Security Mechanism for IPv6 Stateless Address
Autoconfiguration
Supriyanto Praptodiyono
Electrical Engineering Department Universitas Sultan Ageng TirtayasaCilegon, Banten, Indonesia [email protected]
Iznan H. Hasbullah
National Advanced IPv6 CentreUniversiti Sains Malaysia Penang 11800 Malaysia
Mohammed M. Kadhum
National Advanced IPv6 CentreUniversiti Sains Malaysia Penang 11800 Malaysia [email protected]
Raja Kumar Murugesan
School of ComputingTaylor’s University Kuala Lumpur, Malaysia [email protected]
Chong Yung Wey
National Advanced IPv6 CentreUniversiti Sains Malaysia Penang 11800 Malaysia [email protected]
Azlan Osman
School of Computer SciencesUniversiti Sains Malaysia Penang 11800 Malaysia
Abstract—Internet Protocol version six (IPv6) was designed and developed to solve the problem of exhaustion of current Internet address. IPv6 also introduces a number of benefits including address auto-configuration mechanism which allows host to self-generate its own IPv6 address without the presence of a DHCPv6 server. It is one mechanism, among others, provided by Neighbor Discovery Protocol (NDP). However, the protocol does not have a built-in security mechanism and its messages were exchanged without security verification thus leaving the mechanism vulnerable to exploitation by malicious nodes. A malicious node could disrupt or tamper with the IPv6 address auto-generation process that will leave the victim without an IP address needed for communication or having a wrongly formed address. . The NDP standard suggests either IPSec or SeND to secure the mechanism. Unfortunately, both security mechanisms have been extensively studied and were reported to have serious drawbacks that limit their implementation and adoption. This research proposes Trust-ND to secure IPv6 address auto-configuration mechanism based on a distributed trust mechanism. Experiment result shows that this mechanism is more lightweight and uses less bandwidth while still able to fulfill the required security feature.
Keywords—IPv6; address auto-configuration; Trust-ND; security; neighbor discovery
I. INTRODUCTION
Internet grows extremely fast in the last decade. It has been connecting people on around the world. In the future, the Internet not only connects computers but also other electronic equipments and then called Internet of Thing concept [1]. The growth of Internet obviously requires large space of IP address. Since the current Internet Protocol, IPv4 has depleted its IP address space; IETF developed a new version of IP, and then named IPv6. The development of IPv6 not only solves the IP address problem but also introduces some benefits.
One of the improvements on the IPv6 is stateless address auto-configuration (SLAAC) mechanism [2]. Using this mechanism, an IPv6 host is able to generate IPv6 address automatically without any help from DHCP server. This address generation mechanism is provided by the Neighbor
Discovery Protocol (NDP) [3]. NDP uses five ICMPv6 messages to perform the address auto-configuration. However, since there is no security verification for NDP messages exchange, SLAAC is prone to various attack vectors.
Attackers can exploit one or more NDP messages used by SLAAC mechanism to disturb the address generation process or making the generated address wrongly by sending wrong prefix information. Either way, the host cannot communicate with other nodes or it communicates using a wrong address. Hence, the SLAAC mechanism needs to be secured. The importance of securing SLAAC has attracted a number of researchers to propose security mechanism for SLAAC such as [4-7].
Original standard on NDP, RFC 4861 recommends to use IPSec [4] or Secure Neighbor Discovery (SeND) [5] on securing SLAAC. IPSec is a complete security mechanism for network layer. However, since SLAAC is an operation performed by a new IPv6 host that has yet to have any IPv6 address, the implementation of IPSec faces bootstrapping issue as analyzed by [8]. SeND mechanism was recommended to solve security issue on NDP including SLAAC, but its implementation is not trivial. This is because SeND mechanism adds four options on NDP messages which include CGA option and RSA signature option. The two options require high resources on their computation and consume high bandwidth as studied in [7].
