RESEARCH ARTICLE
Enhanced Route Discovery Mechanism of Ad-Hoc
On Demand Distance Vector for MANET
May Sayed A. Nouh
Electronics & Communications Department, Faculty of Engineering, Ain Shams University, Cairo, Egypt.
[email protected]
Salwa H. El-ramly
Electronics & Communications Department, Faculty of Engineering, Ain Shams University, Cairo, Egypt.
[email protected]
M. Zaki
Computers and Systems Department, Faculty of Engineering, Al Azhar University, Cairo, Egypt.
[email protected]
Husein A.A Elsayed
Electronics & Communications Department, Faculty of Engineering, Ain Shams University Cairo, Egypt.
[email protected]
Published Online: 15 November 2016
Abstract – The Ad-hoc On Demand Distance Vector (AODV) is one of the most famed reactive routing protocols, which is used in Mobile Ad Hoc Networks (MANETs) for routing purposes, where the routes are built only when it is required. The AODV is related to the problem of route constructing and maintaining among any two-node in the presence of the dynamic topology of a network. High routing control packets, during route construction, is a limiting factor of AODV. Also, the route created during route discovery process may not be optimum (in terms of the number of hop counts between the originating and target node). The construction of non-optimal route arises from many reasons such as temporary congestion of one or more links in the short path to the target node, or nodes in those paths may contend the channel late, or the nodes may be busy for that moment to entertain other engagement. Moreover, during the route discovery phase, a large amount of unnecessary control packets may be generated which result in the debasement of the performance and the efficiency of the protocol by congesting the network and increasing the overhead. In this article the cases at which non-ideal routes are created and unimportant control packets generated during route discovery process will be identified. The modified AODV (AODV_MOD) with enhanced route discovery mechanism is proposed that will be used to avoid these cases by suppressing unimportant control packets and avoiding non-ideal routes formation. Simulation results, conducted in network simulator (NS2), prove the skillfulness of the proposed enhanced route discovery scheme from point of view of packet delivery ratio, end-to-end delay, and normalized overhead.
Index Terms – Overhear, AODV, DSR, DSDV, RREQ, RREP, Broadcast, Collision and Overhear.
1. INTRODUCTION
"Mobile Ad hoc Network" is a wireless network, in which the nodes are allowed to move freely in any direction. Due to the node mobility, a node can insert or depart the network at any time. If the two communicating nodes are within the same area of their transmission range, the routing is not needed. Otherwise, other intermediate nodes are required to realize the function of routers to set up a route in a hop-by-hop manner between the two nodes [1, 2]. The aim of a routing algorithm is to specify a procedure to transfer a data packet from the originating to target node. To make correct routing decision, the routing algorithm must select some criteria for making routing decision, (e.g., bandwidth, number of hop counts, transmission power, etc.)
Due to the nodes mobility, the exchanged routing information between nodes should be modified to reflect changes in network topology, so the conventional routing algorithms of the wired/wireless networks cannot be used directly in MANET. There are different algorithms to follow up the variability of topology of network and to rediscover new routes when the old routes fail. MANET has two fundamental sorts of
"routing protocols": “Proactive routing protocols”, and “Reactive routing protocols” [3-6]. “Proactive routing
protocols” (e.g. , “DSDV” and “OLSR”), also called “table driven” routing protocols, in which the routing information
RESEARCH ARTICLE
contrast, in "reactive routing protocols" (e.g., "AODV" and
"DSR"), also called "on demand routing protocols”, instead of
exchanging routing information among nodes at regular intervals, the route establishing solely in case of being needed.
”Reactive routing protocols” shun the cost of routes
maintenance which are not being used and also never send excessive control packets. Therefore, "reactive routing protocols" do well than "proactive routing protocols".
"Ad hoc On Demand Distance Vector (AODV)" is an efficient reactive scheme for routing purpose [7]. It depends on the hops
style. For route discovery, “AODV” uses only two guidance packets, “Route Request packet (RREQ)” and “Route Reply packet (RREP)”. To establish route between any two nodes,
"RREQ" is sent from the originating node. When "RREQ" reaches the target node, it answers by transmitting "RREP" to originator to confirm the establishment of the route.
AODV protocol has some advantages such as the route creation
is "on demand" and the usage of “destination sequence number”, as time stamp, for getting most recent route to the
target node. Moreover, for route maintenance, the hello packets are used and they do not cause significant unimportant control packets in the network because they are range limited. The disadvantage of AODV protocol is the heavy control packets due to the flooding of RREQ packet and multiple unnecessary RREP packets for responding to a single RREQ packet during the route discovery phase [8]. Also, the selected route may not be optimum (in terms of hops number between the originator and target).
