Informasi Dokumen
- Penulis:
- Daniel J. Barrett
- Richard E. Silverman
- Robert G. Byrnes
- Pengajar:
- Mike Loukides, Editor
- Mary Brady, Production Editor
- Sekolah: O'Reilly Media, Inc.
- Mata Pelajaran: Computer Security
- Topik: SSH, The Secure Shell: The Definitive Guide
- Tipe: book
- Tahun: 2005
- Kota: Sebastopol
Ringkasan Dokumen
I. Introduction to SSH
This section introduces SSH (Secure Shell), a critical component in network security for managing remote connections. It outlines the need for secure communication protocols due to the vulnerabilities of traditional methods like Telnet and FTP, which transmit data in plain text. SSH provides a robust solution by encrypting data and offering secure authentication methods, making it essential for system administrators and users who require secure access to remote systems.
1.1 What Is SSH?
SSH is a software-based protocol that provides secure access to remote computers. It automatically encrypts data sent over the network, ensuring that sensitive information such as usernames and passwords are protected from interception. SSH operates on a client/server architecture, where the SSH server manages incoming connections and the client initiates requests for secure operations, making it a versatile tool for secure remote logins and file transfers.
1.2 What SSH Is Not
Despite its name, SSH is not a command shell like the Unix Bourne shell. It does not perform command interpretation or provide shell features such as command history. Instead, SSH creates secure channels for running shell commands on remote systems. It is also not a comprehensive security solution; while it offers encryption and authentication, it does not protect against all forms of cyber threats like malware or denial-of-service attacks.
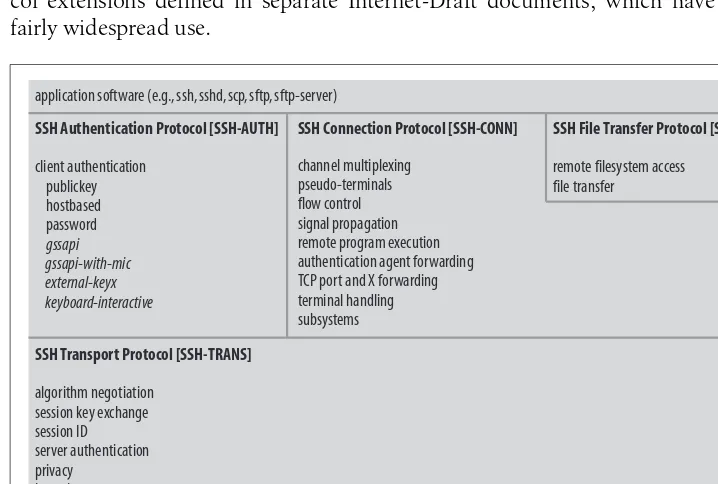
1.3 The SSH Protocol
SSH is defined as a protocol that specifies secure communication methods over networks. It encompasses three primary functions: authentication, which verifies user identities; encryption, which scrambles data to prevent unauthorized access; and integrity checks, which ensure data remains unaltered during transmission. The protocol has evolved, with SSH-2 being the recommended version due to its enhanced security features compared to the older SSH-1.
1.4 Overview of SSH Features
SSH provides several key features that enhance network security, including secure remote logins, file transfers, and command execution. For instance, SSH allows users to log into remote systems securely without exposing sensitive information. It also supports secure file copying through commands like 'scp', and enables administrators to execute commands across multiple machines while maintaining encrypted connections, thereby improving operational efficiency.
1.5 History of SSH
SSH was developed in 1995 by Tatu Ylönen in response to a password-sniffing attack on his university network. Initially released as free software, SSH gained widespread adoption, leading to the establishment of SSH Communications Security Corp. The introduction of SSH-2 in 1996 addressed the limitations of the original protocol, and the subsequent rise of OpenSSH made secure shell access a standard feature across various operating systems.
1.6 Related Technologies
SSH is part of a broader landscape of network security technologies. It shares similarities with traditional r-commands (like rsh and rlogin), which lack encryption. Additionally, SSH incorporates encryption algorithms found in PGP and GnuPG but applies them to secure ongoing sessions rather than individual files. Kerberos also provides secure authentication but operates differently, focusing on ticket-based access in controlled environments.
II. Basic Client Use
This section covers the fundamental operations of SSH clients, emphasizing their practical applications in secure remote access and file management. It provides step-by-step guidance on using SSH for various tasks, making it essential for both novice and experienced users. By understanding the basic client functionalities, users can effectively leverage SSH's capabilities to enhance their network security practices.
