M
The RSA scheme is a block cipher whic the plaintext and ciphertext contains of integers between 0 and n-1.
Description of the Algorithm
RSA is one of the first practical public-key cryptosystems and is widely used for secure data transmission.
The encryption key is public and differs from the decryption key which is kept secret.
For encryption and decryption
Where M is plaintext and C is ciphertext. And then we must find the relation of this form
Which relation between e and d expressed as
This is the process of RSA in multiple blocks
Computational Aspects
Exponentiation In Modular Arithmetic
In RSA, both of encryption and decryption need to raise an integer by mod n.
We can use this form
Efficient Operation Using The Public Key
A specific choice of e is usually made to speed up the operation of the RSA algorithm by using public key.
But, it will be simple to attack if the public key is very small.
To confuse the attack, we can abort by adding a unique pseudorandom bit string as padding to each instance of M to be encrypted.
Efficient Operation Using The Private Key
To speed up computation using CRT, we useKey Generation
Before the application of public key cryptosyste, a pair of keys must be generated.
o Determine two prime number, p and q.
o Select either e or d and calculate the other.
o
The Security of RSA
Kind of attacs that is possible happen :
Brute force
o Try all possible private keys.
Mathematical attacks
o Use several approaches by factoring the product of two primes.
Timing attacks
o Depend on running time of decryption algorithm.
o There are simple countermeasure that can be used : Constant exponention time
Random delay Blinding
Chosen ciphertext attacks
o Exploit properties of the RSA algorithm.
o Recommed to modify the plaintext using optimal asymmetric encryption padding (OAEP).
SOURCE
W. Stallings, Cryptography And Network Security Principles And Practice Fifth Edition, New York: Prentice Hall, 2011.
http://en.wikipedia.org/wiki/Public-key_cryptography diakses pada 6 April 2015
http://www.webopedia.com/TERM/P/public_key_cryptography.html diakses pada 6 April 2015
CHAPTER 10
OTHER PUBLIC-KEY CRYPTOSYSTEMS
10.1 DIFFIE-HELLMAN KEY EXCHANGE
Enable two users exchange a key securely.
Limited to the exchange of secret values.
Depend for the effectiveness on the difficulty of computing discrete logarithms.
The Algorithm
By the rules of modular arithmetic, we caculate key as K below
This algorithm run by this task
Initialization global public elements
Select user A ley generation
Select user B ley generation
Calculate secret key by user A
Calculate secret key by user B
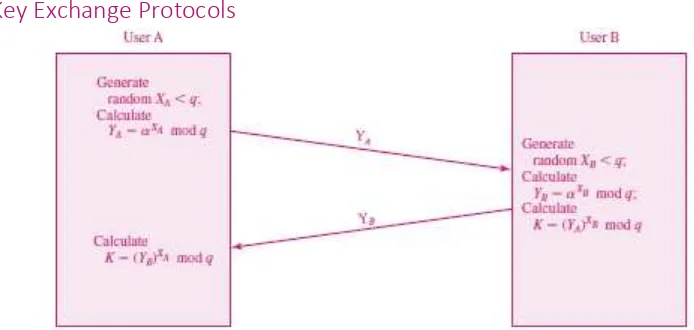
Key Exchange Protocols
Figure above show the calculation of Diffie-Hellman
Man-in-the-Middle Attack
Suppose Alice wishes to communicate with Bob. Meanwhile, Mallory wishes to intercept the conversation to eavesdrop and possibly (although this step is unnecessary) deliver a false message to Bob.
Alice, believing this public key to be Bob's, encrypts her message with Mallory's key and sends the enciphered message back to Bob. Mallory again intercepts, deciphers the message using her private key, possibly alters it if she wants, and re-enciphers it using the public key Bob originally sent to Alice. When Bob receives the newly enciphered message, he believes it came from Alice.
1. Alice sends a message to Bob, which is intercepted by Mallory:
Alice"Hi Bob, it's Alice. Give me your key"--> Mallory Bob
2. Mallory relays this message to Bob; Bob cannot tell it is not really from Alice:
Alice Mallory"Hi Bob, it's Alice. Give me your key"--> Bob
3. Bob responds with his encryption key:
Alice Mallory <--[Bob's_key]Bob
4. Mallory replaces Bob's key with her own, and relays this to Alice, claiming that it is Bob's key:
Alice <--[Mallory's_key]Mallory Bob
5. Alice encrypts a message with what she believes to be Bob's key, thinking that only Bob can read it:
Alice"Meet me at the bus stop!"[encrypted with Mallory's key]--> Mallory Bob
6. However, because it was actually encrypted with Mallory's key, Mallory can decrypt it, read it, modify it (if desired), re-encrypt with Bob's key, and forward it to Bob:
Alice Mallory"Meet me in the windowless van on 22nd Ave!"[encrypted with Bob's key]-->
Bob
7. Bob thinks that this message is a secure communication from Alice.
10.2 ELGAMAL CRYPTOGRAPHIC SYSTEM
ElGamal encryption system is an asymmetric key encryption algorithm for public-key cryptography which is based on the Diffie–Hellman key exchange.