This article aims to signify the cases at which non-ideal routes are created and unimportant RREP is generated during route discovery process in AODV and to propose and test a solution that will be used to avoid or to eliminate these cases by suppressing unimportant RREPs and avoid non-ideal routes that are to occur.
The remaining structure of the article is as follow: In Section 2, the related work of various routing methods has been discussed. The AODV protocol is briefly reviewed in Section 3. Then Section 4 reports the cases at which non-ideal routes are created and unimportant RREP is generated during route discovery process in AODV. The proposed technique for suppressing unimportant route reply (RREP) packets and avoiding non-ideal route creation is presented in Section 5. In Section 6, the simulation environment and performance metrics are given. The simulation results and analysis are then presented in Section 7. Finally, we conclude the paper in Section 8.
2. RELATED WORK
P. Wannawilai and C. Sathitwiriyawong [9] introduced new scheme, called (AODV-SBA). Where, routes are being discovered by the method that shuns congestion and
minimizing extravagant routing overheads. The idea of suggested scheme is based on measuring congestion of local network by using information from the MAC sub-layer. Hence, precluding the congested routes from being discovered. So, the proposed technique improves the performance of a high congested network
A. Abu-Ein and J. Nader [10] proposed a modified version of the original AODV, called (PH-AODV) routing protocol. Where, route selection is based on two factors: the power level of node and the hops number. So that, selected route should consist of relatively minimum hops number and the nodes forming the route must have high power level. Hence, performance of suggested scheme does well off the original "AODV" from point of view of "end-to-end delay", "packets dropping" and "throughput".
Julith Jacob and Shinu Koyakutty [11] presented a novel algorithm, named "Nominated Neighbors to Rebroadcast the RREQ (NNRR)", to minimize the surplus of "RREQ packets" during "route discovery". The proposed algorithm depends on the information of the location of the nodes inside the network. To limit the route discovery area, the proposed algorithm chooses four neighboring nodes as elected nodes to rebroadcast the "RREQ packet" in case of these nodes have not available path to the target node and applies the idea of "expected and requested zone" of "LAR protocol". The developed algorithm results in reduction of the "routing control packets".
Priyaganga G. and Madhumita C. [12], introduced a novel algorithm to reduce routing overhead in MANET. The proposed technique permits the intermediate node to rebroadcast the RREQ based on a newly computed factor, called efficient rebroadcast delay, DR. This factor is a function
of three network parameters, link quality (in terms of S/N ratio) between the nodes, energy level and routing load at each node. Hence, the node efficiency is determined according to the value of its rebroadcast delay, which is located between 0 and 1. If 0<DR<1, then the intermediate re-broadcast (RREQ).
Otherwise discard (RREQ). The proposed algorithm results in the discovery of reliable and stable route with minimum routing load.
3. AD-HOC ON-DEMAND DISTANCE VECTOR (AODV)
“AODV” is “reactive routing protocol” [7, 13, and 14].
Therefore, routes are established only when it is required (i.e.,
on demand). “AODV” composed of 2- stage: “route discovery”
and “route maintenance”.
RESEARCH ARTICLE
originator in its route cache. Among RREQ fields, "originator address", "broadcast ID" and "destination sequence number" which an originating node knows it [15-17]. When the first "RREQ" reaches any intermediate node does not possess valid route to the target node. It rebroadcast the "RREQ". Based on the "originator address" and "broadcast ID", nodes can avoid duplication of receiving the same "RREQ". If nodes received
the same “RREQ” two times, the later comer will be discarded
and do not resend it. On the other hand, when the "RREQ" reaches the target node or any intermediate node has valid route to the target node, it transmits "RREP packet", by using the hops style, to the originating node. During journey of "RREP" to the originating node, each intermediate node creates "forward path" to the target node. When the "RREP" reaches the originating node, it stores the route to the target node in the route cache and can begin sending the "data packets" to the target node. If multiple "RREP packets" received by the originating node, the route which have smallest hops number will be selected.
During "data packets" transmission, if link has been failed, the predecessor node from the failed link transmits "Route Error packet (RERR)" to the originating node by hops style. During journey of the "RERR packet" to the originating node, each intermediate node upstream of the failed link disproves routes to any unreachable target node. On receiving "RERR packet", the originating node rejects the failed route from route cache and restarts again "route discovery process".
4. NON-IDEAL ROUTE FORMATION AND UNNECESSARY RREPS GENERATION This section presents the analysis of the problem of non-optimal route discovery in AODV and generation of
unimportant RREPs by taking “Route Request” cycle and “Route Reply” cycle separately.
