Ethical Hacking and
Counterm easures
Counterm easures
Version 6
Mo d u le LVII
Scenario
OrientRecruitm entInc is an online hum an resource recruitm ent firm .
The web server of the firm is a critical link.
Neo, the network adm inistrator sees som e unusual activity that is
targeted towards the web server. The web server is overloaded with a ge ed o a ds e eb se e e eb se e s o e oaded
connection requests from huge num ber of different sources.
Before he could realize the potential of the attack, the website of
O i tR it tI f ll t th h f D i l f
OrientRecruitm entInc falls prey to the m uch fam ous Denial of
Service Attack.
The com pany m anagem ent calls up the local Incident Response
Team to look into the m atter and solve the DoS issue.
What steps will the incident response team take to investigate the
Module Objective
This m odule will fam iliarize you with:
• Com puter Forensics
• What is an Incident
This m odule will fam iliarize you with:
• What is an Incident
• Categories of Incidents
• Incident Response Checklist
• Procedure for Handling Incident
g
• Incident Managem ent
• Incident Reporting
• What is CSIRT
• Types of Incidents and Level of Support
• Incident Specific Procedures
• Best Practices for Creating a CSIRT
W
ld CERT
Module Flow
Com puter Forensics Incident Reporting
What is CSIRT What is an Incident
Categories of Incidents Types of Incidents and Level of Support
Incident Response Checklist Incident Specific Procedures
Best Practices for Creating a CSIRT Procedure for
To Kn o w Mo re Ab o u t
To Kn o w Mo re Ab o u t
Co m p u te r Fo re n s ics ,
A
d EC C
il’ CH FI
Atte n d EC-Co u n cil’s CH FI
P ro gra m
C
t
F
i
What is Com puter Forensics
“The preservation, identification, extraction, interpretation, and
docum entation of com puter evidence to include the rules of evidence
docum entation of com puter evidence, to include the rules of evidence,
legal processes, integrity of evidence, factual reporting of the
inform ation found, and providing expert opinion in a court of law or
other legal and/ or adm inistrative proceeding as to what was found.”
"Forensic Com puting is the science of capturing, processing and
Need for Com puter Forensics
“Com puter forensics is equivalent of surveying a crim e scene or perform ing an
autopsy on a victim ”
p y
{Source: J am es Borek 20 0 1}
Presence of a m ajority of electronic docum ents
Presence of a m ajority of electronic docum ents
Search and identify data in a com puter
Search and identify data in a com puter
Digital Evidence can be easily destroyed if not handled properly
Digital Evidence can be easily destroyed, if not handled properly
Objectives of Com puter Forensics
To recover, analyze and present com
puter-To recover, analyze and present com puter
based m aterial in such a way that it can be
p re s e n te d a s e vid e n ce in a co u rt o f la w
Stages of Forensic Investigation in
Tracking Cyber Crim inals
Tracking Cyber Crim inals
An Incident occurs in Whi h h C ’
The Client contacts the C ’ Ad
The Advocate contracts E l F i Which, the Com pany’s
Server is com prom ised
Com pany’s Advocate for Legal Advice
an External Forensic Investigator
The Forensic Investigator Prepares First Response
of Procedures (FRP) The FI seizes the
evidences in the Crim e scene & transports them to the Forensics Lab The Forensic Investigator
(FI) prepares the Bit-Stream im ages of the files
The Forensic Investigator creates an MD5 #
of the files
The Forensic Investigator exam ines the evidence files for proof of a Crim e
The FI prepares Investigation reports and concludes the
Investigation, enables the Advocate identify required proofsdvocate de t y equ ed p oo s
The FI handles the sensitive Report to the The Advocate studies the
report and m ight press charges The Forensic Investigator
usually destroys sensitive Report to the
Key Steps in Forensic
Investigations
Investigations
1
• Com puter crim e is suspected2
• Collect prelim inary evidence3
• Obtain court warrant for seizure (if required)4
• Perform first responder procedures4
p p5
• Seize evidence at the crim e scene6
• Transport them to the forensic laboratoryKey Steps in Forensic
Investigations (cont’d)
Investigations (cont d)
8
• Generate MD5 checksum on the im ages9
• Prepare chain of custody10
• Store the original evidence in a secure location11
• Analyze the im age copy for evidence12
• Prepare a forensic report13
• Subm it the report to the clientI
id
H
dli
Present Networking Scenario
Increase in the num ber of com panies venturing into e-business
l d ith
hi h
I t
t
coupled with high Internet usage
Decrease in vendor product developm ent cycle and product
i
l
testing cycle
Increase in the com plexity of Internet as a network
Increase in the com plexity of Internet as a network
Alarm ing increase in intruder activities and tools, expertise of
g
,
p
hackers, and sophistication of hacks
What is an Incident
Com puter security incident is defined as “Any real or suspected adverse