In order to address the heavy computation on SeND mechanism, a Simple Secure Addressing Scheme for IPv6 Auto-configuration (SSAS) was proposed by [6]. SSAS introduces a different signature scheme compared to SeND that resulted in the faster message generation and verification. However, the signing process still requires significant amount of time that reaches 367.59 milliseconds if using RSA algorithm and 223.08 milliseconds if using ECC algorithm. It increases when security level is higher. SSAS mechanism adds SSAS signature option on NDP messages. As the issue on SeND is CGA and RSA signature processing and bandwidth consumption, the adding of SSAS signature option would 2015 International Conference on Automation, Cognitive Science, Optics, Micro Electro-Mechanical System, and
Information Technology (ICACOMIT), Bandung, Indonesia, October 29–30, 2015
result are larger NDP messages and thus, the NDP packet size will also increase. As a result, SSAS mechanism will consume higher bandwidth.
This paper introduces Trust-ND for securing SLAAC using a lightweight and distributed trust mechanism. The rest of this paper presents an overview of SLAAC in Section 2 followed by related works in Section 3. Section 4 discusses the implementation of Trust-ND on securing SLAAC. Section 5 provides the results and discussion and followed by a conclusion of this paper on Section 6.
II. OVERVIEW OF SLAAC ON IPV6
IPv6 address consists of two parts: network prefix and interface identifier. IPv6 supports both manual address configuration and address auto-configuration. The protocol involves two types of address auto-configuration mechanisms: stateful and stateless mechanism. The first mechanism uses DHCPv6 server as in the current IPv4 central address distribution. The second mechanism – the focus of this research – does not use DHCPv6 server but uses default router information to generate IPv6 address. An IPv6 host obtains network information including network prefix from router using router advertisement (RA) message and generate the interface identifier by itself. The mechanism is illustrated in Fig. 1.
Fig. 1. Stateless Address Auto-Configuration.
In the figure, there is no DHCP server connected. Default router is an access router that supports IPv6 and placed in the same link with the IPv6 hosts. The default router sends RA message containing prefix information, router lifetime and other information. The RA message is sent periodically every five minutes to all hosts connected to the router. After receiving the RA message, IPv6 host uses the information to configure IPv6 address by concatenating IPv6 prefix inside the message and an its own generation interface identifer. In case of no RA message received, the host can request the message by sending router solicitation (RS) to multicast group of router in the link.
Generation of interface identifier at the host machine could use one or more mechanisms. Firstly, EUI-64 mechanism by using the uniqueness of MAC address of each interface. This mechanism is mainly used by Unix OS. Secondly, random generation or privacy extension mechanism which is used in Windows OS. Whichever mechanism to generate interface identifier is used, both will require information inside the RA message.
However, the generated IPv6 address by the host is considered as tentative address, until it has been determined not being used by other host within the network. The detection mechanism is called duplicate address detection (DAD). The
DAD is performed by sending neighbor solicitation message (NS) to all neighbors in the link with the tentative address as the target. If there is no respond from the neighbors, the address is considered o be unique. Otherwise, there is address duplication. In this case, the host should generate other tentative address.
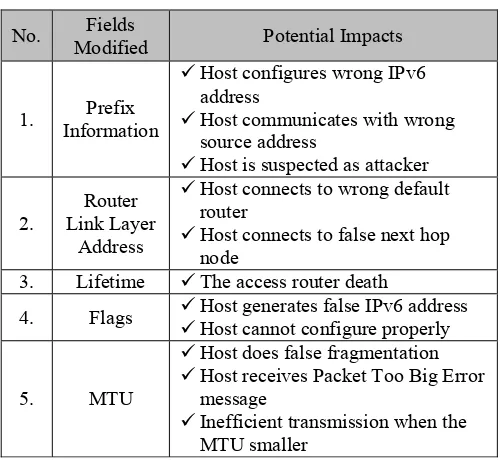
Since RA message information is important for stateless address auto-configuration mechanism on IPv6, neglecting its security exposes the mechanism to attack. Attacker could exploit the message to do malicious activities. Malicious nodes may modify one or more fields on the RA message. Table 1 lists potential impacts on modifying RA message.
TABLE I. IMPACTS ON MODIFYING RAMESSAGE
No. Fields
Modified Potential Impacts
1. Prefix Information
9Host configures wrong IPv6 address
9Host communicates with wrong source address
9Host is suspected as attacker
2.
