International Conference on Electronics, Computer and Communication
A study on the Adaptive Secured Ad hoc on demand distance vector (AODV) routing
protocol for MANets
Tanveer Haque
1, Nazmus Sakib
1, Hasib-Bin-Shakur
1, Sohel Hossain
1 1Computer Science and Information Technology, Islamic University of Technology
E-mail: thaque@iut-dhaka.edu, sakib999@iut-dhaka.edu, hasibcit@iut-dhaka.edu, kbr_iut@iut-dhaka.edu
,
ABSTRACT
Security in wireless network is a challenging issue in this era. While much effort has been made to address issues at physical, data link, and network layers, little attention has been paid to the security aspects central to the realistic deployment of AODV routing protocol. In this paper we propose a two-way-security to the existing protocol of AODV. The first maintains the security of the nodes and the other to that of messages, which are relayed through the nodes. So if any node fails in any case it doesn’t let the messages to be passed to the malicious outsiders.
KEY WORDS:
Whirlpool-512, Sha -160, AODV, Ad hoc
1. INTRODUCTION
A mobile Ad hoc network (MANets) is a kind of wireless Ad hoc network, and is a self-configuring network of mobile routers (and associated hosts) connected by wireless links – the union of which form an arbitrary topology [8]. Each node communicates directly with other nodes within a specified transmission range. The nodes communicate via other nodes if they are not within a specified transmission range.
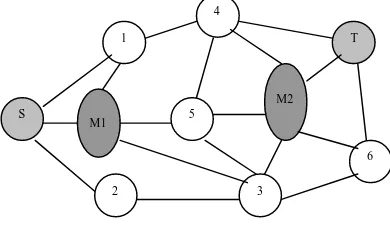
Node mobility causes frequent changes in topology. MANets are usually set up in situations of emergency for temporary operations or simply if there are no resources to set up elaborate networks. These types of networks operate in the absence of any fixed infrastructure, which makes them easy to deploy. But at the same time, due to the absence of any fixed infrastructure, it becomes difficult to make use of the existing routing techniques for network services. Hence this poses a number of challenges in ensuring the security of the communication. This wireless nature of communication and lack of any security infrastructure makes this infrastructure actually open to various types of attacks from outsider malicious nodes. Figure 1 depicts the existing AODV routing protocol [5].
From Figure 1 we see that when senders transmit Route Request (RREQ) it is not secured. Any malicious node can respond to this RREQ and include itself in the route. The same may happen in case of route reply (RREP). Moreover the malicious node can generate false route error (RERR) to force sender to retransmit the massage during the data transmission to get the full massage. In order to secure the data transmission we need to secure the RREQ, RREP, RERR first. So that the possibility of inside attacks is reduced. At last the receiver should transmit an acknowledgement (ACK) to confirm the sender that the
full massage is received so that no malicious node can generate false RERR to obtain the massage.
Any routing protocol must encapsulate an essential set of security mechanisms. These are the mechanisms that help to prevent, detect, and respond to security attacks. There are four major security goals that need to be addressed in order to maintain a reliable and secure Ad hoc networking environment [9]. They are mainly:
Confidentiality: Protection of any information from being exposed to unintended entities.
Authentication: Here the receiver needs to be sure of the sender’s identity and that an imposter has not sent the message.
Integrity: Message being transmitted is never altered.
Non-repudiation: Ensures that sending and receiving parties can never deny of sending or receiving the message.
