CSC383 Computer Networks
CSC383 Computer Networks
Dr. Allen M. Johnson, Jr.
History…
History…
11stst networks designed to share large-scale networks designed to share large-scale
computational power
computational power
11stst commercially available network system commercially available network system
was IBM’s PROFS system. (mainframes)
was IBM’s PROFS system. (mainframes)
Late 1960s, ARPA started investigating data Late 1960s, ARPA started investigating data
networking.
networking.
– Idea of networking computers of different Idea of networking computers of different
architectures
architectures
…
…
History…
History…
In the late 1970s inexpensive In the late 1970s inexpensive
minicomputers provided time-sharing
minicomputers provided time-sharing
facilities to people within a department.
facilities to people within a department. Organizations installed Local Area Organizations installed Local Area
Networks (LANs) to interconnect these
Networks (LANs) to interconnect these
machines together.
…
…
History…
History…
ARPA chose to investigate a revolutionary ARPA chose to investigate a revolutionary
approach, known as
approach, known as packet switchingpacket switching..
They hired people to work on network They hired people to work on network
research and contractors to turn the designs
research and contractors to turn the designs
into a working system called the
into a working system called the ARPANETARPANET..
This was so successful that ARPA continued This was so successful that ARPA continued
funding research into a networking
funding research into a networking
technology called
…
…
History
History
By the 1970s, internetworking was the By the 1970s, internetworking was the
focus of ARPA research and the
focus of ARPA research and the InternetInternet
had emerged.
had emerged.
ARPA continued funding research into the ARPA continued funding research into the
1980s,
1980s,
Internet became a commercial success in Internet became a commercial success in
the 1990s.
Growth of Internet
Growth of Internet
The Internet has grown from an early research The Internet has grown from an early research
prototype into a global communications system
prototype into a global communications system
that connects every country.
that connects every country.
By 1999, the Internet was growing so fast that a By 1999, the Internet was growing so fast that a
new computer was added to the Internet every
new computer was added to the Internet every
second.
…
…
Growth of Internet
Growth of Internet
…
Protocols and Layering
Protocols and Layering
Computer networks are complex systems Computer networks are complex systems
including both hardware and software.
including both hardware and software. Designers divided the communication Designers divided the communication
problem into subparts, called
problem into subparts, called layerslayers, with the , with the interfaces between the layers defined by
interfaces between the layers defined by
TCP/IP Layered Model
TCP/IP Layered Model
physical layer corresponds to basic network hardware.physical layer corresponds to basic network hardware.
Network interface layer specifies how data is divided into Network interface layer specifies how data is divided into frames for transmission over a network.
frames for transmission over a network.
Internet layer protocols specify the format of packets sent Internet layer protocols specify the format of packets sent
across an internet as well as the mechanisms used to forward across an internet as well as the mechanisms used to forward
packets from a computer through one or more routers to a packets from a computer through one or more routers to a
final destination. final destination.
Transport layer specifies how to provide reliable transfer and Transport layer specifies how to provide reliable transfer and the
the Transmission Control ProtocolTransmission Control Protocol (TCP) software also (TCP) software also
provides additional facilities required by higher-level provides additional facilities required by higher-level
applications. applications.
Probing the Internet
Probing the Internet
Simplest probing tool is the Simplest probing tool is the Packet InterNet Packet InterNet
Groper
Groper, or , or pingping. .
According to the Internet requirements According to the Internet requirements
document
document [RFC 1122] [RFC 1122] , every TCP/IP stack , every TCP/IP stack should implement such a program.
PING Command Example
PING Command Example
penguin(101)% ping -c5 www.netbook.cs.purdue.edu PING lucan.cs.purdue.edu (128.10.19.20) from 193.61.29.127: 56(84) bytes of data 64 bytes from lucan.cs.purdue.edu (128.10.19.20): icmp_seq=1 ttl=235 time=131 ms 64 bytes from
lucan.cs.purdue.edu (128.10.19.20): icmp_seq=2 ttl=235 time=131 ms 64 bytes from lucan.cs.purdue.edu (128.10.19.20): icmp_seq=3 ttl=235 time=131 ms 64 bytes from lucan.cs.purdue.edu
(128.10.19.20): icmp_seq=4 ttl=235 time=131 ms 64 bytes from lucan.cs.purdue.edu (128.10.19.20): icmp_seq=5 ttl=235 time=131 ms --- lucan.cs.purdue.edu ping statistics --- 5 packets transmitted, 5 received, 0% loss, time 4008ms rtt min/avg/max/mdev =
131.394/131.742/131.978/0.317 ms penguin(102)%
• -c5 instructs ping to stop after sending five probes
• summary on the first line indicates an alternative name for the target is
lucan.cs.purdue.edu, that its IP address is 128.10.19.20, and it’s sending 56 bytes of data in an 84-byte IP datagram.
