Abu Rayhan Alif, ID Number of the Department of Computer Science and Engineering, Daffodil International University, has been accepted as sufficient for the partial fulfillment of the requirements for the degree of B.Sc. Department of Computer Science and Engineering Faculty of Science and Information Technology Daffodil International University. Gazi Zahirul Islam, Assistant Professor in the Department of Computer Science and Engineering, Daffodil International University, in partial fulfillment of the requirements for the degree of Bachelor of Science in Computer Science and Engineering.
We would like to express our sincere and heartfelt respect and gratitude to Gazi Zahirul Islam, Assistant Professor, Daffodil International University, Department of Computer Science and Engineering. We are truly committed to the person who not only supervised us, but also had a leadership role throughout the entire journey of the project. It is none other than Professor Syed Akther Hossain, Head of the Department of Computer Science and Engineering, Daffodil International University, for his insightful guidance and also for providing the resources we needed and guiding us in the right direction to complete the project. Wifi, also known as Wi-Fi or wifi, is a common technology that allows an electronic device to wirelessly exchange data or connect to the Internet.
Wi-Fi allows us to simultaneously connect many computers to the same high-speed Internet connection. Within the Wi-Fi network coverage area, anyone with a Wi-Fi-enabled laptop or other device can connect to the Internet. In contrast, the router receives data from the Internet, converts it into radio waves and sends it to the computer's wireless adapter.
Motivation
To ensure the safety of your Wi-Fi network, both at home and in public, it is essential that it is secure. Anyone with a wireless card can use the network administrator's signal if they configure their router to create an open access point. On the other hand, most people would prefer strangers to stay out of their network.
Additionally, the user can choose to block WAN requests, which prevent the router from responding to IP queries made by remote users, limit the number of devices that can connect to the router, and disable remote administration.
Wi-Fi Security
Attacking Way on Wi-Fi
Wireless intruders: Wireless intrusion prevention systems (IPS) such as Motorola AirDefense, AirMagnet and AirTight can detect hostile Wi-Fi clients in or near a company's airspace. However, 802.11n introduces a plethora of somewhat complicated configuration choices, the effects of which are highly dependent on the capabilities of (extremely varied) Wi-Fi clients. Ad Hocs and Soft APs: Risky peer-to-peer ad hoc connections that bypass network security measures have long been possible with Wi-Fi laptops.
Unfortunately, new laptops with Intel and Atheros Wi-Fi interfaces and "soft access points" in Windows 7 eliminate this obstacle. Misbehaving Customers: Customers who intentionally or unintentionally establish unauthorized Wi-Fi connections are hurting themselves and their businesses. Some companies use GPOs to establish authorized Wi-Fi connections and prevent end-user modification.
Use host-resident agents or WIPS to monitor the behavior of Wi-Fi clients and close high-risk connections. The widespread deployment, increased reach, and deeper integration of consumer electronics have made accidental or incorrect Wi-Fi connections easier than before. Endpoint attacks: Wi-Fi endpoints are being targeted by attackers as wireless encryption and network edge security have improved.
Several bugs in Wi-Fi drivers have been exploited to execute arbitrary instructions, sometimes at the ring 0 level, via buffer overflows (high-privilege kernel mode). Despite the fact that vendors (usually) fix these vulnerabilities when they are discovered, Wi-Fi driver updates are not automatically delivered with OS upgrades. WiFi endpoint vulnerabilities can be tracked using WiFiDEnum, and Wi-Fi drivers must be updated to protect your employees from hackers.
Wireless spoofing: Wi-Fi users continue to be tricked by hackers, despite man-in-the-middle attacks that have already been exposed. A Wi-Fi network can be monitored and protected with a few open source auditing tools available to keep you aware of these dangers.
Objective
It is possible to poison Wi-Fi client browser caches, for example, if an Evil Twin is used on an open Wi-Fi hotspot to gain access to a previous Web session. After leaving a hotspot, poisoned customers can be redirected to phishing sites even when connected to a wired business network.