Figure 1: Existing AODV routing protocol
Send ACK
No
Yes
{
Start
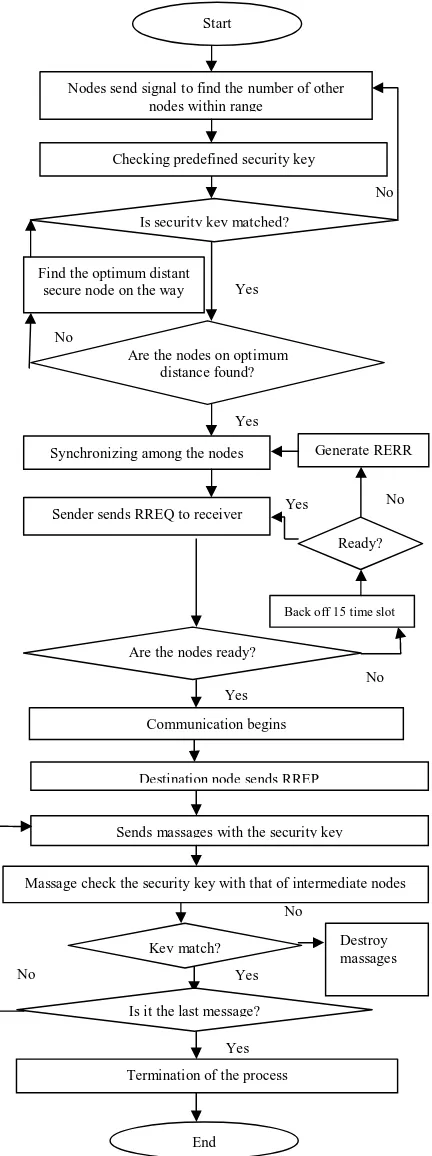
Nodes send signal to find the number of other nodes within range
Synchronizing among the nodes
Sender sends RREQ to receiver
No
Ready? Generate RERR
Yes
{
Receiving node send back RREP
Back off 15 time slot
End Are the nodes ready?
Communication begins
Services should be available whenever required. There should be an assurance of survivability despite the Denial of Service (DOS) attack in which an attacker monopolizes a system with so many service requests that the system collapse and denies service to every request.
From the architecture we see that the nodes are actually open to various types of malicious attacks.
All the above security mechanisms must be implemented in any Ad hoc network to ensure the security of the transmissions along that network.
Broadly there are two major categories of attacks when considering any network Attack from external sources and attacks from within the network. The second attack is more severe and here detection and correction are more difficult. Routing protocol should be able to secure themselves against both of these attacks.
2. RELATED WORK:
2.1 Secure Ad Hoc On Demand Distance Vector Routing Protocol (S-AODV):
S-AODV’s [7] basic functionality lies in securing the ADOV protocol by authenticating the non-mutable fields of the routing message using digital signatures.
It also provides an end-to-end authentication and node-to-node verification of these messages. The source node-to-node digitally signs the route request packet (RREQ) and broadcasts it to its neighbors. When an intermediate node receives a RREQ message, it first verifies the signature before creating or updating a reverse route to its predecessor. It then stores or updates the route only if the signature is verified. A similar procedure is followed for the route reply packet (RREP).The only mutable field in S-AODV messages is the hop-count value.
2.2 Secure Routing Protocol (SRP):
The basic idea of SRP [2, 4] is to set up a security association (SA) between the source and the destination node [6]. The SA is usually set up by negotiating a shared key based on the other party’s public key, and after that the key can be used to encrypt and decrypt the messages. The routing path information is always sent through the packets, unencrypted since none of the intermediate nodes have knowledge of the shared key. Figure 2 explain this.
Figure 2: Working principle of SRP
2.3 Security-Aware Ad hoc Routing (SAR):
The SAR [3] protocol makes use of trust levels (security attributes assigned to nodes) to make informed, secure routing decision. Although current routing protocols discover the shortest path between two nodes, SAR can discover a path with desired security attributes. The different trust-levels are implemented using shared symmetric keys. In order to forward or receive a packet by a node, it has to decrypt it first and therefore it needs the required key. Any node which is not on the requested trust level will not have the key and cannot forward or read the packets.
2.4 Authenticated Routing For Ad Hoc Networks (ARAN):
ARAN’s [1] main usage is seen in managed-open environments. It consists of a preliminary certification process followed by a route instantiation process that guarantees end-to-end authentication. This protocol requires the use of a trusted certificate server T, which public key is known to all the nodes of the network. As a result it is not a fully Ad hoc network.
2.5 Drawbacks of the Previously Described Works:
One of the main issues with the ARAN protocol is the requirement of a certificate server, which means that the integrity of that server is vital. This is however, can only be applied for securing communication over a managed-open environment but not for an Ad hoc network.
