This project titled “Design and Implementation of Network Management for Corporate Offices” submitted by Md. Jobaer Hossain, ID at the Department of Computer Science and Engineering, Daffodil International University, has been accepted as satisfactory in partial fulfillment of the requirements for the degree of B.Sc. Department of Computer Science and Engineering Faculty of Science and Information Technology Daffodil International University.
We hereby declare that we have carried out this project on our own under the supervision of Sharmin Akter, a lecturer in the department of CSE Daffodil International University. We also declare that neither this project nor any part of this project has been submitted elsewhere for the award of any degree or diploma. The deep knowledge and great interest of our supervisor in the field of "networking" for the implementation of this project.
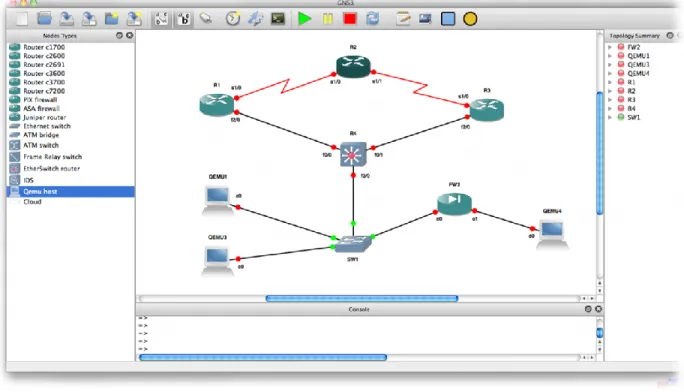
Her endless patience, scientific guidance, constant encouragement, constant and energetic supervision, constructive criticism, valuable advice, reading many inferior drafts and correcting them at all stages have made the completion of this project possible. We used GNS3 Software to design this project and after implementation we tested this project in virtual machine (VMware).
LIST OF TABLES
INTRODUCTION
- Project Goal
- Motivation
- Objectives
- Scope of Studies
- Outcomes
- Report Layout
The project on the design and implementation of network administration for business offices is an important aspect of networking that will make the network sector more secure and easy to use for business offices. This project builds a relationship that brings together the head office and their branches into a specific network from where it can easily maintain a continuous connection to share its data, as well as observe from a specific location. The main goal of this project is to develop our network infrastructure for the desire of efficient and powerful communication that our corporate office really needs.
This project gave us the opportunity to figure out our internal questions about the design and implementation of network administration. Our knowledge of network field at the beginning was accidental. This project is mainly valuable for the network related organizations to understand the network system which includes various network devices, physical and wireless devices communication, routing protocol and configuration, network monitoring tools, servers, network security tool, and MikroTik router and so on. We are proud to say that this project will bring positive results to the corporate arena.
We have described our entire project on design and implementation on Design and Implementation of Network Administration for Corporate Office through this report. Fourth Chapter: In this chapter we implement our design and configure this design also server configuration.
BACKGROUND
- Related Works
- Comparative Studies
- Scope of Problem
- Challenges
Design Implementation and Monitoring of an ISP's Network: The ISP Xenial Broadband in Baridhara area of Dhaka [2], monitors their customers and bandwidth provider through a network system. We are influenced by Design and Simulation by Banking Network System and ISP Network System. Now the system is connected to a private network system where online banking user also communicate between their branches and head office.
We have been influenced by these two network systems, but there is no similarity in our project. Our project also offers extra services that modernize this project and make it user-friendly. This can be a big problem in a corporate office because they depend on this system where they need a better optimized and sufficiently secure network system.
But we're trying to include something in our project that makes the system more secure and faster. We have designed this so that not only the network system also has additional services like faster download, download, fast response etc.
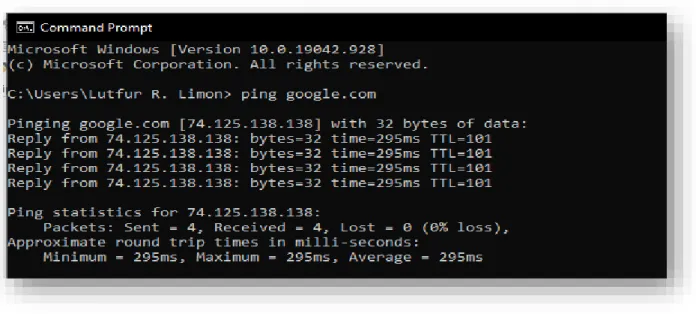
REQUIREMENT SPECIFICATION & USAGE 3.1 Hardware Requirements
- Project Requirements
- Switch
- MikroTik Router
- GSN3: Graphical Network Simulator
- Winbox
We also used some software and hardware devices that we did not mention in Table 3.1, but we used this device and software to implement this project. We choose cisco switch, the switch designed by cisco is too reliable and provides better services. Basically Network switch used to connect network devices in a specific platform from like a computer, connect to printer, router, server, other resources.
