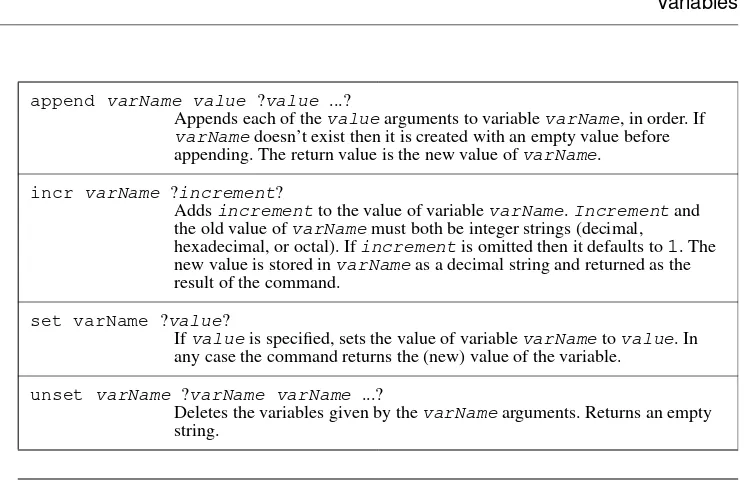
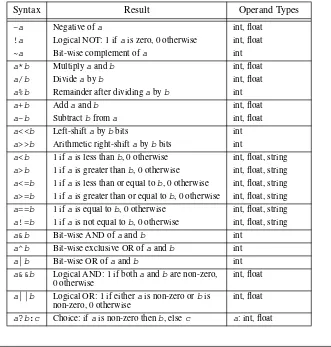
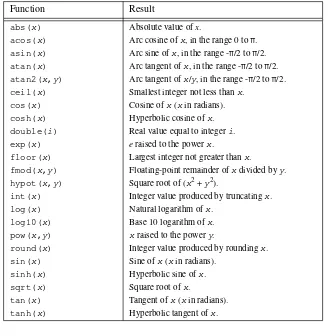
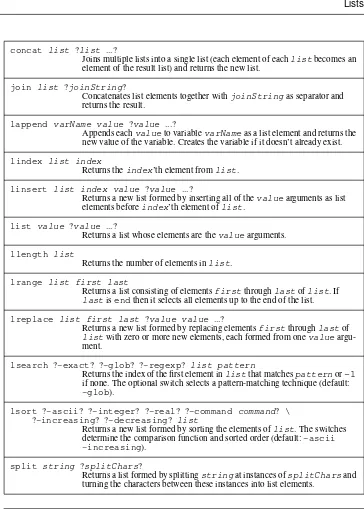
Tcl and the Tk Toolkit Ebook free download pdf pdf
Teks penuh
Gambar
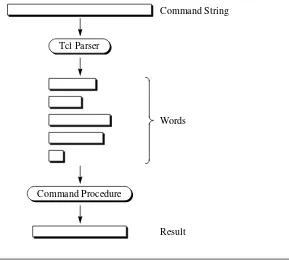
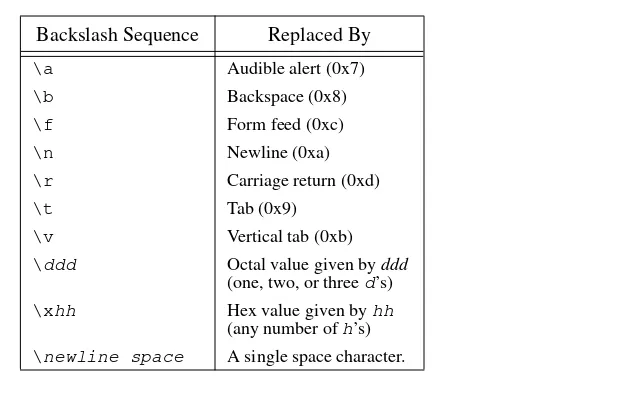
Dokumen terkait
It also means multi- plying the nodes you’ll need to manage, doubling all of the data replication, code, and configuration deployment, and multiplying all of your monitoring
The supervisor sends messages to each of the three worker actors asking them to perform their specific tasks.. When each worker completes its task, it sends a message back to
Not to be confused with the FTC’s Privacy Framework, Commerce released its own privacy report , entitled “Commercial Data Privacy and Innovation in the Internet Economy: A
Despite the promise and potential of AI and ML to revolutionize medicine, the majority of healthcare providers stick with traditional processes to diagnose and treat patients.. Part
These are JUG-led global programs founded by the London Java Community, and are designed to provide ways for ordinary Java developers to contribute to the development of new
He helps to organize the London Java Community and represents them on the Java Community Process Executive Committee, where he works to define new standards for the Java ecosystem.
Before you can start the MongoDB service, you need to create a data directory for MongoDB to store its files in.. By default, MongoDB stores the data in the
The fact that this industry represents our best protection when we are entering in this new hyperdigital world with all its cybersecurity perils should instill a sense