Expected Outcome
BACKGROUND
- Introduction
- Related Works
- Research Summary
- Scope of the problem
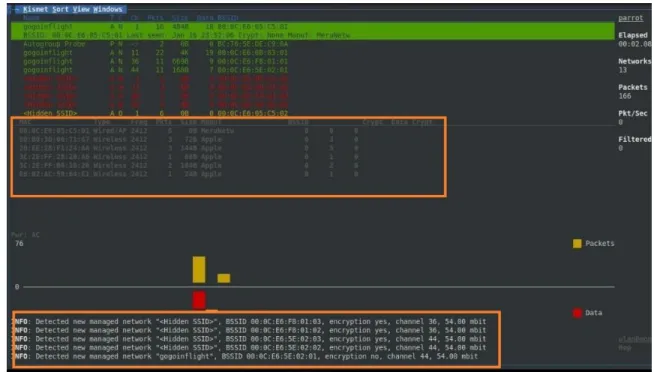
De-authentication and open Telnet access were used to bring down the Bebop UAV and Parrot AR, respectively, at Defcon 23, according to the author of [4]. As part of our approach, we use the Telnet application to send malicious Java script (JSON) objects over port 44444, but we do not access the UAV's telnet server or kill any processes. Using a Raspberry Pi, Perl script and free software, security researcher Samy Kamkar was able to deauthenticate a Parrot AR Drone from its controller.
This attack, known as "Skyjack", uses a de-authentication mechanism to access the Wi-Fi on the UAV. According to the author of [8], Parrot AR UAV 1.0 and 2.0 were found to be vulnerable to ARP (Address Resolution Protocol) poisoning, as well as DHCP (Domain Host Configuration Protocol). Although this attack is comparable to ours, we think we have shown that the newer Parrot Bebop UAV is susceptible to ARP Cache poisoning for the first time.
Bebop also has the same ARP Cache Poisoning vulnerability as the previous UAV platform, according to our analysis. Additionally, we have uncovered a brand new vulnerability, the ARDiscovery process, on the Parrot UAV platform that has never been disclosed before. Commercially available UAVs are unlikely to be developed or manufactured in a secure manner, putting the public at risk if used on a large scale without proper safety controls, according to previous studies and the zero-day vulnerabilities we revealed.
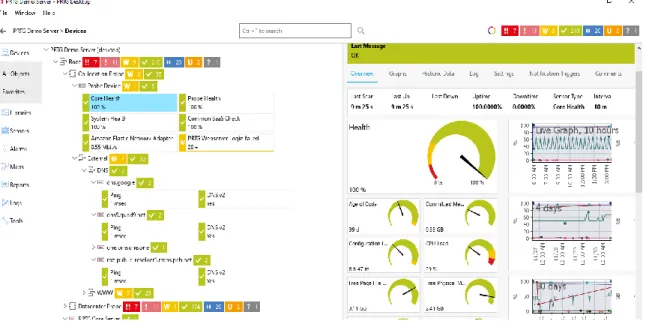
We can easily use open source tools to ensure wireless network security, and open source technologies can meet all the requirements previously stated. Free software auditing tools can also be used to audit wireless networks in the academic sector, such as universities, colleges and schools. Based on our findings, we recommend that all academic network administrators employ PRTG and wireshark to monitor the wifi zone.