For the SAR, however, if a malicious node somehow retrieves the required key during passing it from node to node, the protocol has no further security measure to prevent against the attacker from bringing the entire network to a standstill.
In the case of SRP, however, it exposes network infrastructure information to potential attacks. In fact one of the main security issues in SRP is that it has no defense against the “invisible node attack” that simply puts itself somewhere along the message path without adding itself to the path and thereby causing potentially big problems as far as routing goes.
3. TYPES OF ATTACKS FACED BY ROUTING
PROTOCOLS:
Due to the underlined architecture, Ad hoc networks are more easily attacked than a wired network. The attacks prevalent on Ad hoc routing protocols can be broadly classified into passive and active attacks [10].
A Passive Attack does not disrupt the operation of the protocol, but tries to discover valuable information by listening to traffic. Passive attacks basically involved by obtaining the vital routing information through sniffing about the network.
An Active Attack, however, injects arbitrary packets and tries to disrupt the operation of the protocol in order to limit availability, gain authentication, or attacks packets destined to other nodes.
S
2 1
M2
3
6 5
4
T
3.1 Attacks Based On Modification
This is the simplest way for a malicious node to disturb the operations of an Ad hoc network. The only task that the malicious node needs to perform, is to announce the better routes (to reach other nodes or just a specific one) than the existing one.
3.2 Impersonation Attacks
Here the malicious node hides its IP address or MAC addresses and uses that of another node. Since current Ad hoc routing protocols like AODV and DSR do not authenticate source IP address, a malicious node can launch many attacks in this way.
3.3 Attacks by Fabrication of Information
This attack can be done by:
1. Generation of false Route Error Messages
2. Corruption of Routing State (alteration of messages by malicious nodes)
Considering all the above attacks we can draw a conclusion that we need an algorithm to ensure the secure passage of messages through the whole network.
3. OUR PROPOSAL:
Our proposed method is mainly based on “Secure Ad hoc On-Demand Distance Vector (SAODV) Routing” [2]. Our proposal is to ensure the security of the AODV routing protocol as follows:
1. An active attack and attack by fabrication of information can be checked by the process described in our algorithm, where we use the Sha -160 bit security code for the safety of messages.
2. Passive attack which involves sniffing about the network can be checked in our algorithm through the Whirlpool-512 bit security code for the safety of nodes.
3. In our proposal, the answer to the RREQ message exists only on the particular nodes and these answers are not transmittable. Thus there exists almost no chance of the answer key being sniffed by the intruders. In this case RREQ is maintained by matching the security key and not according to the IP address or MAC address of the optimum nodes. So as we give only one chance to match the security key, the possibility of breaking this Whirlpool-512 bit code is 1/2512. Same thing happens in the case of messages, when it does not match the security key of its own and in the second time the message is destroyed by itself automatically. But if the destination node misses one message, it sends the message to the sender node through the entrusted zone. The process is shown in figure 3.
Figure 3: Flowchart of the proposed method
Yes
Ready? Generate RERR
No
Yes
Termination of the process
End Yes Yes
No Communication begins
Sends massages with the security key
Destroy massages Key match?
Is it the last message?
Massage check the security key with that of intermediate nodes Destination node sends RREP
No
No
Are the nodes ready?
Back off 15 time slot
Yes No
No
Are the nodes on optimum distance found?
Synchronizing among the nodes
Sender sends RREQ to receiver Yes Checking predefined security key
Start
Nodes send signal to find the number of other nodes within range
Is security key matched?
3.2 Example:
Previous algorithm shows that it only takes these steps necessary to find the optimum path for relaying messages through the nodes. It actually becomes vulnerable to all sorts of outsiders that provide smaller hop counts than that of the optimum path.
But in our algorithm at first we mainly check the security of the node throughout the checking of security keys. For this at first we transmit the RREQ encrypted by Whirlpool-512 with a security question. Node of the same organization knows the answer. This answer is not transmittable. If any node can answer the question then it is counted for the route. As the security answer is not transmittable the possibility of getting the correct answer from a malicious node is very low.