event in relation to the security of com puter system s or com puter
event in relation to the security of com puter system s or com puter
networks”
• Source: www.cert.org
It also includes external threats such as gaining access to system s,
disrupting their services through m alicious spam m ing, execution of
m alicious codes that destroy or corrupt system s
Category of Incidents: Low Level
Low level incidents are the least severe kind of incidents
Low level incidents are the least severe kind of incidents
They should be handled within one working day after the event occurs
They should be handled within one working day after the event occurs
They can be identified when there is:
Loss of personal password
Suspected sharing of organization ’s accounts Suspected sharing of organization s accounts
Unsuccessful scans and probes
Category of Incidents: Mid Level
h i
id
hi l
l
i
l
i
d h
h
ld b
The incidents at this level are com paratively m ore serious and thus, should be
handled the sam e day the event occurs
• Violation of special access to a com puter or com puting
They can be identified by observing:
Violation of special access to a com puter or com puting facility
• Unfriendly em ployee term ination
• Unauthorized storing and processing data
• Destruction of property related to a com puter incident (less p p y p ( than $ 10 0 ,0 0 0 )
• Personal theft of data related to com puter incident($ 10 0 ,0 0 0 )
• Com puter virus or worm s of com paratively larger intensity Ill l t b ildi
Category of Incidents: High Level
These are the m ost serious incidents and are considered as “Major” in nature
High level incidents should be handled im m ediately after the incident occurs
These include:
• Denial of Service attacks
• Suspected com puter break-in
• Com puter virus or worm s of highest intensity; e.g. Trojan back door
back door
• Changes to system hardware, firm ware, or software without authentication
• Destruction of property exceeding $ 10 0 ,0 0 0
• Personal theft exceedin g $ 10 0 ,0 0 0 and illegal electronic g g fund transfer or download/ sale
How to Identify an Incident
A system alarm from an intrusion detection tool indicating security breach
Suspicious entries in a network
Accounting gaps of several m inutes with no accounting log
Other events like unsuccessful login attem pts, unexplained new user or files, attem pts to write s stem files m odification or deleting of data
system files, m odification, or deleting of data
How to Prevent an Incident
A key to preventing security incidents is to elim inate as m any vulnerabilities
ibl
as possible
Intrusions can be prevented by:
Intrusions can be prevented by:
• Scanning the network/ system for security loopholes
• Auditing the network/ system
• Deploying Intrusion Detection/ Prevention System s on the network/ system
• Establishing Defense-in-Depth
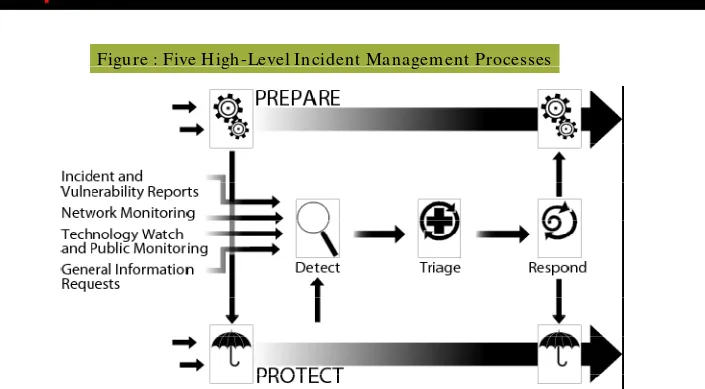
Defining the Relationship between Incident
Response, Incident Handling, and Incident
Managem ent
Incident Response Checklist
Potential Incident Verified
Contact departm ent/ agency security staff
• I.T. Manager
-• [designee/ others by departm ent procedure] -[ g / y p p ]
Security designee will contact CSIRT m em ber
• Call 8 0 2-250 -0 525 (GOVnet Beeper)
• GOVnet will then contact CSIRT m em bers ([email protected])( @ ) • If no response within ten m inutes call the Office of the CIO
Isolate system (s) from GOVnet [unless CSIRT decision is to leave the system connected to m onitor active hacker]
Begin a log book - who/ what / when / where
Identify the type of Incident - Virus, worm , and hacker
Incident Response Checklist
(cont’d)
(cont d)
Contact local police authority with jurisdiction at location of incident (This MUST BE coordinated with CSIRT)
Follow server/ operating system specific procedures to snapshot the system Inoculate/ restore the system
Inoculate/ restore the system
Close the vulnerability and ensure that all patches have been installed Return to norm al operations
Prepare report and conduct follow-up analysis Revise prevention and screening procedures
Handling Incidents
Incident handling helps to find out trends and patterns regarding intruder activity by analyzing it
intruder activity by analyzing it
It involves three basic functions:
• Incident reporting, • Incident analysis, and • Incident response
It recom m ends network adm inistrators for recovery, containm ent, and prevention to constituents
It ll i id t t t b th d i l ti th t t
It allows incident reports to be gathered in one location so that exact trends and pattern can be recognized and recom m ended strategies can be em ployed
I h l h di ff d d h f
Procedure for Handling Incident
The incident handling process is divided into six stages
These stages are:
• Preparation
• Identification
• Containm ent
E
di
ti
Stage 1: Preparation
Preparation enables easy coordination am on g staff
p
y
g
Create a policy
Develop preventive m easures to deal with threats