4.1.Route Request Cycle
In the route discovery process, each node keeps track of "RREQ packets" it has been received, this will help to discard duplicates received from different neighbor nodes. To detect duplication, the nodes use "originator address" and "broadcast
ID" of the “RREQ packet”. If nodes receive “RREQ” more
than one, it will drop late comer whatever hop-count it has.
However, “RREQ” with the smaller number of hop- count may arrive late due to temporary link congestion, channel access
and collision at that time. As a result, “RREQ” which passes
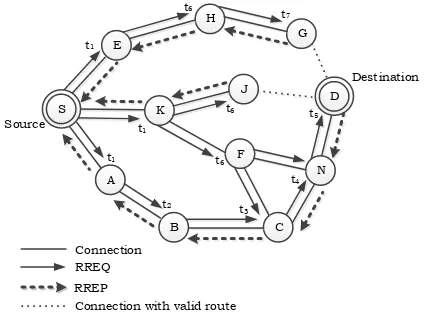
through less number of hops may be dropped because of its late arrival. Thus, a longer (non-ideal) path may be taken as a path for routing the data to the target node. This situation is illustrated, as an example, as shown in Figure 1. When node "S" has the desire to make up communication with node "D". It investigates its "route cache", if it does not found valid route to node "D", then node "S" starts the "route discovery process", by transmitting "RREQ packet" to neighboring nodes (A, E,
K). On receiving the "RREQ" at time t1, assume that the nodes
E and K are busy or the links K-F, K-J, and E-H are temporarily congested or collision occurs in these links. This will results in arriving three "RREQ packets" to the target node "D" at different times. The first one at time t5 through the path
<S-A-B-C-N-D>, the second one at time t7 through the path
<S-K-J-D> and the third one at time t9 through the path
<S-E-H-G-D>. On receiving the first “RREQ” at time t5, target node "D"
immediately transmits "Route Reply (RREP) packet", with hops number =5, to the originating node "S" through the path < D-N-C-B-A-S>, which is not the optimal path/route. And the
other two “RREQs”, which are lately arrived, will be neglected
by node "D". Therefore, the optimal route, with hops number = 3, through <S-K-J-D> does not taken as route between node "S" and "D", but the non-optimal route, < S-A-B-C-N-D>, is selected as route between node "S" and "D".
We have proposed an algorithm that considers all RREQs irrespective of their arrival time at a node and decides based on both the hop-count and “destination sequence number” before dropping a lately arrived RREQ. By considering hop-count, we may avoid the formation of a longer path as a route. The detail of thealgorithm is discussed successively.
Figure1 Non-Optimal Route Formation 4.2.Route Reply Cycle
The second phenomenon that we have observed is the propagation of ineffective RREPs through the network. This happens in some situations at which RREPs generated by intermediate nodes and/or target nodes pass through more hops than other RREPs to reach to the originating node of the respective RREQ, which are dropped by the originator on their arrival based on the comparison of their hop-count. This can be illustrated, as an example, as shown in Figure 2. Whenever node "S" initiates the "route discovery process" by flooding "RREQ packet", it will propagate through network till it arrives to the intermediate node "J" and "G" as well as the target node "D". Assume that each one of intermediate nodes J and G has valid route to the target node "D". On receiving "RREQ packet" at time t6, node "J" sends "RREP packet" to the originating
node "S" through path <J-K-S>, with hop count = 3, at time t5
RESEARCH ARTICLE
node "D" sends "RRPE packet" through path <D-N-C-B-A-S>, with hop count = 5 and at time t7 node "G" sends "RRPE
packet" through path <G-H-E-S>, with hop count = 4. On
receiving these three “RREPs”, the originating node "S" elects
the "RREP" of the minimum hops count, (i.e. "RREP" of node
“J”, with hops count = 3, through path <J-K-S>). The other two
"RREPs" of “G” and “D” will be dropped on their arrival at the
originating node "S" where, they contain larger hops count. However, these two "RREPs" were flooded the network to reach to the target node "S", so this may increase the "routing overhead" and congest the network unnecessarily which will not result in route to the required target. They might even cause long route to occur which is taken as route between the two nodes if the "RREP" following the short path is dropped due to collision or other. Problem of the unnecessary "RREPs" will have significant drawback in case of high- density "Ad-hoc network". Solution for the stated problem is also added in the proposed algorithm which is discussed in the following section.
