Full Terms & Conditions of access and use can be found at
http://www.tandfonline.com/action/journalInformation?journalCode=vjeb20
Download by: [Universitas Maritim Raja Ali Haji], [UNIVERSITAS MARITIM RAJA ALI HAJI Date: 12 January 2016, At: 17:49
Journal of Education for Business
ISSN: 0883-2323 (Print) (Online) Journal homepage: http://www.tandfonline.com/loi/vjeb20
Computer Security in the Introductory Business
Information Systems Course: An Exploratory Study
of Textbook Coverage
Kenneth J. Sousa , Laurie E. MacDonald & Kenneth T. Fougere
To cite this article: Kenneth J. Sousa , Laurie E. MacDonald & Kenneth T. Fougere (2005) Computer Security in the Introductory Business Information Systems Course: An Exploratory Study of Textbook Coverage, Journal of Education for Business, 81:1, 15-20, DOI: 10.3200/ JOEB.81.1.15-20
To link to this article: http://dx.doi.org/10.3200/JOEB.81.1.15-20
Published online: 07 Aug 2010.
Submit your article to this journal
Article views: 19
View related articles
ABSTRACT. The authors conducted
an evaluation of Management
Informa-tion Systems (MIS) textbooks and
found that computer security receives
very little in-depth coverage. The
text-books provide, at best, superficial
treat-ment of security issues. The research
results suggest that MIS faculty need to
provide material to supplement the
textbook to provide adequate coverage
of this important and timely issue.
here is no question that computer security is a major issue. Accord-ing to Leyden (2004), Microsoft’s Bill Gates has called security the greatest challenge ever faced by the computer industry. The spread of the SoBig.F virus via e-mail is one example of the extent of the security problem. SoBig.F spread like wildfire. America Online reported it had blocked 23.2 million copies of this worm, and the e-mail security company Postini quarantined 3.5 million copies (Warner & Abreu, 2003). The British Internet security firm MessageLabs, estimated that 1 out of every 17 e-mails sent around the world was infected by the SoBig.F virus.
The importance of computer security has grown in tandem with the importance of computer systems in all aspects of business. The Internet has provided the basis for the implementation of innova-tive business applications, such as elec-tronic commerce, elecelec-tronic data inter-change, and interorganizational systems. These major changes to the information technology infrastructure have produced new security challenges not found in early information systems. Security was focused traditionally on employees and internal safeguards. System administra-tors must now be concerned with outside threats that may come via the Internet. Their customers and clients are also experiencing these new challenges and are more concerned about the possibility
of hackers gaining access to information than with how private companies and government agencies use this informa-tion (Wellner, 2000).
The Federal Trade Commission reported that Internet-related consumer fraud amounted to $200 million in 2003 and accounted for 55% of all fraud reports (2004 National and State Trends). The Computer Security Insti-tute (CSI, 2003) found that 74% of cor-porations and government agencies responding to a survey reported a secu-rity breach within the past 12 months. A survey conducted by the American Institute of Certified Public Accoun-tants found that information security (IS) was the number one concern among respondents (Kepczyk, 2003). Security threats have been on the increase and the growth is expected to continue (Cyber crime, 2003; Radcliff, 2002).
Security Issues Trends
Several surveys relating to industry security issues and perceptions all con-clude that this topic remains important within organizational and information technology priorities. More than half of the respondents to an InfoWorld survey expressed concern about potential breaches in security; virus attacks illus-trated the highest degree of concern at 73% (Connolly, 2001).