What Good Is PING
What Good Is PING
ConsCons
– Little info for average userLittle info for average user – Not good as debug toolNot good as debug tool
» Output occurs only when computer respondsOutput occurs only when computer responds » Fails if network is congestedFails if network is congested
» PING cannot determine cause of problemPING cannot determine cause of problem
» Some companies configure systems to reject pingsSome companies configure systems to reject pings
ProsPros
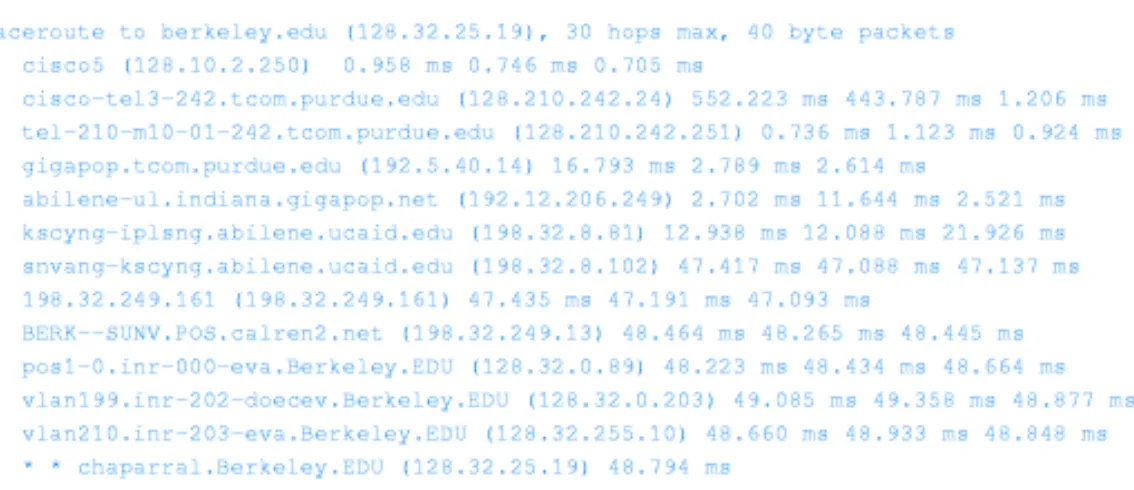
Traceroute
Traceroute
Determine intermediate computers along Determine intermediate computers along
the way
the way
Uses same arguments as PING (remote Uses same arguments as PING (remote
computers name or address)
computers name or address)
Shows how the hops between source and Shows how the hops between source and
destination.
destination.
Figure 2.6
Chapter 3 Introduction
Chapter 3 Introduction
Use of a network requires programs (and Use of a network requires programs (and systems) that are “network-aware.”
systems) that are “network-aware.”
Some applications are usually provided with Some applications are usually provided with machines (e.g. web clients, e-mail clients, file
machines (e.g. web clients, e-mail clients, file
sharing).
sharing).
New custom applications must use the interface New custom applications must use the interface (API) to the network facilities provided by the
(API) to the network facilities provided by the
system.
system.
We will look at a simple API and three sample We will look at a simple API and three sample applications (both the client and the server).
Network Communication
Network Communication
Networks are the mechanisms that transmit data Networks are the mechanisms that transmit data
from one point to another.
from one point to another.
Logically, networks are (or should be) passive, Logically, networks are (or should be) passive,
and do not understand, act on, or modify the data
and do not understand, act on, or modify the data
being moved.
being moved.
There are two ends of a network communication, There are two ends of a network communication,
each associated with an application program that
each associated with an application program that
understands the generation and interpretation of
understands the generation and interpretation of
the data being moved across the network.
Client-Server Computing
Client-Server Computing
The two applications that communicate using a The two applications that communicate using a network must locate each other.
network must locate each other.
Typically, one application (the server) starts and Typically, one application (the server) starts and then waits for the other application (the client) to
then waits for the other application (the client) to
contact it.
contact it.
This arrangement is usually called the This arrangement is usually called the client- client-server paradigm
server paradigm, or just , or just client-server computingclient-server computing.. The client must, of course, be able to locate the The client must, of course, be able to locate the
server for this arrangement to work.
Addressing Internet Applications
Addressing Internet Applications
Each network server application has a two-part address of the Each network server application has a two-part address of the form (
form (computercomputer,,applicationapplication).).
The The computercomputer part of the address identifies the particular part of the address identifies the particular computer on which the application is running. This can be
computer on which the application is running. This can be
provided in symbolic (e.g. apollo.unomaha.edu) or numeric
provided in symbolic (e.g. apollo.unomaha.edu) or numeric
(e.g. 137.48.1.12) form.