Figure 2 Generation of Unnecessary RREP 5. AODV WITH ENHANCED ROUTE DISCOVERY
MECHANISM
Based on the above-mentioned problems, we have proposed a solution that may helpful to enhance the route discovery mechanism. The proposed solution is based on two main ideas. The first one is based on the concept of Overhear RREP packet [18-20], which is the feature of DSR routing protocol used by a node to learn more routes from RREP packets that are not directed to it by promiscuous listing. The second idea is that all the RREQs should be processed and evaluated by a node irrespective of their arrival time. The proposed solution is discussed in the following two cases:
5.1.Non - Optimal Route Suppression
For the case at which non-optimal route is to occur, we have proposed an algorithm that may suppress the non-optimal route which is to be built, so that optimal route can be formed. This can be achieved by processing and evaluating all the received
RREQs, irrespective of their arrival time, at all nodes instead of dropping the late coming RREQ received after the first RREQ. Based on the hop-count, Nodes are allowed to perform a comparison between the current received RREQ with the previously received one in addition to the comparison of
“destination sequence number”. The result of the comparison
is used in deciding for further broadcasting, replying or
dropping the “RREQ” according to the following rules, as
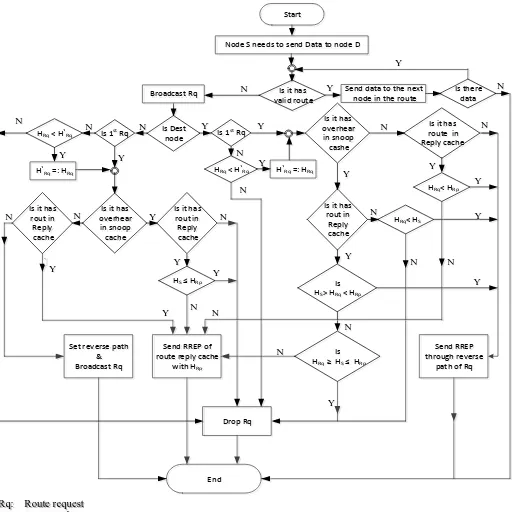
illustrated in Figure 3.
5.1.1. In Case of Intermediate Node
Whenever "RREQ" has been received by intermediate node for first time, it should obey the following rules:
1- If the received RREQ has Overhear RREP, (with hop-count HS), in the Snoop Cache and RREP, (with hop- count
HRP), in the Route Cache. If HS <= HRP, then the RREQ
is dropped.
2- If the received RREQ has only Overhear RREP, then the RREQ is dropped.
3- If there is no Overhear RREP or HRP < HS, then the node
sends RREP with hop count HRP.
4- If there is neither Overhear RREP nor RREP, then the node attaches its address in "route record" of RREQ, and rebroadcast RREQ.
When the current received RREQ is not the first one has less hop-count (HRQ) than the previously received RREQ (HʹRQ),
then the node repeats the above steps form1 to 4. Otherwise, the late comer will be dropped by the node.
5.1.2. In Case of Target Node
When “RREQ” has been received by the target node for first
time, it should obey the following rules:
1- If there is neither Overhear RREP nor “RREP”, then the
target node transmits “RREP” through reverse path of the
received RREQ.
2- If there is only RREP, (with hop-count HRP), in the Route
Cache. If HRQ < HRP, then destination node sends RREP
through the reverse path of the received RREQ. Otherwise, the node sends RREP with hop counts HRP.
3- If there is only Overhear RREP, (with hop-count HS), in the
Snoop Cache. If HRQ < HS, then destination node sends
RREP through the reverse path of the received RREQ. Otherwise, the node drops RREQ.
If the received RREQ has Overhear RREP, (with hop-count HS), in the Snoop Cache and RREP, (with hop-count HRP), in
the Route Cache. If HS > HRQ < HRP, then the target node sends
RREP through the reverse path of the received RREQ. Else if HRQ >= HS <= HRP, then the RREQ is dropped. Otherwise, the
RESEARCH ARTICLE
Figure 3. Flow Chart that Shows Action of Node on Receiving Route Request Packet
Start
Node S needs to send Data to node D
Is it has vali d route Broadcast Rq
Is Dest
node Is 1
st
Rq
Is it has overhear in snoop cashe
Is it has route in Reply cache
Send RREP through reverse
path of Rq Is 1st Rq
HRq < H`Rq
H`Rq =: HRq
Is it has overhear in snoop cache Is it has
rout in Reply cache
Is it has rout in Reply cache
HRq < H`Rq
HS HRp
Is it has rout in Reply cache
Is HS> HRq < HRp
Is HRq HS HRp
HRq< HRp
HRq< HS
H`Rq =: HRq
Set reverse path & Broadcast Rq
Send RREP of route reply cache
with HRp
End
Send data to the next node in the route
Is there data
`
Rq: Route request Rp: Route reply
HRq: Hop count in the current Rq H`
Rq: Hop count in the previous Rq
HRp: Hop count in Rp
Hs: Hop count in snoop cache (overhear)
Y N
Y
Y
