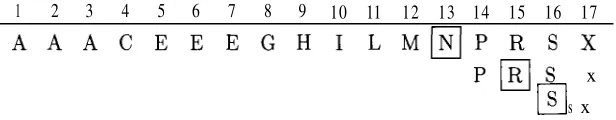ALGORITHMS ROBERT SEDGEWICK Free ebook download
Teks penuh
Gambar

Garis besar
Dokumen terkait
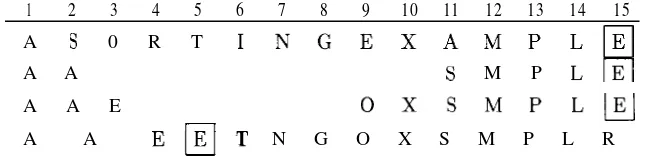
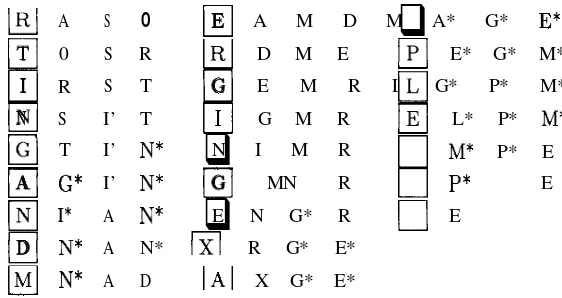
If @array has one element `blue' and %hash has a corresponding key `blue', the match is true if %hash{'blue'} has a true value, but false if %hash{'blue'} has a false
After we have created my initialization logic in my App.js file, we will then create an instance of the app, and call the run function at the very bottom of the page, as shown in
The following program illustrates how to obtain the address of the memory location or the address of the variable where data is stored..
IBookDao dependency in the Spring context file, you will, by virtue of the fact that there is only one instance of the WebApplication class per web application, end up with a
A metabotropic glutamate receptor AmGluRA identifi ed in the honey bee genome is expressed in the brain of pupae and adult honey bees and is involved in olfactory memory
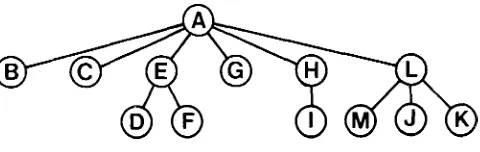
This is the idea that a class provides certain methods (the interface ) to the code that uses its objects, so the outside code does not directly access the data structures of
That’s what we’re going to program in this capstone project that brings together network-enabled projects like the Web-Enabled Light Switch and the Android Door Lock
The configuration file consists of two components. The first is an array of paired values that consists of a time marker and a string of text. That string can be plain text or