Computer Security in the Introductory
Business Information Systems Course: An
Exploratory Study of Textbook Coverage
KENNETH J. SOUSA LAURIE E. MACDONALD KENNETH T. FOUGERE BRYANT UNIVERSITY
SMITHFIELD, RHODE ISLAND
T
The CSI and the InfoWorld studies confirm that cyber-crime and security incidents continue to be an issue in information technology management. External hacking is considered a serious cause for concern by organizations (Connolly, 2001; Harreld, 2001). A sig-nificant number of organizations have detected a variety of security violations originating from outside the organiza-tion. These violations can include denial of service attacks, system penetration, Web site vandalism, and theft of propri-etary information (CSI, 2003; Connolly; Harreld). Internet connections are the source of an increasing number of attacks as compared with remote dial-in and internal systems. In 2003, 78% of respondents reported the Internet as the source of attack, up from 57% in 1999 (CSI, 2003). The growth in the use of Web-based systems has led to a consis-tent increase in denial of service attacks, from 27% in 2000 to 42% in 2003 (CSI; Harreld). Of the organizations reporting a Web-based system attack, 32% report-ed at least five incidents in the past year (CSI). Most of these incidents are either vandalism or denial of service.
Each of the surveys also reported an increase in the number of internal securi-ty breaches, such as unauthorized use of technology resources by employees, lap-top theft, and insider abuse of network access. The CSI 2003 survey also identi-fied a number of potential vulnerabilities. The two most likely sources of attack are independent hackers and disgruntled employees, cited by 82% and 77% of respondents, respectively (CSI, 2003). Security attacks committed by insiders and employees are coincidently consis-tent with the abuse of network access.
Problem Statement
A recent study concluded that securi-ty issues are not sufficiently covered in Information Systems (IS) curricula (Anderson & Schwager, 2002). The results of the study also concluded that security issues are of enough impor-tance to justify their inclusion in all IS courses.
With this in mind, we decided to undertake a comprehensive review of introductory Management Information Systems (MIS) textbooks to examine
and measure the degree of coverage of security. The evaluation of MIS text-books was used to assess the depth in which a typical MIS course addresses the issue of computer security. The text-book is typically the central organizing component for the course with both pro-fessors and students relying on the text-book to a large extent.
METHOD Keywords
Our objective of this research was to determine the depth of coverage relating to IS topics in introductory MIS text-books. To provide a framework for this objective, we developed a set of key-words to identify security issues. We developed the keyword list after review-ing security textbooks (Erbschloe, 2003; Holden, 2004; Volonino & Robin-son, 2004; Whitman & Mattford, 2004) and Web sites devoted to computer security (Develop a Computer, 2003; Introduction, 2003; ISO, 2003). Using keywords to study the textbooks
allowed us to include the variety of ter-minology used to describe these issues. To facilitate the analysis of the text-book coverage, we needed to develop a structure for the keyword concepts. Therefore, we grouped the keywords into four categories to regularize the data. The keyword categories, as shown in Table 1, are: (a) Security Threats, (b) Risk Management, (c) Security Educa-tion, and (d) Security Technology. For example, spoofing, viruses, and worms are categorized under the common rubric of security threats.
Textbook Analysis
We collected a sample of MIS text-books that are commonly used in an introductory MIS course. The textbook selection was based on the recommenda-tions of 11 MIS instructors (5 full pro-fessors, 4 associate propro-fessors, and 2 assistant professors) whom we asked to provide a list of the MIS textbooks they had used or reviewed recently. These textbooks, as shown in Appendix A, are representative of those textbooks found
TABLE 1. Keyword Categories
Category Definition
Security Threats Hacking Denial of Service Malicious Code Incident Response Team Security Planning
A person, group, or entity that poses an ongoing danger to one or more information assets (Holden, 2004; Whitman & Mattford, 2004).
Identify security threats and act to eliminate or at least minimize the impact on your information assets (Erbschloe, 2003; Introduction to risk analy-sis, 2003; ISO, 2003).
Ensure that staff members understand the need for security and are prepared to make security an inte-gral part of the job (Volonino & Robinson, 2004; Whitman & Mattford, 2004).