Y
Y Y
Y Y
Y
Y Y
Y Y Y
Y Y
Y
Y N
N
N
N N
N N
N
N N
N
N N
N
N N
Y
N N
RESEARCH ARTICLE
Figure 4 Flow Chart That Shows Action of Nodes on Receiving Overhear Route Reply
Figure 5 Flow Chart That Shows Action of Nodes on Receiving Route Reply
N N
Y Y
Y Start
Overheard RREP
Is 1st
one
Is it Has route reply
in Reply Cac he Store in Snoop Cache
HS<HʹS
HʹS =: HS
Drop Overhear
RREP
Hs≤ HRp
End
HRp : Hop count of rout reply in reply c ache
HS : Hop count in the current ove rhear reply HʹS : Hop count in the pre vious overhear re ply
N
Y N
Start
Receive RREP
Is 1st one
Is it Has overheard reply in Snoop Cache
Store in Reply Cache and Forward It HRp<HʹRp
HʹRp =: HRp
Drop
RREP HRp< Hs
End
HRp : Hop count in current RREP HʹRp : Hop count in previous RREP
HS : Hop count in snoop cache (overhe ard)
Y N
Y Y
Y
N
RESEARCH ARTICLE
5.2.Unnecessary Route Reply Suppression
The unnecessary Route Reply Suppression is handled by adding a feature to AODV nodes so as to Overhear RREP packet that is not directed to it. In the proposed algorithm, the Overheard RREP is examined for further processing. To facilitate the searching and comparison in the Route Cache and Snoop Cache, we have included additional information in the
“RREP packet” such as “broadcast ID” of the respective “RREQ”, total hops number among the originator and target
node, and originator address that will help to determine further processing. On hearing RREP by a node (i.e. RREP not directed to a node), it obeys the following rules, as shown in Figure 4.
1- If Overheard RREP, with hop-count HS, is the first one and
there is no RREP in the Reply Cache for the same required route, then the Overheard RREP is stored in Snoop Cache. In the case of there is RREP in the Reply Cache with hop count HRP and HS < HRP, then also the Overheard RREP is
stored in Snoop Cache. Otherwise, if HS > HRP, then the
Overheard RREP is dropped.
2- If the current Overheard RREP is not the first one has less hop-count HS than the previously received one with HʹS,
then the node repeats step1. Otherwise, the node drops the late comer.
In the case of receiving RREP by a node (i.e. RREP directed to a node), it obeys the same above two steps, as shown in Figure 5.
6. SIMULATION ENVIRONMENT 6.1. Simulation Model
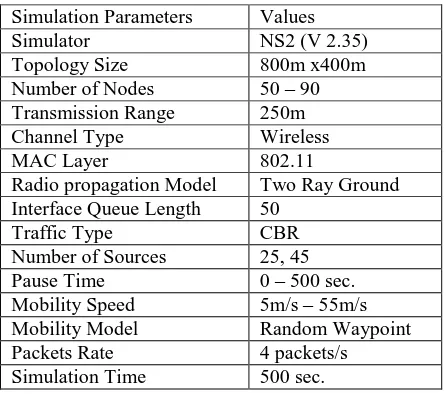
Table 1: Simulation Parameters
To test and evaluate the performance of the proposed scheme, we used simulation system, named NS2. AWK command has
been used to analyze the experimental results contained in the generated output trace files. The traffic sources that we have used are Continuous Bit Rate (CBR). Node mobility
description is based on the "random waypoint model”. The pause time is varied from 0 to 500 second. A pause time 0 sec. means the nodes are continuously in motion and pause time 500 sec. means nodes are stationary. Table 1 illustrates the simulation parameters.
6.2.Performance Metrics
The performance comparison of suggested algorithm (AODV_MOD) against the standard “AODV” have been carried
out under the same conditions, such as identical mobility and traffic scenarios. To evaluate the two algorithms in all important aspects, the following three performance metrics have been used.
1. “Packet Delivery Fraction” (PDF): It is the ratio of number
of received data packets at the target node to the number of data packets transmitted from the originating node. Where, high PDF meets good performance.
2. “Average End-to-End Delay”: it is the consumed average
time during journey of data packets from the originating node to the target node. It involves "processing time", "waiting time" and "propagation delay". Where, minimum
“end-to-end delay” meets better performance.
“Normalized Routing Overhead”: It is the ratio of sum of all
transmitted routing packets to the sum of all data packets
delivered to the target. Where, minimum “Normalized Routing Overhead” ratio meets better performance.
7. SIMULATION RESULTS AND ANALYSIS The following scenarios have been taken into consideration to compare the simulation results of the proposed AODV_MOD
and the original AODV, based on the aforementioned performance metrics.