Obtain resources required to deal with incidents
effectively
Develop infrastructure to respond and support
Develop infrastructure to respond and support
activities related to incident response
Stage 2: Identification
Identification involves validating, identifying, and
reporting the incident
reporting the incident
Determ ining the sym ptom s given in ‘how to identify an
incident’
Identifying the nature of the incident
Identifying events
Stage 3: Containm ent
Containm ent lim its the extent and intensity of an incident
Containm ent lim its the extent and intensity of an incident
It avoids logging as root on the com prom ised system
It avoids logging as root on the com prom ised system
Avoid conventional m ethods to trace back as this m ay alert the
k
attackers
Perform the backup on the system to m aintain the current state of
the system for facilitating the post-m ortem and forensic
the system for facilitating the post-m ortem and forensic
investigation later
Stage 4: Eradication
Investigate further to uncover the cause of the incident by analyzing system logs
of various devices such as firewall, router, and host logs
Im prove defenses on target host such as:
• Reloading of a new operating systemReloading of a new operating system • Enabling firewalls
• Assigning new IP address
Install all the latest patches
Install all the latest patches
Disable any unnecessary services
Install anti-virus software
Stage 5: Recovery
Determ ine the course of actions
Determ ine the course of actions
Monitor and validate system s
y
Determ ine integrity of the backup itself by m aking an
attem pt to read its data
attem pt to read its data
Verify success of operation and norm al condition of system
Monitor the system by network loggers, system log files, and
potential back doors
Stage 6: Follow-up
Post-m ortem analysis:
• Perform a detailed investigation of the incident to identify the
extent of the incident and potential im pact prevention m echanism s
Revise policies and procedures from the lessons learned from the past
Determ ine the staff tim e required and
f th f ll i t l i
• Extent to which the incidents disrupted the organization • Data lost and its value
perform the following cost analysis:
Stage 6: Follow-up (cont’d)
Docum ent the response to incident by finding answers to the
following:
Was the preparation for the incident sufficient?
Whether the detection occurred prom ptly or not, and why?
Using additional tools could have helped or not? Using additional tools could have helped or not?
Was the incident contained?
What practical difficulties were encountered?
Incident Managem ent
Incident m anagem ent is not just responding to an incident when it happens but
includes proactive activities that help prevent incidents by providing guidance
includes proactive activities that help prevent incidents by providing guidance
against potential risks and threats
Includes the developm ent of a plan of action, a set of processes that are consistent,
p
p
,
p
,
repeatable, of high quality, m easurable, and understood within the constituency
Who perform s Incident Managem ent?
Hum an resource personnel
Legal council
Incident Managem ent (cont’d)
Why don’t Organizations Report
Com puter Crim es
Com puter Crim es
Misunderstanding the scope of the problem
• This does not happen to other organizations
Proactive reporting and handling of the incident will allow m any
organizations to put their spin on the m edia reports
Potential loss of custom ers
Desire to handle things internally
Estim ating Cost of an Incident
Tangible: Can be quantified
• Lost productivity hours
• Investigation and recovery efforts
L f b i
g
q
• Loss of business
• Loss or theft of resources
Intangible: More difficult to identify and
• Dam age to corporate reputation • Loss of goodwill
Intangible: More difficult to identify and
quantify
Loss of goodwill
• Psychological dam age
• Those directly im pacted m ay feel victim ized • May im pact m orale or initiate fear
• Legal liabilityLegal liability
Whom to Report an Incident
Incident reporting is the process of reporting the inform ation regarding p g p p g g g the encountered security breach in a proper form at
The incident should be reported to the CERT Coordination center, site security m anager, or other sites
It can also be reported to law enforcem ent agencies such as FBI,USSS Electronic crim es branch, or Departm ent of Defense Contractors
Incident Reporting
When a user encounters any breach, report the following:
Intensity the security breach
Circum stances, which revealed the vulnerability
Sh t i i th d i d i t l l f k Shortcom ings in the design and im pact or level of weakness
Entry logs related to intruder’s activity
Specific help needed should be clearly defined
Vulnerability Resources
US-CERT Vulnerability Notes Database:
• Descriptions of these vulnerabilities are available from this web page in a searchable database form at, and are published as "US-CERT Vulnerability Notes".