Technology designed to guard against threats to information assets (Develop a computer deploy-ment plan, 2003; Erbschloe, 2003; Holden, 2004).
in an introductory MIS course. The text-book list used for this research included the most popular textbooks as of November 2004 (M. P. Martin, personal communication, November 23, 2004): Laudon, Haaf, Stair/Reynolds, O’Brien, Jessup/Valaich, Turban, McLeod, Post, and Oz. The presentation of the list, as provided by the publishing representa-tive, does not indicate any ranking of these authors. It is simply a list of the most popular adoptions. We used each of these books in the textbook evaluation sample.
We based the textbook analysis methodology on the technique employed by MacDonald and Fougere (2003). Our analysis team was composed of three Computer Information Systems (CIS) faculty, who were also the authors of this study: (a) a full professor with 20 years of industry experience and 22 years of teaching CIS, (b) a full professor with 17 years of industry experience and 23 years of teaching CIS, and (c) an assis-tant professor with 15 years of industry experience and 10 years of teaching CIS. One member of the analysis team also taught a graduate-level security course.
Data Collection and Analysis
We developed a data collection form that included the keywords and cate-gories as previously defined. We docu-mented the evaluation procedure and each member had a copy along with a form for each of the textbooks to record our evaluation. Each of the authors con-ducted an independent analysis of the textbooks using the following steps
1. Table of Contents (TOC). Identify each term that is included in the table of contents. Note each keyword identified in the TOC on the data collection form with a “Y.”
2. Index. Identify each term that is included in the index. As each instance of the keyword is identified, log the page references on the data collection form in the respective column.
3. Quality of Coverage.Read the text-book material presented for each key-word and conduct a heuristic evaluation of the quality of the coverage provided for the concept. Assign an evaluation of the quality of the coverage.
We began the analysis of the text-books by examining the table of con-tents for citations of security topics. When a textbook included significant coverage of any issue, that issue would have appeared as chapter or section headings in the TOC (K. S. Bachrach, personal communication, November 3, 2003). The next step involved reviewing the index of each textbook. A book’s index will direct a reader of the book to subjects that are discussed in the book (Columbia Encyclopedia, 2002). We recorded page numbers noted in the TOC and index for each textbook. Then, we read the textbook material content and assigned an evaluation rank using a 4-point, forced-choice Likert scale ( Lik-ert scaling, 2004). We did not read these sections searching for specific method-ologies to ensure computer security. Rather, they were evaluating the depth and quality of coverage that would pro-vide students with a sound introduction to the security issues. Significant cover-age of an issue will present material and concepts that will form the basis of class discussion and allow the instructor and students to build on the textbook mater-ial. Thus, an issue presented in-depth in a textbook will not be the final word but an important starting point for the learn-ing process. We were looklearn-ing for mate-rial that would make the importance of the topic clear to the students and offer a framework for building a sound secu-rity practice.
We summarized the unique page ref-erences recorded for each keyword by keyword category, eliminating the possi-bility of “double counting” a citation within the same category. We analyzed the data to determine the mean page count devoted to each keyword category, whether or not a category was cited in the index, and whether a category was cited in the TOC. The result of this analysis provided the foundation for the research findings and conclusions.
RESULTS
Keyword Citations
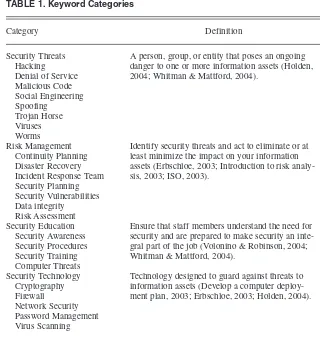
We compiled an analysis of the TOC for each category to show the percentage of books with a citation. As illustrated in Figure 1, we identified each of the secu-rity categories in at least half of the text-books reviewed. The Security Technolo-gy category, at 70%, received the most significant coverage in the TOC of the textbook population. Each of the remain-ing categories received a lower coverage: Security Education (50%), Risk Manage-ment (60%), and Security Threats (55%). The TOC analysis provided a limited, binary indication of the coverage in the conceptual issue. To determine the depth of coverage, we needed to com-plete an analysis of the frequency of index citations as well as a quantitative measure of citation depth. Therefore, we analyzed the data to determine the
Security Technology
Security Education
Risk Management
Security Threats
0% 10% 20% 30% 40% 50% 60% 70% 80%
FIGURE 1. Table of contents citations.