(e.g. 137.48.1.12) form.
The application part of the address identifies the particular The application part of the address identifies the particular application. It, too, can be provided symbolically or
application. It, too, can be provided symbolically or
numerically.
numerically.
When transmitted on a network, the (When transmitted on a network, the (computercomputer,,applicationapplication) ) address is always sent in binary.
Communication Paradigm
Communication Paradigm
Most Internet applications follow this basic Most Internet applications follow this basic
sequence of operations for communication: sequence of operations for communication:
– The server starts first, and waits for contact from a The server starts first, and waits for contact from a
client.
client.
– The client contacts the server by specifying its location The client contacts the server by specifying its location
and requesting communication.
and requesting communication.
– The client and the server exchange messages.The client and the server exchange messages.
– After they finish, the client and server each send an After they finish, the client and server each send an
end-of-file
end-of-file to terminate communication. to terminate communication.
Functions are provided in the class library on Functions are provided in the class library on
An Example Application Program Interface
An Example Application Program Interface
The term “application program interface,” or The term “application program interface,” or API, is used to describe the set of operations
API, is used to describe the set of operations
available (in a particular programming
available (in a particular programming
domain) to a programmer.
domain) to a programmer.
The simplified API presented in the textbook The simplified API presented in the textbook hides much of the complexity in network
hides much of the complexity in network
programming, but also doesn’t provide the
programming, but also doesn’t provide the
richness of the usual networking API. We will
richness of the usual networking API. We will
see more details in later chapters.
Example API Overview
Example API Overview
Operation Meaning
await_contact used by server to wait for a contact make_contact used by client to contact a server cname_to_comp translate a computer name to an
equivalent internal binary value appname_to_appnum translate a program name to an
equivalent internal binary value
send used by client or server to send data recv used by client or server to receive data send_eof used by client or server after all data
An Intuitive Look at the API
An Intuitive Look at the API
The application actions usually follow this pattern:The application actions usually follow this pattern:
– The server calls The server calls await_contactawait_contact to wait for contact from a to wait for contact from a
client. The client calls
client. The client calls make_contactmake_contact to establish the to establish the connection. [The server is said to be
connection. [The server is said to be blockedblocked until the until the contact is made.]
contact is made.]
– Once contact is made, the applications use Once contact is made, the applications use sendsend and and recvrecv to exchange data. [The
to exchange data. [The protocolprotocol dictates when each dictates when each application sends or receives.]
application sends or receives.]
– Once the data exchange is complete, the client or the Once the data exchange is complete, the client or the
server terminates the connection by calling
server terminates the connection by calling send_eofsend_eof. . The other application detects the termination of the
The other application detects the termination of the
communication when
A Trivial Example
API Definition – Data Types
API Definition – Data Types
There are three data types (in addition to the usual There are three data types (in addition to the usual
integer, character, and real data types) used in the
integer, character, and real data types) used in the
API:
API:
–appnumappnum: a binary value used to identify an : a binary value used to identify an application [this is really a
application [this is really a port numberport number].].
–computercomputer: a binary value used to identify a : a binary value used to identify a computer [this is really an
computer [this is really an Internet Protocol addressInternet Protocol address, , or
or IP addressIP address.].]
–connectionconnection: a value used to identify one : a value used to identify one
endpoint of a connection between a client and a server endpoint of a connection between a client and a server [normally this identifies a
API Definition –
API Definition –
await_contact
await_contact
A server calls A server calls await_contactawait_contact to wait to wait
for a contact from a client. The function
for a contact from a client. The function
expects one argument of type
expects one argument of type appnumappnum, and , and returns a
returns a connectionconnection which is then used which is then used in
in sendsend, , recvrecv, and , and send_eofsend_eof functions. functions.
connection await_contact connection await_contact
API Definition –
API Definition –
make_contact
make_contact
A client calls A client calls make_contactmake_contact to establish to establish contact with a server. The arguments identify
contact with a server. The arguments identify
the
the computercomputer on which the server is running, on which the server is running, and the application number to be contacted.
and the application number to be contacted.