• Integrates all publicly available U.S. Governm ent vulnerability resources and provides references to industry resources
NVD (National Vulnerability Database):
• List or dictionary of publicly known in form ation security vulnerabilities and
l d f f bl
CVE (Com m on Vulnerabilities and Exposures List):
exposures international in scope an d free for public use
OVAL (Open Vulnerability Assessm ent Language):
What is CSIRT
Com puter Security Incident Response Team (CSIRT):
p
y
p
(
)
Incident Response Services 24x7
CSIRT provides 24x7 Com puter Security
Incident Response Services to any user,
com pany, governm ent agency or organization
CSIRT provides a reliable and trusted single
point of contact for reporting com puter
security incidents worldwide
security incidents worldwide
CSIRT provides the m eans for reporting
i
id
d f di
i
i
i
CSIRT: Goals and Strategy
CSIRT’s goals:
• To organize the m anagem ent of security problem s by taking a proactive approach to our custom ers’ security vulnerabilities and by responding effectively to potential inform ation security i id t
CS
s goa s:
incidents
• To m inim ize and control the dam age
• To provide or assist with effective response and recovery • To help prevent future events
• It provides a single point of contact for reporting local
Strategy of CSIRT:
t p o des a s g e po t o co tact o epo t g oca problem s
• It identifies and analyzes what has happened including the im pact and threat
• It researches solutions and m itigation strategiesg g
Why an Organization needs an
com puter security
b
h
d h
It is a form alized team
that perform s incident
response work as its
m ajor job function
As an ad-hoc team , it
is responsible for
ongoing com puter
CSIRT Case Classification
Types of Incidents and Level of
Support
The Com puter Security Incident Response Team will assign
resources according to the following priorities, listed in the
Support
• Threats to the physical safety of hum an beings
• Root or system -level attacks on an y m achine either m ulti-user or
dedicated-resources according to the following priorities, listed in the
decreasing order:
y y
purpose
• Com prom ise restricted confidential service accounts or software
installations, in particular those with authorized access to confidential data • Denial of service attacks on any of the above two item s e a o se v ce attac s o a y o t e above t o te s
• Large-scale attacks of any kind, e.g. sniffing attacks, IRC "social engineering" attacks, password cracking attacks, and destructive virus outbursts
• Com prom ise of individual user accounts, i.e. unauthorized access to a user or service account
service account
• Forgery and m isrepresentation, and other security-related violations of local rules and regulations, e.g. Netnews and e-m ail forgery, unauthorized use of IRC bots
Incident Specific Procedures-I
(Virus and Worm Incidents)
(Virus and Worm Incidents)
Step 1: Isolate the system
Step 2: Notify appropriate people
Step 3: Identify the problem
Step 4: Include the virus or worm
Step 5: Inoculate the system (s)
Step 6: Return to a norm al operating m ode
Incident Specific Procedures-II
(Hacker Incidents)
(Hacker Incidents)
(A) Attem pted Probes into a State of Verm ont System
• Step 1: Identify the problem
• Step 2: Notify appropriate people • Step 3: Identify the Hacker
• Step 4: Notify CERT
• Step 5: Follow up analysis • Step 5: Follow up analysis
• Step 1: Notify Appropriate People
(B) Active Hacker Activity
p y pp p p
• Option 1: Rem oval of Hacker from the system • Step 2: Snap-shot the System
• Step 3: Lock out the Hacker • Step 4: Restore the System • Step 5: Notify other Agencies • Step 5: Notify other Agencies • Step 6: Follow up Analysis
• Option 2: Monitoring of Hacker Activity
Incident Specific Procedures-III
(Social Incidents, Physical Incidents)
(Social Incidents, Physical Incidents)
Social Incidents:
• Step 1: Identify Potential Risk
• Log all actions*
• Step 2: Notify Appropriate People
Physical Incidents:
How CSIRT Handles Case: Steps
KEEP A LOG BOOK
INFORM THE
APPROPRIATE PEOPLE
MAINTAIN LIST OF CONTACTS
RELEASE THE INFORMATION
O FOLLOW UP ANALYSIS
Exam ple of CSIRT
In te rn a l CS IRT provides services to their parent organization such as
bank, m anufacturing com pany, university, or any governm ent agencies