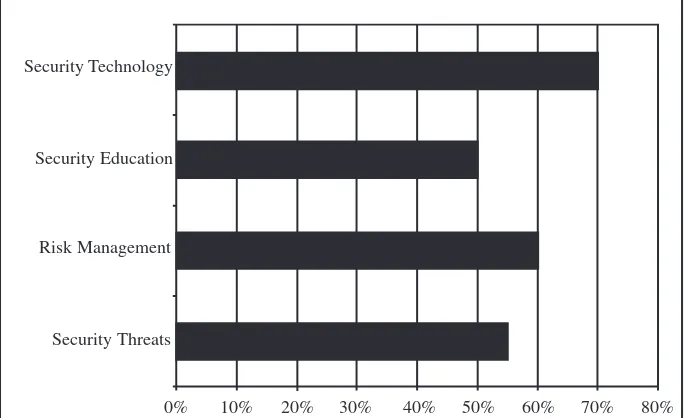
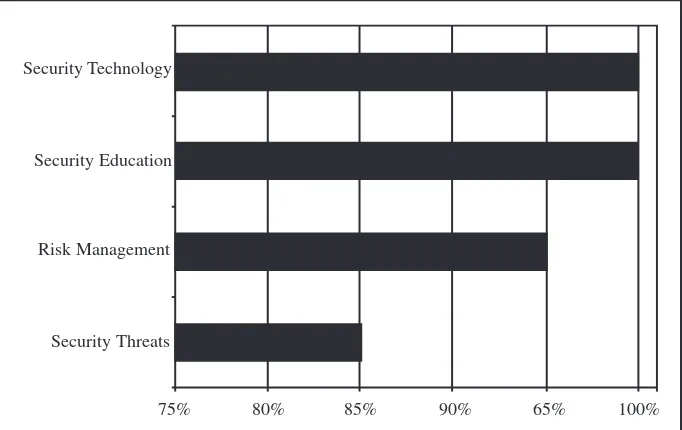
frequency of index citations. The results of this analysis, as shown in Figure 2, indicated that each of the categories was cited significantly in the textbook popu-lation. The categories of Security Tech-nology and Security Education were each cited in 100% of the textbooks. We found Risk Management in 95% of the textbooks, and the Security Threat cate-gory appeared in 85% of the textbooks. We compiled the data recorded for the mean page counts by keyword category in Figure 3. The category resulting in the most significant coverage was Security Technology (9.6 pages). The remaining three categories illustrated a variety of page coverage: Security Threats (7.4 pages), Security Education (6.8 pages), and Risk Management (5.2 pages).
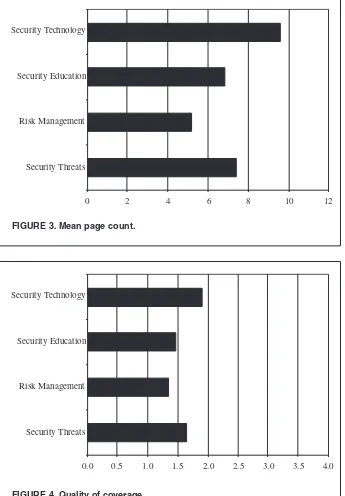
Figure 4 shows the results for the eval-uation of the depth and quality of cover-age. A score of 1 indicates minimal cov-erage and a score of 4 indicates comprehensive coverage of a security topic. Figure 4 reveals that the coverage for all keyword groups was below 4. Security Technology earned the highest score (1.9) by a small margin. Risk Man-agement was the lowest (1.4), and Secu-rity Threats (1.6) and SecuSecu-rity Education (1.5) were only marginally higher.