Systems administration is the need for some components for switches and keys that allow our connection to connect at least one PC to another PC, even different systems. The MikroTik router is a more powerful device than other routers, which has many good reasons to use, including Internet sharing and bandwidth control. It is a device like a switch/router, ranging in size from a small box to a large box.
This device has one port for the Internet connection and LAN port for local area network just like other routers. This router acts as an internet sharing server and it is possible to use multiple devices on the same network using this device. MikroTik Operating System (ISO): The developers of MikroTik Router have also developed it as an operating system.
We used the devices for free, whatever was easy to set up on this platform. Connect and simulate VMware/Virtual Box to GNS3 and can create some of complex network labs. Winbox is a small utility that allows the administration of MikroTik RouterOS using a simple graphical user interface.
We choose Winbox to configure our router because Winbox has some interesting features and services, such as making it easy to configure devices and manage them. There are other alternatives to Winbox, but in the worst case scenario they are relatively easy to use and reliable to get the expected outcome.
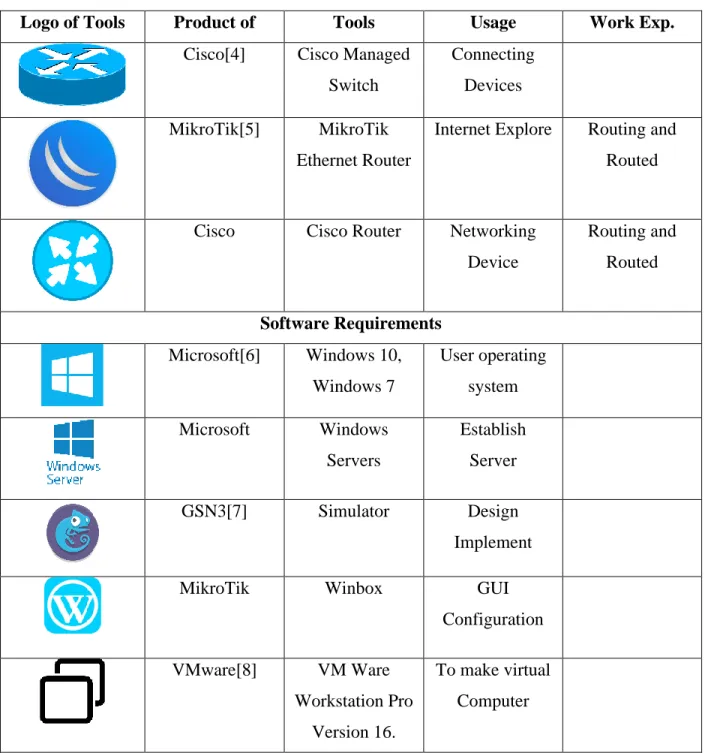
DESIGN AND IMPLEMENTATION 4.1 Design a Network
Backbone Network Design
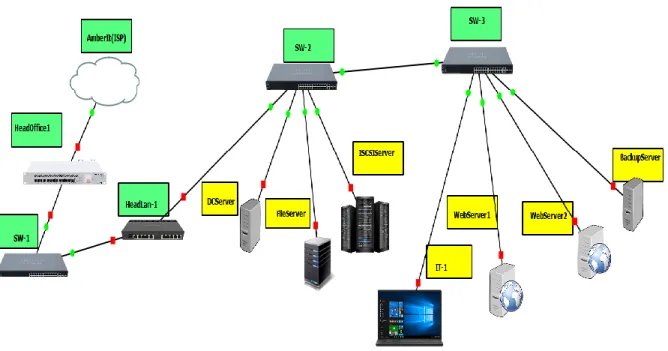
Overall design of a Network Planning
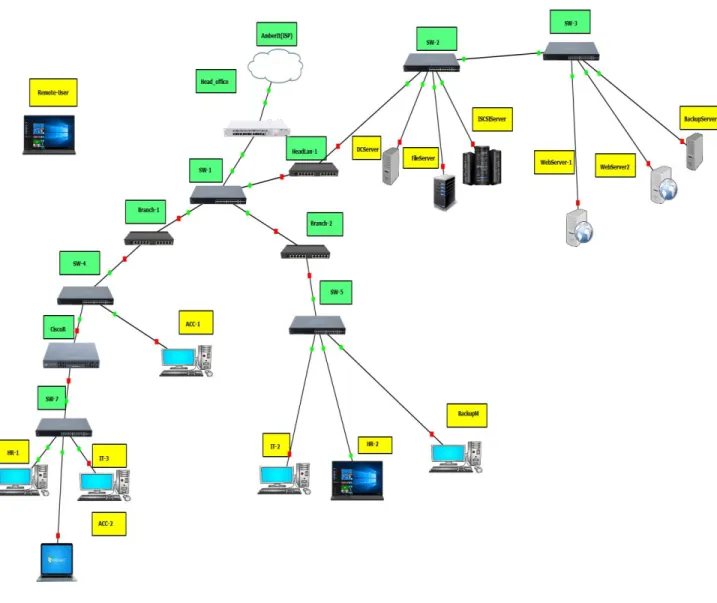
The aforementioned image above shows that it consists of several WAN and LAN and the head office and their branches and servers. In Figure 4.3 we can see that the server and offices are connected using routers and switches. In Figure 4.3 we see a small connection using a workstation and a server. LAN stands for Local Area Network.