Router Link Layer
Address
9Host connects to wrong default router
9Host connects to false next hop node
3. Lifetime 9The access router death
4. Flags 99Host generates false IPv6 address Host cannot configure properly
5. MTU
9Host does false fragmentation
9Host receives Packet Too Big Error message
9Inefficient transmission when the MTU smaller
Some experiments were done by Marc Houser [9] on exploiting RA message as listed in Table 2. The exploitation caused a number of operating system to crash and freeze. Considering the impact of RA message exploitation, a security mechanism on preventing RA exploitation is needed. Related works on securing NDP message especially RA message is discussed in Section 3.
TABLE2.EXPERIMENTS ON EXPLOITING RAMESSAGE
No. Experiments Operating
System Impacts
1. RA flood
Windows, Android, MacBook Air,
iPad1
Freezing
2. Wireless Attack iPad 3
Consume 10 – 20% CPU,
Crashes
3.
More Prefix Information
Option
Mac Crash
4. DoS Attack by
RA Packets All Windows Freezes Totally RA Message
III. RELATED WORKS ON SECURING SLAAC
As introduced in aforementioned Section 1, there are three recommended security mechanisms on securing SLAAC. This section provides detail evaluation and discussion on the mechanisms to understand the reason for their limited implementation. IPSec is a network security mechanism that is used not only in IPv6 but also in IPv4. It provides integrity, confidentiality and non-repudiation as important security goals. However, when implemented on SLAAC, IPSec has a number of issues such as its performance and the bootstrapping phase. Decreasing performance of IPSec is due to the heavy reliance on encryption algorithm [10]. The issue of bootstrapping phase arises because when the host is undergoing SLAAC process, its network interface is not yet assigned an IP address which is required by IPSec to establish security association [8]. Furthermore, the IPSec cannot be implemented in the stage, or otherwise the use of manual keying that is impractical on a large network.
Ferguson & Schneier [11] and Stockebrand [12] criticized the cryptographic mechanism of IPSec. The security protocol is overly complex but fulfills only a limited range of security goals at a very high price. In addition, it only operates in network layer that does not cover transport layer and application layer, thus requires the use of other security such as SSL (Secure Socket Layer), TLS or SSH (Secure Shell). Specification of IPv6 security architecture requires MD5 for the computation. However, MD5 has been shown to have problems especially on the current high-speed data transfer [13]. The problems with using MD5 in IPv6 include the higher latency cost compared to the value used and the processor was occupied entirely by the computation of MD5 algorithm. In addition, MD5 was found to be vulnerable to collision attack in 2004 [14]. As a result, the usage of MD5 is not recommended.
Secure Neighbor Discovery (SeND) is introduced to address the issue on IPSec especially on the bootstrapping phase. It introduces four NDP options: CGA option, Nonce option, Timestamp option and RSA signature option as well as two ICMPv6 messages: Certificate Path Solicitation (CPS) and Certificate Path Advertisement (CPA) as specified in [5]. This mechanism is believed to prevent malicious attacks on IPv6 neighbor discovery. However, it has been reported to have a number of drawbacks as investigated by [7, 15, 16]. Firstly, SeND introduces high computation to generate the options especially the CGA option and RSA signature. When used with higher security level, the computation time also increased. Secondly, the four options introduced by SeND expanded the size of NDP messages by 368 bytes for each message. This resulted in increased network bandwidth consumption.
The usage of RSA signature on SeND was analyzed by [15]. Based on the analysis, RSA signature mechanism adds significant processing time on SeND as shown in Table 3. When SeND does not include RSA signature, it requires only 0.44 milliseconds. When RSA algorithm is used on SeND operation the processing time increases up to 75.97
milliseconds. This showed that RSA is the source of 99% of processing time increase on SeND.
TABLE3.PROCESSING TIME OF SEND
Protocol ICMPv4 NDP SeND w/o
RSA SeND
Processing
Time (ms) 0.29 0.34 0.44 75.97
The operation of SeND begins with the generation of CGA address for IPv6 nodes that implements SeND. The IPv6 address is generated using cryptographic algorithm as specified in RFC 3972. Sending node generates SeND messages which are actually NDP messages with an additional four NDP options provided by SeND mechanism. CGA option delivers a public key from the IPv6 address where the key originates. This key allows receiver to verify the digital signature using its corresponding private key. The RSA signature option proves that the public key in the CGA option corresponds to the receiver’s private key. Cost for the generation of CGA address is O(259+16*sec) as analyzed by [17]. The CGA generation time depended on Sec value: the higher the Sec values, the longer the generation time. RSA signature involves key generation, encryption or signing process and decryption or verification process as specified in RFC 3447. Time complexity of RSA signature is O(n2) as analyzed by [18] where n is the key size.