7.1.Scenario 1:
In this scenario, the pause time of nodes is changed from 0 to 500 sec. The number of nodes and source connections is fixed at 50 and 25 respectively, node speed is fixed at 5 m/s and the other network parameters are considered as in Table1. 7.1.1. Packet Delivery Fraction
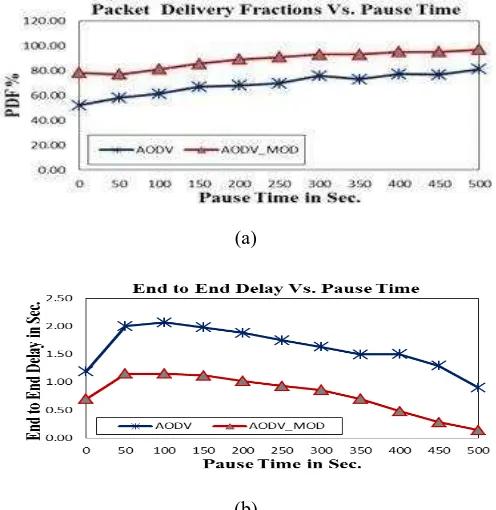
Figure 6.a shows PDF versus pause time for the studied protocols. It is clearly seen from the graph that as the pause time increases, the PDF of both protocols increases because the network becomes stable since the routes are stable and valid for a long time. On the other hand, lower pause time (i.e., nodes have higher mobility) results in lower PDF due to the increase of packet drops, since the routes are unstable. The AODV_MOD
has a higher delivery ratio, where the average PDF=88.63%, than the original AODV, where the average PDF=69.09%, this Simulation Parameters Values
Simulator NS2 (V 2.35) Topology Size 800m x400m Number of Nodes 50 – 90 Transmission Range 250m Channel Type Wireless MAC Layer 802.11
Radio propagation Model Two Ray Ground Interface Queue Length 50
RESEARCH ARTICLE
is due to the enhanced route discovery mechanism. In general, the large route length leads to the high probability of packets drop. The AODV_MOD can create shorter route length, which
result in the improvement of PDF. For the same reason, the improvement of PDF of AODV_MOD is more observable in a
high dynamic network.
7.1.2. Average End-to-End Delay
Figure 6.b illustrates the “end-to-end delay” of the two routing protocols. We note that, the delay time for both protocols decreases with increasing the pause time because as the mobility decreases the network becomes stable and the routes are available for long periods. The AODV_MODhas lower “end
-to-end delay”, where the average delay=0.77sec, than the original AODV, where the average delay= 1.61sec. This is because the enhanced route discovery mechanism can create shorter route than that taken by the original AODV, which
results in reduction of the “end-to-end delay”. 7.1.3. Normalized Routing Overhead
Normalized routing overhead versus pause time for the studied protocols is shown in Figure 6.c. We note that, as the mobility of nodes increases (i.e., at low pause time), the possibility of link failure increases and hence, the routing overhead increases, due to the rediscovery of the route, in the two protocols. The routing overhead of AODV_MOD, (Avg.
NRL=1.18), is lower than the original AODV, (Avg. NRL=1.18), because the enhanced route discovery mechanism can avoid unnecessary route reply packets from flooding the network.
(a)
(b)
(c)
Figure 6. Varying Network Pause Time 7.2.Scenario 2
Effect of node speed on performance of the AODV and AODV_MOD is addressed in this scenario. The nodes speed is
varied between 5m/sec and 55m/sec. The nodes number and source connections are fixed at 50 and 25 respectively, pause time is fixed at 5 sec. and the other network parameters are listed in Table1.
7.2.1. Packet Delivery Fraction (PDF)
Figure 7.a shows the packet delivery fraction against nodes speed of the AODV and AODV_MOD. PDF for both two
protocols decreases as the mobility speed increases, because at high speeds, possibility of link failure may occur more recurrently and therefore the PDF is decreased. The AODV_MOD has a higher delivery ratio under the same node
speed due to the enhanced route discovery mechanism, where the ideal (shorter) route is selected.
7.2.2. Average End-to-End Delay
Figure 7.b illustrates the "average end-to-end delay" versus nodes speed of the AODV and AODV_MOD. We observe that, the average delay of both two protocols increases as the mobility speed increases. This due to, the frequent changing of network topology results in high probability of links failure which in turns may lead to extra "route discovery process", so the average delay have been increased. Also, we note that, in case of dynamic topology, the AODV_MOD has better performance than "AODV" because the proposed scheme can create shorter path than that taken by the original AODV, which leads to reduction of the "end-to-end delay".