After that we select only those nodes which are secured and on optimum distance to maintain the flawless passage of messages.
The RREP from the receiver node also came in the same way. As a result the route discovery is secured and the possibility of insider attack is zero.
We take our second security steps to secure the massage. When the massage is transmitted through the path it is encrypted by Sha-160. It also contains a security question which must be answered to receive the massage. If the question is not answered correctly at the first time, the massage destroys itself instantly. Eventually if any node wants to capture the transmitted massage it gets nothing.
Moreover the RERR massage also carries the security question so that no malicious node can generate the false RERR to capture the massage. Sender node only responses to those RERRs that have the security question.
When transmitting a massage the entrusted node only reply to other entrusted nodes so that the DOS attack cannot be performed.
Thus our algorithm provides a secured AODV routing protocol.
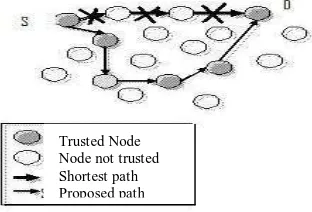
Figure 4: Secured route maintenance
In figure 4, the shortest path is the crossed one. The message is not delivered through this path, because there are some unsecured nodes. So according to our algorithm, it takes a longer way to confirm the security of the messages. In the longer way all the nodes are trusted, because they can answer the security key of the messages.
4. CONCLUSIONS AND FUTURE PLAN:
Security is vital for a successful deployment of services over MANets. In this paper, we have discussed prevention and detection mechanisms that were adopted to provide security in Ad hoc networks. A prevention-only strategy will only work if the prevention mechanisms are perfect; otherwise, someone will find how to get around them. Most of the attacks and vulnerabilities have been the result of bypassing prevention mechanisms. In view of this reality, detection and response are essential. In this paper we discussed proposals representing all of these classes. In future, we will analyze the performance of our proposed approach using Network Simulator (NS2).REFERENCE:
[1] Bridget Dahill, Brian Neil Levine, Elizabeth Royer, Clay Shields. A Secure Routing Protocol for Ad hoc Networks In Proceedings of the 10 Conference on Network Protocols (ICNP), November 2002.
[2] Panagiotis Papadimitratos and Zygmunt J. Haas Secure Routing for Mobile Ad hoc Networks SCS Communication Networks and Distributed Systems Modeling and Simulation Conference (CNDS 2002), San Antonio, TX, January 27-31, 2002.
[3] S. Yi, P. Naldurg, and R. Kravets Security-Aware Ad hoc Routing for Wireless Networks The Second ACM Symposium on Mobile Ad hoc Networking & Computing (MobiHoc'01), 2001.(another version Security-Aware Ad hoc Routing Protocol for Wireless Networks, Report, August, 2001).
[4] Sarat Sreepathi, Vamsi Venigalla, Akshay Lal. A Survey Paper on Security Issues Pertaining to Ad hoc Networks.
[5]
Perkins, E. Belding-Royer, S. Das
Network Working Group, Nokia Research Center
University of California, Santa Barbara, University
of Cincinnati
July 2003.
[6] P. Papadimitratos, Z.J. Haas, P. Samar, The Secure Routing Protocol (SRP) for Ad hoc Networks. draft-papadimitratos-secure-routing-protocol-00.txt 2002-12-11.
[7] Manel Guerrero Zapata. Secure Ad hoc On-Demand Distance Vector (SAODV) Routing INTERNET-DRAFT draft-guerrero-manet-saodv-00.txt, August 2002. First published in the IETF MANET Mailing List (October 8th 2001).
[8] Wikipedia- Mobile Ad hoc network.
[9] Behrouz A Forouzan -Data Communication and Networking –Page -961-962.
[10] William Stallings -Cryptography and Network Security Principals and Practices
Page-13, 14.
![Figure 1 depicts the existing AODV routing protocol [5]. From Figure 1 we see that when senders transmit Route](https://thumb-ap.123doks.com/thumbv2/123dok/2097971.1607803/1.612.311.536.394.704/figure-depicts-existing-routing-protocol-figure-senders-transmit.webp)