The results of the data analysis showed limited coverage relating to the four categories associated with informa-tion security topics. The textbook treat-ment did not provide sufficient depth to
provide a solid and appropriate founda-tion in any of the four security cate-gories identified in this study.
DISCUSSION
Computer security has always been an important issue, and its importance will continue to grow as business and society in general become more depen-dent on computer systems. The high frequency of citations in the TOCs and indexes of the textbooks that we ana-lyzed demonstrates that security issues receive some level of coverage in most MIS textbooks. However, the lack of in-depth coverage, as shown by the small number of textbook pages devot-ed to security issues and the quality of conceptual coverage, indicate that information systems faculty must develop ways to teach students how to address computer security issues at all levels of the business enterprise. The nature of the threats relating to com-puter security evolves to correspond to the changes in technology. It may ulti-mately be impossible for authors and publishers to provide textbook materi-als that remain current with the evolv-ing security threats.
Suggested Supplemental Content
For classroom teaching, the results of this research may act as a teaching
aid for enhancing the coverage of security topics in the introductory MIS course. Source material, such as those shown in Appendix B, can be used to augment lectures and student projects. One example of a student assignment that has been used suc-cessfully by us is the Briefing Paper. For this assignment, students select an article from the current literature and make a presentation to the class to dis-cuss the salient points in the article. This is an effective way to get the stu-dents involved in reading the current literature as it addresses computer security issues. Student teams can be assigned to visit local resources such as: (a) power plants, (b) water supply facilities, (c) communication compa-nies, (d) transportation compacompa-nies, and (e) various business firms to study their policies and procedures for ensuring a secure computer environ-ment.
The Web sites shown in Appendix B provide a wide range of security topics. The contents of these sites allow the instructor to select a wide range of assignments.
CERT Web site
There are many security topics at the CERT®Web site, but the one that should be of particular interest to students, as most own their own computers, is one on home network security. This Web page has information on security, tech-nology, risks to home users, accidents and other risks, and actions that can be taken to protect one’s home computer system.
Internet Security Alliance
The Internet Security Alliance was created to provide a forum for informa-tion sharing and thought leadership on information security issues.
Disaster Recovery Site
The Disaster Recovery site is a fee-required site for certain archival infor-mation, but provides free access to its journal, the Disaster Recovery Jour-nal. The journal is dedicated to the field of disaster recovery in business and was the first publication of its Security Technology
Security Education
Risk Management
Security Threats
75% 80% 85% 90% 65% 100%
FIGURE 2. Index citations.
kind. There are currently over 60,000 subscribers.
ADDSecure Web Site
The ADDSecure.Net, Inc.’s Web site is a network security audit site. One of ADDSecure’s main functions is to review the integrity of corporate networks and servers, including Web and e-mail servers. There is free access to its journal, The Journal of Internet Security. Topics covered in the journal include networks,
Internet, and database; security, risk assessment and management; viruses, worms, and other malicious code; and mobile and satellite security.
Institute of Internal Auditors
The Institute of Internal Auditors (IIA) was formed in 1941. It serves as the global voice for the internal auditing profession. Its Web site provides inter-national standards for internal auditing as well as certification, research, and
educational products, through its IIA Research Foundation.
Stanford Research Institute
The Stanford Research Institute Web site is an independent, nonprofit research institute that conducts research and development for business, govern-ment, foundations, and other types of organizations. Among its many activi-ties are issues of security. Within that area, it conducts risk forums and com-puter security workshops. The informa-tion from its foundainforma-tion workshops is available at no charge.
SANS Institute
The SANS Institute (SysAdmin Audit Network Security) Web site is the largest source of information security training in the world. It also develops, maintains, and makes available at no cost the largest collection of research documents con-cerning various aspects of IS.
Some examples of student assign-ments, based on these Web sites are
1. Visit the CERT® Coordination Center site and prepare a report on secu-rity risks and prevention when installing a home computer.
2. Visit the Internet Security Alliance site and prepare a report that analyzes and forms conclusion about a particular forum topic on computer security.
