The sum of the carrier and modulated frequencyfcþfmþϕwith the same phase shift of the message signal. Since the frequency is the derivative of the phase, the relationship between the input signal and the frequency can be written as [9]. In this expression, P is the average transmitted signal power and N is the average noise power.
Introduction
- Android and application definition
- Malware definition and statistics
- Android permissions and security model
- Android application scanning framework
Android runtime allows the application to run on mobile devices by converting the Android code into DEX format or bytecode. AndroidManifest.xml file: This describes the app's capabilities and informs the operating system about the other components of the app. It identifies the required hardware and software features such as the camera, in addition to the minimum API level required by the application.
The permissions requested by the application and the permissions needed to access the application's interfaces/data are defined in its manifest file. Dangerous: the permission to private data, system processes and other hardware is referred to as dangerous and must be expressly granted at the time of installation or use of the application. The files in the application are always private unless they are explicitly set to be shared by two modes, (1) readable and (2) writable.
For two applications to share each other's files, the application ID must be the same for both applications, as well as the user ID. If the application or process is allowed to access a Bluetooth, its application ID will be added to the group access list for Bluetooth and similarly for others.
Android application
App source and download
Source code generation
Android application analysis
- Feature extraction
- Static analysis
- Dynamic analysis
- Ransomware detection
- Dataset creation and utilization
However, this approach cannot detect loaded and obfuscated malicious applications at runtime because it relies on static analysis [47]. AppContext identifies applications that use machine learning based on contexts that trigger security-sensitive behaviors (eg, conditions and events that cause security-sensitive behaviors to occur). Non-executable code may be missed by this approach, but it can effectively detect malware behaviors that are not detectable by static analysis.
Wang [57] also proposed a dynamic analysis to analyze an application on the fly to detect malicious behavior. The prototype identifies the state statements in applications that can cause the malicious acts of malware, which cannot be recognized by static analysis. The authors presented R-PackDroid as a static analysis approach that classifies Android applications into ransomware, malware, or benign using random forest classifier.
However, R-PackDroid cannot analyze applications with function code that is dynamically loaded at runtime or classes that are fully encrypted because it relies on static analysis. The main disadvantage is that dynamic analysis is only applied to suspicious applications, leaving the possibility that static analysis will not successfully identify malware.
Android malware application detection and ranking
For example, for Android apps containing malware, VirusTotal has been one of the main sources for many researchers [38, 60]. The authors in [75] used similar hypotheses to list the permissions in each app and count the occurrence of permissions in similar apps (a game category in their case), excluding the user-defined permissions that have no impact on privacy . When discussing the approaches in the existing risk scoring systems and their main reliance on the Android permissions, it is worth asking how many of them have considered involving the user in the scoring results and, if they decided to involve the user , how the risk was displayed and communicated to the user.
They calculated the level of risk based on the type of permissions and the likelihood that they will be requested by the app. In addition to the permissions and their categories, they also took input from various antivirus tools to calculate the score. On the other hand, the authors in [80] have considered the statistical distribution of the Android permissions in addition to the probabilistic functions.
From the related work above, we can see that most of the previous solutions relied primarily on permissions either statistically or by probability to analyze Android apps, classify them as malware and measure their level of risk. Such approaches resort to static analysis of the malware and others use dynamic analysis while some methods use both static and dynamic analysis to better detect a malicious incident.
Statistical analysis
In addition, the generated datasets will be analyzed to detect potential security threats, regardless of whether these datasets have been compiled on the basis of static or dynamic tests or even both. Typically, data mining techniques can be used to detect and classify attacks [42, 52]. In addition, intelligence techniques can be used to even rank the risk by assigning the attack a risk score [42, 86].
The scanning service could provide results in the development of a mobile application installed on the user's devices to inspect the Android application and discriminate whether it is a clean application or a malicious application to alert the user and protect her/his Android device. Another example of anti-malware software is HinDroid [88], which was integrated as one of Comodo's mobile security scanning tools. HinDroid structures APIs based on a heterogeneous information network to predict the application under test.
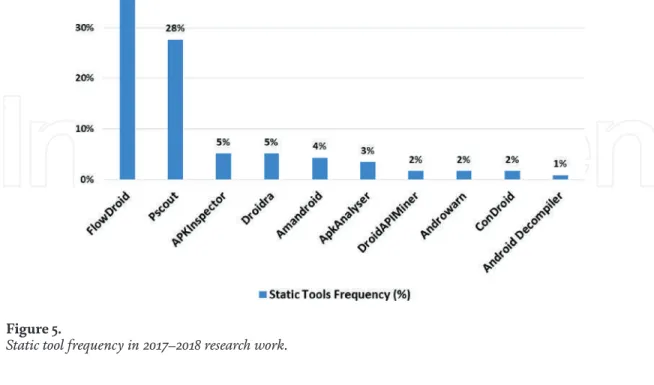
We can see that 48% of statically designed systems used the FlowDroid tool in their solutions.