Here we see another network connected to the Internet and consisting of three branches and each branch workstation. This is WAN and stands for Wide Area Network.
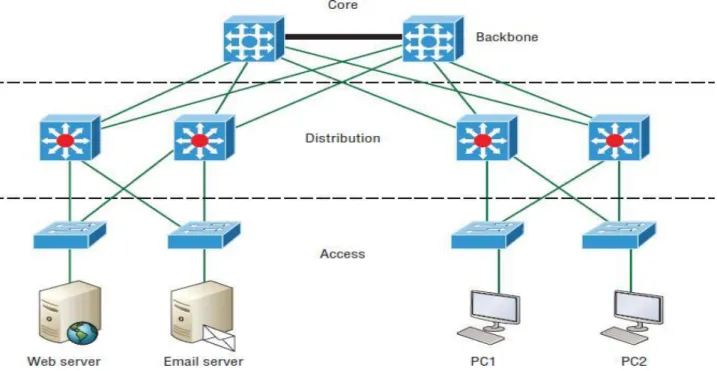
Layer Network
Design Implementation on Head Office
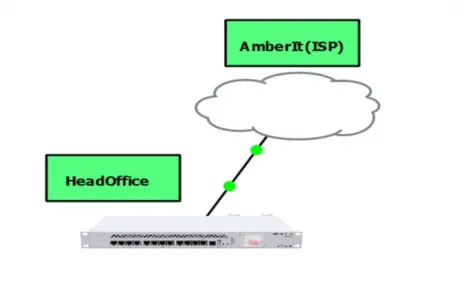
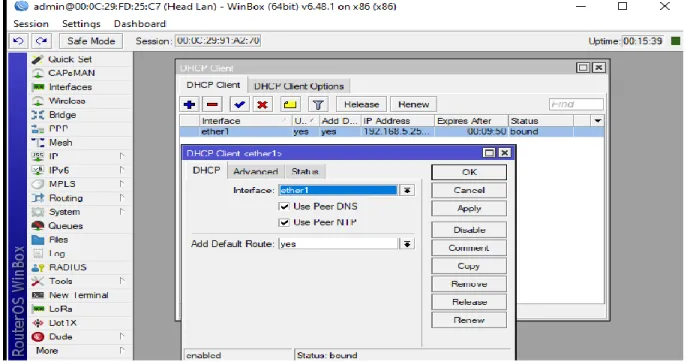
Internet Connectivity
Local Area Network of Head Office
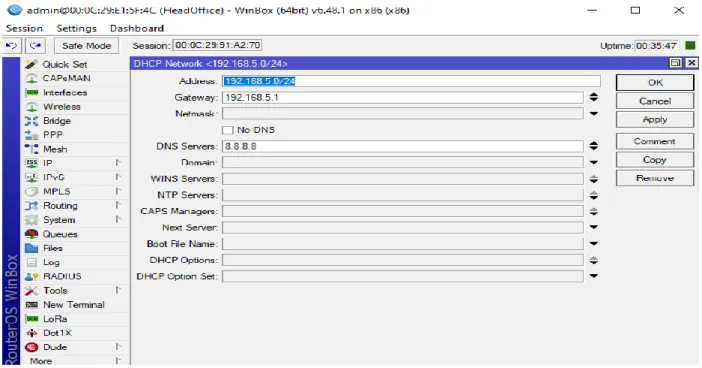
LAN Configuration for Head Office
Design implantation on branch 1
Branch1 Configuration
Figure 4.10.5 shows that we used a Cisco router in Branch1 connecting from the main office. CiscoR(config)#IP access list default 1 CiscoR(config-std-nacl)#permit any CiscoR(config-std-nacl)#exit. After configuring Cisco Router, we need to connect the user to Branch1's network so that they can use the Internet connection.