The complexity of CGA as well as RSA signature causes the implementation of SeND in IPv6 environment to be limited. Even though major networking device vendors such as Cisco and Juniper have been supporting SeND in their routers to various degrees, major operating system vendors have been reluctant to provide a decent level of support [7]. Existing implementations of SeND such as Easy-SeND [19] and WinSeND [20] are basically proofs of concept rather than production-ready implementation. In addition, Easy-SeND author has yet to implement router authorization messages. This has encouraged researchers to analyze the use of SeND in order to study its performance and drawbacks that has been a limiting factor for its adoption as the default security mechanism to secure SLAAC.
RSA. The author claimed ECC took only 223.1 milliseconds instead of 367.6 milliseconds required by RSA to perform signature related processes. The decrease of processing time of SSAS is due to the significant reduction in key size of ECC which is only 192 bits instead of 1280 bits used by RSA.
IV. IMPLEMENTATION OF TRUST-ND ON SLAAC The introduction of SLAAC in IPv6 is evidence that the protocol supports the decentralization mode of operation. SLAAC provides each individual host in IPv6 network with a capability to generate its own IPv6 address without depending on a server. Nevertheless, the support for centralized management of IPv6 address allocation is still available via DHCPv6, if needed.
In line with the decentralized nature of SLAAC, Trust-ND make use of distributed trust management concept to secure SLAAC. Trust-ND nodes perfoming SLAAC operation is allowed to generate and verify Trust-ND messages as well as to maintain and update its own trust table. Each Trust-ND node could either be a sender or a receiver of Trust-ND messages. Each node independently calculates trust value of its neighboring nodes on the same link. Trust-ND nodes do not distribute trust value, thus do not require a central authority or a server for such purpose. The trust value calculation is based on Beta Reputation System [21].
Trust-ND improves security on the NDP by introducing a new ICMPv6 option called Trust Option [22]. The Trust Option includes three main fields: Message Generation Time, Nonce and Message Authentication Data. The Message Authentication Data is a result of SHA-1 operation as the message integrity check. It is attached to all five NDP messages to fulfill the security goals. The NDP messages are then named as Trust-RS, Trust-RA, Trust-NS, Trust-NA and Trust-Redirect respectively. Trust-ND messages are used by IPv6 nodes that implements Trust-ND on IPv6 NDP operation. Sending node generates the Trust-ND messages and receiving node verifies the messages. Upon receiving the Trust-ND messages, receiver conducts trust computation. Results of the computation are trust status of the sender that could take one of three values: trusted, distrusted or uncertainty. The result of the calculation will be stored by the receiver in its trust neighbor cache table.
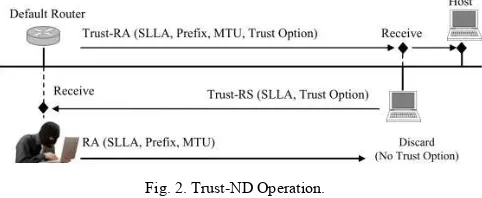
Fig. 2 shows the operation of Trust-ND in IPv6 local network. The default router sends Trust-RA which is an RA message carrying Trust Option to all nodes multicast group in the link. In the case of a host not able to receive Trust-RA message, it can solicit a request by sending Trust-RS message to the router. Receivers, either host or a router, should verify Trust-ND messages. The first verification is a validation process on the received NDP message which is exactly similar to existing NDP mechanism. A message is considered as valid if it has correct checksum, hop limit value of 255 and the message length is in multiple of 4 bytes. The next validation process is verification of the availability of Trust Option. Any NDP message without Trust Option is automatically considered to be unsecured; otherwise the process will proceed to the next verification stage. The third verification is checking the value of message generation time, Nonce and
Message Authentication Data as the main content of Trust Option.