7.2.3. Normalized Routing Overhead
RESEARCH ARTICLE
AODV_MOD, (Avg. NRL= 3.01), is lower than the original
AODV, (Avg. NRL= 4.14), because it suppresses unnecessary route reply packets from flooding the network.
(a)
(b)
(c)
Figure 7 Varying Network Mobility Speed 7.3.Scenario 3
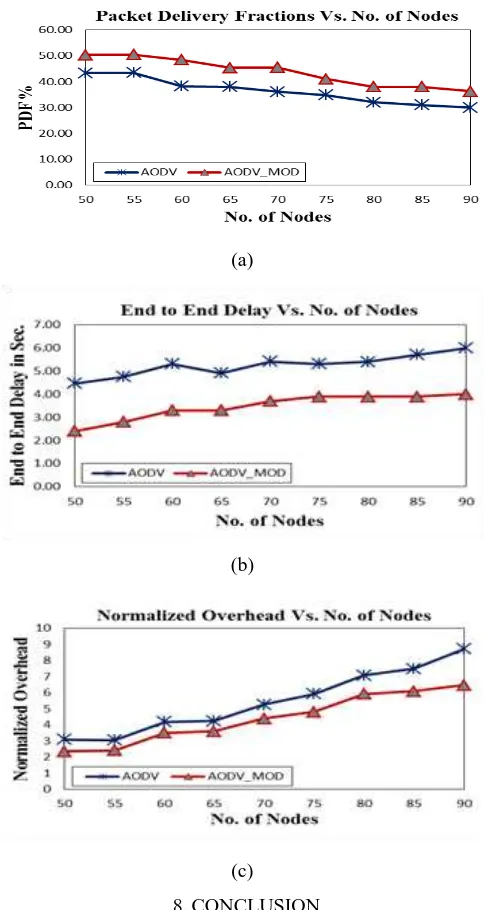
The effect of nodes density on performance of the two routing protocols is addressed in this scenario. We have varied the number of nodes from 50 to 90 with step 5, keeping the pause time to be 5 sec, node speed is 10m/s and number of source connections is 45. Other parameters remain fixed as shown in Table 1.
As shown in Figure 8, as the nodes density increases, the coinciding packets from various originating nodes may have
higher likelihood in channel contention at the same intermediate nodes, which results in lower packet delivery ratio, higher delay and higher normalized overhead. The AODV_MOD has better performance than AODV because the enhanced route discovery mechanism can avoid the unnecessary control packets and create shorter route than that taken by the original AODV under the same number of nodes,
which is useful to improve the “packet delivery ratio, diminish the “end-to-end delay” and control packets.
(a)
(b)
(c) 8.CONCLUSION
RESEARCH ARTICLE
formation and the second one, suppression of unimportant control packets. And it is compared with the original "AODV", for different scenarios, in terms of "packets delivery fraction", "end-to-end delay" and "normalized routing overhead". It is observed that, the AODV_MOD has better performance than the original "AODV".
REFERENCES
[1] Schiller J.,”Mobile Communications”, Addison Wesley, 2nd edition, 2003.
[2] Ravneet kaur, Dr.Neeraj Sharma, “Dynamic node recovery in MANET for high recovery probability”, International Journal of Computer Networks and Applications (IJCNA), Vol 2, Issue 4, July - August 2015. [3] Shaheen Khan, Javed Khan Bhutto and Gautam Pandit,”Reactive and Proactive Routing Protocol Performance Evaluation for Quantitative Analysis in MANET”, International Journal of Scientific Research and Education, Vol. 2, Issue12, pp: 2540-2551, December 2014.
[4] Chandni, Sharad Chauhan and Kamal Kumar Sharma,”Routing Protocol in MANET – A Survey”, International Journal of Recent Research Aspects, Vol.1, Issue 2, pp: 48-52, September 2014.
[5] Rajeshwar Sharma, Tarun Sharma and Aditi Kalia ,”A Comparative Review on Routing Protocols in MANET”, International Journal of Computer Applications, Vol. 133, No.1, January 2016.
[6] Saima Zafar, Hina Tariq, Kanza Manzoor,” Throughput and Delay Analysis of AODV, DSDV and DSR Routing Protocols in Mobile Ad Hoc Networks,” International Journal of Computer Networks and Applications (IJCNA) ,Vol. 3, Issue 2, March – April 2016.
[7] C. Perkins, E. Belding Royer and S. Das,”Ad-Hoc On Demand Distance Vector (AODV) Routing”, rfc 3561, July 2003.
[8] Vinayak Bashetti, Sayed Abdulhayan,” A Cost Effective Flooding Algorithm for AODV Routing Protocol in Mobile Ad Hoc Network”, International Journal of Advanced Research in Computer and Communication Engineering, Vol. 5, Issue 1, January 2016.