RESEARCH METHODOLOGY
- Introduction
- Research Subject and Tools
- Data Collection Procedure
- Implementation Requirements
- Introduction
- Experimental Results
- Peer-to-peer Network Security Using Wireshark
- Summary
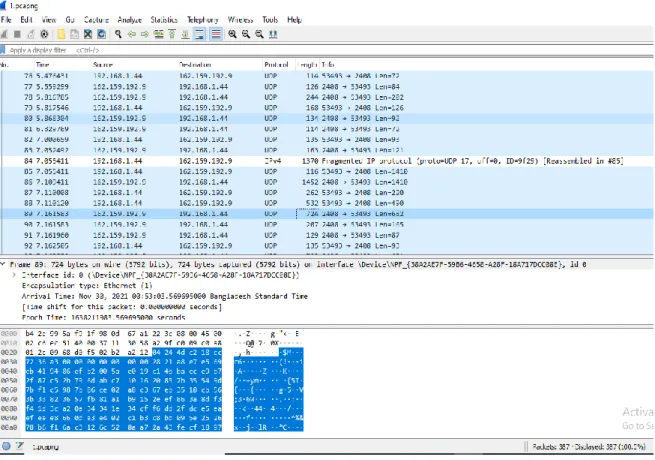
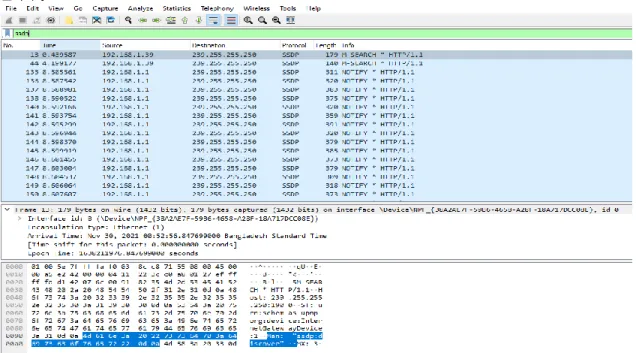
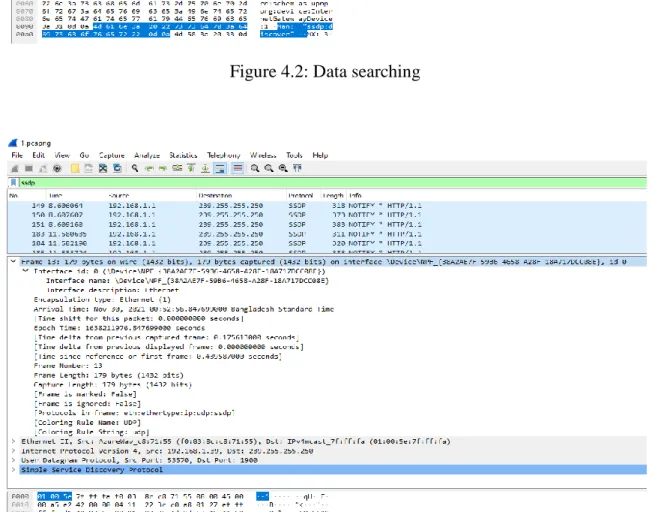
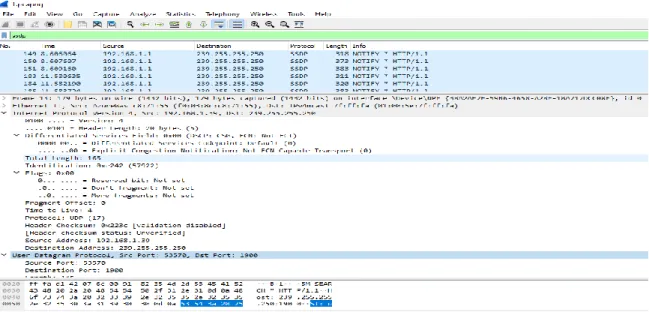
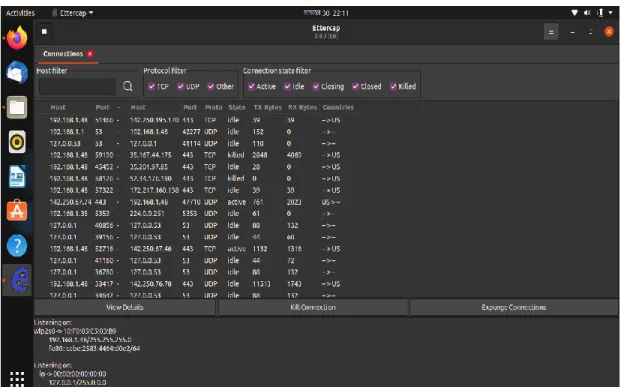
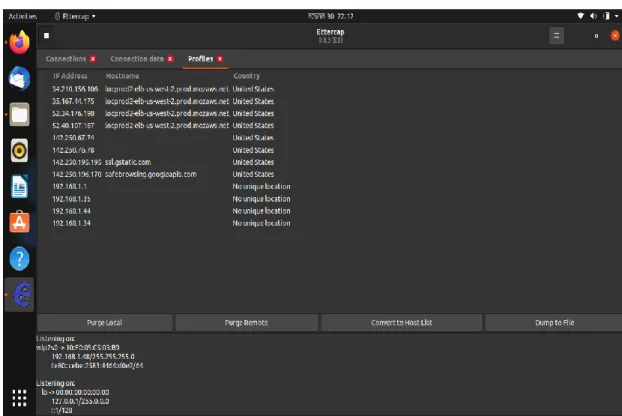
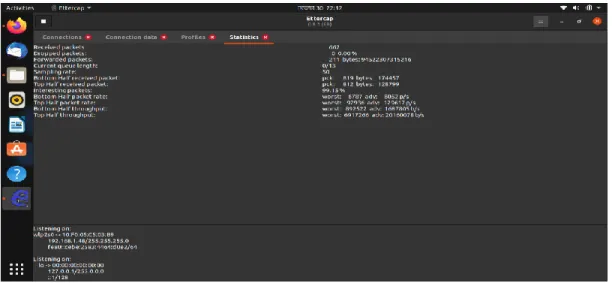
A packet sniffer captures (sniffs) packets from a computer, and stores and/or displays the information about the various protocol elements in these captured messages. Ettercap is a network security feature for LAN man-in-the-middle threats that is free and open source. As a result, it can act as a "man in the middle" and launch a variety of attacks on victims.
It is essential to have a thorough understanding of peer-to-peer networks in order to understand the security implications in a peer-to-peer environment. We need to know, for example, that security features are available in traditional client/server networks, but not in peer-to-peer networks. A client/server network is designed for small organizations or a small work group of individuals within a larger organization, while a peer-to-peer network is designed for small organizations or a small work group of people within a larger organization. big.
Although there is no set limit on the number of clients that can participate in a peer-to-peer network, the practical limit is 10. When a peer-to-peer network grows to more than 10 machines, performance and challenges administrative problems are likely to arise. This is due to the fact that a peer-to-peer network is intended to be the simplest type of network.
One of the most important pieces of information for a digital investigator is the identification of other people interested in the suspected file. Threats: Because peer-to-peer malicious threats still require access to the system's current workstation, user authentication can guard against the insider threat. Authentication, on the other hand, may not be the best way to be security in the future.
