Java Network Programming Developing Networked Applications 4th Edition pdf pdf
Teks penuh
Gambar



Dokumen terkait
Each user was located in client area that will login to access a Web Server SI, then immediately directed (redirect) to the CAS Server that was located in the SSO Server Area with
Because it would be time-consuming to add dependencies manually with --add-modules, all automatic modules on the module path are automatically resolved when the application requires
Even though the client has dual IBGP sessions to two route reflectors, the router that is designated as the route reflector (physically connected) in the cluster is already a
Similarly, if you’re running an internal mail server and want to monitor email that exits your enterprise, you’ll need to prevent your users from send- ing email through external
The implicit deny policy should be applied to all aspects of an organization’s security, from physical security and access control, to file and resources permissions on a file
If one of the operations that is used in the algorithm is division, then we need to work in arithmetic defined over a field.. For convenience and for implementation efficiency,
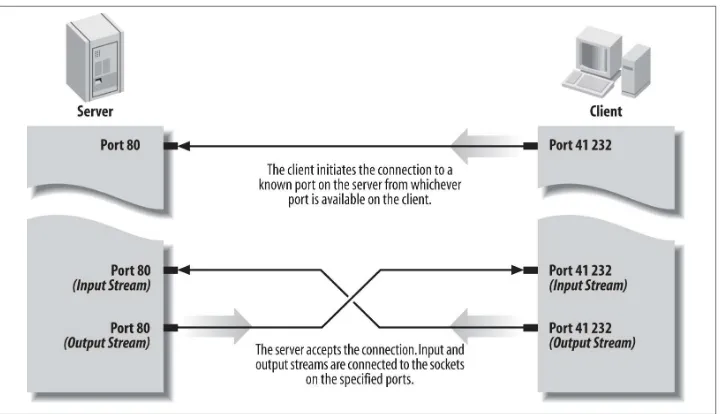
The easiest kinds of links are actually links to a spot on another Web server. That’s because you can easily get the URL for the link — it’s the same as the URL you see when you go