[9] P. Wannawilai and C. Sathitwiriyawong ,“AODV with Sufficient Bandwidth Aware Routing Protocol”, Proceedings of the 6th International Wireless Communications and Mobile Computing Conference, pp: 281-285, June28 – July 2, 2010.
[10] Ashraf Abu-Ein and Jihad Nader,”An Enhanced AODV Routing Protocol for MANETs”, International Journal of Computer Science Issues, Vol. 11, Issue 1, No 1, January 2014.
[11] Julith Jacob and Shinu Koyakutty,”An Improved Flooding Scheme for AODV Routing Protocol in MANETs”, International Journal of Advanced Trends in Computer Science and Engineering, Vol. 3, No. 4, pp: 83-89, September 2014.
[12] Priyaganga Guruswamy, Madhumita Chatterjee,” A Novel Efficient Rebroadcast Protocol for Minimizing Routing Overhead in Mobile Ad-Hoc Networks”, International Journal of Computer Networks and Applications (IJCNA), Vol. 3, Issue 2, March – April 2016.
[13] Perkins C. and E. Royer,“Ad-Hoc On-Demand Distance Vector Routing”, Proceedings of Second IEEE Workshop on Mobile Computing Systems and Applications, pp:90-100, February1999.
[14] Prashant Kumar Maurya, Gaurav Sharma, et al,”An Overview of AODV Routing Protocol”, International Journal of Modern Engineering Research, Vol.2, Issue.3, pp:728-732, May-June 2012.
[15] Abdul Hadi A. R. and Zuriati A. Z.,”Performance Comparison of AODV, DSDV, and I-DSDV Routing Protocols in Mobile Ad Hoc Networks”, European Journal of Scientific Research, Vol. 31, No. 4, pp: 566-576, 2009.
[16] M. Krishnamoorthi and Dr. K. Gokulraj,” A Study on AODV and DSR MANET Routing Protocols”, International Journal of Computer Networks and Wireless Communications (IJCNWC), Vol.5, No 4, pp: 549-555, August 2015.
[17] Kalpana Sharma, Neha Mittal and Priyanka Rathi,”Comparative Analysis of Routing Protocols in Ad-Hoc Networks”, International Journal of Advanced Science and Technology Vol.69, pp:1-12, 2014.
[18] D. B. Jagannadha Rao, Karnam Sreenu and Parsi Kalpana,” A Study on Dynamic Source Routing Protocol for Wireless Ad-Hoc Networks”, International Journal of Advanced Research in Computer and Communication Engineering, Vol. 1, Issue 8, October 2012.
[19] David B. Johnson, David A. Maltz. “Dynamic Source Routing in Ad- Hoc Wireless Networks”, In Mobile Computing, Vol. 353, chapter 5, pp: 153-181, Kluwer Academic Publishers, 1996.
[20] Boon-Chong, Seet-Bu Sung Lee and Chiew-Tong Lau,”Optimization of Route Discovery for Dynamic Source Routing in Wireless Ad Hoc Networks”, IEE Electronics Letters, Vol. 39, No. 22, pp: 1606-1607. October 2003.
Authors
May Sayed A. Nouh is a lecturer at the electronics and communications Dept., the higher technological institute tenth of Ramadan city, Cairo, Egypt. She received her B.Sc. from higher technological institute tenth of Ramadan city in 2010. Since then, she served in different positions and built both practical and theoretical experience in electronics and communications field. Her areas of interest include mobile systems, networks and wireless communications. She supervised on different training students in industrial areas.
Salwa H. EL-Ramly received the B.Sc. and M.Sc. degrees from Ain Shams University, Cairo, Egypt in 1967 and 1969 respectively. She received her D.E.A. (Diplome d'Etudes Approfondies en Electronique) from Grenoble University, France. In 1976, she received her PhD in Electrical Engineering (Communications) from Nancy University, France. From 1976 to August 1982 she was an assistant professor in the Electronics and Communication Engineering Dept., Faculty of Engineering, Ain Shams University. After which she served for 5 years, as an Associate Professor, in the same Faculty. Since 1989 she is a professor of communications systems in the same department where she is also the director of the "Signal Processing & Communications Research Lab" (CSPRL).
M. Zaki is the professor of software engineering, Computer and System Engineering Department, Faculty of Engineering, Al-Azhar University at Cairo. He received his B.Sc. and M.Sc. degrees in electrical engineering from Cairo University in 1968 and 1973 respectively. He received his Ph. D. degrees in computer engineering from Warsaw Technical University, Poland in 1977. His fields of interest include artificial intelligence, soft computing, and distributed systems.