2.1 A Running Example
The section introduces a practical example to illustrate SSH's capabilities. It demonstrates how to establish a secure connection between two computers, highlighting the commands used and the expected outcomes. This example serves as a foundation for understanding more complex SSH functionalities, making it easier for users to grasp the practical applications of SSH in real-world scenarios.
2.2 Remote Terminal Sessions with ssh
This subsection explains how to initiate remote terminal sessions using the SSH client. It details the command syntax for logging into remote systems securely, ensuring that users understand the importance of encrypted connections. By using SSH for remote access, users can perform operations on remote machines without exposing sensitive information, thus enhancing overall security.
2.3 Adding Complexity to the Example
Here, the document explores more advanced scenarios involving SSH, such as executing commands on remote systems and managing multiple sessions. This section emphasizes the flexibility of SSH in handling complex tasks while maintaining security. Users learn how to navigate various SSH features, preparing them for more intricate operations in network management.
2.4 Authentication by Cryptographic Key
This subsection focuses on the authentication methods available in SSH, particularly the use of cryptographic keys. It explains the process of generating key pairs and configuring them for secure access. By utilizing key-based authentication, users can enhance their security posture and eliminate the need for password-based logins, which are more susceptible to interception.
2.5 The SSH Agent
The SSH agent is introduced as a tool for managing keys securely. This subsection discusses how the SSH agent stores private keys in memory, allowing users to authenticate without repeatedly entering passphrases. This functionality streamlines the authentication process while maintaining security, making SSH more user-friendly without compromising its robust security features.
2.6 Connecting Without a Password or Passphrase
This section elaborates on configuring SSH for passwordless connections, emphasizing the convenience and security benefits. It details the setup process for enabling secure access without needing to enter passwords, which can reduce the risk of credential theft. By following the guidelines, users can achieve seamless and secure remote access across multiple systems.
2.7 Miscellaneous Clients
The document highlights various SSH client implementations available across different operating systems. This subsection discusses the features and functionalities of popular clients, allowing users to choose the most suitable one for their needs. Understanding the diversity of SSH clients enhances users' ability to operate securely in varied environments.
2.8 Summary
This summary encapsulates the key points discussed in the section, reinforcing the importance of understanding basic SSH client operations. It emphasizes the practical applications and security enhancements provided by SSH, encouraging users to apply the knowledge gained in their own network environments.
III. Inside SSH
This section delves into the internal workings of SSH, exploring its architecture and cryptographic foundations. By understanding the technical principles underlying SSH, users can better appreciate its security features and make informed decisions regarding its implementation. The detailed analysis of SSH's structure equips readers with the knowledge necessary to troubleshoot and optimize their SSH deployments.
3.1 Overview of Features
This subsection provides a comprehensive overview of SSH's core features, including secure communication, authentication methods, and data integrity measures. It highlights how these features work together to create a secure environment for remote access and file transfers. Understanding these functionalities is crucial for users aiming to implement SSH effectively in their networks.
3.2 A Cryptography Primer
This primer introduces the cryptographic principles that underpin SSH, including symmetric and asymmetric encryption, hashing, and digital signatures. It explains how these concepts are applied within SSH to ensure secure communications. A solid understanding of cryptography is essential for users to grasp how SSH protects their data and identities.
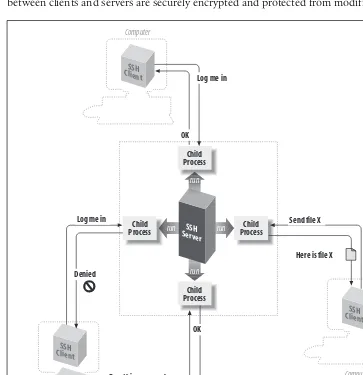
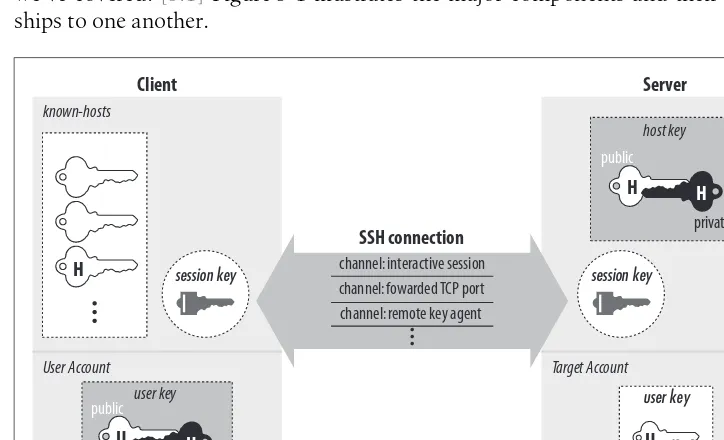
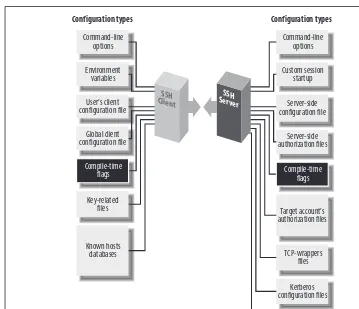
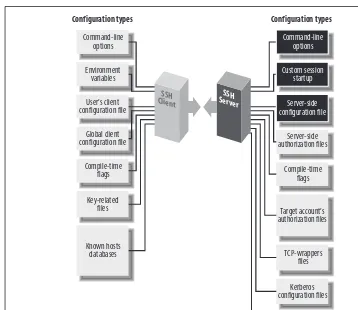
3.3 The Architecture of an SSH System
This subsection outlines the architecture of SSH, detailing the roles of clients and servers in establishing secure connections. It explains the interactions between components and how they facilitate encrypted communication. Understanding the architecture is vital for users looking to configure and manage SSH systems effectively.