Fig. 2. Trust-ND Operation.
After the verification, receiver performs trust calculation for the message sender. The trust calculation is based on the verification result and knowledge based on previous information. The trust calculation yields one of three trust status: trusted, distrusted or uncertainty. Trusted status is issued if a good verification is obtained and good previous experience for the sender stored. Distrusted is given if one or both of the two components of trust calculation result in bad value. Uncertainty status is assigned if the message is a first message received from the particular sender and there is no prior record available in the trust table. The status of a sender is then stored in node’s trust table for future trust calculation.
V. RESULT AND DISCUSSION
The main issue of SeND mechanism is complexity. This is the main consideration on designing Trust-ND. Trust-ND integrates both traditional hard security and soft security approaches to reduce the complexity. The integration is in the form of message verification and trust calculation as discussed in aforementioned section. This section provides result on implementation of Trust-ND and discussion to benchmark the performance of Trust-ND on securing SLAAC.
Implementation of Trust-ND is done in an isolated IPv6 network to avoid interruption to existing network. Apart from Trust-ND, implementation of the standard NDP and SeND mechanisms were also performed for comparison. Three parameters are used to measure Trust-ND performance on securing NDP especially SLAAC on IPv6. First, complexity both in generation and verification since the complexity is the main issue on SeND. Second, bandwidth consumption is measured as a consequence of extending NDP message size by adding new options. Third, integrity checking performance is included also as the main function on securing NDP from exploitation. The analysis is then discussed in the next paragraphs.
the time required performing the process increases in quadratic form, which is in a non-linear fashion. In Big-O analysis, a linear time algorithm is always faster than a quadratic-time algorithm.
As mentioned earlier, Trust-ND uses SHA-1 to provide message integrity check. Big-O notation for SHA-1 is O(n), where n is the message size [23]. Thus, the complexity of Trust-ND depends on the message size. Larger NDP message needs more time than smaller message size. Since the Big-O notation of SHA-1 is in linear category, the complexity of Trust-ND is linear accordingly. Based on Big-O categories, an algorithm with a linear complexity is faster than the one with quadratic complexity. Hence, SeND mechanism that uses RSA signature is slower than Trust-ND that uses SHA-1 algorithm.
In addition, based on the benchmark provided in [24], the generation of RSA 1024 signature is 1.48 milliseconds per operation and 0.07 milliseconds for verification. Further, the use of RSA signature option in SeND resulted in a very high processing time. If SeND is operated without RSA, it only requires 0.44 milliseconds; whereas with RSA, the processing time increases significantly to 75.97 milliseconds (see Table 3). This implies that the use of RSA took 172 times longer than without RSA option. In other word, RSA signature has added 17,166% for the SeND processing time. However, without RSA, SeND is useless because it is used to protect the integrity of NDP messages and to authenticate the sender of the messages.
SASS uses elliptic curve cryptography (ECC) as the signature algorithm to change RSA algorithm. In term of complexity, the ECC algorithm has sub-quadratic complexity as elaborated in [25]. With a shorter key, the usage of ECC implementation on SASS signature scheme makes it faster than RSA used in SeND. However, since the ECC Big-O notation is sub-quadratic, it still contains a quadratic component and the worst case time complexity is also O(n2) as with RSA.
There are two parameters used to calculate the bandwidth consumption: packet length and transmission time. Packet length is the total bytes of the entire NDP message with the use of all general defined ICMPv6 options; while the total time of transmission is assumed to be constant for any NDP messages since the experiment is conducted in the same local network with the same medium. Each of the NDP messages has different length based on the options contained within the NDP message. Measurement of the bandwidth consumption can be done by calculating the total size of all NDP messages used in SLAAC process as shown in Table 4.
TABLE4.COMPARISON OF BANDWIDTH CONSUMPTION
Comparison on Table 4 is only for SeND with the reason the size of SeND is fixed and it has been standardized in RFC
3971. The option size is 368 bytes that has to be attached in each NDP messages. In contrast, Trust-ND just adds 32 bytes option. As a result, the implementation of Trust-ND could reduce bandwidth consumption by up to 32.256 Kbps for every SLAAC process. The saved bandwidth can be utilized by other processes in the local network. In addition, the smaller messages size also reduces potential network delay in the network due to congestion.