N a tio n a l CS IRT provides services to the entire nation exam ple being
J apan Com puter Em ergency Response Team Coordination Center J apan Com puter Em ergency Response Team Coordination Center (J PCERT/ CC)
An a lys is Ce n te rs synthesize data, determ ine trends, and patterns in an
incident activity to predict future activity or provide early warnings
Ve n d o r te a m s identify vulnerabilities in software and hardware products
Ve n d o r te a m s identify vulnerabilities in software and hardware products
In cid e n ts Re s p o n s e P ro vid e rs offer services to paid clients
Best Practices for Creating a
CSIRT
CSIRT
1
• Obtain m anagem ent support and buy-in1
2
• Determ ine the CSIRT strategic plan3
• Gather relevant inform ation4
• Design the CSIRT vision4
5
• Com m unicate the CSIRT vision and operational plan6
• Begin CSIRT im plem entationStep 1: Obtain Managem ent
Support and Buy-in
Support and Buy in
Without m anagem ent approval and support, creating an
effective incident response capability can be extrem ely difficult
and problem atic
Once the team is established, how is it m aintained and
d d ith b d
t
l d q i
t
?
expanded with budget, personnel, and equipm ent resources?
Step 2: Determ ine the CSIRT
Developm ent Strategic Plan
Developm ent Strategic Plan
Are there specific tim efram es to be m et? Are they realistic, and if
p
y
,
not, can they be changed?
Is there a project group? Where do the group m em bers com e from ?
How do you let the organization know about the developm ent of the
CSIRT?
If you have a project team , how do you record and com m unicate the
inform ation you are collecting, especially if the team is
hi
ll di
d?
Step 3: Gather Relevant
Inform ation
Inform ation
Meet with key stakeholders to discuss the expectations, strategic direction,
definitions, and responsibilities of the CSIRT
i
The stakeholders could include:
• Business m anagers
• Representatives from IT
• Representatives from the legal departm ent
• Representatives from hum an resources
Representatives from hum an resources
• Representatives from public relations
Step 4: Design your CSIRT
Vision
Vision
In creating your vision you should:
• Identify your constituency: Who does the CSIRT support and service?
• Define your CSIRT m ission, goals, and objectives: What does the CSIRT do
In creating your vision, you should:
y , g , j
for the identified constituency?
• Select the CSIRT services to provide to the constituency (or others): How does the CSIRT support its m ission?
• Determ ine the organizational m odel: How is the CSIRT structured and g organized?
• Identify required resources: What staff, equipm ent, and infrastructure is needed to operate the CSIRT?
Step 5: Com m unicate the CSIRT
Vision
Vision
Com m unicate the CSIRT vision
Com m unicate the CSIRT vision
and operational plan to
m anagem ent, constituency, and
others who need to know and
understand its operations
Step 6: Begin CSIRT
Im plem entation
Im plem entation
Hire and train initial CSIRT staff Hire and train initial CSIRT staff
Buy equipm ent and build any necessary network infrastructure to support y q p y y pp the team
Develop the initial set of CSIRT policies and procedures to support your Develop the initial set of CSIRT policies and procedures to support your services
D fi h ifi i f d b ild i id ki
Define the specifications for and build your incident-tracking system
Step 7: Announce the CSIRT
When the CSIRT is operational, announce it to the
constituency or parent organization
It is best if this announcem ent com es from sponsoring
m anagem ent
Include the contact inform ation and hours of operation for the
CSIRT in the announcem ent
World CERTs
http:/ / www.trusted-introducer.nl/ team s/ country.htm l
http:/ / www.trusted introducer.nl/ team s/ country.htm l
Asia Pacific CERTs
• Australia CERT (AUSCERT) • Hong Kong CERT (HKCERT/ CC) • Indonesian CSIRT (ID-CERT) • J apan CERT-CC (J PCERT/ CC)p / • Korea CERT (CERT-KR)
• Malaysia CERT (MyCERT) • Pakistan CERT(PakCERT) • Singapore CERT (SingCERT) • Taiwan CERT (TWCERT) • Taiwan CERT (TWCERT) • China CERT (CNCERT/ CC)
North Am erican CERTs
• CERT-CC • US-CERT • Canadian Cert • CancertCancert
World CERTs (cont’d)
South Am erican CERTs
• CAIS
IRTs Around the World
f / Courtesy of CERT/ CC