3.4 Inside SSH-2
Focusing on the SSH-2 protocol, this subsection explores its features and improvements over SSH-1. It discusses the enhancements in security and functionality, making SSH-2 the preferred choice for modern implementations. Users will gain insights into why SSH-2 is the standard for secure communications today.
3.5 Inside SSH-1
This subsection reviews the SSH-1 protocol, discussing its limitations and vulnerabilities. While SSH-1 was revolutionary at its inception, understanding its shortcomings is essential for users to appreciate the advancements made in SSH-2. The comparison highlights the importance of transitioning to more secure protocols.
3.6 Implementation Issues
This section addresses common implementation challenges encountered when deploying SSH. It discusses best practices for configuration, troubleshooting, and ensuring security during implementation. Users will benefit from understanding these issues to avoid pitfalls and enhance the effectiveness of their SSH deployments.
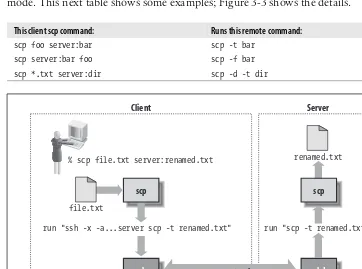
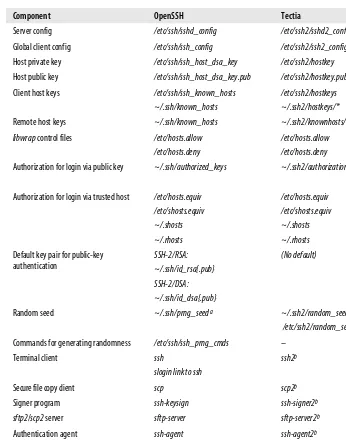
3.7 SSH and File Transfers (scp and sftp)
This subsection explains the file transfer capabilities of SSH, focusing on secure copy (scp) and secure file transfer protocol (sftp). It outlines the commands and usage scenarios for each method, emphasizing their importance in maintaining data security during transfers. Users will learn how to utilize these tools effectively in their workflows.
3.8 Algorithms Used by SSH
This section provides an overview of the cryptographic algorithms employed by SSH, detailing their roles in encryption, authentication, and data integrity. Understanding these algorithms is crucial for users to evaluate the security of their SSH implementations and make informed choices regarding algorithm selection.
3.9 Threats SSH Can Counter
This subsection discusses the various threats that SSH is designed to mitigate, including eavesdropping, man-in-the-middle attacks, and data tampering. By understanding these threats, users can appreciate the importance of using SSH in securing their communications and protecting sensitive data.
3.10 Threats SSH Doesn’t Prevent
While SSH provides robust security, this section outlines the threats it cannot mitigate, such as denial-of-service attacks and certain types of malware. Users must be aware of these limitations to implement additional security measures alongside SSH for comprehensive protection.
3.11 Threats Caused by SSH
This subsection highlights potential security risks introduced by SSH itself, such as misconfigurations and vulnerabilities in implementations. Understanding these risks is critical for users to ensure secure deployments and to take proactive measures against exploitation.
3.12 Summary
The summary of this section encapsulates the key concepts discussed regarding the internal workings of SSH. It reinforces the importance of understanding both the features and limitations of SSH to effectively utilize it in securing network communications.