The last measurement is on the performance of integrity checking of Trust-ND. One of the drawbacks on the existing NDP is unavailability of satisfying integrity check. It uses checksum as other ICMPv6 messages. However, in the sense of security, checksum has some disadvantages as summarized in [26]. First, it has low assurance against malicious attack. Further, the checksum cannot protect the data from malicious activities. Second, it is very simple to create a new data with matching checksum. If only checksum is used, the possibility to fool the receiver by creating the same checksum value is higher.
Trust-ND uses SHA-1 algorithm to generate a hash code. The hash code is carried in the Message Authentication Data field to ensure the integrity of Trust-ND messages. Experiments were done to study the ability of Trust-ND to prevent spoofing attacks by executing some hacking tools such as parasite6 and replay attack. Fig. 3 is a captured Trust Neighbor Cache of a victim when attacked. The last entry in the list is the sender IP address for the spoofed Trust-ND message.
Fig. 3. Trust Neighbor Cache of Victim.
The value of trust in the last entry is 0.0 which means the alteration on Trust-ND message has been detected by the victim’s machine. Trust-ND is able to protect the host from spoofing attacks. Spoofing attacks could be done by spoofing the sender’s identity or altering the message content. Since the attacking activity is done by an attacker acting as a middle man, the receiver should be able to detect the spoofed packet. This is because the Message Authentication Data generated by the original sender will be different from the one generated by the man in the middle. The message is suspected as distrusted when it fails the verification process. Otherwise, it will be considered as trusted.
In term of integrity checking, SeND mechanism relies on RSA signature option. RSA signature is used to ensure the integrity of the message and also to authenticate the sender of the message. However, as discussed earlier, RSA is a highly complex algorithm and this remains as the main issue of SeND mechanism. Hence, Trust-ND mechanism was designed to use lightweight algorithm in its operation to avoid the pitfall of SeND. The experiment result showed that Trust-ND could achieve the integrity requirement on NDP with low NDP Process Trust-ND SeND Saved (Kbps)Bandwidth
Kbps % Kbps %
complexity. In addition, with less complexity, message processing time is reduced and this means SLAAC operation would be concluded faster without compromising security.
VI. CONCLUSION
Neighbor discovery protocol in IPv6 provides a mechanism for host to self-generate its own IPv6 address without the presence of a DHCPv6 server. This mechanism is known as Stateless Address Auto-Configuration or SLAAC. Unfortunately, since NDP was not designed with built-in security mechanism, SLAAC is vulnerable to various attacks. Standard on SLAAC suggested Secure Neighbor Discovery or SeND to secure the mechanism. However, SeND is overly complex of a security mechanism for this particular purpose. This is the reason for lack of adoption and implementation of SeND on most common operating system. This research proposes Trust-ND as a new lightweight alternative security mechanism on SLAAC. We introduced Trust Option which includes a Message Authentication Data to provide integrity check. Analysis was performed on Trust-ND performance which measures complexity, bandwidth consumption and integrity check. Results of the experiments showed Trust-ND is lighter than SeND. It also consumes less bandwidth than SeND since the number of options and sizes were reduced. On the integrity analysis, Trust-ND is able to detect alteration on the message content. However, since the experiments were performed on a limited-sized network, further research can be carried out to measure its scalability performance by implementations on larger network.
ACKNOWLEDGMENT
This research was supported by the Research University Grant No: 1001/PNAV/811298 funded by Universiti Sains Malaysia, in collaboration with Directorate General of Higher Education, Ministry of Science, Technology and Higher Education, the Republic of Indonesia; and Taylor’s University, Malaysia.
REFERENCES
[1] Gubbi, J., et al., "Internet of Things (IoT): A vision, architectural elements, and future directions", Future Generation Computer Systems, 2013. 29(7): pp. 1645-1660.
[2] Thomson, S., T. Narten, and T. Jinmei, "IPv6 Stateless Address Autoconfiguration", in Request for Comments 4862, 2007, Internet Engineering Task Force.