3. Visit the Disaster Recovery site and prepare a report on terrorists’ attacks and their potential effects on businesses.
4. Visit the ADDSecure.Net, Inc. site and prepare a report on e-commerce security issues.
5. Visit the Institute of Internal Audi-tors site and prepare a report on internal auditing issues in Iraq.
6. Visit the Stanford Research Insti-tute site and prepare a report on risks to the public when using wireless systems. 7. Visit the SANS Institute site and prepare a report on security training.
Obviously, there are many Web sites that can be used when giving security assignments, but we feel those listed are among the leaders. Other Web sites can be used in concert with these assignments, which are somewhat gen-eral in the above examples, but can be Security Technology
Security Education
Risk Management
Security Threats
0 2 4 6 8 10 12
FIGURE 3. Mean page count.
Security Technology
Security Education
Risk Management
Security Threats
0.0 0.5 1.0 1.5 2.0 2.5 3.0 3.5 4.0
FIGURE 4. Quality of coverage.
refined by the instructors. The assign-ments can also be presented in class by students, synthesized by the instructor before becoming part of a general class discussion, or any variation thereof. The point is that learning is now active, not passive.
The fast-paced changes in technology require similar changes to the delivery of academic instruction in technology-based courses. The integration of tech-nology concepts, such as those described in this article, must be supplemented by materials and assignments that will expand the limited coverage in the text-books. The gap between the coverage of these topics and their importance can only be improved through the integration of these assignments. The expanded knowledge gained will provide a positive element to students as users of technolo-gy as well as future business employees in corporate organizations.
REFERENCES
2004 national and state trends in fraud & identity theft. Retrieved January 19, 2004, from http:// www.consumer.gov/sentinel/pubs/Top10Fraud 2003.pdf
Anderson, J. E., & Schwager, P. H. (2002). Secu-rity in the information systems curriculum: Identification and status of relevant issues.
Journal of Computer Information Systems, 42(3), 16-23.
The Columbia Encyclopedia. (6th ed.). (2002). New York: Columbia University Press. Computer Security Institute (2003). CSI/FBI
Computer Crime and Security Survey. San Francisco: Author.
Connolly, P. J. (2001, November 19). IT security outlook appears gloomy. InfoWorld, 23,48-49.
Cyber crime bleeds U.S. corporations, survey shows; financial losses from attacks climb for third year in a row (2003). Retrieved October 1, 2003, from http://www.gocsi.com/press/ 20020407.jhtml?_requestid=1091763
Develop a computer deployment plan that includes security issues (2003). Retrieved Sep-tember 10, 2003, from http://www.cert.org/ security-improvement/practices/p065.html Erbschloe, M. (2003). Guide to disaster recovery
(1st ed.). Boston: Course Technology. Harreld, H. (2001, March 26). Security: An
uneasy alliance. InfoWorld, 23, 42.
Holden, G. (2004). Guide to firewalls and network security: Intrusion detection and VPNs. Boston: Course Technology.
Introduction to risk analysis (2003). Retrieved September 10, 2003, from http://www.security-risk-analysis.com/introduction.htm
ISO 177799 directory (2003). Retrieved Septem-ber 10, 2003, from http://www.iso-17799.com/ Leyden, J. (2004). Security is our biggest chal-lenge. Retrieved April 1, 2004, from http:// www.securityfocus.com/news/8375
Likert scaling (2004). Retrieved January 19, 2004, from http://trochim.human.cornell.edu/kb/scal-lik.htm
MacDonald, L., & Fougere, K. (2003). Software piracy: A study of the extent of coverage in introductory MIS textbooks. Journal of Infor-mation Systems Education, 13, 325–330. Radcliff, D. (2002, June 3). Security under the
gun. ComputerWorld, 23,36.
Volonino, L., & Robinson, S. R. (2004). Principles and practice of information security. Boston:
Prentice-Hall.