Conclusions
In: Proceedings of the International Conference on Cyber Security and Protection of Digital Services 2017 (Cyber Security). Proceedings of High Performance Computing and Communications (HPCC), 2015 IEEE 7th International Symposium on Cyberspace Safety and Security (CSS), 2015 IEEE 12th International Conference on Embedded Software and Systems (ICESS), 2015 IEEE 17th International Conference on. In: Proceedings of the IFIP International Conferences on Security of ICT Systems and Protection of Privacy (SEC).
In: Proceedings of the 23rd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining—KDD 17. This chapter discusses the expandability of fiber to the x (FTTx) households, particularly in the territory of the European Union. The Czech Republic has committed to other Member States to provide half of households with connectivity of at least 100 Mbit/s by 2020.
The cost of the next generation PON terminal units (XG-PON) is still quite high regardless of the price of the OLT unit. The price of the technology itself is determined by the price of the optical network unit (ONU) terminal units.
Current state of the access networks in the Czech Republic
The available bandwidth can be operationally changed over time and according to demand using dynamic bandwidth allocation (DBA) algorithms [10–13]. The ever-lower costs of the necessary devices allow service providers to use GPON optical line termination (OLT) more often; on the other hand, the standard in use may not be sufficient for the future. The advantage of deploying next-generation networks would be the ability to achieve a total transmission speed of up to 10 Gbit/s.
GPON networks theoretically allow us to transfer data at up to 19 Mbit/s for each ONU (considering for the maximum transfer rate and a split ratio of 1:128). In other words, the transfer speeds are the highest possible in both GPON and XG-PON networks. Usually the guaranteed transfer rates are many times lower when using a transmission container (T-CONT) [14].
In contrast, FTTx connections only depend on the chosen standard as with the fiber to the home (FTTH) version. FTTx connections can support transmission rates up to 10/10 Gbit/s (depending on the number of end units connected to the OLT control unit).
Household penetration
Another goal of the current FTTB/H connection analysis is to focus on the global market (see Figure 3). IDATE focused on the global market analysis and comparison of the state of connections in buildings in four phases, December 2014, September 2015, September 2016 and September 2017 (see Figure 4). Unfortunately, the Czech Republic has not been included in this analysis because the number of connections is not that great.
The report shows that at the end of 2010 the total number of customers was balanced between the EU28 and the Commonwealth of Independent States (CIS). However, this difference must be attributed in particular to the 11 other countries that we count in the EU39. Later, the number of EU28 parties increased and the previous dominance of the CIS declined.
In September 2017, the total number of customers was about 25 million, while for CIS it was "only". During the preparation of the work, the developers are working hard to build the data infrastructure and negotiations are taking place between the Internet Service Providers (ISPs) and the developers.
Access networks and 5G networks
In general, the reach of NG-PON2 (up to 20 km from the OLT) is sufficient to cover an acceptable number of end users and for the effective use of its coverage (the division of the covered territory into several sectors/smaller cells ). Using a coexistence element (CE), such a coexistence scheme can be created for older PON standards according to ITU recommendations. A disadvantage of this radio tower connection method is the custom blocking method that is publicly available, but is much more complex than in the case of the IEEE network.
GPON frame structure and activation process analysis
OMCI channel analysis
At this point, the critical phase of the OMCI analysis is the inspection of the software image entity type, as the ONU must be authorized by its own serial number against the database of the OLT (depending on the specific ISP implementation). In case the OLT does not have the ONU's record in the database, the ONU is not allowed to download the software image along with the configuration. The message parameters are reported as "inactive" because they are in the initial stages of downloading the file.
In the case of most service providers, this value is set to 512 kbit/s. In summary, by analyzing the OMCI channel data, we performed active monitoring of distribution network alarms. A special case of the activation process is the message sequence that can be seen in Table 3.
This part of the activation is not mandatory for end units, but is the last deactivation process aimed at the previously assigned parameters, mostly the ONU ID. When a certain number of errors are detected, which are mostly defined by the manufacturer of the control unit, a "Dying Gasp" message follows.
Conclusion
This chapter is distributed under the terms of the Creative Commons Attribution License (http://creativecommons.org/licenses/.by/3.0), which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly quoted . Tomas Horvath would like to dedicate his role to his girlfriend (Lucie Baierova) and his family (Dagmar, Jan and Petra). He also wants to thank Ales Buksa for his support of the university.