[3] Narten, T., et al., "Neighbor Discovery for IP version 6 (IPv6)", in Request for Comments 4861, 2007, Internet Engineering Task Force. [4] Kent, S. and K. Seo, "Security Architecture for the Internet Protocol",
in Request for Comments: 4301, 2005, Internet Engineering Task Force.
[5] J. Arkko, E., et al., "SEcure Neighbor Discovery (SEND)", in Request for Comments: 3971, 2005, Internet Engineering Task Force.
[6] Rafiee, H. and C. Meinel, "SSAS: A simple secure addressing scheme for IPv6 autoconfiguration", in 2013 Eleventh Annual International Conference on Privacy, Security and Trust (PST). 2013.
[7] AlSa'deh, A. and C. Meinel, "Secure neighbor discovery: Review, challenges, perspectives, and recommendations", Security & Privacy, IEEE, 2012. 10(4): pp. 26-34.
[8] Arkko, J. and P. Nikander, "Limitations of IPsec policy mechanisms", in Proceedings of the 11th international conference on Security Protocols 2005, Springer-Verlag: Cambridge, UK.
[9] Hause, M, "Killing Mac OS X and Server 2012". Available from: https://samsclass.info/ipv6/proj/RA_flood2.htm#1. 2012.
[10] Wen, X., et al., "Performance investigation of IPsec protocol over IPv6 network", Proceedings of the 2010 International Conference on Advanced Intelligence and Awarenss Internet (AIAI 2010). 2010. [11] Ferguson, N. and B. Schneier, "A Cryptographic Evaluation of IPsec"
2003: Unpublished Work.
[12] Stockebrand, B., "IP Security (IPsec)", in IPv6 in Practice. 2007, Springer Berlin Heidelberg. p. 311-317.
[13] Barchett, L.D., et al., "Problems using MD5 with IPv6". Perform. Eval., 1996. 27-28: pp. 507-518.
[14] Xie, T. and F. Dengguo, "How To Find Weak Input Differences For MD5 Collision Attacks", Available from: https://eprint.iacr.org/2009/223.pdf. 2009.
[15] Gaeil, A., et al. "Analysis of SEND Protocol through Implementation and Simulation". in Proceedings of the International Conference on Convergence Information Technology, 2007.
[16] Supriyanto, et al., "Survey of Internet Protocol Version 6 Link Local Communication Security Vulnerability and Mitigation Methods". IETE Technical Review, 2013. 30(1): pp. 64-71.
[17] Qadir, S. and M.U. Siddiqi, "Cryptographically Generated Addresses (CGAs): A survey and an analysis of performance for use in mobile environment", International Journal of Computer Science and Network Security, 2011. Vol. 11(No. 2).
[18] Khatoon, A.A., AI, "Performance Evaluation of RSA Algorithm in Cloud Computing Security", International Journal of Innovation and Scientific Research, 2014. vol. 12(no. 1): p. pp. 336-345.
[19] Chiu, S. and E. Gamess, "A Free and Didactic Implementation of the SEND Protocol for IPv6 Machine Learning and Systems Engineering", Springer Netherlands. p. 451-463. 2010.
[20] Rafiee, H., A. Alsa'deh, and C. Meinel, "WinSEND: Windows SEcure Neighbor Discovery", in Proceedings of the 4th international conference on Security of information and networks, ACM: Sydney, Australia.
[21] Josang, A. and R. Ismail. "The beta reputation system". in Proceedings of the 15th Bled Electronic Commerce Conference. 2002.
[22] Praptodiyono, S., et al. "Improving Security of Duplicate Address Detection on IPv6 Local Network in Public Area". in 2015 9th Asia Modelling Symposium. 2015. Kuala Lumpur: IEEE Computer Society.
[23] Cormen, T.H., et al., "Introduction to Algorithm". 2009, Massachusetts London, England: The MIT Press Cambridge, McGraw-Hill Book Company
[24] Dai, W., "Crypto++ 5.6. 0 benchmarks". Available from: http://www. cryptopp. com/benchmarks. html, 2009.
[25] Venturini, Y.R. and U. Sorocaba, "Performance analysis of parallel modular multiplication algorithms for ECC in mobile devices". Revista de Sistemas de Informaçao da FSMA, 2014(13): pp. 57-67. [26] Hosmer, C., "Proving the integrity of digital evidence with time".