Warner, B., & Abreu, E. M. (2003). Virus that infects E-mails expanding its reach. Retrieved August 22, 2003, from http://www.washington post.com/ac2/wp-dyn/A28502-2003Aug21?
lan-guage=printer
Wellner, A. S. (2000). TrustUS.com. American Demographics, 22(11), 47.
Whitman, M. E., & Mattford, H. J. (2004). Prin-ciples of information security(1st ed.). Boston: Course Technology.
APPENDIX A Textbook Review Listing
Applegate, L. M., McFarlan, F. W., & McKenney, J. L. (1999). Corporate Information Systems Management(5th ed.). Boston: Irwin McGraw-Hill.
Beekman, G., & Rathswohl, E. J. (2003). Computer Confluence: Exploring Tomorrow's Technology(5th ed.). Upper Saddle River, NJ: Prentice Hall.
Gordon, S. R., & Gordon, J. R. (2004). Information Systems: A Management Approach
(3rd ed.). Hoboken, NJ: John Wiley & Sons.
Jessup, L., & Valacich, J. (2003). Information Systems Today. Upper Saddle River, NJ: Prentice Hall.
Laudon, K. C., & Laudon, J. P. (2004). Management Information Systems: Managing the Digital Firm. Upper Saddle River, NJ: Pearson/Prentice Hall.
Long, L., & Long, N. (2004). Computers: Information Technology in Perspective(11th ed.). Upper Saddle River, NJ: Pearson Prentice Hall.
Martin, E. W., Brown, C. V., DeHayes, D. W., Hoffer, J. A., & Perkins, W. C. (2002).
Managing Information Technology(4th ed.). Upper Saddle River, NJ: Prentice Hall. McKeown, P. (2003). Information Technology & The Networked Economy(2nd ed.).
Boston: Course Technology.
McLeod, R., Jr., & Schell, G. P. (2004). Management Information Systems(9th ed.). Upper Saddle River, NJ: Pearson Prentice Hall.
McNurlin, B. C., & Sprague, R., Jr. (2004). Information Systems Management in Prac-tice(6th ed.). Upper Saddle River, NJ: Pearson Prentice Hall.
O'Brien, J. A. (2002). Managing Information Systems: Managing Information Technol-ogy in the E-Business Enterprise(5th ed.). Boston: McGraw-Hill Irwin.
Oz, E. (2002). Management Information Systems(3rd ed.). Boston: Course Technology. Parsons, J. J., & Oja, D. (2003). Computer Concepts(9th ed.). Boston: Course
Tech-nology.
Pearlson, K. E., & Saunders, C. S. (2004). Managing and Using Information Systems: A Strategic Approach(2nd ed.). New York: John Wiley & Sons.
Pfaffenberger, B., & Daley, B. (2004). Computers in Your Future(Complete ed.). Upper Saddle River, NJ: Pearson Prentice Hall.
Shelly, G. B., Cashman, T. J., & Vermaat, M. E. (2004). Discovering Computers 2004 A Gateway to Information. Boston: Course Technology.
Stair, R. M., & Reynolds, G. W. (2003). Principles of Information Systems(6th ed.). Boston: Course Technology.
Turban, E., McLean, E., Wetherbe, J., Bolloju, N., & Davison, R. (2002). Information Technology for Management: Transforming Business in the Digital Economy(3rd ed.). New York: John Wiley & Sons.
Turban, E., Rainer, R. K., & Potter, R. E. (2003). Introduction to Information Tech-nology(2nd ed.). Hoboken, NJ: John Wiley & Sons.
APPENDIX B
Computer Security Web Sites and URL Addresses
CERT®Coordination Center http://www.cert.org
The Internet Security Alliance http://www.isalliance.org Disaster Recovery http://www.drj.com ADDSecure.Net Inc. http://www.addsecure.net The Institute of Internal Auditors http://www.theiia.org Stanford Research Institute http://www. sri.com The SANS Institute http://www.sans.org