Network scanning and monitoring may become more desirable if peer-to-peer networks become standard in corporate and university computing infrastructures[30]. Such scanning is not straightforward since, by definition, peer-to-peer data transfer does not go through a central server, such as Amazon's server. Network scanning technologies such as Wireshark, as well as regular forensic analysis of collected data, can be helpful in preventing hostile threats from exploiting peer-to-peer data passing in and out businesses.
However, companies should be careful when choosing a peer-to-peer network architecture, as the Invisible Internet Project (I2P) paradigm will render network probing ineffective because all data is encrypted.
SUMMARIZATION OF THE STUDY AND CONCLUSION
Summary
Conclusion
To address these issues, Free Software Audit tools should be implemented as part of the security system process. Open Source audit tools can also be used to audit wireless networks in the academic sector such as universities, colleges and schools. Based on our findings, we recommend that all academic network administrators use PRTG and wireshark to analyze the Wi-Fi zone.
Lu, "Component-Based Security Control for Information Network," Proceedings of the Multi-Conference on "Computer Engineering in System Applications, p. Li, "Probability of Trojan Attacks on Multi-Level Security Strategy-Based Network, International Conference on Multimedia Information Networks and Security, 2010, p . Wang, “A Study of Rough Set and Clustering Algorithm in Network Security Management International Conference on Network Security, Wireless Communications and Trusted Computing, 2009, p.
Dong, "Research on Network Security Situation Prediction-Oriented Adaptive Learning Neuron Second International Conference on Network Security, Wireless Communications and Trusted Computing, 2010, pp. Data (Big Data), 2019, pp.