The function returns a connection used for
The function returns a connection used for
send
send, , recvrecv, and , and send_eofsend_eof by the client. by the client.
connection make_contact (computer
connection make_contact (computer
c, appnum a)
API Definition –
API Definition –
appname_to_appnum
appname_to_appnum
This function is used to translate from a This function is used to translate from a
predefined human-readable name [character
predefined human-readable name [character
string] to a binary application number. Standard
string] to a binary application number. Standard
application names are defined in the /etc/services
application names are defined in the /etc/services
file on a UNIX system. It takes a string argument
file on a UNIX system. It takes a string argument
and returns the binary application number.
and returns the binary application number.
appnum appname_to_appnum (char appnum appname_to_appnum (char
API Definition –
API Definition –
cname_to_comp
cname_to_comp
This function translates a symbolic This function translates a symboliccomputer name (
computer name (cnamecname) to the equivalent ) to the equivalent binary form (which is returned) of type
binary form (which is returned) of type computer
computer..
computer cname_to_comp (char computer cname_to_comp (char
API Definition –
API Definition –
send
send
SendSend arranges to transmit data (a sequence of arranges to transmit data (a sequence of
n
n bytes in a char array bytes in a char array bufbuf) over an established ) over an established connection
connection cc, returning the number of bytes , returning the number of bytes actually transmitted. The last argument is
actually transmitted. The last argument is
always
always 00 in this simplified API. in this simplified API.
int send (connection c, char int send (connection c, char
API Definition –
API Definition –
recv
recv
RecvRecv receives at most receives at most nn bytes of data from a bytes of data from a
connection
connection cc, placing it in a char array , placing it in a char array bufbuf, and , and returning the number of bytes received and stored. returning the number of bytes received and stored.
Recv
Recv will return 0 only when the end of file is will return 0 only when the end of file is reached, and a negative value when an error
reached, and a negative value when an error occurred (e.g.
occurred (e.g. recvrecv without a valid connection). without a valid connection).
int recv (connection c, char *buf, int recv (connection c, char *buf,
API Definition –
API Definition –
recvln
recvln
RecvlnRecvln reads one line of data (terminated by an reads one line of data (terminated by an end of line character) from a connection
end of line character) from a connection cc into a into a char array
char array bufbuf; no more than ; no more than nn-1 bytes will be -1 bytes will be read (allowing one byte for string termination).
read (allowing one byte for string termination).
Recvln
Recvln uses uses recvrecv to read one byte at a time. to read one byte at a time.
int recvln (connection c, char
int recvln (connection c, char
*buf,
*buf,
int n)
API Definition –
API Definition –
send_eof
send_eof
Send_eofSend_eof terminates the connection terminates the connection cc, ,
returning a negative number if an error
returning a negative number if an error
occurred.
occurred.
The ECHO Application
The ECHO Application
The ECHO application server merely resends each line it The ECHO application server merely resends each line it
receives from a client. The server is started (from a
receives from a client. The server is started (from a
command line) by typing the program name and a selected
command line) by typing the program name and a selected
application number (usually in the range 1025 to 32767).
application number (usually in the range 1025 to 32767).
The client application is started by typing its name, the The client application is started by typing its name, the
name of the computer on which the server is running, and
name of the computer on which the server is running, and
the same application number.
the same application number.
Lines are then read by the client, echoed by the server, and Lines are then read by the client, echoed by the server, and
displayed by the client, until an end of file (control-D on
displayed by the client, until an end of file (control-D on
UNIX, or control-Z on Windows) is entered.
UNIX, or control-Z on Windows) is entered.
An Important Observation
An Important Observation
If you examine the code for the echo client, you If you examine the code for the echo client, you
will find that it does not immediately read
will find that it does not immediately read
another line from the keyboard after reading data
another line from the keyboard after reading data
from the connection. This is because recv only
from the connection. This is because recv only
returns as much data as it has actually read.
returns as much data as it has actually read.
The reason for this is that the underlying network The reason for this is that the underlying network
may send a group of data bytes in several
may send a group of data bytes in several
different packets. Thus the received data may
different packets. Thus the received data may
arrive in pieces with sizes different from those
arrive in pieces with sizes different from those
used when the data was sent.
The CHAT Application
The CHAT Application
The chat application is similar to the echo The chat application is similar to the echo
application. Here, however, the server displays
application. Here, however, the server displays
the received data line and waits for a response
the received data line and waits for a response
from the user on that machine, which is then
from the user on that machine, which is then
sent back to the client for display.
sent back to the client for display.
Either the user at the server machine or the user Either the user at the server machine or the user
at the client machine may terminate the chat
at the client machine may terminate the chat
session by entering an end of file.
session by entering an end of file.
The WEB Application
The WEB Application
Our final example is a simple text-mode web server Our final example is a simple text-mode web server and browser. Only two web pages are provided by and browser. Only two web pages are provided by the server: “/” and “/time”. It is easy, however, to the server: “/” and “/time”. It is easy, however, to extend this application to deliver arbitrary pages extend this application to deliver arbitrary pages stored as files on the server machine.
stored as files on the server machine.
The server and client both use the standard HTTP The server and client both use the standard HTTP protocol, and the server delivers HTML documents protocol, and the server delivers HTML documents with appropriate headers. Thus a commercial web with appropriate headers. Thus a commercial web browser could be used to contact our server.