Key generation
The key generator works as follows:
o Alice generates an efficient description of a cyclic group G, of order q, with generator g,. See below for a discussion on the required properties of this group.
o Alice chooses a random x, from {1, . . . , q-1}. o Alice computes h = gx
Encryption
The encryption algorithm works as follows: to encrypt a message m, to Alice under her public key (G,q,g,h),
o Bob chooses a random y, from {1, . . . , q-1}, then calculates c1 = gy
Bob calculates the shared secret s=hy,.
Bob converts his secret message m, into an element m' of G.
Bob calculates c2=m' . s
Bob sends the ciphertext (c1,c2)=(gy, m' . hy)=(gy, m' . (gx)y), to Alice.
Decryption
The decryption algorithm works as follows: to decrypt a ciphertext (c1,c2) with her private key
x,
o Alice calculates the shared secret s=c1x
o and then computes m'=c2 . s-1 which she then converts back into the plaintext message m,
where s-1 is the inverse of s in the group G. (E.g. modular multiplicative inverse if G is a
subgroup of a multiplicative group of integers modulo n). The decryption algorithm produces the intended message, since
10.3 ELLIPTIC CURVE ARITHMETIC
Abelian Groups
An abelian group denoted by {G,*}
Is a set of elements with a binary operation, denoted by *
Associates to each ordered pair (a,b) of elements in G an element (a * b) in G.
An elliptic curve is defined by an equation in two variables with coefficient.
That’s coefficient result in the definition of a fine abelian group.
Elliptic Curves over Real Numbers
Weierstrass equation
For our purpose, we use
In geometric description of addition, there are a condition that
In algebraic description of addition, we calculate
Elliptic Curves over Zp
Make use of elliptic curves which is the variables and coefficients are restricted to elements of a finite field.
For a prime curve, we use a cubic equation which the variables and coefficients set from 0 until p-1.
For binary curve, variables and coefficient take from values in GF(2m)
Elliptic Curves over
A finite field GF(2m) consists of 2m elements.
The form
10.4 ELLIPTIC CURVE CRYPTOGRAPHY
Analog of Diffie-Hellman Key Exchange
The order n of a point G on elliptic curve is the smallest positive integer n such that nG = 0 and G are parameters of the cryptosystem known.
ECC Diffie-Hellman Key Exchange
Elliptic Curve Encryption/Decryption
To encrypt and send message, we use
Security of Elliptic Curve Cryptography
Security of ECC depends on difficultness when determine k given kP and P.
The fastest technique to take elliptic curve logarithm is Pollard rho method.
Comparable key size
10.5 PSEUDORANDOM NUMBER GENERATION BASED ON AN ASYMMETRIC CIPHER
PRNG Based on RSA
RSA algorithm is secure and good candidate to form the basis of PRNG.
Ilustration of PRNG
Defining PRNG o Setup
Select standard RSA setup selection. o Seed
Select a random seed x0 of bitlength r.
o Generate
Generate a pseudorandom sequence of length k x m. o Output
The output sequence is Z1 || Z2 || . . . || Zm
PRNG Based on Elliptic Curve Cryptography
Defining PRNG
o Let P and Q be known points on a given elliptic curve.
o The seed is a random integer where not same E(GF)p)
o Let x denote a function that gives x-xoordinate of a point of the curve.
o Let lsbi(s) denote i least significant bits of an integer s.
In security, PRNG use in a system that already implements ECC.
But, that’s system does not implement any other symmetric, asymmetric, or hash cryptographic algorithm.
SOURCE
W. Stallings, Cryptography And Network Security Principles And Practice Fifth Edition, New York: Prentice Hall, 2011.
http://en.wikipedia.org/wiki/Man-in-the-middle_attack diakses pada 6 April 2015
http://en.wikipedia.org/wiki/ElGamal_encryption diakses pada 6 April 2015
http://en.wikipedia.org/wiki/Elliptic_curve diakses pada 6 April 2015