After we have configured the Cisco router and also secured the user connection, we need to check that the Branch1 user has internet.
Design Implementation for Branch2
Point-to-point over Ethernet refers to the system used to connect multiple devices, computer, laptop, smart phone and so on to an Ethernet Local Area Network (LAN). The main purpose of PPPoE used in a building or office allows the user to share a common digital subscriber line.
PPPOE Server Configuration i. Address Assigning in PPPOE
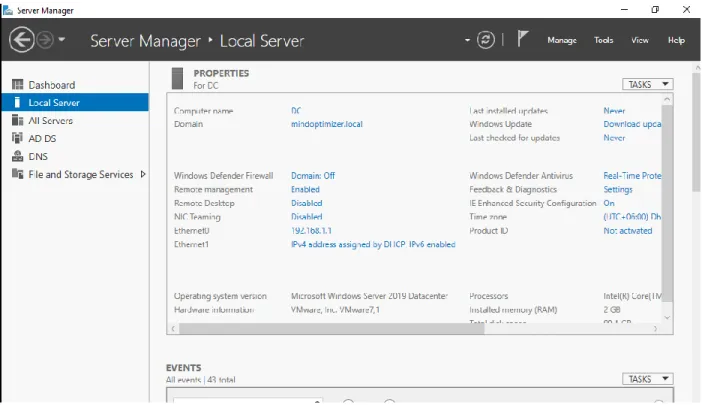
Windows Server Installation
ADDS Install in Windows Server
Promote Server as a Domain Controller
Domain Controller Promotion is a tool in Active Directory that installs and removes ADDS and promotes domain controllers.
Organizational Unit, Groups, User Creating
File Server
After choosing role, we check if the role is installed in our windows function, then we configure the server from server manager.
File Server Configure
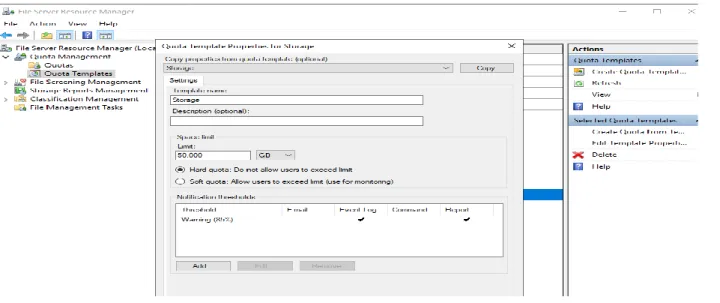
Go to File Manager and Create Folder > File Server > Right Click > Properties > Sharing >. Advanced sharing > check in share this folder > Permission > Full control > Add groups > it >. To apply quota, go to Server Manager > Tools > FSRM > Expand Quota Management > Quota.
File Screening Management is a feature that allows us to control the types of files that the user can store on a file server. In our system, we once again use the same way that the head office HR department can access and edit specific files that employees in branches cannot access. Go to Server Manager > Tools > FSRM > Expand File Screening Management > Create File Screening Management > Settings > Template Name > Block Audio and Video > Screening Type > Active Screening > Select File Groups > Audio and Video Files > ok.
Before applying File Screening, go to Server Manager > Tools > FSRM > Expand File Screening Management > File Screens > Create Screen > Drive File Screen Path > Drive Properties that we create d> Create.
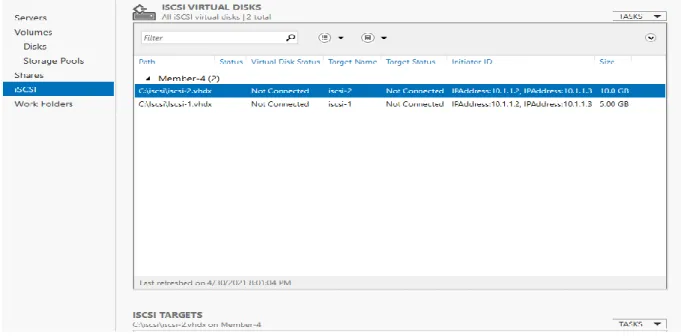
In Figure 4.19.1 Management of iSCSI Virtual Disk crating state iSCSI Virtual Disk which can be used by many users if the main server is full. Go to disk management > select iSCSI storage > new storage > name > iSCSI-2 > OK.
Failover Clustering
NLB Clustering
Group Policy Management
TESTING
- Test case 1
- Test case 2
- Test Case 3
CONCLUSION
- Achievements
- Future Plan
- Appendices
This project has sharpened our concept in the network sector, installation devices and the software-hardware interface. The success of this project can bring pleasure to business users in our country.
Plagiarism Status